Last week, KrebsOnSecurity broke the news of an ongoing credit card breach involving CiCi’s Pizza, a restaurant chain in the United States with more than 500 locations. What follows is an exclusive look at a point-of-sale botnet that appears to have enslaved dozens of hacked payment terminals inside of CiCi’s locations that are being relieved of customer credit card data in real time.
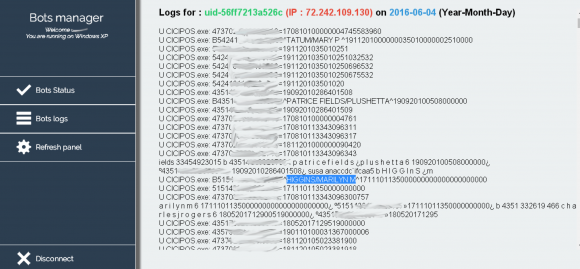
Over the weekend, I heard from a source who said that since November 2015 he’s been tracking a collection of hacked cash registers. This point-of-sale botnet currently includes more than 100 infected systems, and according to the administrative panel for this crime machine at least half of the compromised systems are running a malicious Microsoft Windows process called cicipos.exe.

This admin panel shows the Internet address of a number of infected point-of-sale devices as of June 4, 2016. Many of these appear to be at Cici’s Pizza locations.
KrebsOnSecurity has not been able to conclusively tie the botnet to CiCi’s. Neither CiCi’s nor its outside public relations firm have responded to multiple requests for comment. However, the control panel for this botnet includes the full credit card number and name attached to the card, and several individuals whose names appeared in the botnet control panel confirmed having eaten at CiCi’s Pizza locations on the same date that their credit card data was siphoned by this botnet.
Among those was Richard Higgins of Prattville, Ala., whose card data was recorded in the botnet logs on June 4, 2016. Reached via phone, Higgins confirmed that he used his debit card to pay for a meal he and his family enjoyed at a CiCi’s location in Prattville on that same date.
An analysis of the botnet data reveals more than 100 distinct infected systems scattered across the country. However, the panel only displayed hacked systems that were presently reachable online, so the actual number of infected systems may be larger.
Most of the hacked cash registers map back to dynamic Internet addresses assigned by broadband Internet service providers, and those addresses provide little useful information about the owners of the infected systems — other than offering a general idea of the city and state tied to each address.
For example, the Internet address of the compromised point-of-sale system that stole Mr. Higgins’ card data is 72.242.109.130, which maps back to an Earthlink system in a pool of IP addresses managed out of Montgomery, Ala.
Many of the botnet logs include brief notes or messages apparently left by CiCi’s employees for other employees. Most of these messages concern banal details about an employee’s shift, or issues that need to be addressed when the next employee shift comes in to work. Continue reading




 Over the past two months, KrebsOnSecurity has received inquiries from fraud fighters at more than a half-dozen financial institutions in the United States — all asking if I had any information about a possible credit card breach at CiCi’s. Every one of these banking industry sources said the same thing: They’d detected a pattern of fraud on cards that all had all been used in the last few months at various CiCi’s Pizza locations.
Over the past two months, KrebsOnSecurity has received inquiries from fraud fighters at more than a half-dozen financial institutions in the United States — all asking if I had any information about a possible credit card breach at CiCi’s. Every one of these banking industry sources said the same thing: They’d detected a pattern of fraud on cards that all had all been used in the last few months at various CiCi’s Pizza locations.

![The sales thread on exploit[dot]in.](https://krebsonsecurity.com/wp-content/uploads/2016/05/buggicorp-580x255.png)


 Over the past weekend, KrebsOnSecurity began hearing from sources at multiple financial institutions who said they’d detected a pattern of fraudulent charges on customer cards that were used at various Noodles & Company locations between January 2016 and the present.
Over the past weekend, KrebsOnSecurity began hearing from sources at multiple financial institutions who said they’d detected a pattern of fraudulent charges on customer cards that were used at various Noodles & Company locations between January 2016 and the present. The 2012 breach was first exposed when a hacker posted a list of some 6.5 million unique passwords to a popular forum where members volunteer or can be hired to hack complex passwords. Forum members managed to crack some the passwords, and eventually noticed that an inordinate number of the passwords they were able to crack contained some variation of “linkedin” in them.
The 2012 breach was first exposed when a hacker posted a list of some 6.5 million unique passwords to a popular forum where members volunteer or can be hired to hack complex passwords. Forum members managed to crack some the passwords, and eventually noticed that an inordinate number of the passwords they were able to crack contained some variation of “linkedin” in them.