Microsoft is urging Windows users who browse the Web with Internet Explorer to use a free tool called EMET to block attacks against a newly-discovered and unpatched critical security hole in IE versions 7, 8 and 9. But some experts say that advice falls short, and that users can better protect themselves by surfing with an alternative browser until Microsoft issues a proper patch for the vulnerability.
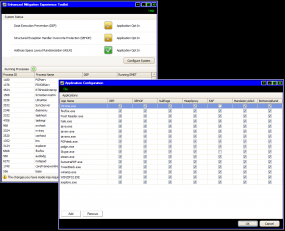
EMET, short for the Enhanced Mitigation Experience Toolkit, is a tool that can help Windows users beef up the security of commonly used applications, whether they are made by a third-party vendor or by Microsoft. EMET allows users to force applications to use one or both of two key security defenses built into Windows Vista and Windows 7 — Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP).
Put very simply, DEP is designed to make it harder to exploit security vulnerabilities on Windows, and ASLR makes it more difficult for exploits and malware to find the specific places in a system’s memory that they need to do their dirty work.
Before I get into the how-tos on EMET, a few caveats. EMET is a great layer of security that Windows users can and should use to enhance the security of applications. But EMET may not block the exploit code now publicly available through the Metasploit framework. In fact, Tod Beardlsey, an engineering manager with Rapid7, the security firm that manages Metasploit, told The Associated Press that EMET does not appear to be completely effective against this exploit.
I asked Metasploit founder HD Moore what he thought was the best way to block this exploit, and he pointed out that the exploit available through Metasploit requires the presence of Java on the host machine in order to execute properly on IE 8/9 on Windows 7 and Vista systems (the exploit works fine without Java against IE7 on XP/Vista and IE8 on XP). Obviously, while the lack of Java on a Windows machine may not prevent other exploits against this flaw, it is a great first start. I have consistently urged computer users of all stripes to uninstall Java if they have no specific use for it.