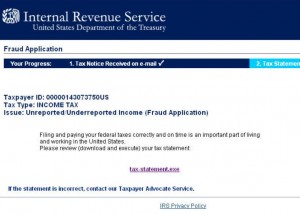
![]() As promised, Adobe has released a new version of its Flash Player software to fix a critical security flaw that hackers have been exploiting to break into vulnerable systems. The update also corrects at least 31 other security vulnerabilities in the widely used media player software.
As promised, Adobe has released a new version of its Flash Player software to fix a critical security flaw that hackers have been exploiting to break into vulnerable systems. The update also corrects at least 31 other security vulnerabilities in the widely used media player software.
The latest version, v. 10.1, fixes a number of critical flaws in Adobe Flash Player version 10.0.45.2 and earlier. Don’t know what version of Flash you’ve got installed? Visit this page to find out. The new Flash version is available for Windows, Mac and Linux operating systems, and can be downloaded from this link.
Note that if you use both Internet Explorer and non-IE browsers, you’re going to need to apply this update twice, once by visiting the Flash Player installation page with IE and then again with Firefox, Opera, or whatever other browser you use.
Please take a moment to check if you have Flash installed and — if so — to update it: A working copy of the code used to exploit this vulnerability has been included in Metasploit, an open source penetration testing framework. Also note that Adobe likes to bundle all kinds of third party software — from security scanners to various browser toolbars — with its software, so if you don’t want these extras you will need to uncheck the box next to the added software before you click the download button.
The vulnerability that prompted Adobe to issue this interim update (the company had been slated to issue these and other security updates on July 13) also is present in Adobe Reader and Acrobat, although Adobe says it does not plan to fix the flaw in either of these products until June 29.
Now would be a great time for longtime users of Adobe’s free Reader software to consider removing Reader and switching to an alternative free reader, such as Foxit or Sumatra.
Note that Flash generally comes with Adobe Download manager, a package that in prior versions has been found to harbor its own security vulnerabilities. The download manager is designed to uninstall itself from machines after a reboot, so to be on the safe side, you may want to reboot your system after updating Flash.