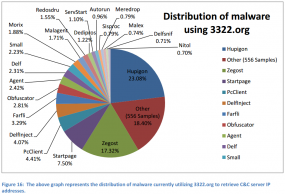
Security experts are accustomed to direct attacks, but some of today’s more insidious incursions succeed in a roundabout way — by planting malware at sites deemed most likely to be visited by the targets of interest. New research suggests these so-called “watering hole” tactics recently have been used as stepping stones to conduct espionage attacks against a host of targets across a variety of industries, including the defense, government, academia, financial services, healthcare and utilities sectors.
Espionage attackers increasingly are setting traps at “watering hole” sites, those frequented by individuals and organizations being targeted.
Some of the earliest details of this trend came in late July 2012 from RSA FirstWatch, which warned of an increasingly common attack technique involving the compromise of legitimate websites specific to a geographic area which the attacker believes will be visited by end users who belong to the organization they wish to penetrate.
At the time, RSA declined to individually name the Web sites used in the attack. But the company shifted course somewhat after researchers from Symantec this month published their own report on the trend (see The Elderwood Project). Taken together, the body of evidence supports multiple, strong connections between these recent watering hole attacks and the Aurora intrusions perpetrated in late 2009 against Google and a number of other high-profile targets.
In a report released today, RSA’s experts hint at — but don’t explicitly name — some of the watering hole sites. Rather, the report redacts the full URLs of the hacked sites that were redirecting to exploit sites in this campaign. However, through Google and its propensity to cache content, we can see firsthand the names of the sites that were compromised in this campaign.
According to RSA, one of the key watering hole sites was “a website of enthusiasts of a lesser known sport,” hxxp://xxxxxxxcurling.com. Later in the paper, RSA lists some of the individual pages at this mystery sporting domain that were involved in the attack (e..g, http://www.xxxxxxxcurling.com/Results/cx/magma/iframe.js). As it happens, running a search on any of these pages turns up a number recent visitor logs for this site — torontocurling.com. Google cached several of the access logs from this site during the time of the compromise cited in RSA’s paper, and those logs help to fill in the blanks intentionally left by RSA’s research team, or more likely, the lawyers at RSA parent EMC Corp. (those access logs also contain interesting clues about potential victims of this attack as well).
From cached copies of dozens of torontocurling.com access logs, we can see the full URLs of some of the watering hole sites used in this campaign:
- http://cartercenter.org
- http://princegeorgescountymd.gov
- http://rocklandtrust.com (Massachusetts Bank)
- http://ndi.org (National Democratic Institute)
- http://www.rferl.org (Radio Free Europe / Radio Liberty)
According to RSA, the sites in question were hacked between June and July 2012 and were silently redirecting visitors to exploit pages on torontocurling.com. Among the exploits served by the latter include a then-unpatched zero-day vulnerability in Microsoft Windows (XML Core Services/CVE-2012-1889). In that attack, the hacked sites foisted a Trojan horse program named “VPTray.exe” (made to disguise itself as an update from Symantec, which uses the same name for one of its program components). Continue reading