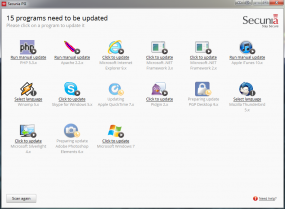
A new version of the Personal Software Inspector (PSI) tool from vulnerability management firm Secunia automates the updating of third-party programs that don’t already have auto-updaters built-in. The new version is a welcome development for the sort of Internet users who occasionally still search their keyboards for the “any” key, but experienced PSI users will probably want to stick with the comparatively feature-rich current version.
PSI 3.0 introduces one major new feature: Auto-updating by default. The program installs quickly and immediately begins scanning installed applications for missing security updates. When I ran the beta version, it found and automatically began downloading and installing fixes for about half of the apps that it detected were outdated. The program did find several insecure apps that it left alone, including iTunes, PHP and Skype; I suspect that this was based on user feedback. It may also just avoid auto-patching busy programs (all three of those applications were running on my test machine when I installed PSI 3.0); for these, PSI presents the “run manual update,” or “click to update,” option.
But users familiar with previous versions of PSI may be frustrated with the beta version’s intentional lack of options. The beta is devoid of all settings that are present in the current version of PSI, and the user dashboard that listed updated software alongside outdated programs and other options no longer exists. In fact, once a program is updated, it is removed from the update panel, leaving no record of what was updated (I had to sort my Program Files folder by date to learn which programs were touched after running PSI 3.0).