The owner and curator of bobbear.co.uk, a site that specializes in exposing Internet scams and phantom online companies, announced Saturday that he will be shuttering the site at the end of April.
Bobbear and its companion site bobbear.com, are creations of Bob Harrison, a 66-year-old U.K. resident who for the last four years has tirelessly chronicled and exposed a myriad of fraud and scam Web sites. The sites, which are well-indexed by Google and other search engines and receive about 2,000 hits per day, often are among the first results returned in a search for the names of fly-by-night corporations advertised in spam and aimed at swindling the unsuspecting or duping the unwitting.
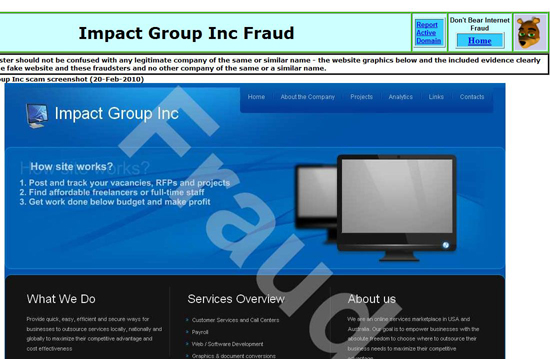
Indeed, bobbear.co.uk has been extremely valuable resource to krebsonsecurity.com, which has used it to track the constant stream of new fraudulent corporations used to recruit so-called money mules, people lured into helping organized criminals launder money stolen through online banking theft.
In an interview with krebsonsecurity, Harrison said he’s been considering this move for some time now, and finally decided to quit the site for health and quality-of-life reasons.
“The wife says I spend about 15 hours a day on it, although it may not be quite that much,” joked the pseudonymous Harrison, speaking via phone from his home near Kent, about 50 miles outside of London. “Things are quite hard and health isn’t that good, so the time has come.”