A group tasked with devising strategies to deter cyber attacks is calling for mandatory public disclosure of fraud and hacking incidents by governments and organizations of all sizes, including banks.
 The recommendations were a major thrust of a report issued earlier this month by the National Research Council, which was asked to examine the issue by the Office of the Director of National Intelligence. The 400-page document is actually well worth the time to read, or at least skim. The bulk of the paper addresses how solving the problems associated with cyber crime requires aligning incentives and liabilities so that those in the best position to fix the problems have an incentive to do so.
The recommendations were a major thrust of a report issued earlier this month by the National Research Council, which was asked to examine the issue by the Office of the Director of National Intelligence. The 400-page document is actually well worth the time to read, or at least skim. The bulk of the paper addresses how solving the problems associated with cyber crime requires aligning incentives and liabilities so that those in the best position to fix the problems have an incentive to do so.
But to me, the most interesting and useful components of the report come at the end, where the group makes several broad policy recommendations, including:
- Mitigating malware infections via ISPs by subsidized cleanup
- Mandatory disclosure of fraud losses and security incidents
- Mandatory disclosure of industrial control system incidents and intrusions
- Aggregating reports of cyber espionage and reporting to the World Trade Organization
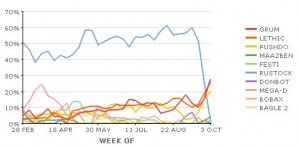
I don’t know how effective or realistic the last two recommendations would be, but as a reporter I’m naturally inclined toward disclosing data whenever possible. Loyal readers no doubt know where I stand on the first two points. I have long called for some kind of system in which ISPs are encouraged or given incentives to regularly scrub their networks for bot-infested customers and compromised Web sites.
And hardly a month goes by when I don’t hear from someone asking me where to find aggregated statistics on the costs of cybercrime and Internet banking fraud in the United States. The banks don’t have to publish reports of their losses, and although they are supposed to publish indicators of fraud (through suspicious activity reports) financial institutions seem to be spotty and begrudging about this level of reporting as well. Writing for SC Magazine earlier this summer, Charles Jeter of security software maker ESET penned a useful three part series on the lack of reporting by banks about the costs of online banking Trojans.
The free report is available at this link.
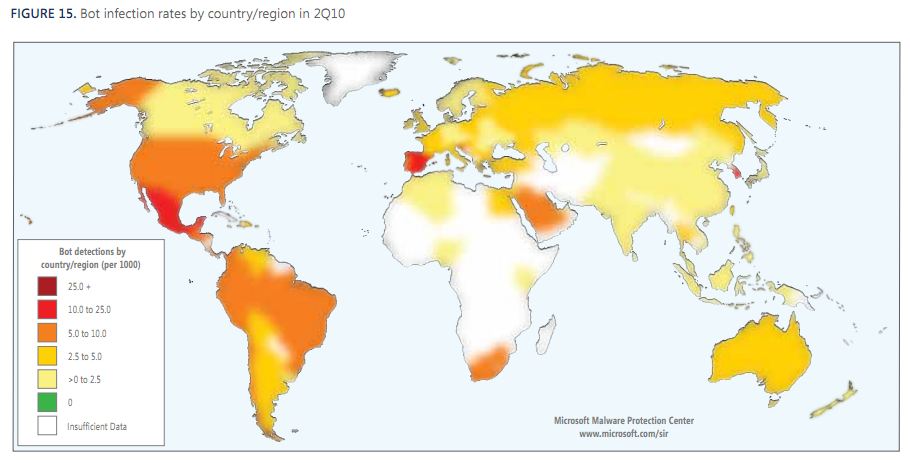
Speaking of global trends in cybercrime, Microsoft published its biannual Security Intelligence Report covering cybercrime activity it has observed in the first half of 2010. Anyone looking for granular data on which threats are most prevalent (at least from Microsoft’s perspective in scrubbing millions of PCs) should have a look at this informative report. Unsurprisingly, the United States (or more accurately — US-based ISPs) continues to lead the world in botnet infections.
 While we’re on the subject of data breach and attack disclosure, now seems like a perfect time to mention that Arbor Networks is seeking additional perspective for its annual Worldwide Infrastructure Security Threat Report. Arbor is looking for a few clueful network administrators to anonymously share experiences and perspectives about operational risks and challenges involved in building, operating and defending large networks. If this describes you, check out their survey.
While we’re on the subject of data breach and attack disclosure, now seems like a perfect time to mention that Arbor Networks is seeking additional perspective for its annual Worldwide Infrastructure Security Threat Report. Arbor is looking for a few clueful network administrators to anonymously share experiences and perspectives about operational risks and challenges involved in building, operating and defending large networks. If this describes you, check out their survey.