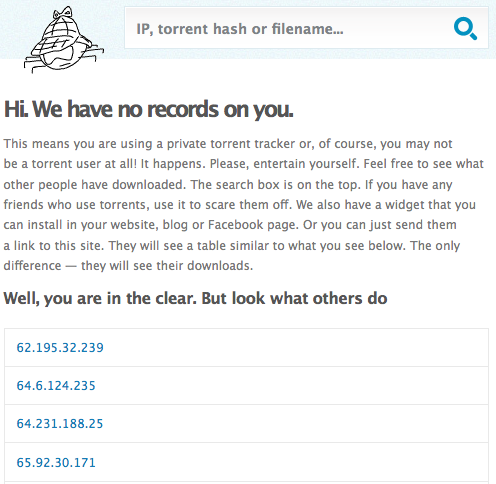
Recently leaked online chat records may provide the closest look yet at a Russian man awaiting trial in Wisconsin on charges of running a cybercrime machine once responsible for sending between 30 to 40 percent of the world’s junk email.

Oleg Nikolaenko
Oleg Y. Nikolaenko, a 24-year-old who’s been dubbed “The King of Spam,” was arrested by authorities in November 2010 as he visited a car show in Las Vegas. The U.S. Justice Department alleges that Nikolaenko, using the online nickname “Docent” earned hundreds of thousands of dollars using his “Mega-D” botnet, which authorities say infected more than half a million PCs and could send over 10 billion spam messages a day. Nikoalenko has pleaded not guilty to the charges, and is slated to appear in court this week for a status conference (PDF) on his case.
The Justice Department alleges that Nikolaenko spammed on behalf of Lance Atkinson and other members of Affking, an affiliate program that marketed fly-by-night online pharmacies and knockoff designer goods. Atkinson told prosecutors that one of his two largest Russian spamming affiliates used the online moniker Docent. He also said that Docent received payment via an ePassporte account under the name “Genbucks_dcent.” FBI agents later learned that the account was registered in Nikolaenko’s name and address in Russia, and that the email address attached to the account was 4docent@gmail.com.
According to my research, Docent also spammed for other rogue pharmacy programs. In fact, it’s hard to find one that didn’t pay him to send spam. In my Pharma Wars series, I’ve detailed how Russian cybercrime investigators probing the operations of the massive GlavMed/SpamIt rogue pharmacy operation seized thousands of chat logs from one of its principal organizers. The chats were later leaked online and to select journalists. Within those records are hundreds of hours of chats between the owners of the pharmacy program and many of the world’s biggest spammers, including dozens with one of its top earners — Docent.
According to the SpamIt records, Docent earned commissions totaling more than $325,000 promoting SpamIt pharmacy sites through spam between 2007 and 2010. The Docent in the SpamIt database also had his earnings sent to the same ePassporte account identified by the FBI. The Docent in the leaked chats never references himself as Nikolaenko, but in several cases he asks SpamIt coordinators to send documents to him at the 4docent@gmail.com address.
The chats between Docent and Stupin show a young man who is ultra-confident in the value and sheer spam-blasting power of his botnet. Below are the first in a series of conversation snippets between Docent and SpamIt co-administrator Dmitry Stupin. Before each is a brief note providing some context.
In the transcript that follows, Stupin tries to woo Docent to join SpamIt. Docent negotiates a much higher commission rate than is usually given to new spamming partners. The typical rate is 30 percent of each sale, but Docent is a known figure in the spamming underground, and argues that his botnet will bring such massive traffic to the SpamIt pharmacies that he deserves a higher 45 or 50 percent cut of the sales. This conversation was recorded on Feb. 1, 2007.
Stupin: Hello! You have communicated with ICQ 397061228, I am writing regarding your case, Docent.
Docent: Which case?
Stupin: Do you want to send spam regarding our partnerka [“partnerka” is Russian slang for a mix of private and semi-public affiliate groups that form to facilitate cybercrime activities].
Docent: Which exactly do you mean? I have not yet communicated with this 397061228.
Stupin: Here is the letter which recently came from you: “It is usual spam, GI bases, not opt-in. Big volume of emails. I mail a lot of [competing pharmacy] programs, Bulker, Mailien, SRX. I’m a member of most bulk forums. So if you need references, i can provide them. Usual traffic is 2k+ uniques. Also i need bulk-host.”
Docent: Yes, I got it. It’s just nobody IM’d me.
Stupin: ок) What kind of volumes of spam can you deliver? We are soon deploying our own “partnerka” for spam, we just do not have it right now.
Docent: Volumes are huge, 500 million + / day.
Stupin: Wow! Are you not accidentally on [Spamhaus] ROKSO List ?
Docent: Yes, it’s a list of idiots :), with the exception of a couple of people.
Stupin: We do contract people for our spam campaigns, but only verified people. We are not publicly opened yet.
Continue reading →
![]() Microsoft today issued software updates to patch at least 19 security holes in Windows, including three flaws that earned the company’s most serious “critical” rating. Separately, Oracle released a security update that fixes several issues in its Java software.
Microsoft today issued software updates to patch at least 19 security holes in Windows, including three flaws that earned the company’s most serious “critical” rating. Separately, Oracle released a security update that fixes several issues in its Java software.