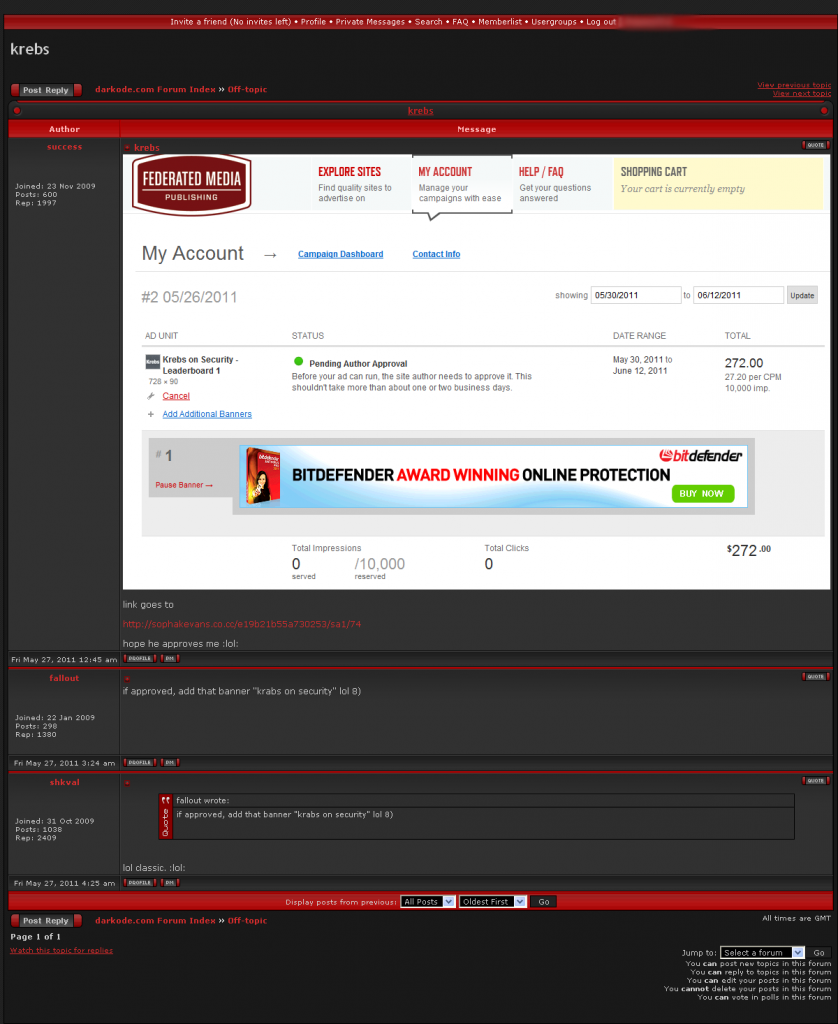
A recent cyber attack on a city water utility in Illinois may have destroyed a pump and appears to be part of a larger intrusion at a U.S. software provider, new information suggests. The incident is the latest to raise alarms about the security protecting so-called supervisory control and data acquisition system, or “SCADA” networks — increasingly Internet-connected systems designed to monitor and control complex industrial networks.
 CNN is reporting that federal officials are investigating the attack, but quoted a Department of Homeland Security official downplaying the incident. Wired.com says the focus of the attack may be the Curran-Gardner Public Water District near Springfield, Ill. The Register quotes DHS’s Peter Boogaard saying the agency and the FBI are gathering facts surrounding the report of a water pump failure, but that “at this time there is no credible corroborated data that indicates a risk to critical infrastructure entities or a threat to public safety.”
CNN is reporting that federal officials are investigating the attack, but quoted a Department of Homeland Security official downplaying the incident. Wired.com says the focus of the attack may be the Curran-Gardner Public Water District near Springfield, Ill. The Register quotes DHS’s Peter Boogaard saying the agency and the FBI are gathering facts surrounding the report of a water pump failure, but that “at this time there is no credible corroborated data that indicates a risk to critical infrastructure entities or a threat to public safety.”
The incident was first reported in a state cyber fusion notice dated Nov. 10, and soon was summarized on the blog by Joe Weiss, managing partner of Applied Control Solutions, a SCADA systems security firm. Weiss criticized the lack of response and alerting by the US-CERT, Department of Homeland Security, and the information sharing and analysis center (ISAC) run by the water industry.
Weiss read KrebsOnSecurity sections of the report, which traced the origin of the attack to Russian Internet addresses.
“Sometime during the day of Nov. 8, 2011, a water district employee noticed problems with a SCADA system. An information technology service and repair company checked the computer logs of the SCADA system and determined the system had been remotely hacked into from an Internet provider address located in Russia.”
The alert also indicates that this attack may be linked to a SCADA provider that also serves other industries, in addition to the water sector. From the alert:
“The SCADA system that was used by the water district was produced by a software company based in the US. It is believed the hackers had acquired unauthorized access to the software company’s database and retrieved the usernames and passwords of various SCADA systems, including the water district systems.”
The intrusions apparently took place over several months, during which time the attackers remotely logged into the water district’s SCADA networks and toggled systems off and on, eventually causing the failure of a water pump at the facility.
“Over a period of 2-3 months, minor glitches have been observed in remote access to the water district’s SCADA system. Recently, the SCADA system would power on and off, resulting in the burnout of a water pump.”
The notice also stated that the method of attack appears to be similar to the recent compromise of servers at the Massachusetts Institute of Technology (MIT), which involved security weaknesses around phpMyAdmin, a popular Web-based database administration tool.
“This network intrusion is the same method of attack recently used against the MIT Server,” the water district alert stated. “The water district’s attack and the MIT attack both had references to PHPMyAdmin in the log files of the computer systems. It is unknown at this time the number of SCADA usernames and passwords acquired from the software company’s database, and if any additional systems have been attacked as a result of this theft.”
Michael Assante, president and CEO of the National Board of Information Security Examiners and a former chief security officer for the North American Electric Reliability Corporation (NERC), said the attack highlights the potential pitfalls of utilities increasingly turning to off-the-shelf commercial solutions and remote access to trim costs in an era of tight state and local budgets.
Continue reading →
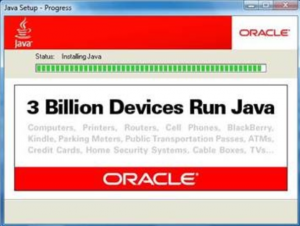 On Monday, I disclosed how the Java exploit is being sold on cybercrime forums and incorporated into automated crimeware kits like BlackHole. Since then, security researchers @_sinn3r and Juan Vasquez have developed a module for Metasploit that makes the attack tool available to penetration testers and malicious hackers alike. According to a post on the Metasploit blog today, the Java vulnerability “is particularly pernicious, as it is cross-platform, unpatched on some systems, and is an easy-to-exploit client-side that does little to make the user aware they’re being exploited.”
On Monday, I disclosed how the Java exploit is being sold on cybercrime forums and incorporated into automated crimeware kits like BlackHole. Since then, security researchers @_sinn3r and Juan Vasquez have developed a module for Metasploit that makes the attack tool available to penetration testers and malicious hackers alike. According to a post on the Metasploit blog today, the Java vulnerability “is particularly pernicious, as it is cross-platform, unpatched on some systems, and is an easy-to-exploit client-side that does little to make the user aware they’re being exploited.”