In December 2021, researchers discovered a new ransomware-as-a-service named ALPHV (a.k.a. “BlackCat“), considered to be the first professional cybercrime group to create and use a ransomware strain written in the Rust programming language. In this post, we’ll explore some of the clues left behind by a developer who was reputedly hired to code the ransomware variant.

Image: Varonis.
According to an analysis released this week by Varonis, ALPHV is actively recruiting operators from several ransomware organizations — including REvil, BlackMatter and DarkSide — and is offering affiliates up to 90 percent of any ransom paid by a victim organization.
“The group’s leak site, active since early December 2021, has named over twenty victim organizations as of late January 2022, though the total number of victims, including those that have paid a ransom to avoid exposure, is likely greater,” Varonis’s Jason Hill wrote.
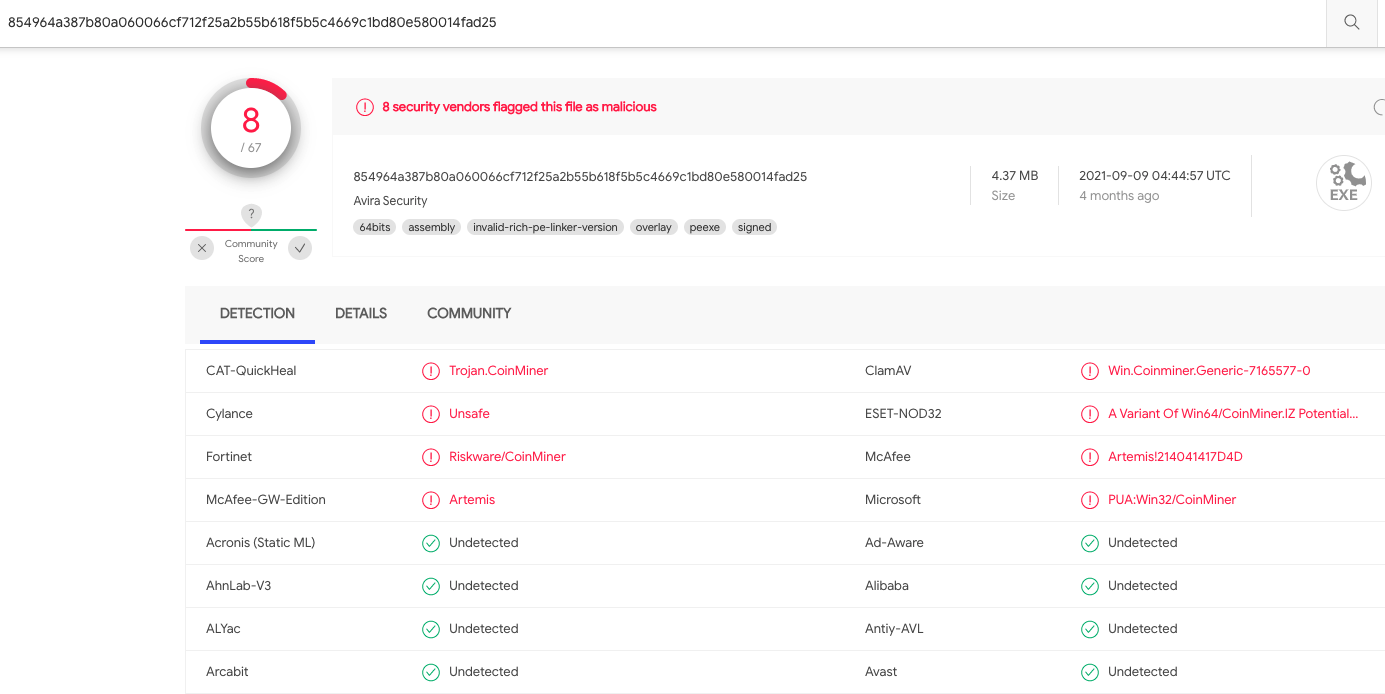
One concern about more malware shifting to Rust is that it is considered a much more secure programming language compared to C and C++, writes Catalin Cimpanu for The Record. The upshot? Security defenders are constantly looking for coding weaknesses in many ransomware strains, and if more start moving to Rust it could become more difficult to find those soft spots.
Researchers at Recorded Future say they believe the ALPHV/BlackCat author was previously involved with the infamous REvil ransomware cartel in some capacity. Earlier this month the Russian government announced that at the United States’ request it arrested 14 individuals in Russia thought to be REvil operators.
Still, REvil rolls on despite these actions, according to Paul Roberts at ReversingLabs. “The recent arrests have NOT led to a noticeable change in detections of REvil malicious files,” Roberts wrote. “In fact, detections of files and other software modules associated with the REvil ransomware increased modestly in the week following the arrests by Russia’s FSB intelligence service.”
Meanwhile, the U.S. State Department has a standing $10 million reward for information leading to the identification or location of any individuals holding key leadership positions in REvil.
WHO IS BINRS?
A confidential source recently had a private conversation with a support representative who fields questions and inquiries on several cybercrime forums on behalf of a large and popular ransomware affiliate program. The affiliate rep confirmed that a coder for ALPHV was known by the handle “Binrs” on multiple Russian-language forums.
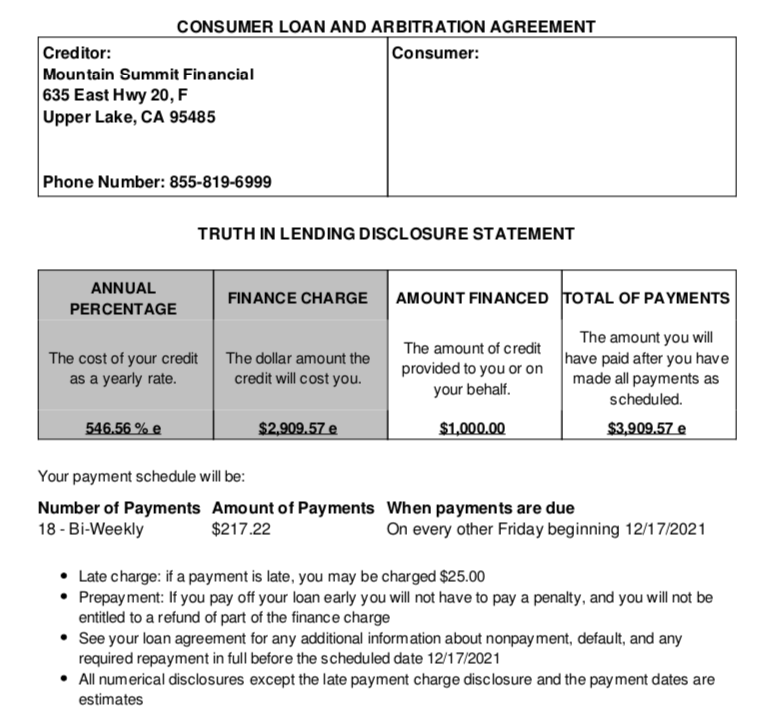
On the cybercrime forum RAMP, the user Binrs says they are a Rust developer who’s been coding for 6 years. “My stack is Rust, nodejs, php, golang,” Binrs said in an introductory post, in which they claim to be fluent in English. Binrs then signs the post with their identification number for ToX, a peer-to-peer instant messaging service.
That same ToX ID was claimed by a user called “smiseo” on the Russian forum BHF, in which smiseo advertises “clipper” malware written in Rust that swaps in the attacker’s bitcoin address when the victim copies a cryptocurrency address to their computer’s temporary clipboard.
The nickname “YBCat” advertised that same ToX ID on Carder[.]uk, where this user claimed ownership over the Telegram account @CookieDays, and said they could be hired to do software and bot development “of any level of complexity.” YBCat mostly sold “installs,” offering paying customers to ability to load malware of their choice on thousands of hacked computers simultaneously.
There is also an active user named Binrs on the Russian crime forum wwh-club[.]co who says they’re a Rust coder who can be reached at the @CookieDays Telegram account.
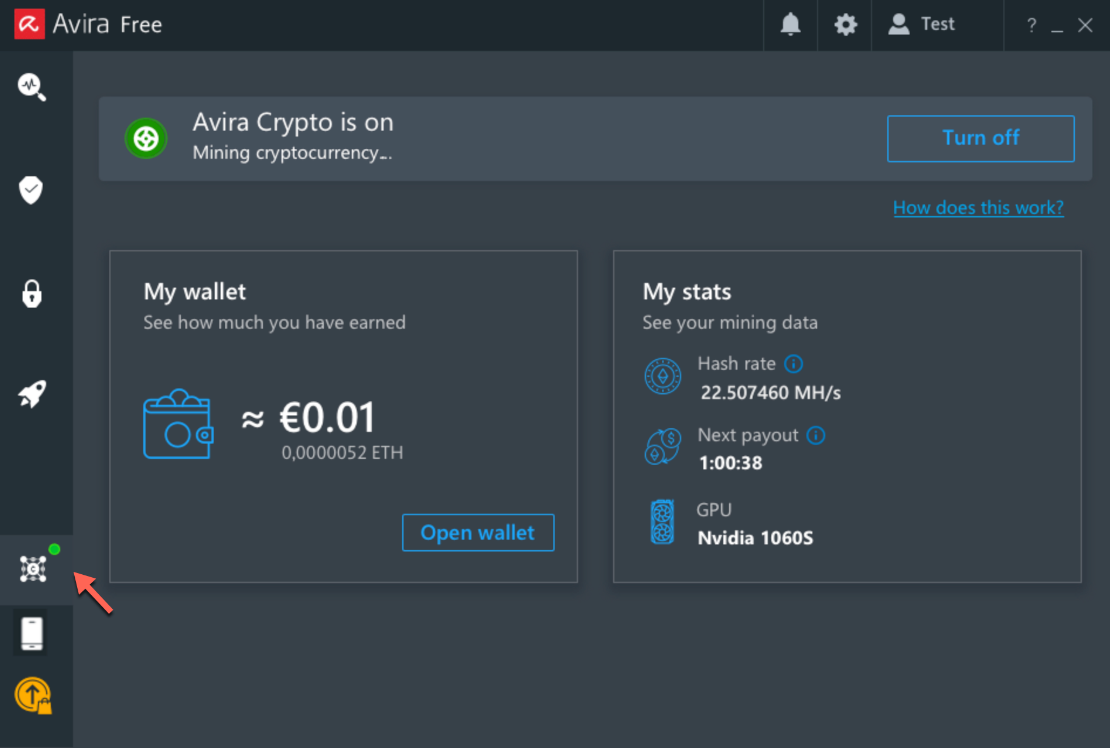
On the Russian forum Lolzteam, a member with the username “DuckerMan” uses the @CookieDays Telegram account in his signature. In one thread, DuckerMan promotes an affiliate program called CookieDays that lets people make money by getting others to install cryptomining programs that are infected with malware. In another thread, DuckerMan is selling a different clipboard hijacking program called Chloe Clipper.

The CookieDays moneymaking program.
According to threat intelligence firm Flashpoint, the Telegram user DuckerMan employed another alias — Sergey Duck. These accounts were most active in the Telegram channels “Bank Accounts Selling,” “Malware developers community,” and “Raidforums,” a popular English-language cybercrime forum. Continue reading