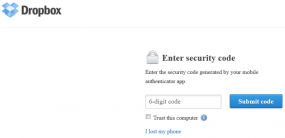
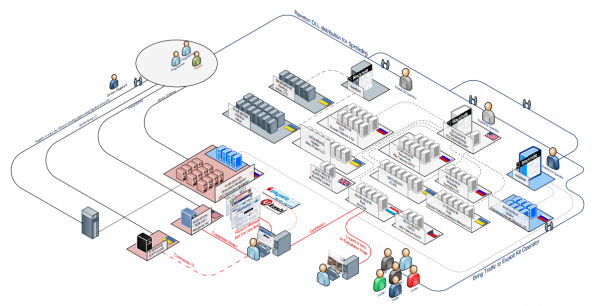
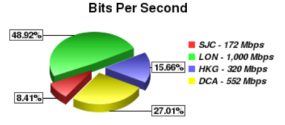
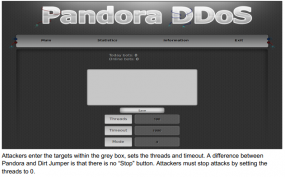
For this fifth edition in a series of advice columns for folks interested in learning more about security as a craft or profession, I interviewed Charlie Miller, a software bug-finder extraordinaire and principal research consultant with Accuvant LABS.
 Probably best known for his skills at hacking Apple‘s products, Miller spent five years at the National Security Agency as a “global network exploitation analyst.” After leaving the NSA, Miller carved out a niche for himself as an independent security consultant before joining Accuvant in May 2011.
Probably best known for his skills at hacking Apple‘s products, Miller spent five years at the National Security Agency as a “global network exploitation analyst.” After leaving the NSA, Miller carved out a niche for himself as an independent security consultant before joining Accuvant in May 2011.
BK: How did your work for the NSA prepare you for a job in the private sector? Did it offer any special skill sets or perspectives that you might otherwise not have gotten in the private sector?
Miller: Basically, it provided on the job training. I got paid a decent salary to learn information security and practice it at a reasonable pace. It’s hard to imagine other jobs that would do that, but if you have a lot of free time, you could simulate such an experience.
BK: The U.S. Government, among others, is starting to dedicate some serious coin to cybersecurity. Should would-be cyber warriors be looking to the government as a way to get their foot in the door of this industry? Or does that option tend to make mainly sense for young people?
Miller: For me, it made sense at the beginning, but there are some drawbacks. The most obvious drawback is government pay isn’t as competitive as the private industry. This isn’t such a big deal when you’re starting out, but I don’t think I could work for the government anymore for this reason. Because of this, many people use government jobs as a launching point to higher paying jobs (like government contracting). For me, I found it very difficult to leave government and enter a (non govt contracting) industry. I had 5 years of experience that showed up as a couple of bullet points on my resume. I couldn’t talk about what I knew, how I knew it, experience I had, etc. I had a lot of trouble getting a good job after leaving NSA.
BK: You’ve been a fairly vocal advocate of the idea that companies should not expect security researchers to report bugs for free. But it seems like there are now a number of companies paying (admittedly sometimes nominal sums) for bugs, and there are several organizations that pay quite well for decent vulnerabilities. And certainly you’ve made a nice chunk of change winning various hacking competitions. Is this a viable way for would-be researchers to make a living? If so, is it a realistic rung to strive for, or is bug-hunting for money a sort of Olympic sport in which only the elite can excel?
Miller: In some parts of the world, it is possible to live off bug hunting with ZDI-level payments. However, given the cost of living in the US, I don’t think it makes sense. Even if you mix in occasional government sales, it would be a tough life living off of bug sales. If I thought it was lucrative, I’d being doing it! For me, it is hard to imagine making more than I do now as a consultant by selling bugs, and the level of risk I’d have to assume would be much higher.
Continue reading →
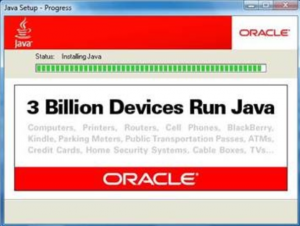 Esteban Guillardoy, a developer at the security firm Immunity Inc., said the underlying vulnerability has been around since July 28, 2011.
Esteban Guillardoy, a developer at the security firm Immunity Inc., said the underlying vulnerability has been around since July 28, 2011.