Several readers have called attention to warnings coming out of Canada about a supposedly new form of card skimming called “shimming” that targets chip-based credit and debit cards. Shimming attacks are not new (KrebsOnSecurity first wrote about them in August 2015), but they are likely to become more common as a greater number of banks in the United States shift to issuing chip-based cards. Here’s a brief primer on shimming attacks, and why they succeed.
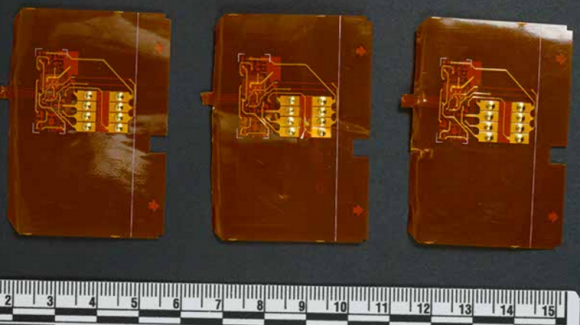
Several shimmers recently found inside Canadian point-of-sale devices. Source: RCMP.
Most skimming devices made to steal credit card data do so by recording the data stored in plain text on the magnetic stripe on the backs of cards. A shimmer, on the other hand, is so named because it acts a shim that sits between the chip on the card and the chip reader in the ATM or point-of-sale device — recording the data on the chip as it is read by the underlying machine.
Data collected by shimmers cannot be used to fabricate a chip-based card, but it could be used to clone a magnetic stripe card. Although the data that is typically stored on a card’s magnetic stripe is replicated inside the chip on chip-enabled cards, the chip contains an additional security components not found on a magnetic stripe.
One of those is a component known as an integrated circuit card verification value or “iCVV” for short — also known as a “dynamic CVV.” The iCVV differs from the card verification value (CVV) stored on the physical magnetic stripe, and protects against the copying of magnetic-stripe data from the chip and using that data to create counterfeit magnetic stripe cards.
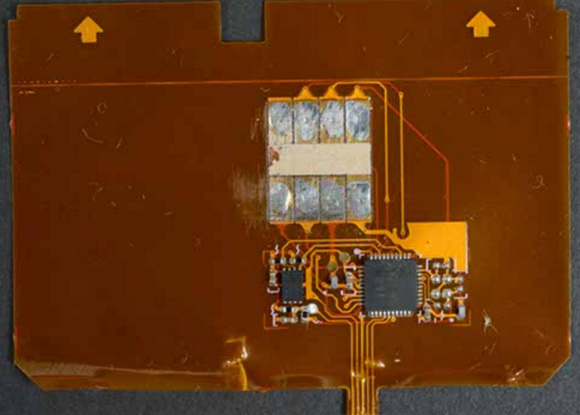
A close-up of a shimmer found inside a point-of-sale device in Canada. Source: RCMP.
The reason shimmers exist at all is that some banks have apparently not correctly implemented the chip card standard, known as EMV (short for Europay, Mastercard and Visa).
“The only way for this attack to be successful is if a [bank card] issuer neglects to check the CVV when authorizing a transaction,” ATM giant NCR Corp. wrote in a 2016 alert to customers. “All issuers MUST make these basic checks to prevent this category of fraud. Card Shimming is not a vulnerability with a chip card, nor with an ATM, and therefore it is not necessary to add protection mechanisms against this form of attack to the ATM.”
Here’s a look at the shimmer I wrote about back in August 2015, which was discovered inside an ATM in Mexico.
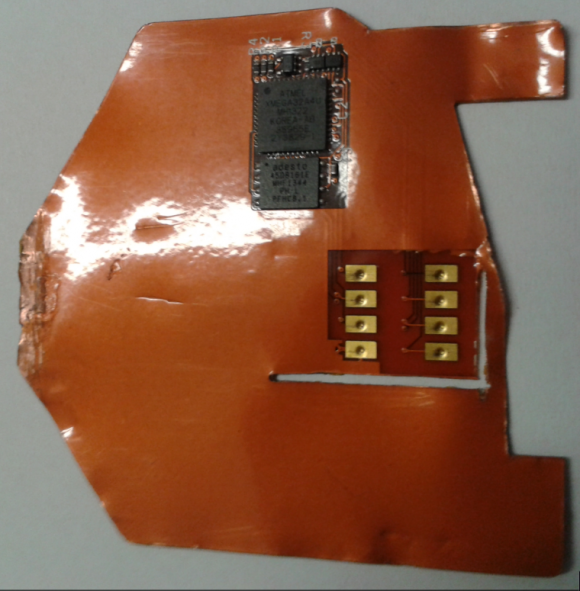
This card ‘shimming’ device is made to read chip-enabled cards and can be inserted directly into the ATM’s card acceptance slot.
This shimming device was removed from an ATM in Europe in 2015:
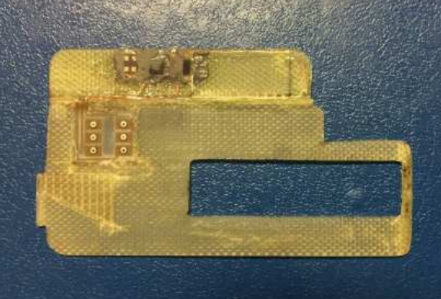
An ATM shimmer. Source: European ATM Security Team (EAST).
Once you understand how stealthy these ATM fraud devices are, it’s difficult to use a cash machine without wondering whether the thing is already hacked. The truth is most of us probably have a better chance of getting physically mugged after withdrawing cash than encountering a skimmer in real life. However, here are a few steps we can all take to minimize the success of skimmer gangs.
-Cover the PIN pad while you enter your PIN.
-Keep your wits about you when you’re at the ATM, and avoid dodgy-looking and standalone cash machines in low-lit areas, if possible.
-Stick to ATMs that are physically installed in a bank. Stand-alone ATMs are usually easier for thieves to hack into.
-Be especially vigilant when withdrawing cash on the weekends; thieves tend to install skimming devices on a weekend — when they know the bank won’t be open again for more than 24 hours.
-Keep a close eye on your bank statements, and dispute any unauthorized charges or withdrawals immediately.
If you liked this piece and want to learn more about skimming devices, check out my series All About Skimmers.




How do you “check the CVV when authorizing a transaction?”
You don’t. The card issuer does for each transaction.
I read that “dynamic CVV” is a firmware counter that increases each time the card is used, and verifies that the actual card is not being misused for fraudulent purposes based on the value of the number at the time of psychical use. If the number is wrong on the next purchase then the card is declined due the stored value not being the same as the value at the bank server
Any truth to this?
It’s more complex than that. More like authenticator tokens that change values in set time increments. Only the issuer/verifier know what the values should be and they expire. So by the time someone tries to use a stolen value it’s invalid.
No, that is not correct, and the article contains a slight error too.
Chip cards have 3 different security codes (sometimes called CVVs or CVCs). There is one printed on the back of the card (that you use when shopping online or on the phone). There is one in the magnetic stripe. The third one is in the chip. All three are different, and static (unchanging). Dynamic security codes refers to a relatively new technology – a small screen on the back of the card shows a security code that changes periodically (e.g. every hour). These types of cards are not widely used (expensive to produce). The chip also includes a transaction counter that issuers can check to prevent duplicate transactions from being submitted.
You are incorrect. I looked it up and dynamic CVV refers to any kind of dynamically generated CVV, be it dynamically printed in e-ink on the back of the card, or dynamically generated by the chip. The point of the e-ink version is for card-not-present usage (eg over the phone).
The standard supports a dynamic CVV and an incremental transaction counter, either/both of which prevent chip card duplication – especially as transaction data is bundled into a cryptogram using the (unreadable) private encryption key stored on the card. At least, they do if the card switch has implemented them and is checking that they are valid for each transaction (poor implementation here could enable replay attacks for example).
The vulnerability discussed in the article is using the static data on the chip to create working Track I/Track II data for a mag-stripe card. As a card issuer, depending on the payment networks encountered by your cardholder base*, it’s easy enough to counter this vulnerability by declining mag-stripe transactions at chip-enabled terminals (forces the cardholder to use the chip when available – which a counterfeiter won’t be able to do).
* Low-quality payment networks result in chip transactions being sent through in ‘mag-stripe mode’ because the data is smaller, which may result in false-positives.
This is all relevant to card-present transactions only – card-not-present is much lower tech and doesn’t benefit from chips in any way. The e-ink CVVs are a great countermeasure though.
Technically, the CVV2/CVC should not be stored on the mag-stripe. It gets passed to the issuer by manual entry and cannot be retained by the merchant in any way. This is why we always have to re-enter it, even if we have the “card information saved for future use” with our billing programs, etc.
Sorry, but I don’t follow.
“Data collected by shimmers cannot be used to fabricate a chip-based card, but it could be used to clone a magnetic stripe card.” But if you’re cloning a magnetic stripe card, isn’t all you need what’s on the magnetic stripe?
Also, when it says that banks aren’t correctly implementing the chip card protocol – are the chips on the cards they issue faulty, or is the ATM software that reads the cards faulty? If it’s the chips that’s wrong, if you have such a card, you’d presumably be at risk everywhere. If the ATM software is wrong, everyone using such an ATM would potentially be at risk. Either way, it would be interesting to know which banks are the problem.
Answers are in the article, if you read all of it and then consider it all as a whole. But, I think what was meant is that shimmers are unable to replicate the code that generates a new unique dynamic CVV. I’m just guessing, but I would expect each card to have a unique encryption key which the bank kept on file from the cards original manufacture. Then possibly some form of random number generator on the banks server sends a unique seed value back to the card, both the bank software & cards software will then generate a new value using the encryption key which is never transmitted. The bank will know what the iCVV will be the next time it is sent from the card. And apparently, some banks do not want to deal with the complications of making use of such a scheme. So perhaps there ought to be a federal credit ranking applied towards such under-performing banks?
Fortunately the penalty and incentive are built into the system. Underperforming banks stand to lose more money from fraudulent transactions against their system. They choose to weigh that cost against the convenience of not having all of the security features implemented. Same goes for vendors. Those who do not adopt the most robust security measures pay more for their transactions. Those who choose to handle payment card data know this going in.
When you swipe a magstripe, the entire strip runs through a reader. When you insert a chip, at most a portion of the magnetic strip is accessible, not enough to clone the information stored on the strip.
This should be enough to prevent someone interacting with a chip transaction from impersonating a magstripe. The only information that a magstripe encodes that isn’t available for trip transactions is a CVV. But, if an issuer is dumb enough not to validate the CVV from a magstripe transaction, then the information available from a Chip transaction would be enough to trick the issuer into accepting the transaction.
Imagine that you and I agree on a system for logging in, I give my name, you ask me for my password, and then you let me in. Imagine if it turns out that no matter what password is given, you allow me to log in. That’s what some credit card issuers apparently did. It certainly simplifies the logic. It also means that if I ever go somewhere else and am asked for my name, but not my password, anyone listening to that transaction can impersonate me.
This isn’t a bug in the specification, it’s a bug in the implementations. Thus, there’s nothing to fix from the specification side.
If your issuer turns out to be this stupid, please vote with your wallet and replace it.
Reallly? Cmon..carding is dead why people wastong still time for doing skimming dumps cc cashouts bla bla?? Its waste of money no profit i dont see point of doing this. There is nowdays allready alot more easier ways to earn alot more money. Who will waste time for this bs ??? I guess kids who so desperately need some money. Cmon.. guys stop this bbs
Perhaps you are not doing carding correctly…?
And would love to hear about the “alot more easier ways to earn alot more money”.
*work* is the first thing that comes to mind…
I use to work for a guy who spent so much time trying to figure out ways to beat the system. If he spent half that time actually doing honest work he would have been ahead of the game.
I don’t understand the talent that can make this stuff could be making other legitimate things for honest money.
Boredom. Drudgery. Sometimes the less optimal path is better for your health and spirit. Suppose you had two options:
$80k/yr job: Boring, miserable, toxic work environment. Strict work hours in a tiny cube.
$50k/yr “job”: Fun and exciting self-employment that provides new and unique challenges on a frequent basis. Set your own hours; travel wherever you want.
Except for one pesky, little detail, this and all other credit card fraud is ILLEGAL. Wonder what the stress level of always looking over your shoulder adds to the equation.
You say that but people that skim and produce fake cards walk away with a lot of money. More than most make in a day sometimes depending on how long they can do it before the victim or bank realizes it’s happening.
(This is US-centric, though would be nicr for knowledgeable folks from other markets to chime in).
Sadly, the cock-up isn’t surprising, considering the prevaling notion by the banks of what constitutes 2FA (secret questions, I am looking at YOU). Add to that the widespread lack of transaction authentication (rather than the person) and it is… Yeah.
This article relates to Canada, and not specifically the US.
Unlike the US, Canada went chip-and-PIN nearly ten years ago and the system functions in the same way as the European equivalent.
Therefore if these shimmers sucessfully work in the Canadian environment there is a high probability they will work in the majority of jurisdictions that employ chip-and-PIN.
WRT the last sentence, they might work to target ignorant card issuers (banks) ONLY, so the presence of shimmers in Canada is -I guess- aimed to US cardholders/issuers
‘are the chips on the cards they issue faulty’
Actually, a new card that I received from my bank with a chip was actually faulty (had a bad chip). After several calls to the bank, they finally said they would have to reissue the card.
I also manage the credit cards at our company and someone there had the same issue I did. We had to have the card reissued by the bank (bad chip).
My understanding of the story was that these shims were inserted in handheld terminals. Rather than ATMs
http://www.cbc.ca/news/canada/british-columbia/shimmers-criminal-chip-card-reader-fraud-1.3953438
According to the articles the operators were doing a daily test – so a case of good hygiene. However swapping terminals is pretty rife on the left coast so I expect shimming to have a good run.
One article referenced the images that you use in: https://krebsonsecurity.com/2016/06/how-to-spot-ingenico-self-checkout-skimmers/ as a spotters guide
I think with chipping cards its still improving the security of physical transactions. If your gaining access to information off a chip you still cannot reproduce a chip card. You can only make a non chip card. For now this is a potential risk as vendors still take non chip cards. Especially with many small vendors I’ve experienced who are slow to adopt the new machines required to accept chip cards. It’s going to take some time to switch to a all chip card acceptance only system. That still leaves unanswered what to do about online transactions which the chip card does not address.
I’m not sure if they can enforce chipped card readers thru online transactions so there is always the idea of stealing the card via a chip read then re-creating the non-chipped card to use online.
Apologies had 4 wisdom teeth removed and I’m a bit hazy must have read over that last bit!
This is one of the reason why Apple Pay and Android Pay is implementing web based transaction authentication that can protect the transaction between the online retailers and the customers. These companies need to step up the process to include it in their website.
Most online transactions require the CVV2 from the back of the card, which isn’t available from a chip read (or mag stripe for that matter).
Kindly suppose/alert against such crimes
Thank you
Its waste of time and waste of talent.
Carders are tricked into this. This is just so much efforts they use it to get little money. This is only profit for banks and goverment.
So the siciety can go even in deeper poverty and debt. And more survailence over people. So thos is only good for bankers. Thats it. Everybody else is just loosers here
Explain to me exactly how banks make money from skimming/shimming.
Ever wonder why the chip card you just got didnt work at the new reader on the gas pump? And you had to go in for another read? Ccv number jump? But, don’t worry, it will get worse. Those kiddies just haven’t figured it out yet here. But the security firms will help undo their delima by gradually weakening the algorithm. After all, we have to pay for the Russian hackers.
Actually, no.
I’ve never had a chip card rejected at the pump. On the other hand, all those readers seem to have been swipe readers.
The gas pumps aren’t required to change over to chip readers until next year, October 2018, i believe.
I inquired with my local Marathon, Sheetz and BP gas station operators (owners, not cashiers) and they said they would not be converting to chip readers at the pump until well after 2019. Cited costs, pump upgrades, no capital budgeting, etc. When I asked about the date requirement to implement chip conversion, the Marathon operator said that had been dropped and there is nothing current to force them change over for several years. Don’t know if he was making it up, but currently all their card readers say display NO CHIP signs.
Might this be a point of difference for consumers to consider when choosing with whom to do their banking?
“Do you, as a financial institution, fully implement the EMV specifications for both card present and not present transactions, including verification of the printed, on-stripe and generated via-chip CVV values?”
Perhaps there’d be value in a list of which banks do and don’t… and so focus attention on those banks not up to scratch.
Sadly, specifications are long, and no person will really know the answer. Basically we’d need a service where users can present their card, and it tries various invalid transactions and sees if they’re accepted. But issuers would accuse that vendor of being a hacker and sue and ban it pretty quickly.
Your best bet is getting Consumer Reports to do this investigation. They have the clout.
Other pointless article
World not changing lambs will continue 8-5 lifestyle.
People who really cates never come here and read.
Even then they not even undestood.
Nothing constructive here at all bs
aout >> /dev/null
Brian,
Some banks are implementing the NFC for the ATM machine because of this process. The problem is that most can’t afford to replace it until the end of life cycle. As a matter of fact, I had to dump a local bank because they have not upgraded the mag stripe card to the chip card and not being supported by Android Pay.
using a card for payment is barbaric.
tokenisation via *Pay is where security is at.
I notice that my local (Maryland) Citibank in-bank ATM is now chip-enabled
Duplicate file are really disturbing. Just use “DuplicateFilesDeleter program”
I am a computer science student at a G8 university in Australia. Over the past few years, i noticed many students,housewives, old people, working adults,all who seem look chinese tailing me in person around. They seem to have a massive grid network of spies who can tail seamlessly. But cars with the same plate no. keep reappearing at different dates and locations, a few months apart; Chinese people sitting near me on flights to and fro Australia magically reappear in some other location and date. And there are some indirect circumstantial evidence to me that my house has been bugged,both in sound and spycams but i resisted looking for them, acting as ignorant as possible. Today i finally went to the AFP police station at an airport and reported informally to them. Although i am uncertain whether the reappearances are just coincidental, i stress that i am neither paranoid nor have mental problems, i have a fairly good visual memory and i was in Mensa. I just want to warn all IT people to be careful of your computer and your own physical security. I suspect state-trained chinese spies are working with state hackers to track peole in critical job fields. I don’t have proof but am saying this for my own safety since they know now that i know. And i want to warn as many people as possible.I will strive to stay alive to tell u the details, but IT people have to take their HUMAN physical security seriously. Humans ARE the weak link in IT security.
You can also use a shim on a legitimate card to make purchases without using a correct pin code.
Incredibly detailed post on use of shimmers to dynamic skimmers. Rarely surprised about the content on Krebs or the intelligence of the people responding. Keep up the good work!
we all know that this was going to happen. credit cards are never safe
Since 2015, unofficially I’ve just kept a finger on the Chip Conversion Pulse is my region. Just the major retailers, gas stations, etc. To date my rough estimate is that out of 300 major (well known or national) establishments … about 94% still do not have chip nor accept chip. Obvious by the stickers plastered all over saying No Chip. Especially “franchised” merchants which claim it’s too expensive for them to convert (either because they have to upgrade gas pumps, get new integrated cash registers, their processor wants a Chip Surcharge added to transactions, etc.) Surprisingly … most are not even willing to do Apple Pay, Android Pay, etc. because it doesn’t fit with their business model. Some of the smaller retailers said they may have to stop accepting credit all together. Pizza places, mom and pops shops, small eateries. They stated the fees for accepting credit cards are just eating them alive. Not saying it’s happening everywhere, but chip isn’t being embraced here quickly at all. Mag Strips are going to be around a lot longer than most think. Of course, a lot of these place don’t take Dollar Coins either … so it goes …
They fees ARE eating them alive, especially for low margin businesses, and the cost is going up. The fee structure favors larger businesses over smaller, and the smaller operators are considered higher risk. However, the failure to accept credit cards severely limits the customer base, as we’ve been so indoctrinated to accept the use of credit cards everywhere. Most of us no longer carry cash.
I’ve talked to merchants who say that getting a chip reader POS terminal is going to cost thousands of dollars. Most smaller places I go to just recently changed over or haven’t yet. Most larger places, like Target or Walmart have already. But at a cost of 2.9% + 9 cents per transaction, that can significantly decrease profits for a small margin business…
So as an old electronics technician, a couple of those shimmers look mass produced (second and third pictures) as opposed to what looks like a home-made one (fourth picture). SMT isn’t easy to work with by hand, especially on flex circuits, as can be seen with the forth picture.
So who’s mass producing shimmers, or are they being adapted from circuitry that serves other purposes?
How come these skimmers are effective?
These skimmers steal data from te chip of the card, a hacker could clone the card using the information on the chip but he would need the PIN of the card to actually cash out the money.
I’m guessing they would hide a camera somewhere around the ATM and recor PINs like that.
My favorite explanation of chip transactions and how they work can be found searching AID EMV ATM. Or Youtube / tpH0iwND6v8. There are physical protections that can be installed against shimming, but they are not as common as they should be. Search CPP TMD. The ATM industry sure does love 3 letter acronyms.