The Lizard Squad, a band of young hooligans that recently became Internet famous for launching crippling distributed denial-of-service (DDoS) attacks against the largest online gaming networks, is now advertising its own Lizard-branded DDoS-for-hire service. Read on for a decidedly different take on this offering than what’s being portrayed in the mainstream media.
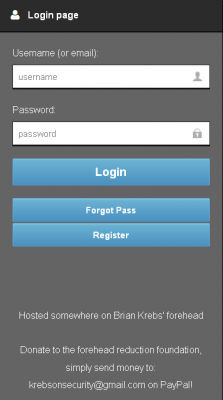
Lizard Stresser login page taunts this author.
The new service, lizardstresser[dot]su, seems a natural evolution for a group of misguided youngsters that has sought to profit from its attention-seeking activities. The Lizard kids only ceased their attack against Sony’s Playstation and Microsoft’s Xbox Live networks last week after MegaUpload founder Kim Dotcom offered the group $300,000 worth of vouchers for his service in exchange for ending the assault. And in a development probably that shocks no one, the gang’s members cynically told Dailydot that both attacks were just elaborate commercials for and a run-up to this DDoS-for-hire offering.
The group is advertising the new “booter service” via its Twitter account, which has some 132,000+ followers. Subscriptions range from $5.99 per month for the ability to knock a target offline for 100 seconds at a time, to $129.99 monthly for DDoS attacks lasting more than eight hours.
In any case, I’m not terribly interested in turning this post into a commercial for the Lizard kids; rather, it’s a brain dump of related information I’ve gathered from various sources in the past 24 hours about the individuals and infrastructure that support the site.
In a show of just how little this group knows about actual hacking and coding, the source code for the service appears to have been lifted in its entirety from titaniumstresser, another, more established DDoS-for-hire booter service. In fact, these Lizard geniuses are so inexperienced at coding that they inadvertently exposed information about all of their 1,700+ registered users (more on this in a moment).
These two services, like most booters, are hidden behind CloudFlare, a content distribution service that lets sites obscure their true Internet address. In case anyone cares, Lizardstresser’s real Internet address currently is 217.71.50.57, at a hosting facility in Bosnia.
In any database of leaked forum or service usernames, it is usually safe to say that the usernames which show up first in the list are the administrators and/or creators of the site. The usernames exposed by the coding and authentication weaknesses in LizardStresser show that the first few registered users are “anti” and “antichrist.” As far as I can tell, these two users are the same guy: A ne’er-do-well who has previously sold access to his personal DDoS-for-hire service on Darkode — a notorious English-language cybercrime forum that I have profiled extensively on this blog.
As detailed in a recent, highly entertaining post on the blog Malwaretech, LizardSquad and Darkode are practically synonymous and indistinguishable now. Anyone curious about why the Lizard kids have picked on Yours Truly can probably find the answer in that Malwaretech story. As that post notes, the main online chat room for the Lizard kids (at lizardpatrol[dot]com) also is hidden behind CloudFlare, but careful research shows that it is actually hosted at the same Internet address as Darkode (5,38,89,132).

A suggested new banner for this blog from the jokers at black hat forum Darkode, which shares a server with the main chat forum for the Lizard kids.
In a show of just how desperate these kids are for attention, consider that the login page for LizardStresser currently says “Hosted somewhere on Brian Krebs’ forehead: Donate to the forehead reduction foundation, simply send money to krebsonsecurity@gmail.com on PayPal.” Many of you have done that in the past couple of days, although I doubt as a result of visiting the Lizard kids’ silly site. Anyway, for those generous donors, a hearty “thank you.” Continue reading →
 Leading the batch of Microsoft patches for 2015 is a drama-laden update to fix a vulnerability in Windows 8.1 that Google researchers disclosed just two days ago. Google has a relatively new policy of publicly disclosing flaws 90 days after they are reported to the responsible software vendor — whether or not that vendor has fixed the bug yet. That 90-day period elapsed over the weekend, causing Google to spill the beans and potentially help attackers develop an exploit in advance of Patch Tuesday.
Leading the batch of Microsoft patches for 2015 is a drama-laden update to fix a vulnerability in Windows 8.1 that Google researchers disclosed just two days ago. Google has a relatively new policy of publicly disclosing flaws 90 days after they are reported to the responsible software vendor — whether or not that vendor has fixed the bug yet. That 90-day period elapsed over the weekend, causing Google to spill the beans and potentially help attackers develop an exploit in advance of Patch Tuesday.