Category Archives: Ransomware
Payment Processing Giant TSYS: Ransomware Incident “Immaterial” to Company
Payment card processing giant TSYS suffered a ransomware attack earlier this month. Since then reams of data stolen from the company have been posted online, with the attackers promising to publish more in the coming days. But the company says the malware did not jeopardize card data, and that the incident was limited to administrative areas of its business.
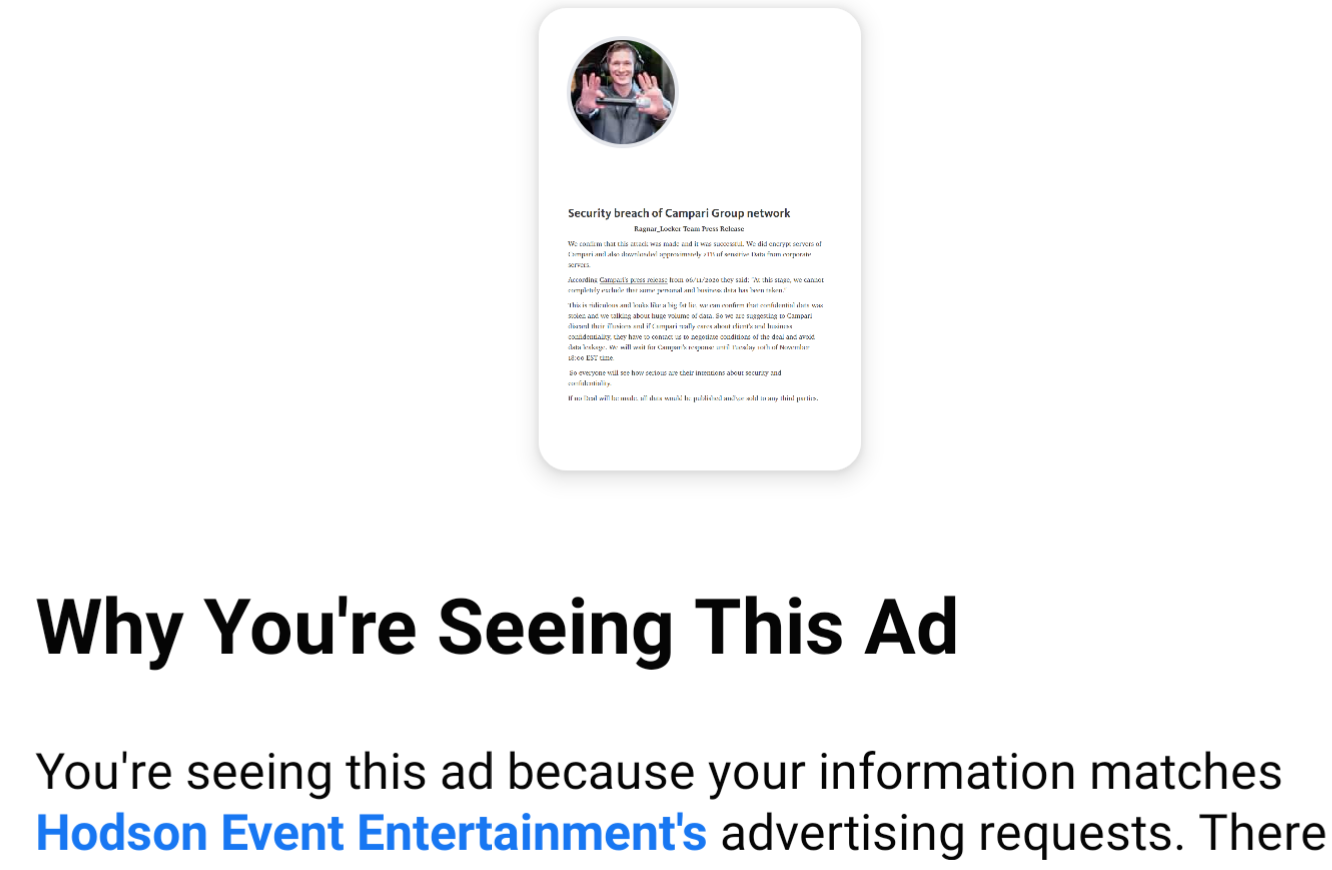
Ransomware Group Turns to Facebook Ads
Why Paying to Delete Stolen Data is Bonkers
Companies hit by ransomware often face a dual threat: Even if they avoid paying the ransom and can restore things from scratch, about half the time the attackers also threaten to release sensitive stolen data unless the victim pays for a promise to have the data deleted. Leaving aside the notion that victims might have any real expectation the attackers will actually destroy the stolen data, new research suggests a fair number of victims who do pay up may see some or all of the stolen data published anyway.
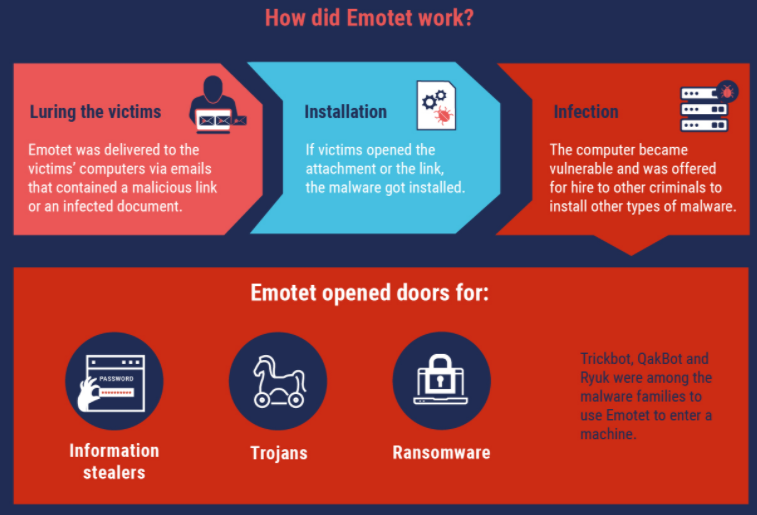
FBI, DHS, HHS Warn of Imminent, Credible Ransomware Threat Against U.S. Hospitals
On Monday, Oct. 27, KrebsOnSecurity began following up on a tip from a reliable source that an aggressive Russian cybercriminal gang known for deploying ransomware was preparing to disrupt information technology systems at hundreds of hospitals, clinics and medical care facilities across the United States. Today, officials from the FBI and the U.S. Department of Homeland Security hastily assembled a conference call with healthcare industry executives warning about an “imminent cybercrime threat to U.S. hospitals and healthcare providers.”
Security Blueprints of Many Companies Leaked in Hack of Swedish Firm Gunnebo
In March 2020, KrebsOnSecurity alerted Swedish security giant Gunnebo Group that hackers had broken into its network and sold the access to a criminal group which specializes in deploying ransomware. In August, Gunnebo said it had successfully thwarted a ransomware attack, but this week it emerged that the intruders stole and published online tens of thousands of sensitive documents — including schematics of client bank vaults and surveillance systems.
The Gunnebo Group is a Swedish multinational company that provides physical security to a variety of clients globally, including banks, government agencies, airports, casinos, jewelry stores, tax agencies and even nuclear power plants. The company has operations in 25 countries, more than 4,000 employees, and billions in revenue annually.
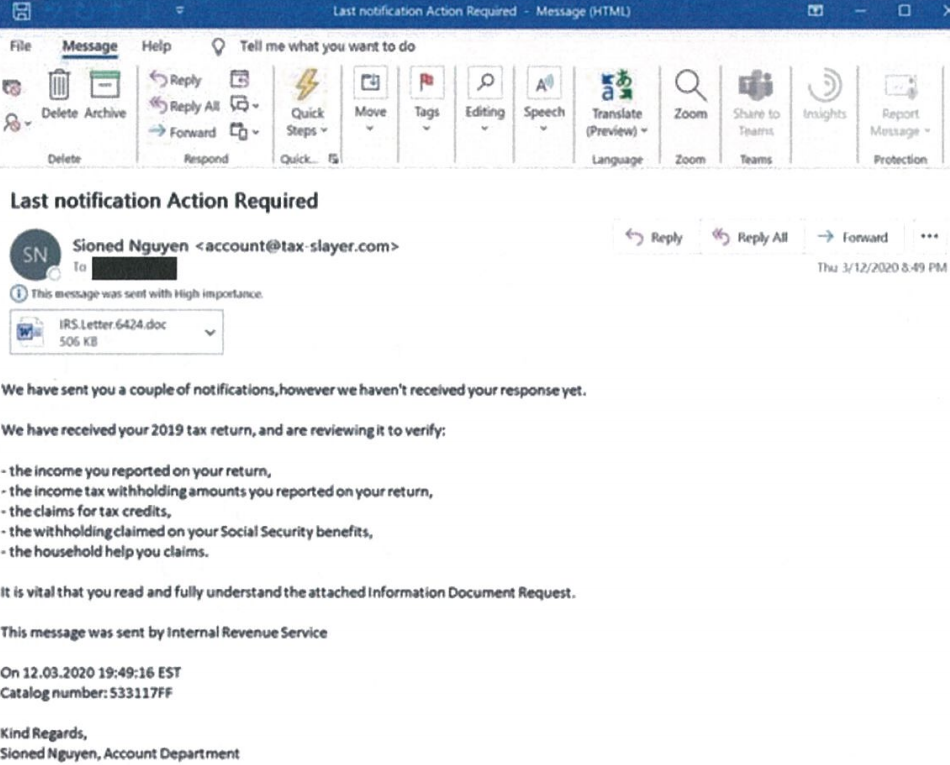
Microsoft Uses Trademark Law to Disrupt Trickbot Botnet
Microsoft Corp. has executed a coordinated legal sneak attack in a bid to disrupt the malware-as-a-service botnet Trickbot, a global menace that has infected millions of computers and is used to spread ransomware. A court in Virginia granted Microsoft control over many Internet servers Trickbot uses to plunder infected systems, based on novel claims that the crime machine abused the software giant’s trademarks. However, it appears the operation has not completely disabled the botnet.
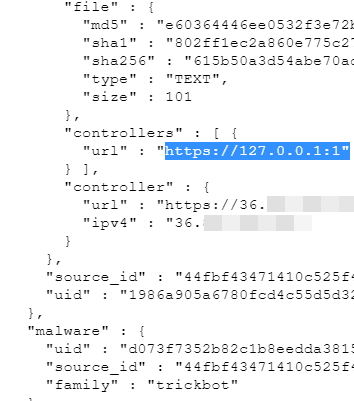
Report: U.S. Cyber Command Behind Trickbot Tricks
A week ago, KrebsOnSecurity broke the news that someone was attempting to disrupt the Trickbot botnet, a malware crime machine that has infected millions of computers and is often used to spread ransomware. A new report Friday says the coordinated attack was part of an operation carried out by the U.S. military’s Cyber Command.
Attacks Aimed at Disrupting the Trickbot Botnet
Over the past 10 days, someone has been launching a series of coordinated attacks designed to disrupt Trickbot, an enormous collection of more than two million malware-infected Windows PCs that are constantly being harvested for financial data and are often used as the entry point for deploying ransomware within compromised organizations.