Norse Corp., a Foster City, Calif. based cybersecurity firm that has attracted much attention from the news media and investors alike this past year, fired its chief executive officer this week amid a major shakeup that could spell the end of the company. The move comes just weeks after the company laid off almost 30 percent of its staff.
Sources close to the matter say Norse CEO Sam Glines was asked to step down by the company’s board of directors, with board member Howard Bain stepping in as interim CEO. Those sources say the company’s investors have told employees that they can show up for work on Monday but that there is no guarantee they will get paid if they do.
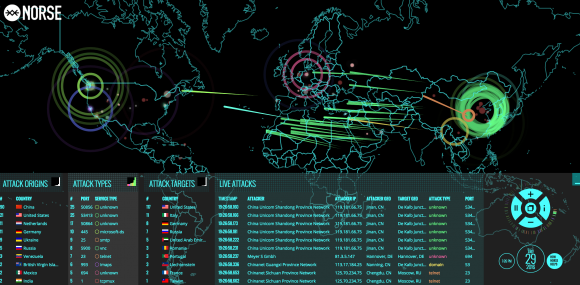
A snapshot of Norse’s semi-live attack map.
Glines agreed earlier this month to an interview with KrebsOnSecurity but later canceled that engagement without explanation. Bain could not be immediately reached for comment.
Two sources at Norse said the company’s assets will be merged with Irvine, Ca. based networking firm SolarFlare, which has some of the same investors and investment capital as Norse. Neither Norse nor SolarFlare would comment for this story. Update, Feb. 1, 12:34 p.m. ET: SolarFlare CEO Russell Stern just pinged me to say that “there has been no transaction between Norse and SolarFlare.”
Original story: The pink slips that Norse issued just after New Years’s Day may have come as a shock to many employees, but perhaps the layoffs shouldn’t have been much of a surprise: A careful review of previous ventures launched by the company’s founders reveals a pattern of failed businesses, reverse mergers, shell companies and product promises that missed the mark by miles.
EYE CANDY
In the tech-heavy, geek-speak world of cybersecurity, infographics and other eye candy are king because they promise to make complicated and boring subjects accessible and sexy. And Norse’s much-vaunted interactive attack map is indeed some serious eye candy: It purports to track the source and destination of countless Internet attacks in near real-time, and shows what appear to be multicolored fireballs continuously arcing across the globe.
Norse says the data that feeds its online attack map come from a network of more than eight million online “sensors” — honeypot systems that the company has strategically installed at Internet properties in 47 countries around the globe to attract and record malicious and suspicious Internet traffic.
According to the company’s marketing literature, Norse’s sensors are designed to mimic a broad range of computer systems. For example, they might pretend to be a Web server when an automated attack or bot scans the system looking for Web server vulnerabilities. In other cases, those sensors might watch for Internet attack traffic that would typically only be seen by very specific machines, such as devices that manage complex manufacturing systems, power plants or other industrial control systems.
Several departing and senior Norse employees said the company’s attack data was certainly voluminous enough to build a business upon — if not especially sophisticated or uncommon. But most of those interviewed said Norse’s top leadership didn’t appear to be interested in or capable of building a strong product behind the data. More worryingly, those same people said there are serious questions about the validity of the data that informs the company’s core product.
UP IN SMOKE(S)
Norse Corp. and its fundamental technology arose from the ashes of several companies that appear to have been launched and then acquired by shell companies owned by Norse’s top executives — principally the company’s founder and chief technology officer Tommy Stiansen. Stiansen did not respond to multiple requests for comment.
This acquisition process, known as a “reverse merger” or “reverse takeover,” involves the acquisition of a public company by a private company so that the private company can bypass the lengthy and complex process of going public.
Reverse mergers are completely legal, but they can be abused to hide the investors in a company and to conceal certain liabilities of the acquired company, such as pending lawsuits or debt. In 2011, the U.S. Securities and Exchange Commission (SEC) issued a bulletin cautioning investors about plunking down investments in reverse mergers, warning that they may be prone to fraud and other abuses.
The founders of Norse Corp. got their start in 1998 with a company called Cyco.net (pronounced “psycho”). According to a press release issued at the time, “Cyco.net was a New Mexico based firm established to develop a network of cyber companies.”
“This site is a lighthearted destination that will be like the ‘People Magazine’ of the Internet,” said Richard Urrea, Cyco’s CEO, in a bizarre explanation of the company’s intentions. “This format has proven itself by providing Time Warner with over a billion dollars of ad revenue annually. That, combined with the CYCO.NET’s e-commerce and various affiliations, such as Amazon.com, could amount to three times that figure. Not a portal like Yahoo, the CYCO.NET will serve as the launch pad to rocket the Internet surfer into the deepest reaches of cyberspace.”
In 2003, Cyco.net acquired Orion Security Services, a company founded by Stiansen, Norse’s current CTO and founder and the one Norse executive who is actually from Norway. Orion was billed as a firm that provides secure computer network management solutions, as well as video surveillance systems via satellite communications.
The Orion acquisition reportedly came with $20 million in financing from a private equity firm called Cornell Capital Partners LP, which listed itself as a Cayman Islands exempt limited partnership whose business address was in Jersey City, NJ.
Cornell later changed its name to Yorkville Advisors, an entity that became the subject of an investigation by the U.S. Securities and Exchange Commission (SEC) and a subsequent lawsuit in which the company was accused of reporting “false and inflated values.”
Despite claims that Cyco.net was poised to “rocket into the deepest riches of cyberspace,” it somehow fell short of that destination and ended up selling cigarettes online instead. Perhaps inevitably, the company soon found itself the target of a lawsuit by several states led by the Washington state attorney general that accused the company of selling tobacco products to minors, failing to report cigarette sales and taxes, and for falsely advertising cigarettes as tax-free.
COPYRIGHT COPS
In 2005, Cyco.net changed its name to Nexicon, but only after acquiring by stock swap another creation by Stiansen — Pluto Communications — a company formed in 2002 and whose stated mission was to provide “operational billing solutions for telecom networks.” Again, Urrea would issue a press release charting a course for the company that would have almost no bearing on what it actually ended up doing.
“We are very excited that the transition from our old name and identity is now complete, and we can start to formally reposition our Company under the new brand name of Nexicon,” Urrea said. “After the divestiture of our former B2C company in 2003, we have laid the foundation for our new business model, offering all-in-one or issue-specific B2B management solutions for the billing, network control, and security industries.”
In June 2008, Sam Glines — who would one day become CEO of Norse Corp. — joined Nexicon and was later promoted to chief operating officer. By that time, Nexicon had morphed itself into an online copyright cop, marketing a technology they claimed could help detect and stop illegal file-sharing. The company’s “GetAmnesty” technology sent users a pop-up notice explaining that it was expensive to sue the user and even more expensive for the user to get sued. Recipients of these notices were advised to just click the button displayed and pay for the song and all would be forgiven.
In November 2008, Nexicon was acquired by Priviam, another shell company operated by Stiansen and Nexicon’s principals. Nexicon went on to sign Youtube.com and several entertainment studios as customers. But soon enough, reports began rolling in of rampant false-positives — Internet users receiving threatening legal notices from Nexicon that they were illegally sharing files when they actually weren’t. Nexicon/Priviam’s business began drying up, and it’s stock price plummeted.
In September 2011, the Securities and Exchange Commission revoked the company’s ability to trade its penny stock (then NXCO on the pink sheets), noting that the company had failed to file any periodic reports with the SEC since its inception. In June 2012, the SEC also revoked Priviam’s ability to trade its stock, citing the same compliance failings that led to the de-listing of Nexicon.
By the time the SEC revoked Nexicon’s trading ability, the company’s founders were already working to reinvent themselves yet again. In August 2011, they raised $50,000 in seed money from Capital Innovators to jump-start Norse Corp. A year later, Norse received $3.5 million in debt refinancing, and in December 2013 got its first big infusion of cash — $10 million from Oak Investment Partners. In September 2015, KPMG invested $11.4 million in the company.
Several former employees say Stiansen’s penchant for creating shell corporations served him well in building out Norse’s global sensor network. Some of the sensors are in countries where U.S. assets are heavily monitored, such as China. Those same insiders said Norse’s network of shell corporations also helped the company gain visibility into attack traffic in countries where it is forbidden for U.S. firms to do business, such as Iran and Syria. Continue reading →
 One big critical update from Redmond mends more than a dozen security problems with Internet Explorer. Another critical patch addresses flaws Microsoft Edge — including four that appear to share the same vulnerability identifiers (meaning Microsoft re-used the same vulnerable IE code in its newest Edge browser). Security vendor Qualys as usual has a good roundup of the rest of the critical Microsoft updates.
One big critical update from Redmond mends more than a dozen security problems with Internet Explorer. Another critical patch addresses flaws Microsoft Edge — including four that appear to share the same vulnerability identifiers (meaning Microsoft re-used the same vulnerable IE code in its newest Edge browser). Security vendor Qualys as usual has a good roundup of the rest of the critical Microsoft updates.





 According to Oracle, some 97 percent of enterprise computers and a whopping 89 percent of desktop systems in the U.S. run some form of Java. This has made Java JRE (the form of Java that runs most commonly on end-user systems) a prime target of malware authors.
According to Oracle, some 97 percent of enterprise computers and a whopping 89 percent of desktop systems in the U.S. run some form of Java. This has made Java JRE (the form of Java that runs most commonly on end-user systems) a prime target of malware authors.

 Bob Bertini, spokesperson for the Dublin, Ohio-based restauranteur, said the company began receiving reports earlier this month from its payment industry contacts about a potential breach and that Wendy’s has hired a security firm to investigate the claims.
Bob Bertini, spokesperson for the Dublin, Ohio-based restauranteur, said the company began receiving reports earlier this month from its payment industry contacts about a potential breach and that Wendy’s has hired a security firm to investigate the claims.