Adobe has issued a patch to fix a zero-day vulnerability in its Flash Player software. Separately, Oracle today released an update to plug more than two-dozen flaws in its Java software. Both programs plug directly into the browser and are highly targeted by malicious software and malefactors. Although Flash and Java are both widely installed, most users could probably ditch each program with little to no inconvenience or regret. Continue reading
Don’t Be Fooled by Fake Online Reviews Part II
In July I wrote about the dangers of blindly trusting online reviews, especially for high-dollar services like moving companies. That piece told the story of Full Service Van Lines, a moving company that had mostly five-star reviews online but whose owners and operators had a long and very public history of losing or destroying their customers’ stuff and generally taking months to actually ship what few damaged goods it delivered. Last week, federal regulators shut the company down.
 NBC Miami reports that Full Service Van Lines (FSVL) was shut down by the U.S. Department of Transportation, but not because of consumer complaints. The DOT reportedly revoked the company’s license due to a pattern of safety violations. And that’s saying something: The NBC story said FSVL received more complaints this year than any other Florida mover of its size.
NBC Miami reports that Full Service Van Lines (FSVL) was shut down by the U.S. Department of Transportation, but not because of consumer complaints. The DOT reportedly revoked the company’s license due to a pattern of safety violations. And that’s saying something: The NBC story said FSVL received more complaints this year than any other Florida mover of its size.
My July story on FSVL concluded that the company’s owners likely inflated and manipulated their online reputation via a search engine optimization (SEO) firm they owned. Unfortunately, this practice is incredibly common among labor-intensive services that do not require the customer to come into the company’s offices but instead come to the consumer. These services include but are not limited to locksmiths, windshield replacement services, garage door repair and replacement technicians, carpet cleaning and other services that consumers very often call for immediate service.
Bryan Seely, a security expert who’s working on an as-yet unpublished book on these so-called dark/black SEO practices, said such services are rife for SEO experts who create hundreds or thousands of phantom companies online with different business names, addresses and phone numbers. The calls to each of these phony firms are eventually all routed back to the SEO company, which sells the customer lead to one of several companies that have agreed in advance to buy such business leads.
As a result, many consumers think they are dealing with one company when they call, yet end up being serviced by a completely unrelated firm that may not have to worry about maintaining a reputation for quality and fair customer service. Continue reading
Adobe, Microsoft Push Critical Security Fixes
Adobe and Microsoft on Tuesday each released security updates to remedy critical vulnerabilities in their software. Adobe pushed patches to plug at least 56 security holes present in Adobe Reader and Acrobat, as well as a fix for Flash Player that corrects 13 flaws. Separately, Microsoft issued six update bundles to address at least 33 security problems in various versions of Windows, Microsoft Office and other software.
Three of the patches Microsoft issued earned the company’s most dire “critical” rating, meaning they could be exploited by hackers or malware to take complete control over vulnerable systems without any help from users. According to security firm Shavlik, four of the flaws involve vulnerabilities that were publicly disclosed by someone other than Microsoft prior to this week. The implication here is that malware writers may have had a head start figuring out ways to exploit several of these flaws, so it’s probably best not to let too much grass grow under your feet before applying this month’s updates. Continue reading
Hacker Who Sent Me Heroin Faces Charges in U.S.
A Ukrainian hacker who once hatched a plot to have heroin sent to my Virginia home and then alert police when the drugs arrived had his first appearance in a U.S. court today, after being extradited to the United States to face multiple cybercrime charges.
Sergey Vovnenko, a.k.a. “Fly,” “Flycracker” and “MUXACC1” (muxa is transliterated Russian for “муха” which means “fly”), was set to appear in a Newark courtroom today on charges of stealing and selling credit card and banking data, emptying bank accounts, and running a botnet of more than 12,000 hacked computers and servers, among other alleged crimes.
I first became acquainted with Fly in 2013, when his Twitter persona (warning: images here may not be safe for work) began sending me taunting tweets laced with epithets and occasional attempts to get me to click dodgy-looking Web links. Fly also took to his Livejournal blog to post copies of my credit report, directions to my home and pictures of my front door.
After consulting with cybercrime researchers at Russian security firm Group-IB, I learned that Fly was the administrator of a closely-guarded but now-defunct cybercrime forum dedicated to financial fraud called thecc[dot]bz (“cc” is a reference to credit cards).
Not long after that, I secretly gained access to his forum. And none too soon: In one lengthy discussion thread on the forum, I found that Fly had solicited donations from fellow fraudsters on the forum to donate Bitcoin currency for a slush fund Fly created for the express purpose of purchasing heroin off of the Silk Road — which was at the time the leading source of illicit drugs on the Dark Web.
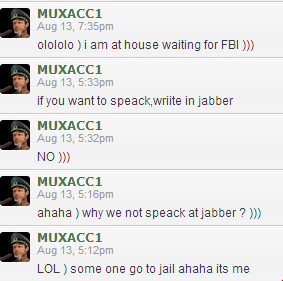
Fly’s plan was simple: Have the drugs delivered to my home in my name, and then spoof a call from one of my neighbors to the local police informing them that I was a druggie, that I had druggie friends coming in and out of my house all day long, and that I was even having drugs delivered to my home.
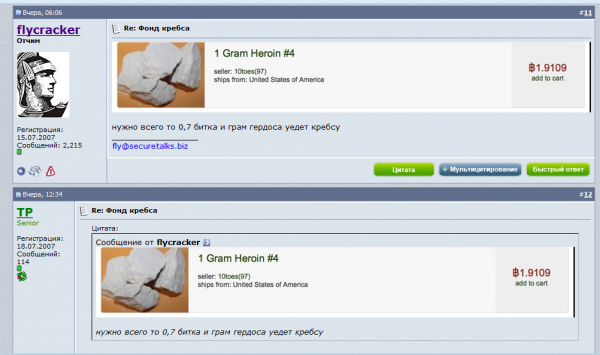
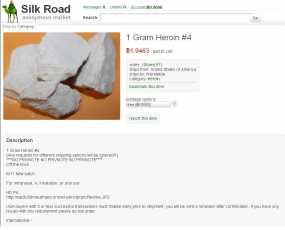
The forum members took care to find the most reputable sellers of heroin on the Silk Road. After purchasing a gram of the stuff from the Silk Road’s top smack seller — a drug dealer who used the nickname “Maestro” — Fly posted the USPS tracking link for the package into the discussion thread on his forum.
At that point, I called the local police and had a cop come out to take an official police report. The officer asked me to contact him again if the drugs actually arrived. Three days later, our local Postal Service carrier hand delivered a thin USPS Express Mail envelope that was postmarked from Chicago. Inside was another blank envelope containing a May 2013 copy of Chicago Confidential, a weekly glossy magazine from the Chicago Tribune.
On the back of the magazine, taped to a full-page ad for jewelry from LesterLampert, were a baker’s dozen individually wrapped packets emblazoned with the same black and gold skull motif that was on Maestro’s Silk Road ad. I immediately contacted the police, who came and dutifully retrieved the drugs, which turned out to be almost pure heroin.
I wrote about the experience of foiling Fly’s plan in a story titled Mail From the (Velvet) Cybercrime Underground. This did not sit well with Fly, who was made to look bad in front of his forum members who’d contributed roughly two Bitcoins to the scheme.
Angry that I’d foiled his plan to have me arrested for drug possession, Fly had a local florist send a gaudy floral arrangement in the shape of a giant cross to my home, complete with a menacing message that addressed my wife and was signed, “Velvet Crabs.”
After this incident, I became intensely curious about the identity of this Fly individual, so I began looking through databases of hacked carding and cybercrime forums. My first real break came when Group-IB provided a key piece of the puzzle: Group-IB researchers found that on the now-defunct vulnes[dot]com, Fly maintained an account under the nickname Flycracker, and signed up with the email address mazafaka@libero.it(.it is the country code for Italy).
According to a trusted source in the security community, that email account was somehow compromised in 2013. The source said the account was full of emailed reports from a keylogging device that was tied to another email address — 777flyck777@gmail.com (according to Google, mazafaka@libero.it is the recovery email address for 777flyck777@gmail.com).
Those keylog reports contained some valuable information, and indicated that Fly had planted a keylogger on his then-fiancee Irina’s computer. On several occasions, those emails show Fly’s wife typed in her Gmail address, which included her real first and last name — Irina Gumenyuk. Continue reading
Arrest of Chinese Hackers Not a First for U.S.
The Washington Post reported last week that the Chinese government has quietly arrested a handful of hackers at the urging of the U.S. government, a move described as “an unprecedented step to defuse tensions with Washington at a time when the Obama administration has threatened economic sanctions.” While this a welcome and encouraging development, it is not the first time Beijing has arrested Chinese hackers in response to pressure from the U.S. government.
The action reported by The Post and other media outlets came shortly before Chinese President Xi Jinping’s state visit to Washington late last month. The hackers arrested had reportedly been identified by U.S. officials as having stolen commercial secrets from U.S. firms to be sold or passed along to Chinese state-run companies.
Although The Post has described this action as unprecedented, U.S. government cybercrime investigators have had success convincing Chinese authorities to take such actions in at least one other case previously.
In a report (PDF) presented to Congress on Feb. 29, 2012, the Office of Inspector General for the National Aeronautics and Space Administration (NASA) noted that a lengthy investigation into the cyber theft of sensitive technical data from its systems culminated in the arrest of a Chinese national in China.
“As a result of an OIG investigation and lengthy international coordination efforts, a
Chinese national was detained in December 2010 by Chinese authorities for violations of
Chinese Administrative Law,” NASA Inspector General Paul K. Martin told a House oversight committee. “This case resulted in the first confirmed detention of a Chinese national for hacking activity targeting U.S. Government agencies. Seven NASA systems, many containing export-restricted technical data, were compromised by the Chinese national.” Continue reading
Credit Card Breach at America’s Thrift Stores
Another charity store chain has been hacked: America’s Thrift Stores, an organization that operates donations-based thrift stores throughout the southeast United States, said this week that it recently learned it was the victim of a malware-driven security breach that targeted software used by a third-party service provider.
 “This breach allowed criminals from Eastern Europe unauthorized access to some payment card numbers,” the company’s CEO said in a statement. “This virus/malware, is one of several infecting retailers across North America.”
“This breach allowed criminals from Eastern Europe unauthorized access to some payment card numbers,” the company’s CEO said in a statement. “This virus/malware, is one of several infecting retailers across North America.”
The statement continues:
“The U.S. Secret Service tells us that only card numbers and expiration dates were stolen. They do not believe any customer names, phone numbers, addresses or email addresses were compromised. This breach may have affected sales transactions between September 1, 2015 and September 27, 2015. If you used your credit or debit card during this time to purchase an item at any America’s Thrift Store location, the payment card number information on your card may have been compromised.”
Nevertheless, several banking sources say they have seen a pattern of fraud on cards all used at America’s Thrift Stores locations indicating that thieves have been able to use the data stolen from the compromised point-of-sale devices to counterfeit new cards.
Founded in 1984, America’s Thrift Stores is a for-profit thrift store and operates in the southeastern United States. The company is headquartered in Birmingham, Alabama and operates stores in Alabama, Georgia, Tennessee, Mississippi and Louisiana. According to the company’s site, the organization employs over 1,000 employees and pays over $4 million to its non- profit partners annually, as it turns donated items into revenue for their missions.
The breach involving America’s Thrift Stores comes on the heels of a similar incident at Goodwill last year. That incident was tied back to security weaknesses at third-party payment vendor C&K Systems, although there is no indication yet which third-party service provider may be at fault in the America’s Thrift Stores breach.
At Experian, Security Attrition Amid Acquisitions
T-Mobile disclosed last week that some 15 million customers had their Social Security numbers and other personal data stolen thanks to a breach at Experian, the largest of the big American consumer credit bureaus. But this actually wasn’t the first time that a hacking incident at Experian exposed sensitive T-Mobile customer data, and that previous breach may hold important clues about what went wrong more recently.
On Dec. 30, 2013, T-Mobile said it notified a “relatively small” number of customers that unauthorized access to a file stored on servers owned by Experian had exposed Social Security numbers and driver’s license numbers. The mobile provider identified the breached vendor as Decisioning Solutions, an identity-proofing and authentication company that was acquired by Experian in April 2013. We’ll revisit this acquisition in a few moments.
Over the past week, KrebsOnSecurity has interviewed a half-dozen security experts who said they recently left Experian to find more rewarding and less frustrating work at other corporations. Nearly all described Experian as a company fixated on acquiring companies in the data broker and analytics technology space, even as it has stymied efforts to improve security and accountability at the Costa Mesa, Calif. based firm.
Jasun Tate worked for a year until April 2014 as a chief information security officer delegate and risk consultant at Experian’s government services and e-marketing business units. Tate said he and several of his colleagues left last year after repeatedly running into problems getting buy-in or follow-up support for major projects to beef up security around Experian’s growing stable of companies handling sensitive consumer and government data.
“What the board of directors at Experian wanted security-wise and the security capabilities on the ground were two completely different things,” Tate said. “Senior leadership there said they were pursuing a very aggressive growth-by-acquisition campaign. The acquisition team would have a very strict protocol on how they assess whether a business may be viable to buy, but the subsequent integration of the business into our core security architecture was just a black box of magic in terms of how it was to be implemented. And I’m not saying successful magic at all.”
Another recent former security employee at Experian who agreed to talk on condition of anonymity said it was clear that the company’s board was not well-informed about the true state of security within the company’s various business units.
“When I was there, the board was very big on security and wanting to invest in it and make sure we were doing what we needed to do in order to avoid situations just like this,” the source said. “In my opinion, there’s no way the board was told the whole story, because if they had been then things wouldn’t be where they are are now. We wouldn’t be talking about this. Some things had to have been hidden or spun in a way to look positive somehow.”
BLACK BOX MAGIC
Not long after it acquired the above-mentioned Decisioning Solutions in April 2013, Experian folded the company into its Decision Analytics platform — a unit which provides credit and noncredit data, customer analytics and fraud detection to lenders, cable and satellite companies, telecommunications firms, third-party debt collectors, utilities and to state and federal government entities.
Within hours of the latest T-Mobile breach news hitting the wires, KrebsOnSecurity was contacted by an anonymous source who sent this author a Web link that, when clicked, opened up a support ticket within that Decision Analytics platform in the United Kingdom — with absolutely no authentication needed. That support ticket I viewed appears to have been filed by someone in an office cube at Experian’s data center in Costa Rica who was requesting hardware support for a component of the company’s Global Technology Services division.
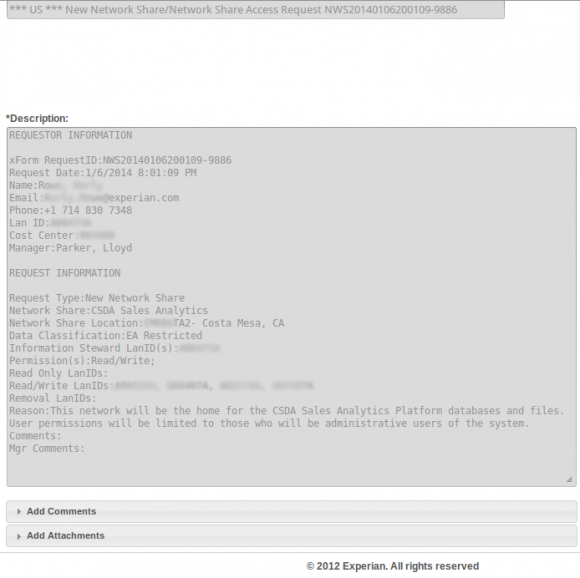
Countless internal support requests for access to Experian’s Decision Analytics credit information platform were exposed to the Internet without authentication until earlier this week.
That particular support ticket was relatively uninteresting, but according to my source anyone could view countless other support tickets filed via the support portal for Experian’s Decision Analytics platform.
The same source demonstrated how modifying just one or two numbers at the tail end of that link revealed requests for access to networked file shares from across a range of Experian’s business units. The requests included specific names of network shares, usernames, userIDs, and LanIDs, as well as email addresses, phone numbers of Experian personnel requesting and approving the changes.
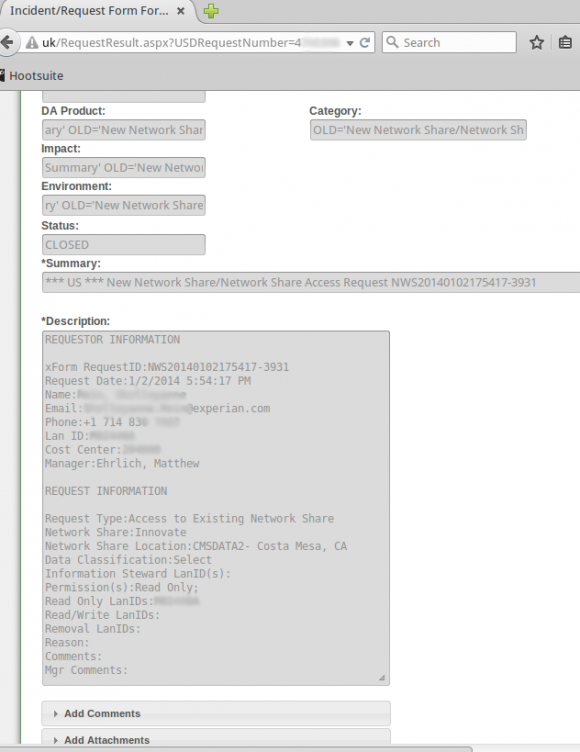
Countless internal support requests for access to Experian’s Decision Analytics credit information platform were exposed to the Internet without authentication until earlier this week.
The support site also apparently allowed anyone to file support tickets, potentially making it easy for clever attackers who’d studied the exposed support tickets to fabricate a request for access to Experian resources or accounts on the system.
In addition, experts I spoke with who examined the portal said the support site allowed anyone to upload arbitrary file attachments of virtually any file type. Those experts said such file upload capabilities are notoriously easy for attackers to use to inject malicious files into databases and other computing environments, and that having such capability out in the open without at least first requiring users to supply valid username and password credentials is asking for trouble.
KrebsOnSecurity sought comment from Experian to find out if it knew that its Decision Analytics support portal allowed anyone to view the tickets within. The company said in a statement that it had disabled the portal in response to what appeared to be unauthorized access to it and had notified law enforcement.
“We take any unauthorized access to our systems very seriously, and when we detected the unauthorized activities, we shut down the website and notified law enforcement,” the company said in a statement. “Our credit database and core infrastructure were not impacted – nor could they be accessed through this website. This site was a legacy version of a service to enable clients and internal users to create and log tickets for issues they may have and we had already deployed its replacement solution.” Continue reading
What’s in a Boarding Pass Barcode? A Lot
The next time you’re thinking of throwing away a used boarding pass with a barcode on it, consider tossing the boarding pass into a document shredder instead. Two-dimensional barcodes and QR codes can hold a great deal of information, and the codes printed on airline boarding passes may allow someone to discover more about you, your future travel plans, and your frequent flyer account.
Earlier this year, I heard from a longtime KrebsOnSecurity reader named Cory who said he began to get curious about the data stored inside a boarding pass barcode after a friend put a picture of his boarding pass up on Facebook. Cory took a screen shot of the boarding pass, enlarged it, and quickly found a site online that could read the data.

An older Delta boarding pass with a bar code that does not include a frequent flyer number. Source: IATA.
“I found a website that could decode the data and instantly had lots of info about his trip,” Cory said, showing this author step-by-step exactly how he was able to find this information. ‘
“Besides his name, frequent flyer number and other [personally identifiable information], I was able to get his record locator (a.k.a. “record key” for the Lufthansa flight he was taking that day,” Cory said. “I then proceeded to Lufthansa’s website and using his last name (which was encoded in the barcode) and the record locator was able to get access to his entire account. Not only could I see this one flight, but I could see ANY future flights that were booked to his frequent flyer number from the Star Alliance.”
The access granted by Lufthansa’s site also included his friend’s phone number, and the name of the person who booked the flight. More worrisome, Cory now had the ability to view all future flights tied to that frequent flyer account, change seats for the ticketed passengers, and even cancel any future flights.
The information contained in the boarding pass could make it easier for an attacker to reset the PIN number used to secure his friend’s Star Alliance frequent flyer account. For example, that information gets you past the early process of resetting a Star Alliance account PIN at United Airline’s “forgot PIN” Web site. Continue reading
Trump Hotel Collection Confirms Card Breach
The Trump Hotel Collection, a string of luxury hotel properties tied to business magnate and Republican presidential candidate Donald Trump, said last week that a year-long breach of its credit card system may have resulted in the theft of cards used at the hotels. The acknowledgement comes roughly three months after this author first reported that multiple financial institutions suspected the hotels were compromised.
In a Web site created to share details about the hack, The Trump Hotel Collection said the breach affects customers who used their credit or debit cards at the hotels between May 19, 2014, and June 2, 2015.
“While the independent forensic investigator did not find evidence that information was taken from the Hotel’s systems, it appears that there may have been unauthorized malware access to payment card information as it was inputted into the payment card systems. Payment card data (including payment card account number, card expiration date, and security code) of individuals who used a payment card at the Hotel between May 19, 2014, and June 2, 2015, may have been affected.
The Trump compromise is just the latest in a long string of credit card breaches involving hotel brands, restaurants and retail establishments. In March, upscale hotel chain Mandarin Oriental disclosed a compromise. The following month, hotel franchising firm White Lodging acknowledged that, for the second time in 12 months, card processing systems at several of its locations were breached by hackers.
On Sept. 25, this author first reported that the Hilton Hotel chain is investigating reports of a pattern of card fraud traced back to some of its properties.
Continue reading
Scottrade Breach Hits 4.6 Million Customers
Welcome to Day 2 of Cybersecurity (Breach) Awareness Month! Today’s awareness lesson is brought to you by retail brokerage firm Scottrade Inc., which just disclosed a breach involving contact information and possibly Social Security numbers on 4.6 million customers.
 In an email sent today to customers, St. Louis-based Scottrade said it recently heard from federal law enforcement officials about crimes involving the theft of information from Scottrade and other financial services companies.
In an email sent today to customers, St. Louis-based Scottrade said it recently heard from federal law enforcement officials about crimes involving the theft of information from Scottrade and other financial services companies.
“Based upon our subsequent internal investigation coupled with information provided by the authorities, we believe a list of client names and street addresses was taken from our system,” the email notice reads. “Importantly, we have no reason to believe that Scottrade’s trading platforms or any client funds were compromised. All client passwords remained encrypted at all times and we have not seen any indication of fraudulent activity as a result of this incident.”
The notice said that although Social Security numbers, email addresses and other sensitive data were contained in the system accessed, “it appears that contact information was the focus of the incident.” The company said the unauthorized access appears to have occurred over a period between late 2013 and early 2014.
Asked about the context of the notification from federal law enforcement officials, Scottrade spokesperson Shea Leordeanu said the company couldn’t comment on the incident much more than the information included in its Web site notice about the attack. But she did say that Scottrade learned about the data theft from the FBI, and that the company is working with agents from FBI field offices in Atlanta and New York. FBI officials could not be immediately reached for comment.
It may well be that the intruders were after Scottrade user data to facilitate stock scams, and that a spike in spam email for affected Scottrade customers will be the main fallout from this break-in.
In July 2015, prosecutors in Manhattan filed charges against five people — including some suspected of having played a role in the 2014 breach at JPMorgan Chase that exposed the contact information on more than 80 million consumers. The authorities in that investigation said they suspect that group sought to use email addresses stolen in the JPMorgan hacking to further stock manipulation schemes involving spam emails to pump up the price of otherwise worthless penny stocks.
Scottrade said despite the fact that it doesn’t believe Social Security numbers were stolen, the company is offering a year’s worth of free credit monitoring services to affected customers. Readers who are concerned about protecting their credit files from identity thieves should read How I Learned to Stop Worrying and Embrace the Security Freeze.