The high-profile Web site defacement and hacker group known as the Syrian Electronic Army (SEA) continues to deny that its own Web server was hacked, even as gigabytes of data apparently seized during the compromise leaked onto the Deep Web this weekend.

Screen shot from SEA site syrian-es.org, listing the nicknames and avatars of top SEA leaders. Image: HP Security Research
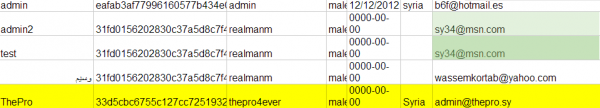
Following a string of high profile attacks that compromised the Web sites of The New York Times and The Washington Post among others, many publications have sought to discover and spotlight the identities of core SEA members. On Wednesday, this blog published information from a confidential source who said that the SEA’s Web site was hacked and completely compromised in April 2013. That post referenced just a snippet of name and password data allegedly taken from the SEA’s site, including several credential pairs that appeared tied to a Syrian Web developer who worked with the SEA.
The SEA — through its Twitter accounts — variously denounced claims of the hack as a fraud or as a propaganda stunt by U.S. intelligence agencies aimed at discrediting the hacker group.
“We can guarantee our website has never been hacked, those who claim to have hacked it should publish their evidence. Don’t hold your breath,” members of the group told Mashable in an interview published on Friday. “In any case we do not have any sensitive or personal data on a public server. We are a distributed group, most of what we have and need is on our own machines and we collaborate on IRC.”
In apparent response to that challenge, a huge collection of data purportedly directly taken from the SEA’s server in April 2013 — including all of the the leaked credentials I saw earlier — was leaked today to Deep Web sites on Tor, an anonymity network. Visiting the leak site, known as a “hidden service,” is not possible directly via the regular Internet, but instead requires the use of the Tor Browser.
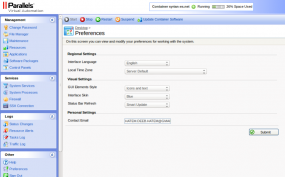
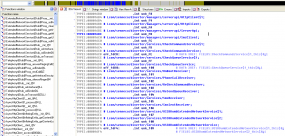
Among the leaked screen shots at the hidden Web site include numerous apparent snapshots of the SEA’s internal blog infrastructure, the Parallels virtual private server that powered for its syrian-es[dot]com Web site, as well as what are claimed to be dozens of credential pairs for various SEA member Twitter and LinkedIn accounts.
News of the archive leak to the Deep Web was first published by the French publication reflects.info (warning: some of the images published at that link may be graphic in nature). As detailed by the French site, the leak archive includes hundreds of working usernames and passwords to various Hotmail, Outlook and Gmail accounts, as well as more than six gigabytes of email messages downloaded from those accounts.