Fresh on the heels of a disclosure that Microsoft Corp. leaked internal customer support data to the Internet, mobile provider Sprint has addressed a mix-up in which posts to a private customer support community were exposed to the Web.
KrebsOnSecurity recently contacted Sprint to let the company know that an internal customer support forum called “Social Care” was being indexed by search engines, and that several months worth of postings about customer complaints and other issues were viewable without authentication to anyone with a Web browser.

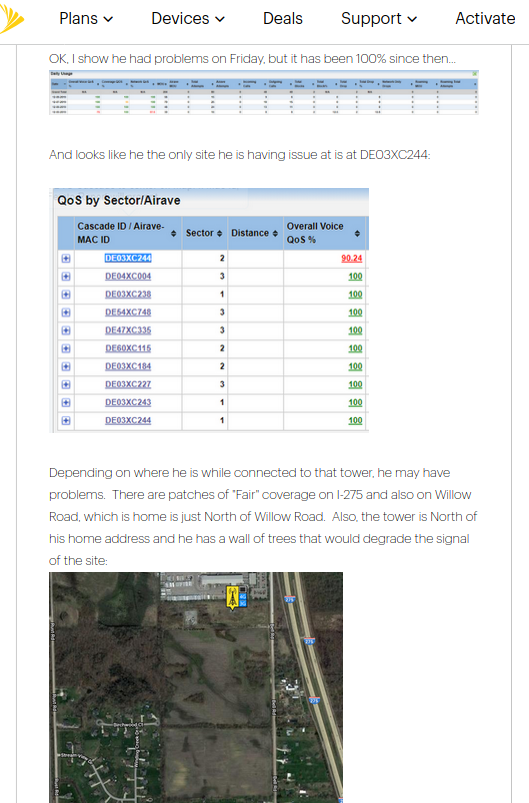
A redacted screen shot of one Sprint customer support thread exposed to the Web.
A Sprint spokesperson responded that the forum was indeed intended to be a private section of its support community, but that an error caused the section to become public.
“These conversations include minimal customer information and are used for frontline reps to escalate issues to managers,” said Lisa Belot, Sprint’s communications manager.
A review of the exposed support forum by this author suggests that while none of the posts exposed customer information such as payment card data, a number of them did include customer account information, such customer names, device identifiers and in some cases location information.
Perhaps more importantly for Sprint and its customers, the forum also included numerous links and references to internal tools and procedures. This sort of information would no doubt be of interest to scammers seeking to conduct social engineering attacks against Sprint employees as way to perpetrate other types of fraud, including unauthorized SIM swaps or in gleaning more account information from targeted customers.
Earlier this week, vice.com reported that hackers are phishing workers at major U.S. telecommunications companies to gain access to internal company tools. That news followed a related Vice report earlier this month which found ne’er-do-wells are now getting telecom employees to run software that lets the hackers directly reach into the internal systems of U.S. telecom companies to take over customer cell phone numbers.
The misstep by Sprint comes just days after Microsoft acknowledged that a database containing “a subset of information related to customer support interactions was accessible to the internet between the dates of Dec. 5 and Dec. 31, 2019.” Microsoft said it was alerting individuals whose information was exposed, which included location information, email and IP addresses, telephone numbers and descriptions of technical issues.
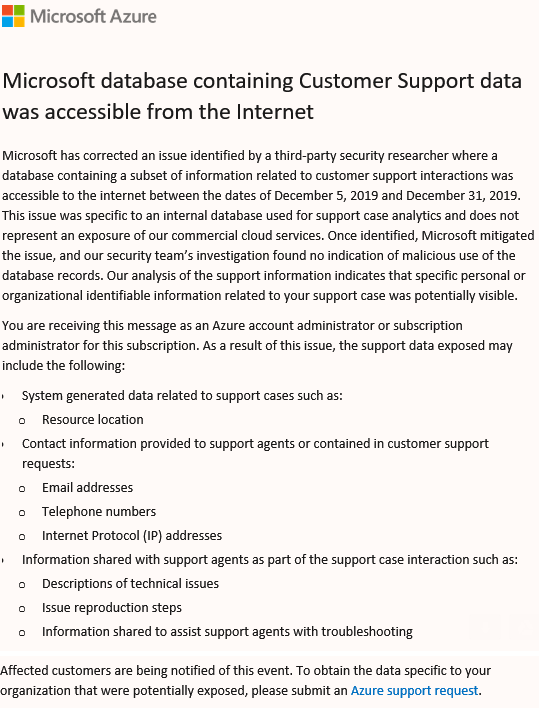
A message Microsoft sent to customers affected by their recent leak of customer support data.
This week marked the annual observance of Data Privacy Day, an occasion in which we are reminded to be more judicious about the types of personal information we voluntarily share on social media and other Web sites. But both the Microsoft and Sprint stumbles are a reminder that billion-dollar companies very often expose this information on our behalf, even when we are doing everything within our power to safeguard it.




This isn’t good, data leaks are occurring a lot more
I think they’re being detected a lot more.
Man, And I thought that Microsoft has learned its lessons from the past and was doing so well…. and Azure from all the places. Not good, Microsoft, not good.
Given the decline in Microsoft (as evidenced not only by these [and other] stumbles but by the poor quality of its Win updates), we should no longer be surprised.
No question that they are in business to make money — and that’s fair — but when cutting corners (for lack of a better term) leads to this erosion in their operations, we should all be concerned.
This is becoming a much too often occurrence. Sending the notice that the event occurred, and the ‘we care about your privacy’ spin just doesn’t get it any more. It is getting to the point that the brand isn’t suffering any damage now.
Seeing these “We value your privacy” popups makes me close the browser tab many a time now.
I don’t want to communicate too much with liars.
All these poopups mean to me today is “the law restricts us, otherwise we’d track your every click, and we’ll do it anyway with trickeries of different kinds like complicated click data distribution firm networks”.
If we don’t make it backfire, they will not change their behavior.
Exactly this! “We care about your privacy… because we’ll get fined from the GDPR if we don’t handle it properly.” It’s such a tired response nowadays. It’s like every company that experiences a breach reads off the same template, but replaces the //INSERT YOUR COMPANY NAME HERE// with their own.
“We take security and privacy seriously”
actually means
“We haven’t taken security and privacy seriously enough.”
I read that as “We take your security and privacy. Seriously.”
You don’t block pop-ups with an exception list? They are invariably used for advertising.
If you loved finding out this, folks, You all are going to love what the Electronic Freedom Foundation has to say about the Ring doorbell app. Bleeping Computer also comments that info was forwarded to Facebook. This includes individuals who do not have a Facebook account.
Electronic Frontier Foundation
An eye-opener. Now I’m not going to get one, although my neighbors have them. Read Snowden’s recent book.
Serves them right for annoying me with their stupid ads. That guy with the thick glasses has such a grating voice.
Wasn’t that the same “Can you hear me now?” guy from Verizon years back?
Right you are, Ken.
Yes!!! Finally someone gets it. You just made my day.
With all this information being hacked it would be easier to report what isn’t being hacked. O weight a minute then there would be nothing to report. What a scary web we are on now days. Thanks for all the reporting you do Brian.
It’s just another in an ever-lengthening reports with an “Oops!” exposure of personal data, not requiring any particularly skillful hacking either…
I’ve been attempting to alert ANYBODY of exploit and vulnerbities related to iPhone 8 plus and Sprint. I’m either right or need a mental health evaluation. Someone has unfettered aces to my device and are doing all sorts of recon work by testing what can be done on it in a jailbroken fashion. I no nothing about this device except how to makes calls but I have actual seen apps disappear right as I am using them. I can not wait till Apple support realizes that they have silently watched as the support handed them keys to Apple iOS support servers.
Maybe instead of “we care about your privacy” statements these companies that leak data should switch to saying we are in “their thoughts and prayers”. That saying works so well with mass killings.
I’ll just add my view on SIM Jacking and leave the Microsoft “can of worms” for another day.
SIM stealing is done via Remote Access Scams or Remote Desktop Protocol [RDP] scams at the telephone carrier level… cough Sprint, cough ATnT…
Basically, scammers are using confidence games to lure low level employees into installing Remote Desktop Protocol (RDP) or Remote Access software on major telephone carrier’s networks without permission.
If you follow all Brian’s links to Vice news [or Motherboard – and all links] the Remote Access Software is “Omni” [Verizon ], “Opus” [ATnT], QuickView [T-Mobile], Splashtop, Citrix software and probably other software, to simply gain SuperUser style of privileges and move the victims iPhone, or Android phone number to criminal’s phone. Other dirty trick can then be done by the criminal.
This is something like the old “log me In” trick where some offshore caller scams a computer user into installing Log Me In to fix a bogus problem. The Scammer takes control the victim’s machine and precedes to scam him.
This is now done at the international telephone carrier level where the criminal begins to get into fraud and wiretapping laws.
For convenience, time savings, and profits, telecommunication carries have let stand-alone store employee’s use this powerful Telephone Remote Access software – which may save some time – but also may cause the store employee to get scammed into SIM Swapping or SIM jacking – for a profit.
The problems are obvious. No, low level phone sales employee should have access to such powerful RDP or Remote Access software. The telephone carrier should audit and log all such SIM Swaps closely. This is not being done. SIM Scamming is happening.
I am sure other posters can describe the SIM Jacking Scam better than I can or correct any mistakes I have made. If so please speak up a post your knowledge here.