In January of this year, I published the results of an investigation into the identity of the man behind the once-infamous Srizbi spam botnet. Today’s post looks at an individual likely involved in running the now-defunct Xarvester botnet, a spam machine that experts say appeared shortly after Srizbi went offline and shared remarkably similar traits.
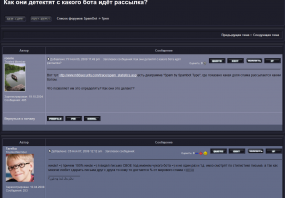
In this screenshot from Spamdot.biz, Ronnie chats with “Tarelka” the Spamdot nickname used by the Rustock botmaster. The two are discussing an M86 report on the world’s top botnets.
Srizbi was also known in the underground as “Reactor Mailer,” and customers could register to spam from the crime machine by logging into accounts at reactormailer.com. That domain was registered to a mserver@mail.ru, an address that my reporting indicates was used by a Philipp Pogosov. More commonly known by his nickname SPM, Pogosov was a top moneymaker for SpamIt, a rogue online pharmacy affiliate program that was responsible for a huge percentage of junk email over the past half-decade.
When reactormailer.com was shuttered, Srizbi customers were instructed to log in at a new domain, reactor2.com. Historic WHOIS records show reactor2.com was registered by someone using the email address ronnich@gmail.com. As I wrote in January, leaked SpamIt affiliate records show that the ronnich@gmail.com address was used by a SpamIt affiliate named Ronnie who was referred to the program by SPM.
The Srizbi botnet would emerge as perhaps the most important casualty of the McColo takedown at the end of 2008. At the time, all of the servers used to control the giant botnet were hosted at McColo, a crime-friendly hosting facility in Northern California. When McColo’s upstream providers pulled the plug on it, that was the beginning of the end for Srizbi. SPM called it quits on spamming, and went off to focus on his online gaming company.
But according a report released in January 2009 by Trustwave’s M86 Security called Xarvester: The New Srizbi, Xarvester (pronounced “harvester”) was a pharmacy spam machine tied to SpamIt that emerged at about the same time that Srizbi disappeared, and was very similar in design and operation. It appears that SPM may have handed control over his botnet to Ronnie before leaving the spamming scene.