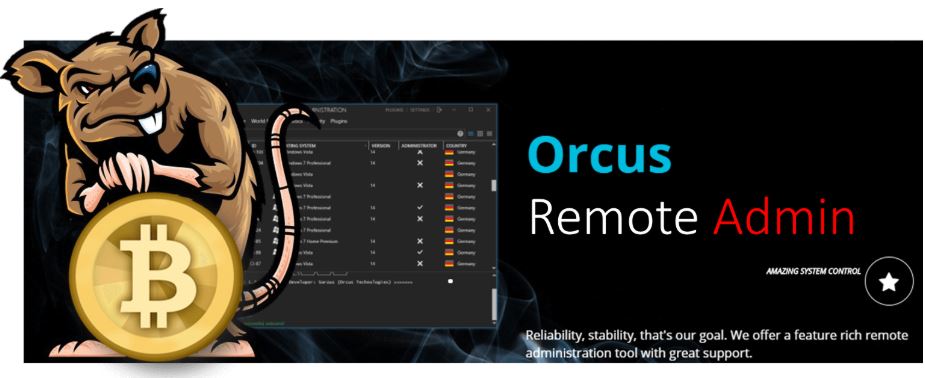
Canadian police last week raided the residence of a Toronto software developer behind “Orcus RAT,” a product that’s been marketed on underground forums and used in countless malware attacks since its creation in 2015. Its author maintains Orcus is a legitimate Remote Administration Tool that is merely being abused, but security experts say it includes multiple features more typically seen in malware known as a Remote Access Trojan.
As first detailed by KrebsOnSecurity in July 2016, Orcus is the brainchild of John “Armada” Revesz, a Toronto resident who until recently maintained and sold the RAT under the company name Orcus Technologies.
In an “official press release” posted to pastebin.com on Mar. 31, 2019, Revesz said his company recently was the subject of an international search warrant executed jointly by the Royal Canadian Mounted Police (RCMP) and the Canadian Radio-television and Telecommunications Commission (CRTC).
“In this process authorities seized numerous backup hard drives [containing] a large portion of Orcus Technologies business, and practices,” Revesz wrote. “Data inclusive on these drives include but are not limited to: User information inclusive of user names, real names, financial transactions, and further. The arrests and searches expand to an international investigation at this point, including countries as America, Germany, Australia, Canada and potentially more.”
Reached via email, Revesz declined to say whether he was arrested in connection with the search warrant, a copy of which he shared with KrebsOnSecurity. In response to an inquiry from this office, the RCMP stopped short of naming names, but said “we can confirm that our National Division Cybercrime Investigative Team did execute a search warrant at a Toronto location last week.”
The RCMP said the raid was part of an international coordinated effort with the Federal Bureau of Investigation and the Australian Federal Police, as part of “a series of ongoing, parallel investigations into Remote Access Trojan (RAT) technology. This type of malicious software (malware) enables remote access to Canadian computers, without their users’ consent and can lead to the subsequent installation of other malware and theft of personal information.”
“The CRTC executed a warrant under Canada’s Anti-Spam Legislation (CASL) and the RCMP National Division executed a search warrant under the Criminal Code respectively,” reads a statement published last week by the Canadian government. “Tips from international private cyber security firms triggered the investigation.”
Revesz maintains his software was designed for legitimate use only and for system administrators seeking more powerful, full-featured ways to remotely manage multiple PCs around the globe. He’s also said he’s not responsible for how licensed customers use his products, and that he actively kills software licenses for customers found to be using it for online fraud.
Yet the list of features and plugins advertised for this RAT includes functionality that goes significantly beyond what one might see in a traditional remote administration tool, such as DDoS-for-hire capabilities, and the ability to disable the light indicator on webcams so as not to alert the target that the RAT is active.
“It can also implement a watchdog that restarts the server component or even trigger a Blue Screen of Death (BSOD) if the someone tries to kill its process,” wrote researchers at security firm Fortinet in a Dec. 2017 analysis of the RAT. “This makes it harder for targets to remove it from their systems. These are, of course, on top of the obviously ominous features such as password retrieval and key logging that are normally seen in Remote Access Trojans.”
As KrebsOnSecurity noted in 2016, in conjunction with his RAT Revesz also sold and marketed a bulletproof “dynamic DNS service” that promised not to keep any records of customer activity.
Revesz appears to have a flair for the dramatic, and has periodically emailed this author over the years. Sometimes, the missives were taunting, or vaguely ominous and threatening. Like the time he reached out to say he was hiring a private investigator to find and track me. Still other unbidden communications from Revesz were friendly, even helpful with timely news tips.
According to Revesz himself, he is no stranger to the Canadian legal system. In June 2018, Revesz shared court documents indicating he has been involved in multiple physical assault charges since 2007, including “7 domestic disputes between partners as well as incidents with his parents.”
“I am not your A-typical computer geek, Brian,” he wrote in a 2018 email. “I tend to have a violent nature, and have both Martial arts and Military training. So, I suppose it is really good that I took your article with a grain of salt instead of actually really getting upset.”
The sale and marketing of remote administration tools is not illegal in the United States, and indeed there are plenty of such tools sold by legitimate companies to help computer experts remotely administer computers.
However, these tools tend to be viewed by prosecutors as malware and spyware when their proprietors advertise them as hacking devices and provide customer support aimed at helping buyers deploy the RATs stealthily and evade detection by anti-malware programs.
Last year, a 21-year-old Kentucky man pleaded guilty to authoring and distributing a popular hacking tool called “LuminosityLink,” which experts say was used by thousands of customers to gain access to tens of thousands of computers across 78 countries worldwide.
Also in 2018, 27-year-old Arkansas resident Taylor Huddleston was sentenced to three years in jail for making and selling the “NanoCore RAT,” which was being used to spy on webcams and steal passwords from systems running the software.
In many previous law enforcement investigations targeting RAT developers and sellers, investigators also have targeted customers of these products. In 2014, the U.S. Justice Department announced a series of actions against more than 100 people accused of purchasing and using “Blackshades,” a cheap and powerful RAT that the U.S. government said was used to infect more than a half million computers worldwide.
Earlier this year, Revesz posted on Twitter that he was making the source code for Orcus RAT publicly available, and focusing his attention on developing a new and improved RAT product.
Meanwhile on Hackforums[.]net — the forum where Orcus was principally advertised and sold — members and customers expressed concern that authorities would soon be visiting Orcus RAT customers, posts that were deleted almost as quickly by the Hackforums administrator.
As if in acknowledgement of that concern, in the Pastebin press release published this week Revesz warned people away from using Orcus RAT, and added some choice advice for others who would follow his path.
“Orcus is no longer to be considered safe or secure solution to Remote Administrative needs,” he wrote, pointing to a screenshot of a court order he says came from one of the police investigators, which requires him to abstain from accessing Hackforums or Orcus-related sites. “Please move away from this software without delay. It has been a pleasure getting to know everyone in my time online, and I hope you all can take my words as a life lesson. Stay safe, don’t do stupid shit.”





What still makes we wonder is why we have not seen hardware manufacturers finally putting an end to abuse of webcams and made sure, hardware-wise, that such cameras cannot be active without their indicators, well, indicating that they are.
I guess I am missing something important here. Can somebody please point me to it?
It seems so obvious that the power going to the webcam should be the same power source that lights the LED indicator – so that it’s electrically impossible for the webcam to be on without the LED also being on. Instead, manufacturers control the LED indicator with firmware, which, as we have seen, can be disabled maliciously. No one is holding device manufacturers responsible for user privacy.
There is one problem with that idea…the fact that doing it that way would require the LED and the camera to have identical power requirements, which they do not. (Not even close, looking at options for cameras at DigiKey…)
So, as a result, they need separate (and different) power feeds, each of which requires their own control. Sure, you could use a relay…a solid-state relay would be the smallest option. But it would still require your laptop lid to be nearly half an inch thick to accommodate it. And thus that power switching control ends up being done via software because, well, people like thin laptops, not thick ones.
You wouldn’t need a SSR. Just one mosfet doing low side switching for the LED, or a BJT and a resistor in series with the base.
Look for my post on Steve Gibson’s podcast.
All you need is a physical switch for both the mic and camera. Switch it off, and neither the mic and camera are capable of being turned on. Thats it, thats all. It can be done with a pretty small switch with 2 separate power cables for each device.
Physical switches cost money. The device manufacturer has to test them with some sort of physical device to move the switch, or a person.
A shutter on the camera might be cheaper.
I use a USB webcam plugged into a USB hub with buttons to turn on/off individual ports.
—
originally, most webcams did have the camera and LED on the same physical circuit so that power to camera sensor would illuminate the LED. I dont know what the market looks like today.
—
re: extra circuitry for led. — are you daft? you just need a resistor.
LED forward voltage is 1.8 volts for red, USB bus power is 5 volts. Indicator LEDs are normally pretty low power – 2 mW is typically fine — its an indicator not a flashlight.
The wizard recommends a 1/8W or greater 1800 ohm resistor. The color code for 1800 ohms is brown grey red. –
thats 2 mW for led, and 6.4 mW for the power across the resistor at 3.2 volts = 8.4 mW total.
—
why wouldnt you do that? what if you had a microcontroller on the board with an extra GPIO pin unused? its already on the board but another resistor increase the part count. what the cost of adding 1 part per every board, or re-writing the firmware to google with mcu and redesigning the PCB for an extra trace.
just my nickel on it.
that last line should be ‘toggle’ the led not ‘google’ the led (?!)
I can somewhat explain this. The camera needs firmware. To keep things cheap, there is no programmable memory in the camera to hold the firmware. Rather the OS driver is what uploads the firmware. So the hacker changes the driver in a manner to allow the rat to not turn on the light.
The “why” is only something I can guess. I suppose one reason is to save the couple of milliamps it takes to drive the LED. Not an issue in a notebook, but the camera module could be used in other applications.
This was discussed on TWIT’s “security now”. I ran a few searches using site:grc.com since Steve Gibson has show transcripts, but I can’t find the episode where this was discussed. Doing a search on RAT itself was a shocker since the website turns out to have medical research on it!
Guess you mean this?
https://www.grc.com/sn/sn-437-notes.pdf
Close and much thanks. Those are the show notes. This is a transcript of the podcast.
https://www.grc.com/sn/sn-437.htm
My recollection was reasonably good. What is missed is they leave the camera in standby. I don’t follow why that is done other than I assume to get the camera working as fast as possible.
So the camera is in standby with the LED off. But standby probably means don’t put the data on the USB bus. The hacker has other ideas.
At one time Apple used the camera to determine ambient light, which in turn would be used to adjust the display backlight. That would be a case where you surely needed the camera operating but bit really on. All modern notebooks have a simple light sensor, totally independent of the camera.
Gary, a question.
I do not use the laptop’s built in camera, but an accessory one connected via USB to the machine. If I Skype and the accessory one is not plugged in I do not get a picture (i.e. the machine does not shift to the built in camera).
Can I assume that no one from the outside can utilize the built in one?
Nope.
Skype has a Video Options menu. Select it, then Source. You may see that two or more camera sources are available, for example, built in and plugged in.
Let’s say you selected the plugged in camera, then unplugged it. Skype won’t try the built in camera until you select it. That’s why it appears that no picture is present.
But Skype’s selective blindness doesn’t mean the built in camera is off or inaccessible to other programs, including a remote access tool (RAT) or any other spyware.
Your best defense against unwanted surveillance is to put a bit of black electrical tape over the built in camera and avoid talking in the presence of the built in microphone. The second best defense is to keep your laptop’s operating system up to date, to avoid spyware altogether.
While I have disabled my camera and mic in the hardware profile, I assume someone could still access such hardware info and turn them on. Since I never use either of them, I permanently removed them via a soldering iron while I was under the PC’s hood doing other things.
Never met a piece of malware that could use a screwdriver and soldering iron to get inside my reconnect the cam and mic, that includes the Gov’t. A switch could be installed to control both items (turn them on/off) if I ever felt they could served a purpose for me, hackers can’t get around that either.
I guess most people think these items are really necessary so my approach won’t work for most people.
This reminds me of those Blackberry phones where the camera wasn’t installed so you could use them on some government facilities. Obama’s iPad had the camera and microphone removed.
There is nothing as effective as physically stopping the problem. As an aside, notebooks used to have a real power off switch. I don’t think such beasts exist anymore. So your notebook is really never off.
Well it is IF you unplug it and remove the battery then hold the power button a few seconds to drain off residual power. But I use mine more like a desk top. It has HDMI so my TV is the monitor and the lid is always closed so camera is seeing nothing mic is disabled if it even works at all as old as it is. I do have a USB cam that is permanently pointed at a picture of Trump and Kim Jong Un smiling and shaking hands. Serves any hackers right if they see that.
In the previous RAT cases, I recall that the authorities had evidence of the RAT authors actively involved in helping customers deploy and use the RAT for illegal purposes.
I don’t think we’ve seem a prosecution based only on the RAT features that facilitate illegal activity. That would be a hard case to prosecute.
Right. Hence, this part from the story:
“However, these tools tend to be viewed by prosecutors as malware and spyware when their proprietors advertise them as hacking devices and provide customer support aimed at helping buyers deploy the RATs stealthily and evade detection by anti-malware programs.”
“tend to be viewed by prosecutors”
… but such views are not the law. The production & distribution of dual-use things is almost always protected by law.
I agree, this is not how the law works.
I guess this explains why it took them this long to arrest the author…
I was under the impression that he would’ve been arrested back in ’15/16 when the evidence of its nefarious use was discovered…
Just my thoughts…
“but such views are not the law”?
“not how the way the law works”?
Is your legal adviser a Hollywood movie?
What makes you think that Rezvesz only has 1-2 “criminal computer activity” charges to worry about now?
His inconvenience started the moment the magistrate signed the search warrant.
The entire address is subject to search and confiscation, to be perused at leisure by police. If other crimes are also discovered, or subsequently discovered, more warrants will flow. It will be charge pile-on time.
And best, Mr. Resvesz has no idea what other evidence the police of at least 3 nations have on him.
Mr. Rezvesz could help all those fighting daily malware, by lying to police, now or during future interviews, on any subject.
Messrs. Michael Flynn and Michael Cohen can now write short true stories about doing that.
We’ll learn how “tough” Mr. Rezvesz really is.
If he knows he’s committed certain crimes, which he would have to assuming he did in fact commit crimes, then he knows exactly what evidence they could have on him. Evidence of potentially every single crime he committed.
I own firearms. Firearms I use for hunting, target competitions, self-defense, and to revolt against tyranny as is my constitutional right in the USA. I’ll bet Venezuelans regret giving theirs up now, in fact, they have said so. Firearms can also be used in violent crime. Should I be searched then? My firearms confiscated for pre-crime? Some “authorities” might think so. How about firearms manufacturers? Should they all be investigated? Are we all guilty until proven innocent?
Don’t mistake me: this guy sounds like a bad actor, but a line may have been crossed by the authorities as well.
As far as we know, he is being afforded his legal rights. A magistrate had to issue the search warrant, the police had to attest to the veracity of the probable cause in the warrant application, and a prosecuting attorney has been assigned to manage the case (US law; YMMV). All of these individuals are members of the court and are subject to severe sanction if they are found to have either perjured themselves, or acted in a manner that violates the suspect’s rights. What are you assuming their motivation is for acting in this case?
As far as we know, the suspect (don’t know if he has been arrested yet) has probably been given some kind of warning against self-incrimination (testimony provided in the course of the investigation can be used as evidence at trial), and he will be provided a bail hearing (arraignment), and allowed to post bail unless he is a flight risk if he is eventually arrested and charged.
Based on what we know now, which isn’t much, all of his legal rights seem to be protected by US/UK Commonwealth legal procedure. Some variation in these processes may apply do to where the investigation has originated, but at this point he is 1) not under arrest, 2) not subject to arbitrary detention, and 3) has his habeas corpus rights intact.
Not sure where your concern that his rights being violated arises from. I’m not in a position to speculate about your motives, so perhaps you can enlighten us at to why you think he may be subject to some irregular/inappropriate/illegal action on behalf of the authorities.
Strange features are probably hard to prove alone, but probably do enhance a prosecutor’s argument, particularly for the features that serve no purpose except for malice.
The one that hugely stands out to me from the linked list is the “let it burn” feature, which literally has no purpose except to mess with the desktop of the affected user. There’s no legitimate remote administrative tool with this sort of feature.
Similar can be said with “password recovery from famous applications” – this would fall afoul of any IT best practices about security (or even mediocre IT practices about security), and would never be included in any legitimate remote administrative tool.
Password recovery is common on remote admin tools. Hirens boot CD has had it for ages. It is useful for unlocking a local admin account on a machine that has lost connection to its domain, and becomes necessary when an admin inherits a domain that is not properly documented.
Well, I’ll start by saying rescue CDs are different than RATs. 🙂
From what I know, OS manufacturers tend to frown on these “password recovery” tools in these rescue CDs (I know some admins use them, but some are “gray hat” in nature). The official Microsoft approach for instance is to create a password reset disk which, if you forget your password, you can use to reset it. Discussion of resetting local passwords is limited on many support forums (eg BleepingComputer) due to the difficulty of determine whether the requester of this support is the legitimate owner.
Many remote administration tools do have the ability to manage local administrative accounts or domain accounts (including passwords). But we are talking about passwords stored in applications like browsers here. These are passwords that quite often do not fall under an administrator’s domain. Why would an admin need to remotely look at potentially sensitive user data that does not necessarily fall under their scope? They don’t need to. Hackers on the other hand would love potentially sensitive login information.
“. “I tend to have a violent nature, and have both Martial arts and Military training”
His one of those internet tough guy hiding behind a keyboard and mouse, using intimation to manipulate and spread false fear.
I have a feeling Krebs was not at all intimidated by this joker.
Threatening someone and leaving a paper trail. This guy is not very bright. With an ego that huge, I don’t think he is capable of stealing a pack of gum from the local market without everyone knowing about it.
I had the same reaction. . . He stored his business records and contacts on site. I wonder if he even went to the trouble of encrypting them? I suspect that the RCMP et al. scored a treasure trove of information. Good for them!
Seems like an edgelord on steroids.
His profile pictures and ego come together for one of the more cringeworthy personas I have seen in a while.
Best part is that you know he will read these comments. I’m just left wondering where he is hiding his Katanas and fedoras.
The only time RCMP prosecutes cyber crime is when the FBI phones them and says “let us fill out that warrant application for you.”
They have 200+ people “investigating” cyber crime (depending on what source you believe) and next to zero prosecutions.
I bet those “legitimate users” of his “software” are now s__ting their pants knowing that their “real” names (according to that sleazeball) are in the hands of Canadian police 🙂
Also when will those “legal” malware paddlers learn that you can’t do this from a Western country. You need to do it having a server in Russia or a similar country.
So where is Sorzus in all of this?
I believe he was the developer of the rat.
This guy developed all this and installing Linux was difficult enough to warrant a thread.
I’m aware he developed it but it seems that Armada is only affected so far.
He did nothing wrong. The customers should be responsible for their own actions. Fuck the police.
There’s this thing called “aiding & abetting” that is indeed a crime. Look it up!
The story needs a phonetic guide to the suspect’s name.
And an update if/when there’s an arrest.
Interesting case.
Canadian judges can prohibit an individual from accessing particular websites, before an arrest or conviction or even an evidentiary hearing on the websites’ content?
IANAL and don’t know American/Canadian/Commonwealth law, but there are definitely places where groups are given gag orders.
There is an entire category in IT relating to addressing gag orders, they’re called Warrant canaries [1].
[1] https://en.wikipedia.org/wiki/Warrant_canary
Thanks, timeless. Ianal, either.
Question: does switching off “Allow Remote Connections” in Windows have any effect on one’s vulnerability — or does the malware just switch this setting to True if it isn’t true already?
CHC of Asheville,
Malware/RATs does not care about this setting. Setting it to False will not stop malware. Malware/RATs does not need to set it to True to operate in their full capacity.
They do need to use Windows built remote desktop abilities to operate in a “remote desktop” capacity. As such the aforementioned option will not protect you. However, you should have it set to False regardless (unless you have a legitimate use for it).
Protect your computer by using making sure you have windows defender enabled, ideally with another antivirus or antimalware solution on top of it such as Malwarebytes, ESET, Kaspersky, Bit Defender, etc. Everyone has their opinions on which is best.
Thanks
That’s a very good point and a great thing to know. Thanks Evan!
You’re giving him way too much credit. Sorzus was the real author, not John “Armada” Rezvesz. Armada couldn’t even code.
That’s messed up that he used the bitcoin logo in his ad. For shame.
I couldn’t tell from the article if that was him or Brian.
(And I’m not going to search because…)
Am I the only one who is disturbed by the fact he has had 42 reported complaints to law enforcement, several domestic abuse calls and he has zero criminal record. WTH
Calls to police and arrests are not evidence of crimes.
A person may just live with habitual complainers and deal with corrupt police. Or he self-harms. Or he is rude to cops. Or he is a mean drunk. Or he eats kittens.
Or nothing.
Every person has the right to a presumption of innocence. Including this guy.
Wooohoooo!!! Go FBI!! Thank you for your service!! This cyberwar preying on on innocents and our Government!! Nope, not today. This is the Greatest country on Earth and we will Win!!!
Good day,
My name is Patricia Valladao and I am the manager of media Relations for the CRTC. I would like to thank you for your recent article and provide you some clarification on our role (CRTC) and the requirements under CASL
Investigation into RAT and search warrant
In February 2018, the Canadian Radio-television and Telecommunications Commission (CRTC) initiated an investigation into a Remote Access Trojan (RAT).
By the fall of 2018, and having gathered sufficient evidence on various third parties connected to the RAT, the CRTC solicited, and obtained, the involvement of the Royal Canadian Mounted Police (RCMP), the Australian Federal Police (AFP) and the Federal Bureau of Investigation (FBI).
On March 27, 2019, the CRTC and the Royal Canadian Mounted Police (RCMP) National Division each executed a warrant at a residence located in the Greater Toronto Area. The CRTC and the RCMP are both part of an international coordinated effort with the AFP and the FBI.
The Canadian Radio-television and Telecommunications Commission (CRTC)
The CRTC is an administrative tribunal that regulates and supervises broadcasting and telecommunications in the public interest. It are dedicated to ensuring that Canadians have access to a world-class communication system that promotes innovation and enriches their lives.
The Electronic Commerce Enforcement Division (ECE)
The ECE is responsible for reducing the harmful effects of spam, malware and related threats. Its goal is to help create a safer and more secure online marketplace, and to that end, it enforces Canada’s Anti-Spam Legislation (CASL).
The law targets those who send commercial electronic messages without the recipient’s consent or install programs on computers or networks without express consent. This includes malware, spyware and viruses in computer programs, in spam messages, or downloaded through infected Web links.
The ECE has primary enforcement responsibility, including powers to investigate and take action against violators, and set administrative monetary penalties.
It also works to promote compliance among organisations and individuals, ensuring that businesses have the information they need to compete in the global marketplace.
Finally, it is responsible for administering the Spam Reporting Centre (SRC).
You can find a snapshot of recent enforcement activities here.
CASL Sections 6-8
CASL prohibits, in the context of a commercial activity, and without a person’s consent:
• [Section 6] The sending of commercial electronic messages, including spam and phishing
• [Section 7] The alteration of transmission data, including botnet activity
• [Section 8] The installation of computer programs on computers or networks, including malware and spyware
CASL Section 9
In addition, [Section 9] of CASL also prohibits an individual or organization from aiding, inducing, procuring or causing to be procured the doing of any of the above acts. This allows us to target intermediaries who, through their actions or through inaction, facilitate the commission of CASL violations.
For instance, the ECE recently took action against Datablocks Inc. and Sunlight Media Network Inc for having violated CASL section 9 by disseminating online ads that caused malicious computer programs to be downloaded onto the computers of unsuspecting victims.
It also released an Information Bulletin on Section 9, which describes the types of activities likely to contravene Section 9, and identifies measures that individuals and organizations may take to ensure compliance with the Act.
Powers under CASL
Under CASL, and for the purposes of verifying compliance or determining whether any of sections 6 to 9 were contravened, the CRTC may
• [Section 17] compel individuals and organizations to provide any information in their possession or control;
• [Section 19] ask a justice of the peace to issue a warrant authorizing entry into a place of residence;
In the event that the CRTC believes, on reasonable grounds, that an individual or organization has contravened one of more of section 6 to 9, it may :
• [Section 21] Issue a Notice of Violation. According to [Section 20], the maximum penalty for a violation is $1,000,000 in the case of an individual, and $10,000,000 in the case of an organization.
• [Section 26] Issue a Restraining Order directing an individual or organization to cease contravening the provision(s) to which the contravention relates.
• [Section 41] Obtain an Injunction from a court of competent jurisdiction in the event an individual or organization is about to do or is likely to do anything that constitutes or is directed toward the contravention of any of sections 6 to 9.
“It are dedicated to ensuring that Canadians have access to a world-class…”
It are?
Lordy….
Its an amazement the documents got typed correctly for the warrant…
*Facepalms*
Brian
I understand why you would want to publish a picture of the search warrant, but for the life of me, I fail to understand why you wouldn’t just redact the name of the Constable involved.
The warrant is not a public document, he never consented to the disclosure of his identity and involvement, and I’m sure he doesn’t need hordes of frustrated script kiddies attempting to compromise his safety and that of his family.
It’s just unnecessary. And unprofessional.
Civility matters.
Mr. Rezvez sent a reporter a legal document about himself. He made no expression of an expectation that it be kept private. I’d wager that most reporters in the United States are not in the habit of redacting the names of law enforcement officers from official legal documents, for a variety of reasons, although perhaps there are exceptions. But not usually when the document is offered by the subject of the story without any restrictions on its use.
The cop out I expected.
My point was that the document concerned people other than the subject of your article. It was not entirely his to release.
I’m glad Mr Revesz sets the standard you’re holding yourself to. Well done Brian. Well done.
Civility matters.