Last week, not long after I published the latest installment in my Pharma Wars series, KrebsOnSecurity.com was the target of a sustained distributed denial-of-service (DDoS) attack that caused the site to be unavailable for some readers between Nov. 17 and 18. What follows are some details about that attack, and how it compares to previous intimidation attempts.
The DDoS was caused by incessant, garbage requests from more than 20,000+ PCs around the globe infected with malware that allows criminals to control them remotely for nefarious purposes. If you’ve noticed that a few of the features on this site haven’t worked as usual these past few days, now you know why. Thanks for your patience.
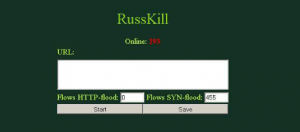 I shared the log files of the attack with Joe Stewart, director of malware research at Dell SecureWorks. Stewart discovered that the botnet responsible for hitting my site appears to have been created with Russkill, a commercial crimeware kit that is sold for a few hundred bucks on the hacker underground. Russkill, sometimes called Dirt Jumper, does its dirty work by forcing infected systems to rapidly request the targeted site’s homepage.
I shared the log files of the attack with Joe Stewart, director of malware research at Dell SecureWorks. Stewart discovered that the botnet responsible for hitting my site appears to have been created with Russkill, a commercial crimeware kit that is sold for a few hundred bucks on the hacker underground. Russkill, sometimes called Dirt Jumper, does its dirty work by forcing infected systems to rapidly request the targeted site’s homepage.
Stewart said he suspects — but can’t prove – that the control center for this botnet is noteye.biz, based on traffic analysis of Internet addresses in the logs I shared with him.
“I did not already have [noteye.biz] under monitoring so it is impossible to say for sure what targets were hit in the past,” Stewart wrote in an email. He noted that the same attacker also apparently runs a Dirt Jumper botnet at xzrw1q.com, which also is currently attacking Ukrainian news site genshtab.censor.net.ua, and kidala.info (“kidala” is Russian slang for “criminal,” and kidala.info is a well-known Russian crime forum).
“According to my logs this botnet did attack your site back in April, so this is some additional circumstantial evidence that suggests the noteye.biz [control network] may have been involved in the recent attack on your site,” Stewart wrote.
As Stewart notes, this is not the first time my site has been pilloried, although it was arguably the most disruptive. In October 2010, a botnet typically used to spread spam for rogue Internet pharmacies attacked krebsonsecurity.com, using a hacked Linux server at a research lab at Microsoft, of all places.
I’ve spoken at more than a dozen events this year, and the same question nearly always comes up: Do you ever get threatened or attacked? For the most part, the majority of the threats or intimidation attempts have been light-hearted.
Yes, occasionally crooks in the underground will get a bit carried away – as in these related threads from an exclusive crime forum, where I am declared the “enemy of carding;” or in the love I received from the guys at Crutop.nu, a major Russian adult Webmaster forum (the site now lives at Crutop.eu).
But some of the “attacks” have been downright funny. In June, someone hacked a news site and planted a story falsely claiming that F-Secure researcher Mikko Hypponen and I had been arrested for selling stolen credit cards.
My name also has been known to show up in malware. In June, a Trojan downloader that peddled adult Web sites included a reference that I had somehow gotten married to security blogger Dancho Danchev. In 2010, Fortinet found a variant of the spam botnet installer Pushdo that was controlled by a domain name called “fuckbriankrebs.com.” In 2009, Sophos wrote about a new email malware campaign disguised as an alert about a wayward DHL package: The message included a “tracking number” that was essentially the same sentiment, only spelled backwards.
I guess my stories about the ZeuS Trojan have angered those guys as well. In February 2010, a piece I wrote warning people about an oddball version of the ZeuS Trojan that stole Microsoft Word documents and PDFs was re-purpopsed to help make a follow-up campaign more successful.
Update, Nov. 23, 9:31 a.m. ET: As noted by one commenter already, a deep dive into Russkill/Dirt Jumper was recently published at DeepEndResearch.org, a new group that includes some well-known security researchers.




Ah yes! Building up your street cred!!! Congratulations Brian! I would be extremely proud if I were you! May continued kudos rain upon thee! 🙂
Brian, This attack on your prominent website has an upside: it demonstrates the dangers aimed at every Internet user. “20,000+ PCs around the globe infected with malware that allows criminals to control them
remotely.” Most Internet users I know are all but completely oblivious to the great scope of the dangers out there. I know I will be forwarding your Digest Email about this attack as well as your URL to my friends and associates. David
Well, this just confirms what I assumed was the problem when I couldn’t reach the site in the early morning hours of (I guess) Nov. 18. However, I did successfully reach the site by using the krebsonsecurity IP address: 94.228.133.163.
I also had a problem accessing Krebsonsecurity last week, and I was concerned that someone had taken the site down. Now I know!
Keep up your good work, Brian. Evidently, it is bothering someone on the other side, and that’s good.
Regards,
RWS
Being the target of DDoS attacks makes your site a very effective botnet detection system. If owners of those malware-infected PCs could be notified (through their respective national CERTs, for example) and then clean up their computers, botnets will shrink in size and lose their destructive power gradually.
Detection, Information Sharing, And Notification, are the three pillars of any effective botnet mitigation, in my opinion.
Brian I was wondering if you could tell us, if its not too personal, why exactly you left the Washington Post.
I don’t think it was Brian’s choice. The Post has suffered financial reverses in recent years due to declining subscriptions (like other newspapers) and they’ve let go more than one veteran journalist in recent years.
It’s no secret. They eliminated my job, along with others that weren’t brought over when the .com merged with the dead tree edition at the end of 2009.
Another casualty of the Post Wars was Mr. Krebs’ colleague Rob Pegoraro, whose blog I now also read regularly. Both did good work at the Post, and both continue to do good work afterwards.
I have information u may find interesting attack reason come from stories released on crimepack and bredolab here person behind these attacks is admin of opensc.ws adequate who is crim
profile here: http://www.opensc.ws/member.php?u=10578
I have information u may find interesting attack reason come from stories released on crimepack and bredolab here person behind these attacks is admin of opensc.ws adequate who is crim
profile here: http://www.opensc.ws/member.php?u=10578
you may also find posts of his botnets many years ago on my website. If you need more information please contact through my blog
Hrm. Crim and I have never seen eye to eye, but from our chats he’s never struck me as the kind of guy who would stoop to DDoSsing my site. I hope I’m not wrong about that.
So it took over a year to initiate the attack?
http://krebsonsecurity.com/2010/08/crimepack-packed-with-hard-lessons/
More likely the people behind Glavmed/rx-promition are attacking, or do you have reasons to believe otherwise?
People meet at Govcert 2011, they travel back home and your site is under attack… Quite sure some bot herders like symposiums and giggle about “legal issues surrounding the Bredolab takedown” and stuff… Someone else got under attack?
Additional information on Dirt Jumper here:
http://www.deependresearch.org/2011/10/dirt-jumper-ddos-bot-new-versions-new.html
Hey Brian seems like you hit a lot of nerves out there . The way I see it that’s to bad , great work Bro . 🙂 . Maybe some one should call R.Lee Ermy from mail call and have a long talk with these miscreants .
If the best they can do is a ddos for a couple of days then you’ve already won.
Congratulations Brian! You must be doing something right!
“kidala” literally means “ripper”, not “criminal”
then a kidala is a ripper, which is a dishonest/disreputable criminal?
thanks for the clarification.
or just “con man”.
yes, “con man” is the most appropriate
Silver lining. If they are wasting resources attacking your site, then they aren’t holding some other site ransom for those few days. If it hasn’t stopped yet, do you think it will with the Xmas online shopping season getting started?
Brian,
Just like others have said, you have already won. I think your security blog is the best out there and I have seen numerous other sites reference it. I think they could have attacked any site similar to yours, but yours is gaining huge popularity (I always reference your site to peers) so that makes you a bigger target. Plus your detailed accounts are hitting them where it hurts. Keep up the great work.
Directed to Brian and any one else:
Maybe I’m naive (quite possibly actually heh) but what do you think the motivations behind this attack might be?
Is it that you have done real damage to the criminals either financially – ie. causing some dismantling of their enterprise – or through smearing their reputations – perhaps some people previously thought they were “clean” but now know the truth. Or in other ways.
Or is it just a general dislike that you report and/or coordinate with other researchers to reveal usually hidden activities to the otherwise ignorant masses (read me for one)?
Just curious as to what you think here.
Nice gain of free advertising, Krebs! I find it very amusing how they’re only bolstering your reputation with all that attention.
By the way, I once sent a link to your post for my friend in Canada, but she said she cannot access the page, while her net-access was otherwise fine, and I was all able to view the site. What do you think about that? I wonder if you’d be interested with helping (with tips & hints) to find out why so, in case the situation is still same when I next time talk with her?
Also, in case you want to be very exact with the names on the post, Mikko’s last name is written as “Hyppönen”. (you can easily copy/paste the letter ö from here, I’d assume)
Thanks for the tip. FYI, I get this same observation from some folks who work in sensitive jobs for the US Govt.; some agencies and contractors are very skittish about allowing access to sites overseas. My sight is hosted in The Netherlands, so perhaps that explains it? Just a thought.
No problems with site access, but the Like/Dislike buttons still aren’t working. Is this feature going to remain switched off?
You may have already thought about this or may be even using it (can’t tell from your nameservers), but switching over your DNS to an Anycast provider with good DDoS protection (EasyDNS comes to mind) would be one way to mitigate such attacks. At least from the DNS side of things.
Hmm so Mr Krebs posts about these criminals on his own blog, and said criminals get mad and DDOS the site? Sounds like youve hit a nerve.Good.
Who’s the censor now eh? Russian hypocrites.
I recommend CloudFlare — a free service that stops DoS and DDoS. It really works, and makes your site load faster. I have been protected from several attacks I know of by it. LulzSec used it last summer to protect their site from their enemies and in the 25 days it was up, no one could take it down.
This sort of thing should dispell any of the sensational stories equating hacking with organized crime. Because if they were some sort of mafia, they’d burned your house down. Maybe rape your wife before that and so on. The sums of money stolen are still of no consequence. In aggregate perhaps but no group is becoming billionaires from this like narcotics.