Employee and financial records leaked from some of the world’s largest sponsors of spam provide new clues about the identity of a previously unknown Russian man believed to have been closely tied to the development and maintenance of “Bredolab,” a massive collection of hacked machines that was disassembled in an international law enforcement sweep in late 2010.
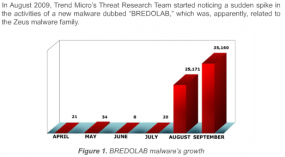
In October 2010, Armenian authorities arrested and imprisoned 27-year-old Georg Avanesov on suspicion of running Bredolab, a botnet that infected an estimated 3 million PCs per month through virus-laden e-mails and booby-trapped Web sites. The arrest resulted from a joint investigation between Armenian police and cyber sleuths in the Netherlands, whose ISPs were home to at least 143 servers that were used to direct the botnet’s activities.
Dutch and Armenian investigators have long suspected that Avanesov worked closely with an infamous Russian botmaster who used the nickname “Birdie,” but so far they have been unable to learn the Russian’s real identity or whereabouts.
“He was a close associate of Gregory A.,” Pim Takkenberg, team leader of the National High Tech Crime Unit in the Netherlands, said of the hacker known as Birdie. “Actually, we were never able to fully identify him.”
According to records leaked from SpamIt — a pharmacy affiliate program that was the victim of a data breach in 2010 — Birdie was an affiliate with SpamIt along with Avanesov. Neither affiliates earned much from SpamIt directly; they both made far more money selling other spammers access to Bredolab.
Birdie was also the nickname of a top member of Spamdot.biz, a now-defunct forum that once counted among its members nearly all of the big names in Spamit, as well as a dozen competing spam affiliate programs. Birdie’s core offering on Spamdot was the “Birdie Load System,” which allowed other members to buy “installs” of their own malware by loading it onto machines already infected with Bredolab.
So successful and popular was the Birdie Load System among Spamdot members that Birdie eventually had to create a customer queuing system, scheduling new loads days or weeks in advance for high volume customers. According to his own postings on Spamdot, Birdie routinely processed at least 50,000 new loads or installs for customers each day.
“Due to the fact that many of my clients very much hate waiting in line, we’ve begun selling access to weekly slots,” Birdie wrote. “If a ‘slot’ is purchased, independently from other customers, the person who purchased the slot is guaranteed service.”
Using Birdie’s Bredolab load system, spammers could easily re-seed their own spam botnets, and could rely upon load systems like this one to rebuild botnets that had been badly damaged from targeted takedowns by anti-spam activists and/or law enforcement. Bredolab also was commonly used to deploy new installations of the ZeuS Trojan, which has been used in countless online banking heists against consumers and businesses.
Below is a translated version of Birdie’s Dec. 2008 post to Spamdot describing the rules, prices and capabilities of his malware loading machine (click the image below twice for an enlarged version of the Spamdot discussion thread from which this translation was taken). Continue reading