Borrowing from the playbook of corporations seeking better ways to track employee productivity, some cybercriminal gangs are investing in technologies that help them keep closer tabs on their most prized assets: “Money mules,” individuals willingly or unwittingly recruited to help fraudsters launder stolen funds. It seems that at least one mule recruitment gang employs custom software to spy on new recruits.
Last month, I heard from a reader in North Carolina named John who’d been roped into working for a company that claimed to be in the digital concierge and outsourcing business. John became suspicious that he was involved in something shady when they told him he should expect a transfer of nearly $10,000 to the personal bank account that he’d provided to his erstwhile employer in order to eventually receive a paycheck.
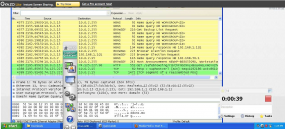
The software stole this glimpse of my test machine’s desktop.
The firm that hired John, a fictitious company called VIP One, recruits mules to help process fraudulent transfers from businesses victimized by account takeovers. Prior to sending its mules money, VIP One has prospective mules spend several weeks doing relatively meaningless busy work, for which they are promised payment at the end of the month.
VIP One requires all new recruits to install a “time tracking” application, basically a digital stopwatch that employees are expected to use to keep track of their time “on the job.” John was kind enough to let me take a peek inside his account at VIP One, and to download the time tracking software. It’s safe to say that time is certainly not the only thing being tracked by this program.
I installed the application in a Window XP virtual machine equipped with Wireshark, a free program that lets you inspect the data packets going in and out of a host machine. I pressed start and left the software alone for a few hours. A review of the Wireshark logs showed that the time tracking tool periodically and surreptitiously took screenshots of my system, uploading them to a site called gyazo.com. This Web site appears to be associated with a legitimate screen-grabbing application that automates the grabbing and posting online of screen captures.
My test machine also had several peripherals plugged into it, including a Webcam. To my surprise, further review of the logs showed that the time tracking tool hijacked my machine’s Web cam and took several pictures, also posting them to gyazo.com.
Continue reading →