Organized cyber thieves stole more than $600,000 from the Catholic Diocese of Des Moines, Iowa earlier this month. The funds were spirited away with the help of dozens of unwitting co-conspirators hired through work-at-home job scams, at least one of whom was told the money was being distributed to victims of the Catholic Church sex abuse scandals, KrebsOnSecurity.com has learned.
 In a statement released last week, the diocese said the fraud occurred between Aug. 13 and Aug. 16, apparently after criminals had stolen the diocese’s online banking credentials. The Diocese it was alerted to the fraud on Aug. 17 by its financial institution, Bankers Trust of Des Moines.
In a statement released last week, the diocese said the fraud occurred between Aug. 13 and Aug. 16, apparently after criminals had stolen the diocese’s online banking credentials. The Diocese it was alerted to the fraud on Aug. 17 by its financial institution, Bankers Trust of Des Moines.
The diocese also said the FBI and U.S. Treasury Department were notified, and that the FBI had taken possession of several diocesan computers. To date, roughly $180,000 has been recovered.
The diocese added that law enforcement had advised them that the theft seems to have been the work of a highly sophisticated operation based overseas, which moved the stolen money out of the United States by recruiting people who unknowingly act as intermediaries.
“While the Diocese of Des Moines is protected by insurance and anticipates the restoration of the funds, we have been advised that such criminal activity is rampant,” Des Moines Bishop Richard Pates said. “Obviously, any entity that experiences such a crime should be significantly concerned.”
Once again, the theft involves so-called money mules willingly or unwittingly recruited by a specific money mule cash-out gang whose work I have written about several times already. Among the mules involved in this incident was a man in Newnan, Ga. who received almost $30,000 of the church’s cash. Daniel Huggins, the 29-year-old owner of Masonry Construction Group LLC, got mixed up with a company calling itself the Impeccable Group, claiming to be an international finance company operating out of New York.
Huggins said the Impeccable Group recruited him via e-mail, claiming it had found his resume on job search site Monster.com. The Impeccable Group told him he would be doing payment processing for the company, and on Aug. 16, Huggins’ erstwhile employers sent him two payments, one for almost $20,000 and another for slightly less than $10,000.
Huggins said he contacted the Impeccable Group shortly after the transfers because the amounts seemed quite high and the transfers appeared to be coming from the Catholic Church. The scammers apparently were ready for this question and were quick on their feet with a reply that was as plausible as it was diabolical: Huggins was told the money was going to be distributed as legal settlements to people who had been affected by the clergy sexual abuse scandals that have rocked the church in recent years.
“The told me it was going to be payouts to some of the settlements in the sex crimes cases against the Church,” Huggins said.
Huggins’ bank discovered the fraud and froze his account while there was still almost $10,000 left in it from the fraudulent transfers. Huggins said he was told to expect a call from lawyers for the Des Moines diocese, but he’s conflicted about whether he will return the money he made from his part in the scam: Minus the Western Union and Moneygram wire fees, Huggins earned commissions totaling nearly $800 for helping the thieves transfer the stolen money out of the country.
“I already sent the money to pay off my credit card balance,” Huggins said. “I guess I’m still up in the air on that one.”
The screen shots below were taken of Huggins’ “task manager,” an online communications panel that Impeccable Group used to communicate with money mules they had recruited.



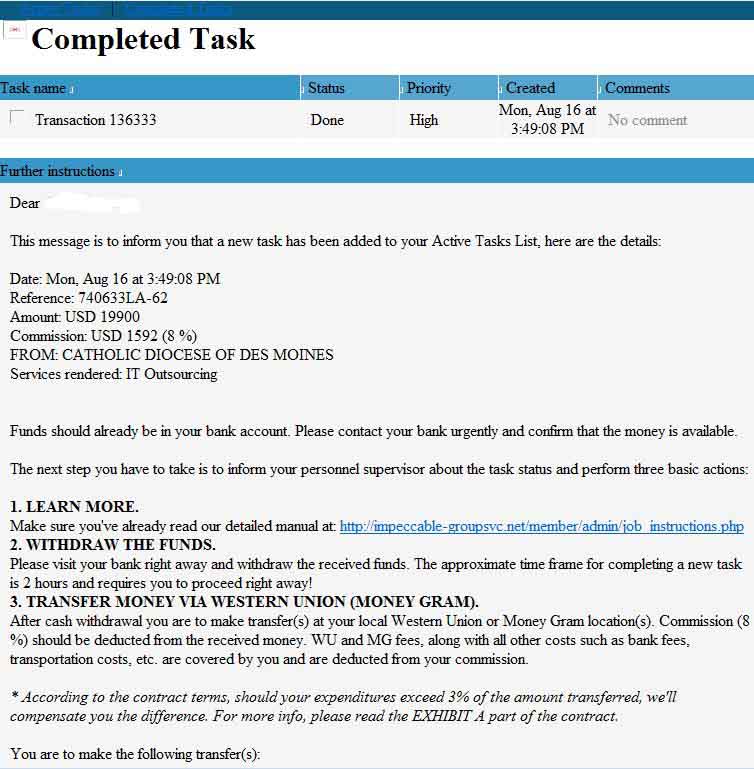
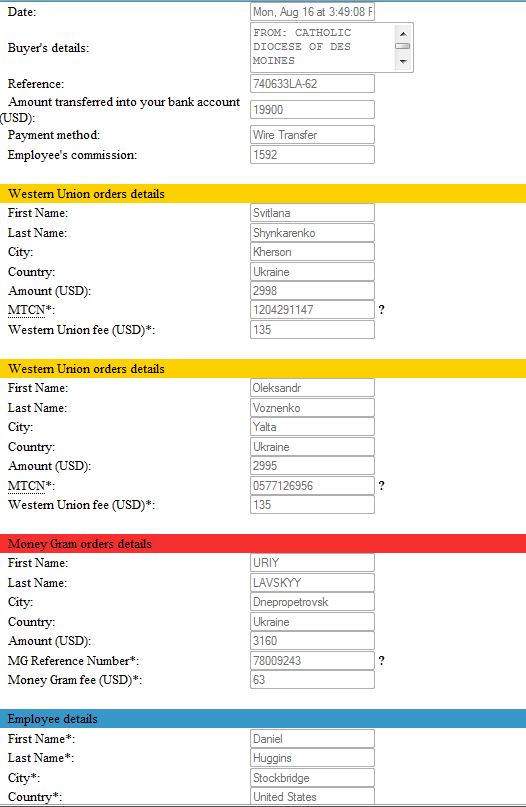


Talk about robbing Peter to pay Paul!
And destinations all over Ukraine. I wonder how the recruitment scheme works on the other side and how much the people there know about what it going on. These people were probably recruited in similar fashion and relay money to its final destination via some payment system common in the former USSR – like WebMoney.
Btw, I tried looking up the names in the phone book – these last names are either too common (phone books don’t store full first names unfortunately, only initials) or there is nothing that looks like a match. I wonder whether these names are real – do people have to show an ID when they come collect the money?
In many parts of the world (such as West Africa), no. Western Union and Moneygram are totally insecure for sending money to someone you don’t know personally.
“but he’s conflicted about whether he will return the money he made from his part in the scam: ”
What else? The money belongs to the church.
I would think that the church would have to prove that Mr. Huggins knew that he was receiving ill-gotten gains rather than just payment for services rendered.
For example, should everyone ever employed by Bernard Madoff (e.g., clerical staff) have to return all of their income because they were paid with money that Madoff acquired through a decades long ponsi scheme?
No need for the diocese to do anything. What happens now is the diocese’s insurance company reimburses the diocese and then go after all liable parties especially those with deep pockets (I’d worry if I’m the bank). Sometimes bloodthirsty insurance companies are a good thing.
Madoff et al (if et al exists) are liable for investor losses regardless of whether they were spent on wages, sin or charity. Investors won’t sue ex-employees who did not knowingly participate in the scheme but had merely exchanged work for wages in good faith (they can try but they won’t win).
Interesting point.
Can Daniel really have the option of keeping his commission? If it’s all a part of a scam I would think his bank would reverse the payments or something. While I understand he didn’t know it was a scam and he’s also a victim, I’m surprised that’s even possible.
Iwould think he could try but in the end he could end up having his account funds frozen until the money is recovered on behlaf of the bank and client. Even if he chose not to give any money back I would think he would still be liable if the police decided to charge him with recieving the stolen funds. I am suprised this guy does not want to turn the money that is remaining back, it defiently casts a matter of caution as to how bad he feels about his part in this, most people if they were in this situation would feel bad and want to give the rightful owner their cash back…but not everyone’s moral compass points the right way
No, he doesn’t get to decide. The money never belonged to his “employers,” so they didn’t have the right to give it to him. And his only defense against the charge of receiving stolen property is that he was not aware there was any illegal activity going on. That will be a harder case to make when the only remorse he’s shown is over the fact that he got caught and didn’t get to keep the money.
I find it interesting that the mule did make the effort to contact Impeccable Group.
However, how can anyone not be suspicious about these “sex abuse” payments being made from the Des Moines diocese to someone in the Ukraine?!
Anyone who desperately needs money or a job is likely to fall for this type of scam (not to mention those who are just plain greedy).
Three simple reasons why people aren’t suspicious:
First, unsophisticated people don’t read blogs like this or any other news source that would alert them, and the mainstream news media don’t often cover this scam.
Second, they’ve probably sent their resumes to lots of internet job search sites, some legitimate and some not, and are assuming that this was a reply from one of them.
Third, there are a lot of people out there who believe that anything in print must be true.
True, no disagreement there. He was suspicious enough to contact Impeccable Group. Too bad he didn’t contact the diocese, the one making the payment.
You know the Ukarine connection raises a few questions. One of which would be what Western Union affilitaes in the Ukraine are receiving these types of payments and how often. The second question I have would be how often are these same Recipients in the Ukraine having money transferred to them. I have to think you would have to show some I.D. to pick up the money so they know you are actually the person it is destined for ( yes I know they could be using phony I.D. ) but that would mean they could only pick up cash for so long before the people running the western union outlet would get suspicious ( cause if you are getting so many transfers in a day or a week you would think it would set off some alarm bells) So I am wondering if they are using a recruitment scam like they do on the mules they use to transfer it, except on those picking it up… I also wonder if the same western union affiliates are being used over and over again, as it could be some of the western union outlets could possibl be taking a cut as well ( you never know..there are a lot of people who are easily induced ) You would have to think Western Union must have a clue some of this is going on, but why is it we never hear from them on any of this since it seems thjere systems are being used to get the loot and quite overly it would seem. You would think if they have roque factions in their network of affilitaes they would want to root them out so as to not have them slapped with any regulation governing better controls on how they run their buisness and the requirements within it. But why is it they dont seem to be taking a look at their transfers to countries where a lot of stolen money is headed , I mean surely they must see a spike on amounts or a odd number of trnsactions in a short period that would lead to a clue, or could it be they aren’t that concerned as they get paid for every transaction regarless of who or how it came to be that it went through their system
I was told that Western Union requires an ID when receiving money. Which makes me believe that the same kind of large-scale recruiting operation is going on on the other side as well. Sure, there could be phony IDs – but that makes things more complicated and more risky (more importantly: that’s risk that money mules are necessarily aware of). And sure, money mules on the receiving end can be reused – but not indefinitely, eventually somebody (hopefully at Western Union) will grow suspicious. So I guess that there are lots of money mules being used to receive the money as well. Who were probably hired in a similarly anonymous way.
Wladimir — I believe you are correct. There is mule recruitment on both sides of these transactions.
What’s more, the thieves orchestrating these scams often change the target recipient in Ukraine as the money is midway. When these mules in the US sign up, they’re asked to send in a scanned copy of their drivers license.
Couldn’t figure out for a while why they were doing that, until found out that the thieves had a habit of calling up WU and saying, you know what, we’d like the money to be sent to this other guy in Ukraine instead. And the WU people were happy to do that. Their catch? They would asked the caller to state the sender’s drivers license number.
Given that an id is just a piece of paper, is it not possible that the link in the Ukraine is corrupt? Can they not just dish out cash over there? “Yeah, mr smith came in and picked up the money just yesterday. Yeah, of course I checked the id, and I picked up a handling fee on the side.” Just a thought.
Actually, I’m being silly. Sorry all.
The wired money from America would still end up going to a central place in the Ukraine, so regardless of someone taking the cash out, you could still point the finger and say “this bank/building is at fault”.
A more intelligent way is for it to go to that single place, and for them to pay it out to many fake offshore companies, who then legitimately pay a single person. Sure, that person is getting a lot of money in, but he’s paying off the local police and probably a few higher, and he’s built the local school, and he employs most the town, and he’s clearly a very successful businessman. So nobody is any the wiser. However, there’s no reason for the offshore companies to be owned by different people, just different aliases.
I hope eventually someone sues the banks for “aiding and abetting” in such scams. I agree that banks don’t have to provide a zero-liability rule for businesses like they do for private citizens, but heck, there are dozens of technological gizmos I can think of that could have HELD the payments and waited for secondary approval from the church. How about something as simple as this: Adding a new payee in an online account generates an email to the account holder, and a new payee can only be “used” in a transaction after five days. DONE, risk lowered significantly, with hardly any inconvenience on everyday use.
Most people are unaware that the banks offer all sorts of security options, including call-backs, email notifications, and secondary approvals. Almost all commercial customers decline these security measures because it is “too much of a pain.” If the commercial customers decline these extra measures, it is they who are negligent and liable.
Well said.
Sorry – but as an owner of a small business account – I can assure you that your statement is absolutely false.
I have called my commercial bank many times and begged for such security measures, but they only continue to parrot back to me that “all transactions are encrypted”.
Reminds me of the the Bait Car program. This set-up has been on TV long enough for everybody to know to stay clear of Escalades with keys in the ignition. Point….Westen Union is the payment of choice for scammers. The last time I wired via WU, there were prominent disclaimers warning about wiring to suspect recipients. Do these mules live in a different realm than the prudent?
I’ve read those “disclaimers” on wiring money to people you’ve never met. The good news is they’re on page 1, the bad news is they read like low-keyed advice. If it’s gotten that far (mules at the WU counter with $thousands in their pockets) without setting off alarm bells, I think it’s unlikely that printed warnings would be effective at that point. Will hazard a guess that even if mules realize they could be doing something illegal then, some will still go through with it and hope they won’t be caught (“I’ll only do this once”). Ethical standards aren’t what they used to be — just consider Huggins’ “conflict” on whether he will return the money.
“I’ll only do this once.”
You can say that again. Mules are a use-’em-once, throw-’em-away kind of resource. Whether the mule comes to the attention of authorities or not, he will never hear from his friends at Impeccable Group again.
It looks like he made more than ~$800 in commissions.
For the $19900 transaction it shows 8% commission @ $1952
For the $9950 transaction it shows 8% commission @ $796
I also found it interesting that the services rendered is listed as “IT Outsourcing”
@Jay — As I noted in the story, and as you can see from the screenshots, he only transferred 2/3 of the money. Add the WU transfer amounts, multiply by .08 and subtract the wire fees.
Thanks for the math (and reading comprehension) lesson Brian, maybe I should post *after* coffee 😉
As always, thanks for the interesting read!
Come on. Just how damned dumb (or greedy?) do you have to be to forward money from a Catholic diocese in America to a Ukrainian recipient? Huggins should get 10 years in the slammer just for being so stupid.
Hey Mr. Huggins, care for a round of three card monty maybe? There’s no excuse for this kind of behavior. As WC Fields pointed out, “You can’t cheat an honest man.”
In fairness, there have been plenty of cases of Americans going overseas to sexually abuse children, and in a few cases, they were missionary priests. However, I don’t know of any cases where children in other countries won the kind of huge civil judgments that get handed out by American courts. Just getting the abusers to face criminal charges in the US for crimes that occurred in foreign countries has only been a recent advance. (The fact that the children don’t have much chance of becoming wealthy as a result of their testimony makes the criminal cases much easier to prosecute, too, I suspect.)
That being said, Huggins’ greedy, stupid statement about not returning the money — when legally, he’s actually responsible for the part he wired to Ukraine, not just the part he kept — doesn’t make me too sympathetic.
The situation with Maidoff is an interesting parallel. I suppose the only reason his employees aren’t expected to return the money is that it went on so long and fooled so many people. They might otherwise have faced criminal charges for being co-conspirators. (AFAIK, prosecutors didn’t even try to get money back from the charities that actually profited because they got into the pyramid scheme early. )
I can’t help myself from saying this yet again – better use of the existing tools can still help in these situations.
All the major small business and corporate banking applications have alerting capability. A simple once a day alert that shows activity or account balances (balance changes) could have alerted the church’s money manager of an issue a day or two sooner. Based on the details it is a little hard to say how much the extra time would have helped but I am sure that it would have helped some.
Cleverly, this all happened over a weekend. There may have been nobody there to receive an alert. Particularly at a Church organization.
Hey Mr. Krebs, you’re on El Reg again… http://www.theregister.co.uk/2010/08/31/church_funds_phishing_scam/
w00t! Maybe I should just go by “El Krebs” from now on? 🙂
BK, one word I never thought I’d see you put in print is “woot.” congrats.
Brian..Enjoy both your writing and the subject matter. On this case in particular, any knowledge on how the cybercriminals (one word or two, or hyphenated, , got access the the diocese online banking account in the first place?
Malware?
Thanks for any insight and keep it up.
Mark
Hi Mark. Yes, they stole the credentials via malware, as always. Beyond that, I can’t go into more detail.
Thank you sir…without going into detail on this specific case, typically what types of malware have proven to be most successful in these kinds of compromises SQL Server Injections, a socially engineered case where a bank employee clicks on a link to a malware-laden site? Just curious.
Thanks, btw, for the prompt reply.
Chees,
Mark
Mark- It’s almost always through e-mail with these guys. Fake UPS tracking label, or bogus FB e-mail or something like that, that is opened by someone at the victim organization who has access to the organization’s bank accounts online.
Thanks again…significantly impressed with your comment response time. I may reach out to you on this topic in the future…seems like that’s the most fertile ground for attack at the moment — playing on people’s human desire to help, ask for help, share and engage in social media settings – and the suspension of critical thinking and B.S. detection in these environments by reasonably intelligent people.
I have a feeling we’re going to be writing about and following the same things for awhile.
Best,
Mark
http://www.twitter.com/@MarkAEvertz
At least it would be a worth cause.
What I find interesting that the Impeccable told the money mule, Huggins, to withdraw the money within the two hour time frame knowing that it sits in the account too long the bank would notice the fraud and freeze the account.
Aside from the fact that it became apparent a fraud took place. the money belongs to the church, period. If Huggins doesn’t return the money, he could possibly be charged with receiving ill-gotten gains in commission of a crime unless it can be proven that he did not know it was stolen. It will be between the parties to sort out the end game.
Thieves stole more than $600,000 from the Catholic Diocese of Des Moines then also FBI really made the fantastic recovery of $180,000. BUt just can’t understand how did they use intermediaries to transfer the money to overseas from US. Must be the theves too.