I spoke this week at Govcert 2011, a security conference in Rotterdam. The talk drew heavily on material from my Pharma Wars series, about the alleged proprietors of two competing rogue Internet pharmacies who sought to destroy the others’ reputation and business and ended up succeeding on both counts. Here is the latest installment.
For those who haven’t been following along, I’ve put together a cheat sheet on the main players, the back story and the conflict. Click here to skip this section.
Actors
 Pavel Vrublevsky: Co-founder and Former chief executive officer of ChronoPay, until recently a major processor of electronic payments in Russia. Vrublevsky has been accused of running an illegal business, a rogue Internet pharmacy affiliate program called Rx-Promotion, and is currently in prison awaiting trial on unrelated cybercrime charges. Known to business partners as “Red” or “RedEye.”
Pavel Vrublevsky: Co-founder and Former chief executive officer of ChronoPay, until recently a major processor of electronic payments in Russia. Vrublevsky has been accused of running an illegal business, a rogue Internet pharmacy affiliate program called Rx-Promotion, and is currently in prison awaiting trial on unrelated cybercrime charges. Known to business partners as “Red” or “RedEye.”
Igor Gusev: Co-founded ChronoPay with Vrublevsky in 2003. Had a falling out with Vrublevsky in 2005, left ChronoPay and started the Internet pharmacy affiliate programs GlavMed and SpamIt. The latter was closed in Sept. 2010, and Gusev has been charged with running an illegal business. He is still at large.
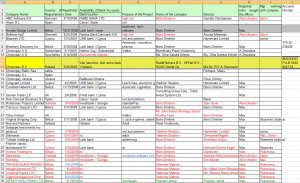
Dmitry Stupin: Gusev’s right-hand man. Helped to build SpamIt and GlavMed. The logs below are from a set of logs leaked to several download sites that contain thousands of conversations between Stupin and Gusev. The logs were obtained shortly after the police detained Stupin as part of the criminal investigation into Gusev.
Conflict: Two former business partners-turned-competitors try to sabotage each others’ business and to get the other arrested.
The conversation below takes place between Feb. 21 and 23, 2010, and is a chat log between Gusev and Stupin. Gusev already knows there are plans to file criminal charges against him, which indeed come just seven months after this conversation was recorded. The two are discussing plans to pay more than $1.5 million to politicians and law enforcement to obtain a criminal prosecution of Vrublevsky.
Several attendees at Govcert 2011 asked about the likelihood of Vrublevsky serving time, if convicted. This chat may provide a clue. In the middle of the following conversation, Gusev says he has secured promises that if arrested, Vrublevsky “would remain in prison and would not be able to pay his way out,” Gusev wrote. “He is going to lose a large portion of his business and will be left with no money to fight the war.”