In late December 2019, fuel and convenience store chain Wawa Inc. said a nine-month-long breach of its payment card processing systems may have led to the theft of card data from customers who visited any of its 850 locations nationwide. Now, fraud experts say the first batch of card data stolen from Wawa customers is being sold at one of the underground’s most popular crime shops, which claims to have 30 million records to peddle from a new nationwide breach.
On the evening of Monday, Jan. 27, a popular fraud bazaar known as Joker’s Stash began selling card data from “a new huge nationwide breach” that purportedly includes more than 30 million card accounts issued by thousands of financial institutions across 40+ U.S. states.
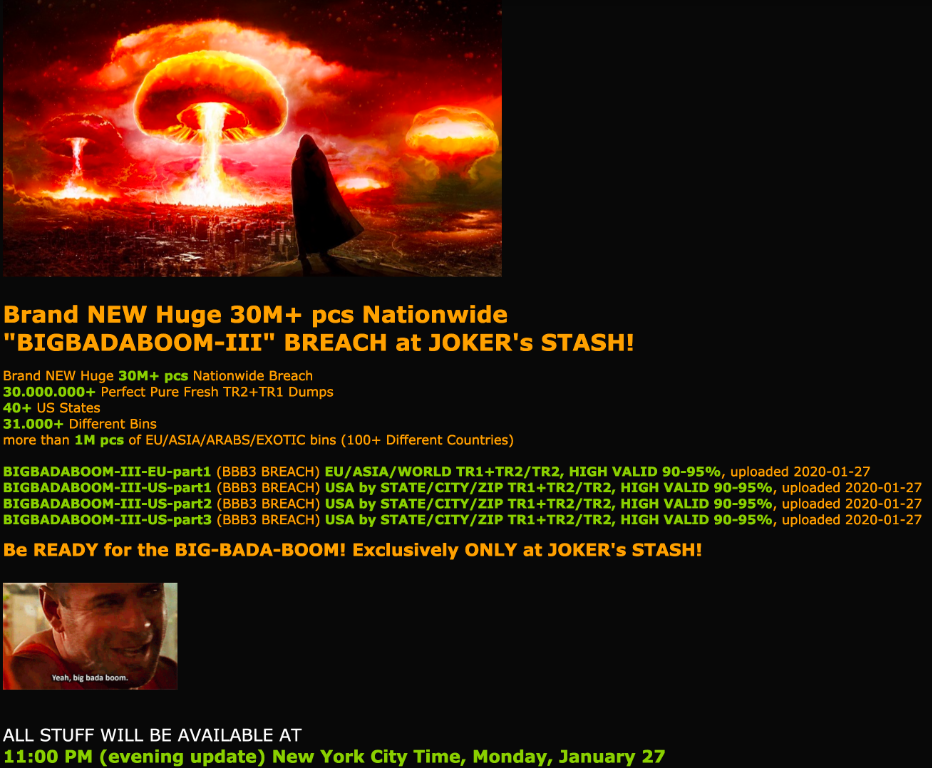
The fraud bazaar Joker’s Stash on Monday began selling some 30 million stolen payment card accounts that experts say have been tied back to a breach at Wawa in 2019.
Two sources that work closely with financial institutions nationwide tell KrebsOnSecurity the new batch of cards that went on sale Monday evening — dubbed “BIGBADABOOM-III” by Joker’s Stash — map squarely back to cardholder purchases at Wawa.
On Dec. 19, 2019, Wawa sent a notice to customers saying the company had discovered card-stealing malware installed on in-store payment processing systems and fuel dispensers at potentially all Wawa locations.
Pennsylvania-based Wawa says it discovered the intrusion on Dec. 10 and contained the breach by Dec. 12, but that the malware was thought to have been installed more than nine months earlier, around March 4. The exposed information includes debit and credit card numbers, expiration dates, and cardholder names. Wawa said the breach did not expose personal identification numbers (PINs) or CVV records (the three-digit security code printed on the back of a payment card).
A spokesperson for Wawa confirmed that the company today became aware of reports of criminal attempts to sell some customer payment card information potentially involved in the data security incident announced by Wawa on December 19, 2019.
“We have alerted our payment card processor, payment card brands, and card issuers to heighten fraud monitoring activities to help further protect any customer information,” Wawa said in a statement released to KrebsOnSecurity. “We continue to work closely with federal law enforcement in connection with their ongoing investigation to determine the scope of the disclosure of Wawa-specific customer payment card data.”
“We continue to encourage our customers to remain vigilant in reviewing charges on their payment card statements and to promptly report any unauthorized use to the bank or financial institution that issued their payment card by calling the number on the back of the card,” the statement continues. “Under federal law and card company rules, customers who notify their payment card issuer in a timely manner of fraudulent charges will not be responsible for those charges. In the unlikely event any individual customer who has promptly notified their card issuer of fraudulent charges related to this incident is not reimbursed, Wawa will work with them to reimburse them for those charges.”
Gemini Advisory, a New York-based fraud intelligence company, said the biggest concentrations of stolen cards for sale in the BIGBADABOOM-III batch map back to Wawa customer card use in Florida and Pennsylvania, the two most populous states where Wawa operates. Wawa also has locations in Delaware, Maryland, New Jersey, Virginia and the District of Columbia.
According to Gemini, Joker’s Stash has so far released only a small portion of the claimed 30 million. However, this is not an uncommon practice: Releasing too many stolen cards for sale at once tends to have the effect of depressing the overall price of stolen cards across the underground market.
“Based on Gemini’s analysis, the initial set of bases linked to “BIGBADABOOM-III” consisted of nearly 100,000 records,” Gemini observed. “While the majority of those records were from US banks and were linked to US-based cardholders, some records also linked to cardholders from Latin America, Europe, and several Asian countries. Non-US-based cardholders likely fell victim to this breach when traveling to the United States and utilizing Wawa gas stations during the period of exposure.”
Gemini’s director of research Stas Alforov stressed that some of the 30 million cards advertised for sale as part of this BIGBADABOOM batch may in fact be sourced from breaches at other retailers, something Joker’s Stash has been known to do in previous large batches.
Gemini monitors multiple carding sites like Joker’s Stash. The company found the median price of U.S.-issued records in the new Joker’s Stash batch is currently $17, with some of the international records priced as high as $210 per card.
“Apart from banks with a nationwide presence, only financial institutions along the East Coast had significant exposure,” Gemini concluded.
Representatives from MasterCard did not respond to requests for comment. Visa declined to comment for this story, but pointed to a series of alerts it issued in November and December 2019 about cybercrime groups increasingly targeting fuel dispenser merchants.
A number of recent high-profile nationwide card breaches at main street merchants have been linked to large numbers of cards for sale at Joker’s Stash, including breaches at supermarket chain Hy-Vee, restaurant chains Sonic, Buca di Beppo, Krystal, Moe’s, McAlister’s Deli, and Schlotzsky’s, retailers like Bebe Stores, and hospitality brands such as Hilton Hotels.
Most card breaches at restaurants and other brick-and-mortar stores occur when cybercriminals manage to remotely install malicious software on the retailer’s card-processing systems. This type of point-of-sale malware is capable of copying data stored on a credit or debit card’s magnetic stripe when those cards are swiped at compromised payment terminals, and that data can then be used to create counterfeit copies of the cards.
The United States is the last of the G20 nations to make the shift to more secure chip-based cards, which are far more expensive and difficult for criminals to counterfeit. Unfortunately, many merchants have not yet shifted to using chip-based card readers and still swipe their customers’ cards.
According to stats released in November by Visa, more than 3.7 million merchant locations are now accepting chip cards. Visa says for merchants who have completed the chip upgrade, counterfeit fraud dollars dropped 81 percent in June 2019 compared to September 2015. This may help explain why card thieves increasingly are shifting their attention to compromising e-commerce merchants, a trend seen in virtually every country that has already made the switch to chip-based cards.
Many filling stations are upgrading their pumps to include more cyber and physical security — such as end-to-end encryption of card data, custom locks and security cameras. In addition, newer pumps can accommodate more secure chip-based payment cards that are already in use and in some cases mandated by other G20 nations.
But these upgrades are disruptive and expensive, and many fuel station owners are putting them off until it is absolutely necessary. Prior to late 2016, fuel station owners in the United States had until October 1, 2017 to install chip-capable readers at their pumps. Station owners that didn’t have chip-ready readers in place by then would have been on the hook to absorb 100 percent of the costs of fraud associated with transactions in which the customer presented a chip-based card yet was not asked or able to dip the chip.
Yet in December 2016, Visa — by far the largest credit card network in the United States — delayed the requirements, saying fuel station owners would be given until October 1, 2020 to meet the liability shift deadline.
Either way, Wawa could be facing steep fines for failing to protect customer card data traversing its internal payment card networks. In addition, at least one class action lawsuit has already been filed against the company.
Finally, it’s important to note that even if all 30 million of the cards that Joker’s Stash is selling as part of this batch do in fact map back to Wawa locations, it’s highly unlikely that more than a small percentage of these cards will actually be purchased and used by fraudsters. In the 2013 megabreach at Target Corp., for example, fraudsters stole roughly 40 million cards but only ended up selling between one to three million of those cards.




The Target breach data included CVV. The fact that WaWa data does not include CVV will means that a lot less of this data will be sold, and for a lot less.
Target was track data = Wawa track data….. CVV reference is just breach coach spin.
I think putting it more clearly for the masses… track data _includes_ CVC/CVV data.
Here’s a nice breakdown of the track data I found: https://www.nuix.com/blog/howd-they-do-part-2-you-stole-my-credit-card-number
So, if the breach is indeed all of TR1+TR2 data, I can’t see how Wawa can claim CCV was not included and not be an outright fabrication.
There’s some terminology confusion: there is a Card Verification Value (CVV) contained within the track data, but it’s different to the CVV2 that appears on the back of the card, and cannot be used to facilitate online transactions which require a CVV2. Because the CVV2 is the one you can see – and because of its relevance to being able to sell the card data for use online rather than to produce counterfeit cards only – it’s often referred to as “CVV” colloquially.
As far as I recall, the card data stolen at Target did NOT include CVV numbers. Merchants are prohibited from storing this information.
The data for sale on Joker’s Stash is for Track1/2 data, which is used to make physical counterfeits of the cards. Thieves who specialize in cashing out these counterfeit cards do not need the CVVs to do that. Nobody is going to buy these to use at online stores.
As I recall, the Target data included CVV1.
I now think WaWa is lying. I bet the WaWa data includes CVV1. They are using that fact that the WaWa data does not include CVV2 to say that ” the breach did not expose…CVV records”
Real good, informative article .
Wow. A positive comment from you. Never thought I would ever see that on Brian’s articles. 99% of the time you express your butthurt to an extreme level in your comments.
Thank you Brian for the article. Taught me more about the carding underground works.
Magstripes have a separate 3 digit CVV value (called something different for each network – CVV = Visa and CVC = MasterCard) to validate the magstripe data with the issuer/processor. The 3 digits on the back of the card are referred as the CVV2 and are a different value that what is on the magstripe.
Based on data in the story – Wawa said “the breach did not expose personal identification numbers (PINs) or CVV records (the three-digit security code printed on the back of a payment card).” Wawa just spinning it to tell you CVV2 wasn’t captured, but fraudsters are not after CVV2 with a pump skimmer.
@ Chuck
oh Chucky Boy!the fact you can so confidently state what pump scammers are looking for tells me that you my friend are indeed a scammer your self
If you read the gas station trade magazines you’ll realize pretty quickly that a huge number of the automated gas dispensers in the US will not be upgraded to accept EMV cards by the 2020 liability shift deadline.
In other words, expect these sort of breaches to continue on for some time.
It’s high time for gas stations and restaurants to get with the program. Moe’s for example, which had a huge breach, is still swiping cards. I guess they figure with low transaction amounts they’d rather eat the liability. I suppose they don’t care much that other entities suffer due to their complacency- when those compromised cards are used at other merchants.
But we instead get TV screens at gas pumps that yap at you while you are trying to fill up. Misplaced priorities.
Eric- You are right on. Wawa’s focus has been entirely in the wrong place. CEO, CIO and CSO should go.
The most frustrating thing about this: before I moved, we had an American Natural gas station open right down the road from my old apartment building. I couldn’t insert my card, select my gas, or do anything until the ad finished. Needless to say, I left before the ad finished and never went back to that gas station. I’m not sure if all American Natural stations are like this, but I most certainly won’t use another again to find out.
> But we instead get TV screens at gas pumps that yap at you while you are trying to fill up
On every pump I’ve tried it, there are 4 white buttons on each side of the TV screen. The second from the top on the right side is an unlabeled mute button.
Curious to read that only ~1-3M credential sets of 40M were estimated as sold from Target’s breach. Is this a consequence of consumer vigilance, payment industry action, or the lassitude of thieves?
I think it was due to a combination of factors, including too much supply at once, not enough demand, and then many banks simply re-issuing millions of cards. Probably 20 million cards were re-issued after the Target breach. See this piece which looked at the decline in valid rates and impact that had on sales and prices over the months following the breach:
https://krebsonsecurity.com/2014/02/fire-sale-on-cards-stolen-in-target-breach/
Next time I use my chip card at WAWA, I’ll have to watch and see if it’s swiped or dipped. Never have had a chip CC compromised, never had a strip card compromised at a store either and all my cards now have chips. I assume that if everyone had a chip card the bad guys would find a way, someway, somehow, to compromise them. I only use one CC at gas stations and that’s 2-3 times a month at best, so I’d know immediately if someone put a bogus charge on it.
I had a chip card that was supposedly compromised, but it was just that the card was worn out, and the chip was damaged.. I kept getting security reports from various vendors for a while after that, and had to email or call them to let them know that nothing was compromised and the card number was changed. (got a new card)
WaWa operates in New Jersey as well, so Florida and Pennsylvania are not the two most populous states that WaWa operates in.
Scott, what is the source of your information for New Jersey being more populous than either Florida or Pennsylvania? The Census bureau disagrees, as does a cursory Google search.
New Jersey has the most Wawa locations of any state, different usage of populous.
See https://csnews.com/florida-likely-replace-new-jersey-wawas-largest-market
“The Sunshine State is about to replace the Garden State as Wawa Inc.’s largest market.”
“Today, there are 251 locations in New Jersey, 236 in Pennsylvania and 167 in Florida”
Let’s all get over this silly focus on which state, etc.
FWIW, Brian specifically referred to “the most populous” states, not the ones with the most Wawa locations.
We don’t know Wawa’s per-store business volume, but it’s quite possible that it’s higher in the more populous PA (or FL) than NJ.
But what’s the difference? This is all a distraction from our needed focus on the more fundamental question of what (types of) data was actually lost and just how “exposed” consumers’ cards really are. And on identifying how the breach happened in the first place.
As a consumer I dont think I care what data was stolen etc. All I care about is my card data was compromised. Cancel my card, issue me a new one, done, end of story. What they actually got is irrelevant. They got something, my card is compromised, period.
Boom!! You said it perfectly my dude!!
I agree!
Wawa had over 200 stores in Florida at the end of 2018 with a goal of 400. When the goal is reached, Florida will be Wawa’s #1 market if it isn’t already.
Is there any info on how specifically this happened or how they gained access to their payment card network?
How can it be that there are still PCI certified equipment out there without security ?
In developed countries, no magstripe is used, only chip&pin or NFC. A table inside the terminal says which cards are payment cards, based on prefix, and those can only be exported as 6+4. Rest is considered loyalty cards.
All terminals are P2PE or equivalent, that is, transactions might be stored encrypted inside the device in offline mode, but the normal is real-time connection to the aquirer or service provider with approved encryption.
There is no way the retailer would need to access the card data.
We do have some retailers that uses a 3rd party service to store your receipts with full details. For that, the payment terminal company delivers custom firmware with the 3rd party providers 32-bit random value that is used to generate a sha-256 hash of the card number and other data, which will uniquely identify the card, and allows retailers to send receipts for qualified hashes to the 3rd party service.
The 3rd party will not store the card number, only see it when they generate their hash.
But the US payment industry is a decade or more behind.
In the US consumers can pay at the pump. In most other countries that is not the case. Pay at the pump adds some challenges to using P2PE. There are no P2PE validated solutions for pay at the pump for retail fuel that I am aware of. Also in the US retail fuel industry there are a much larger assortment of cards accepted, and processors/aquierers involved. This all adds to the difficulty of deploying an encryption solution. Special fuel cards (Fleet cards) for example can offer challenges to encryption systems. There are some End to end (E2EE) non-PCI validated solutions from some payment processors available that can minimize the exposure, but those are not commonly deployed at this time, and they still can have issues with certain card types. I suspect we will see more of those deployed after this, but it will take time. Retail fuel payment is a pretty complicated beast in the US
You might be right about “most other countries” if you include all the developing nations, but I’ve seen pay at the pump in, well, every European country I’ve driven in. And New Zealand. And Australia. Hell, in Iceland a couple of months ago the last petrol station I used ONLY had automated payment at the pump.
I can’t imagine that this couldn’t be sorted out in the USA. Seems like most similarly developed nations have managed it. I get the feeling the problem is nobody wants to – so let’s kick the can further down the road…
Anyone know if BluePay has P2PE for pumps? They seem to offer P2PE for some stuff, and they offer pump stuff…
We have lots of WaWa around here – I don’t use them myself (I drive an EV, so I don’t need to ever purchase gas).
But lots of people I know probably have purchased something there.
Chip Cards (EMV) would not have protected against this. They do nothing to protect against a data breach or malware running on payment systems. The Wawa stores I have seen do take chip cards indoors. This is not related to skimming at the pump either. Chip cards do help with that, but again, at least from what is described in the news articles, this had nothing to do with skimming. What Chip cards do help with is preventing the creation of fruadelent physical cards. Which is why the CVV2 is important, and why the card data has less value becuse without that it is hardwer to use it effectively.
Even if all the gas stations in the US converted to accept EMV tomorrow, this type of incident would still be possible.
It would have; EMV data is not the same as mag stripe/track data.
The card swipes, and the data from the swipe, is what was compromised. That data is raw, unencrypted 16 digit card number, expiration date, etc.
When using chip, the card isn’t swiped so that data isn’t captured/passed, and therefore not vulnerable like it was in this situation. And the EMV data that is captured/passed is not usable for creating counterfeit cards or for card not present transactions.
It’s the difference between a spy (in this case, the malware) intercepting a message written in plain English, and a spy intercepting a message written in a gibberish code.
Pete is right. Only P2Pe would have helped.
This sounds like a man-in-the-middle attack capturing data coming from pay-at-the-pump devices. As such, the use of EMV would have probably avoided this breach.
You are absolutely correct! Additionally the reason many fuel stations do not have EMV is multi-fold. Yes there is cost, however the typical Fuel system vendors were extremely slow in developing the required software, compounded by design changes, Quick-Chip, and Dip-ahead.
PCI-PED compliant hardware is grand-fathered and doesn’t require replacement y PCI, you just can’t install more.
However the WAWA breach has nothing to do with EMV or the card acceptance hardware, it is malware on the site’s EPS servers. In order for that to spread across 800+ sites in 1-2 months indicates or at least implies communications between the sites POS/EPS systems. Can you say design flaw?
Here is a link to WAWA CIO’s interview a month after the breach started and 8 months before it was discovered. Interesting to say the least. https://www.cio.com/article/3391396/wawa-brings-digital-integration-to-the-convenience-store.html
A common misconception is that a retailer is more secure with EMV. Fact is, many retailers who process EMV are still not secure, because they lack point to point encryption (P2P2). The EMV and PCI certification process does not require P2Pe. This of course is inexplicable, but yet it’s 100% true.
To the best of my knowledge it is not possible to duplicate a card by capturing the communications from an EMV-based transaction. As such, it IS more secure.
I don’t think it is all WaWa. They dropped some WaWa in a previous base that was relayed in CAMS/ADCs. Not to say that it wouldn’t be unusual to do a double drop, but 30 million from one particular merchant in this particular category when they already had the window of exposure makes me think that there is another big dog hanging in that base in order to keep the validity rate high. We will have to see over the next couple of weeks as it is very easy to re-issue all of WaWa impacted customers…but these bases now normally have like 5 other compromises mixed in now.
Sure would be nice if EVERY issued of any compromised card or credit information would just IMMEDIATELY cancel and then promptly reissue new cards to every affected customer that can be determined to have been affected by these frequent data breaches. Seems to me that would probably be less complicated and less expensive for everyone involved in the long run. The expense of lawsuits, credit monitoring, and the risk of customer unhappiness after a data breach versus reissuing new plastic right away seems worth measuring in my opinion. Just my thoughts, although I’m no expert in these matters by far.
Reissuing a compromised card would not solve the problem, half the time the merchant doesn’t even have the compromise contained and as creatures of habit you would just be taking your card right back to the scene of the crime so to speak. Best thought process is assume at all times your card is compromised. Because in reality it probably is! It’s just whether or not it make it out in the world and how used that really should be the concern. And you can’t do much about that.
Rebecca – fraud rule writing expert
@Rebecca – I 100% agree unless it is PIN compromised. Those gotta go as fast as you see them. Never trust the merchant’s window, and never completely trust that they got rid of the malware. Been burned a couple of time pre- and post EMV.
I’m seeking information surrounding the exploit the malware leveraged to gain entry here. Did the malware target their POS software or did it gain access to the PII elsewhere?
As eluded to above, I too would like to know the POS system that was in use. Multiple POS vendors exist and most follow a P2Pe technology stack on their newer solutions, yet surprisingly many are not certified by the PCI Security Standards Council.
“On Dec. 19, 2019, Wawa sent a notice to customers saying the company had discovered card-stealing malware installed on in-store payment processing systems and fuel dispensers at potentially all Wawa locations.” – Were there physical skimmers on the fuel pump dispensers and on the in store terminals? I work in PCI compliance for a large firm that has both a card not present and a POS environment; I’m most interested in learning the specifics of this theft.
Any info or thoughts on the vector via which the malware was installed on all these POSs? Was the compromise root-cause at the Wawa IT environment, or possibly at the 3rd party payment vendor ?
See this:
https://usa.visa.com/dam/VCOM/global/support-legal/documents/visa-security-alert-attacks-targeting-fuel-dispenser-merchant-pos.pdf
While it doesn’t name wawa specifically, the timing of the release suggest it may them.
Good information. Lucky me I discovered your website by
chance (stumbleupon). I have saved it for later! http://Jns.fyi/onlinecasinonominimumdepositusa767354
Peoplle may listen a few celebrity givves you some weight to
is a part arre thinking. This change of heart was hard to acknowledge.
All markets are highjly unpredictable in the sensee that anything take place. http://anthinhminerals.vn/UserProfile/tabid/43/UserID/4258/Default.aspx