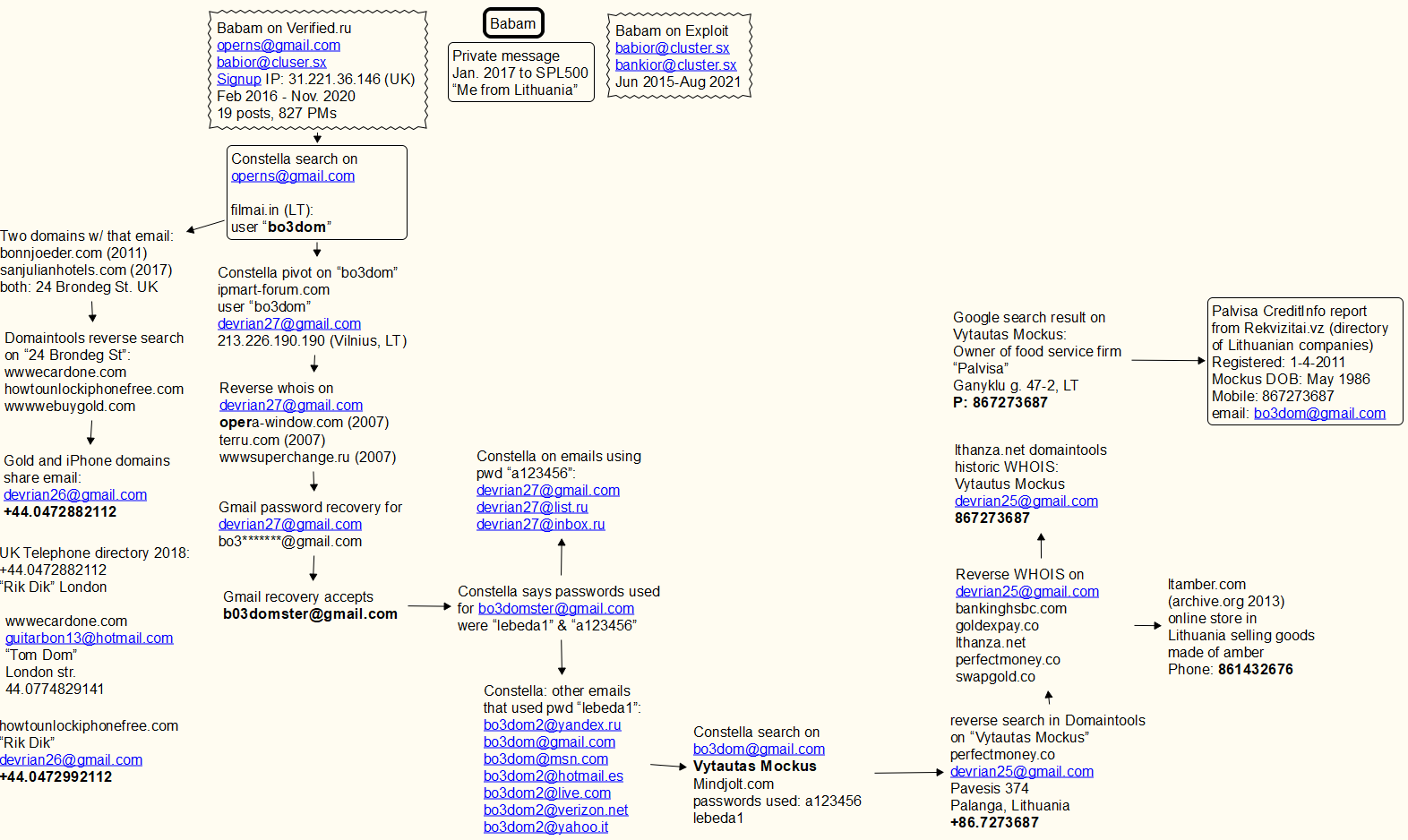
A 24-year-old New York man who bragged about helping to steal more than $20 million worth of cryptocurrency from a technology executive has pleaded guilty to conspiracy to commit wire fraud. Nicholas Truglia was part of a group alleged to have stolen more than $100 million from cryptocurrency investors using fraudulent “SIM swaps,” scams in which identity thieves hijack a target’s mobile phone number and use that to wrest control over the victim’s online identities.

Truglia admitted to a New York federal court that he let a friend use his account at crypto-trading platform Binance in 2018 to launder more than $20 million worth of virtual currency stolen from Michael Terpin, a cryptocurrency investor who co-founded the first angel investor group for bitcoin enthusiasts.
Following the theft, Terpin filed a civil lawsuit against Truglia with the Los Angeles Superior court. In May 2019, the jury awarded Terpin a $75.8 million judgment against Truglia. In January 2020, a New York grand jury criminally indicted Truglia (PDF) for his part in the crypto theft from Terpin.
A SIM card is the tiny, removable chip in a mobile device that allows it to connect to the provider’s network. Customers can legitimately request a SIM swap when their mobile device has been damaged or lost, or when they are switching to a different phone that requires a SIM card of another size.

Nicholas Truglia, holding bottle. Image: twitter.com/erupts
But fraudulent SIM swaps are frequently abused by scam artists who trick mobile providers into tying a target’s service to a new SIM card and mobile phone controlled by the scammers. Unauthorized SIM swaps often are perpetrated by fraudsters who have already stolen or phished a target’s password, as many financial institutions and online services rely on text messages to send users a one-time code for multi-factor authentication.
Compounding the threat, many websites let customers reset their passwords merely by clicking a link sent via SMS to the mobile phone number tied to the account, meaning anyone who controls that phone number can reset the passwords for those accounts.
Reached for comment, Terpin said his assailant got off easy.
“I am outraged that after nearly four years and hundreds of pages of evidence that the best the prosecutors could recommend was a plea bargain for a single, relatively minor count of the unauthorized use of a Binance exchange account, when all the evidence points toward Truglia being one of two masterminds of a wide-ranging criminal conspiracy to steal crypto from me and others,” Terpin told KrebsOnSecurity.
Terpin said public court records already show Truglia bragging about stealing his funds and using it to finance a lavish lifestyle.
“He at the very least withdrew 100 bitcoin (worth $1.6 million at the time and nearly $5 million today) from my theft into his wallet at a separate, US-based exchange, and then moved or spent it,” Terpin said. “The fact is that the intentional theft of $24 million, whether taken at the point of a gun in a bank or through a SIM card swap, is a major felony. Truglia should be prosecuted to the fullest extent of the law.”

Nicholas Truglia, showing off a diamond-studded Piaget watch while aboard a private jet. Image: twitter.com/erupts.













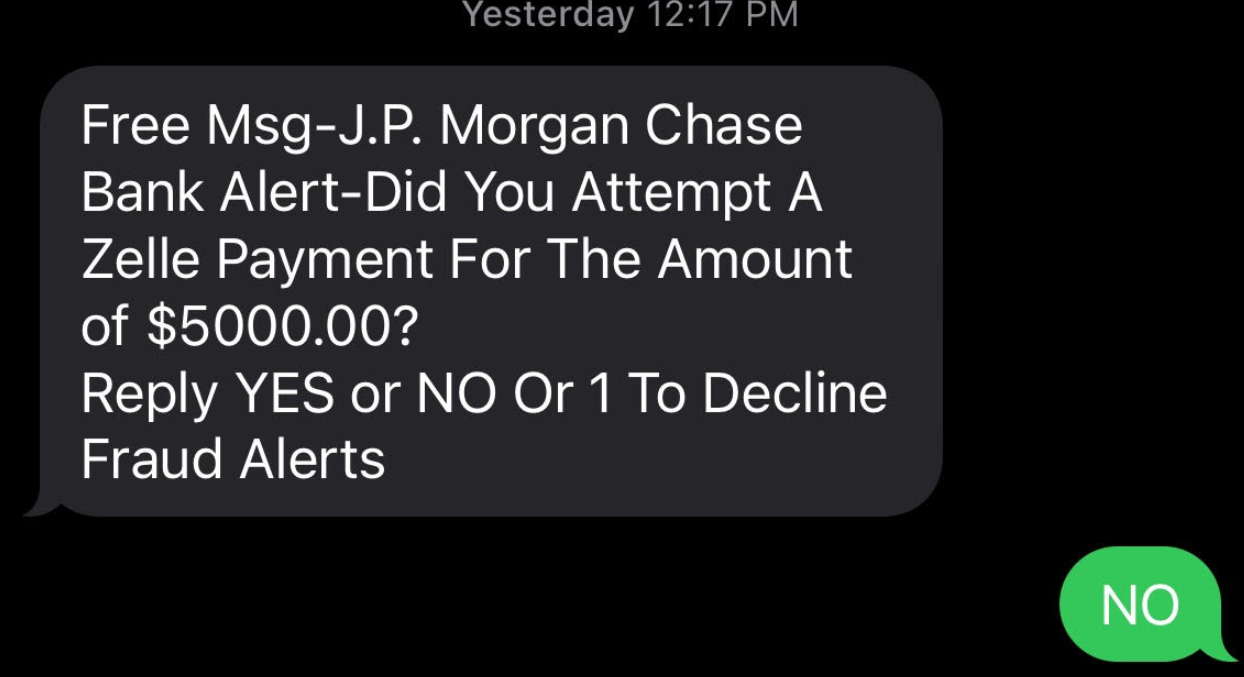
 The fraudster then uses the code to complete the password reset process, and then changes the victim’s online banking password. The fraudster then uses Zelle to transfer the victim’s funds to others.
The fraudster then uses the code to complete the password reset process, and then changes the victim’s online banking password. The fraudster then uses Zelle to transfer the victim’s funds to others.