Internet infrastructure giant Akamai last week released a special State of the Internet report. Normally, the quarterly accounting of noteworthy changes in distributed denial-of-service (DDoS) attacks doesn’t delve into attacks on specific customers. But this latest Akamai report makes an exception in describing in great detail the record-sized attack against KrebsOnSecurity.com in September, the largest such assault it has ever mitigated.
“The attacks made international headlines and were also covered in depth by Brian Krebs himself,” Akamai said in its report, explaining one reason for the exception. “The same data we’ve shared here was made available to Krebs for his own reporting and we received permission to name him and his site in this report. Brian Krebs is a security blogger and reporter who does in-depth research and analysis of cybercrime throughout the world, with a recent emphasis on DDoS. His reporting exposed a stressor site called vDOS and the security firm BackConnect Inc., which made him the target of a series of large DDoS attacks starting September 15, 2016.”
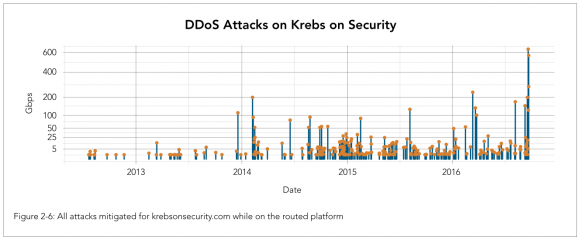
A visual depiction of the increasing size and frequency of DDoS attacks against KrebsOnSecurity.com, between 2012 and 2016. Source: Akamai.
Akamai said so-called “booter” or “stresser” DDoS-for-hire services that sell attacks capable of knocking Web sites offline continue to account for a large portion of the attack traffic in mega attacks. According to Akamai, most of the traffic from those mega attacks in Q3 2016 were thanks to Mirai — the now open-source malware family that was used to coordinate the attack on this site in September and a separate assault against infrastructure provider Dyn in October.
Akamai said the attack on Sept. 20 was launched by just 24,000 systems infected with Mirai, mostly hacked Internet of Things (IoT) devices such as digital video recorders and security cameras.
“The first quarter of 2016 marked a high point in the number of attacks peaking at more than 100 Gbps,” Akamai stated in its report. “This trend was matched in Q3 2016, with another 19 mega attacks. It’s interesting that while the overall number of attacks fell by 8% quarter over quarter, the number of large attacks, as well as the size of the biggest attacks, grew significantly.”
As detailed here in several previous posts, KrebsOnSecurity.com was a pro-bono customer of Akamai, beginning in August 2012 with Prolexic before Akamai acquired them. Akamai mentions this as well in explaining its decision to terminate our pro-bono arrangement. KrebsOnSecurity is now behind Google‘s Project Shield, a free program run by Google to help protect journalists and dissidents from online censorship.
“Almost as soon as the site was on the Prolexic network, it was hit by a trio of attacks based on the Dirt Jumper DDoS tookit,” Akamai wrote of this site. “Those attacks marked the start of hundreds of attacks that were mitigated on the routed platform.”
In total, Akamai found, this site received 269 attacks in the little more than four years it was on the Prolexic/Akamai network.
“During that time, there were a dozen mega attacks peaking at over 100 Gbps,” the company wrote. “The first happened in December 2013, the second in February 2014, and the third in August 2015. In 2016, the size of attacks accelerated dramatically, with four mega attacks happening between March and August, while five attacks occurred in September, ranging from 123 to 623 Gbps. An observant reader can probably correlate clumps of attacks to specific stories covered by Krebs. Reporting on the dark side of cybersecurity draws attention from people and organizations who are not afraid of using DDoS attacks to silence their detractors.”
In case any trenchant observant readers wish to attempt that, I’ve published a spreadsheet here (in .CSV format) which lists the date, duration, size and type of attack used in DDoS campaigns against KrebsOnSecurity.com over the past four years. Although 269 attacks over four years works out to an average of just one attack roughly every five days, both the frequency and intensity of these attacks have increased substantially over the past four years as illustrated by the graphic above.
“The magnitude of the attacks seen during the final week were significantly larger than the majority of attacks Akamai sees on a regular basis,” Akamai reports. “In fact, while the attack on September 20 was the largest attack ever mitigated by Akamai, the attack on September 22 would have qualified for the record at any other time, peaking at 555 Gbps.”
Akamai found that the 3rd quarter of 2016 marks a full year with China as the top source country for DDoS attacks, with just under 30 percent of attack traffic in Q3 2016. The company notes that this metric doesn’t count UDP-based attacks – such as amplification and reflection attacks — due to the ease with which the sources of the attacks can be spoofed and could create significant distortion of the data.
“More importantly, the proportion of traffic from China has been reduced by 56%, which had a significant effect on the overall attack count and led to the 8% drop in attacks seen this quarter,” Akamai reported. The U.S., U.K., France, and Brazil round out the remaining top five source countries.”
A copy of Akamai’s Q3 2016 State of the Internet report is available here.




good read
Why do you try to get 1st comment in every Krebs post with this stupid name ?
I’m pretty sure you have bot drop a post for you and then come in and reply manually sometimes.
So, why respond to a bot?
Seems like the site was being DDOS’d this morning — verified with third-party sites that it was indeed down at times.
It wasn’t an outage caused by DDoS. It was caused by a trial period that expired.
This is the realest of IT woes. 🙂
What’s the matter Brian, didn’t you pay your DDoS protection bill?
something going on
503 Service Temporarily Unavailable
shield
Error: Server Error
The server encountered a temporary error and could not complete your request.
Please try again in 30 seconds.
been like this since around (my time) noon est 11-21-2016
His reporting exposed a stressor site called vDOS and the security firm BackConnect Inc., which made him the target of a series of large DDoS attacks starting September 15, 2016.”
What’s the connection with BackConnect Inc.? I see they are a company that specializes in DDoS mitigation and IT Security services.
Thanks!
See:
https://krebsonsecurity.com/2016/09/ddos-mitigation-firm-has-history-of-hijacks/
and
https://krebsonsecurity.com/2016/09/alleged-vdos-proprietors-arrested-in-israel/
Brian, it seems this is thorough validation that your research and online posts are clearly revealing the secret identities of some nefarious miscreants who would very much prefer to remain hidden, and who have (somewhat petulantly?) retaliated with increasing DDoS ‘force’ in a so-far unsuccessful attempt to shut you up by shutting your website down. Keep up the great work and blind them with the light of exposure!
It might be time for someone like a “Raymond Reddington” to step forward and help put these miscreants “out of business for good”.
Just sayin….
How much does a DDoS attack cost?
Do you have to pay more for a larger attack?
How much does it cost the stressor company?
It costs them more than money. A lot of these devices will be cut off after an attack. Their like a burner phone, once it triggers the payload there is a chance the device will be cut off from the internet.
It’s an ever changing landscape and on Christmas there will be a chunk of mass added to it.
Is it just me, or is the whole web slowing down because of these ioT devices? Every since Brian’s first story came out about the Miria virus, I’ve had to reload. at least twice, almost any page I go to out there. It is getting worse than dial up at times!! I’ve checked my network and done ISP speed tests and other online test services, and there doesn’t seem to be a problem with my broadband. It is very exasperating!! If I have a malware cause, it must be a corker, because I’ve scanned with everything but Kaspersky’s Rescue Disk 10 so far.
Well, your speed test might work fine…but what about your unsecured router with the IOT virus on it that backs off on heavy traffic? You need truly independent assessment here…starting with a base machine you can trust. Rootkit, anyone?
@Christenson – thanks!
I had my router locked down 10 years ago – and that may be the problem too – having such an old router – but for it to come up all on one day isn’t typical evidence for that. I suppose it could be very possible for through put to degrade in big steps. I hate the prospect of having to buy the kind of junk routers they sell now.
Depending on its age you may be looking at a capacitor issue, which typically is what kills routers these days.
As far as new routers go, I’ve had pretty good luck with ones from ASUS, at least in terms of putting third party firmware on them. There’s no way I’d trust an OEM firmware these days, even Cisco gave in and added cloud-based functions to their home/SOHO models. Marketing must have had a temper tantrum about not being able to put the word “cloud” in their materials.
Roll your own.
http://arstechnica.com/gadgets/2016/04/the-ars-guide-to-building-a-linux-router-from-scratch/
I did this, works great! Will never buy an off the shelf router again.
I had a lot of trouble today as well. Problem seemed to be a long wait time for adserver/analytics servers.
Kept seeing the same”waiting for adschmuck.net or whatever popping up on several sites. Sometimes waited 20 seconds or so for page to finish loading, and allow navigation.
https://addons.mozilla.org/en-us/firefox/addon/ublock-origin/
Holy smokes! That seems to be working so far for Mozilla anyway! Thanx Panix!
Now I guess I’m going to have to go back to using adblockers or whatever works for Chrome and Internet Explorer. Script blocking just hasn’t been a pleasant experience for me – too many sites bomb you with an unending supply of scripts that you constantly have to allow to use the site.
All four of my browsers began this poor performance at the same time, so I never expected this to be a platform wide problem in just one day. I was beginning to think patch Tuesday was the culprit, as that was when I first noticed the problem.
You could also try Brave browser.
Filter out all the ads and other useless junk.
It is interesting how much javascript is being put into every webpage now. Even the simplest things are made twenty times bigger just because of all the ads, javascript, and trackers everyone wants to use. lol….back in the day, the idea was to keep all your webpages lean so as to make them load faster and smoother. We might not be on dialup anymore but I think the world would be better for keeping that philosophy alive.
It’s just you. My Internet experience hasn’t changed at both home and work in years.
Akamai buckled. It’s going to be hard to justify them and their price tag going forwards.
Akamai’s service can handle the load, but it takes man-power and resources to deal with different attack types. They cannot justify this for a non-paying client.
Apparently these script kiddies have never heard of the Streisand Effect
Yes, that’s exactly what I was thinking too. Wouldn’t it have been better for them to just hide under a rock for a while?
If there’s one thing they can’t live without, it’s adoration from their peers. And they can only get that adoration by launching attacks and proving their worth to their peers.
These same individuals are the kind who would let peers talk them into doing heroin, but this way instead of self-destructing and only affecting family and friends, they’re trying to take everyone else down with them too.
I develop and run honeypots. When the Mirai source became public, the gafgyt/lizzard infection attempts went down quickly and was replaced with Mirai. Most skiddies don’t change the source code much, they probably aren’t skilled enough. The username/password list is very weak meaning the target (more or less) unprotected HW only. Recently I’ve seen a few new variants in how they test if the system is legit or a honeypot. With the IP’s collected from honeypots and a system where ISP’s block them, most of these infected devices could be taken off the internet.
The vulnerable IoT devices are all made in China. The largest perpetrator of DDoS attacks from hijacked IoT devices is China. Coincidence? I think not…
Re the watching TV on the phone thing… I’m also a middle aged white man
NJ\r\n\r\nSouth Jersey diner network\r\n\r\nDiana Meccico – import\export business
It would be good to hear about experiences with Google’s project shield.
Your incident with the alleged Mirai Botnet and the subsequent IoT attacks on web infrastructure leave questions over how businesses are storing data and managing third party risks. Big questions are being surfaced as to whether vendors are keeping up with threat actor capabilities and affording their client sufficient protection in the event of an overwhelming incident (and then the knock on effects on the wider community of clients).
Funny – I was just going through some old 2012 IDS reports from my gateway UTM appliance, and Akamai was a top attacker one of those months that year!
I’d be interested in the krebsonsecurity.com attack data post-Google shield move. Seems like that might be taboo, though. I highly doubt the attacks just stopped.
Ohhh look, they gather a new watchlist for NSA…