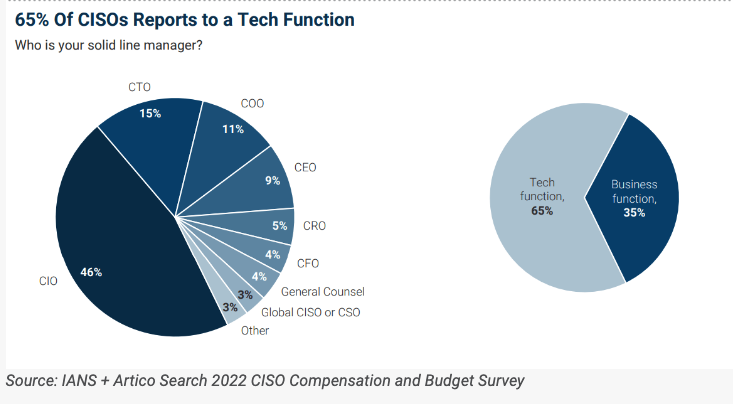
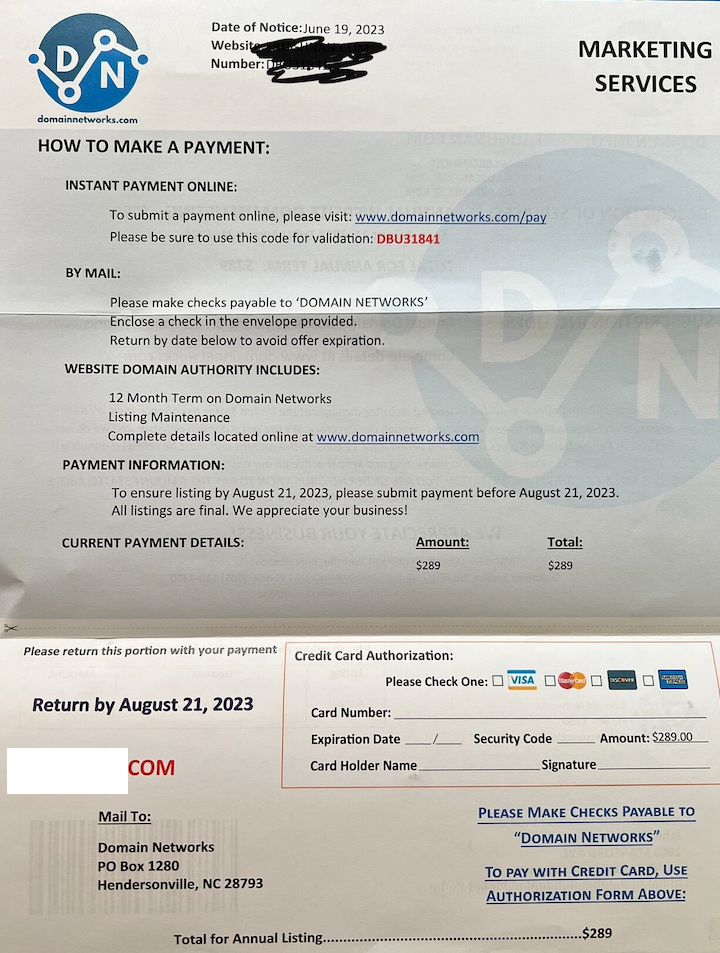
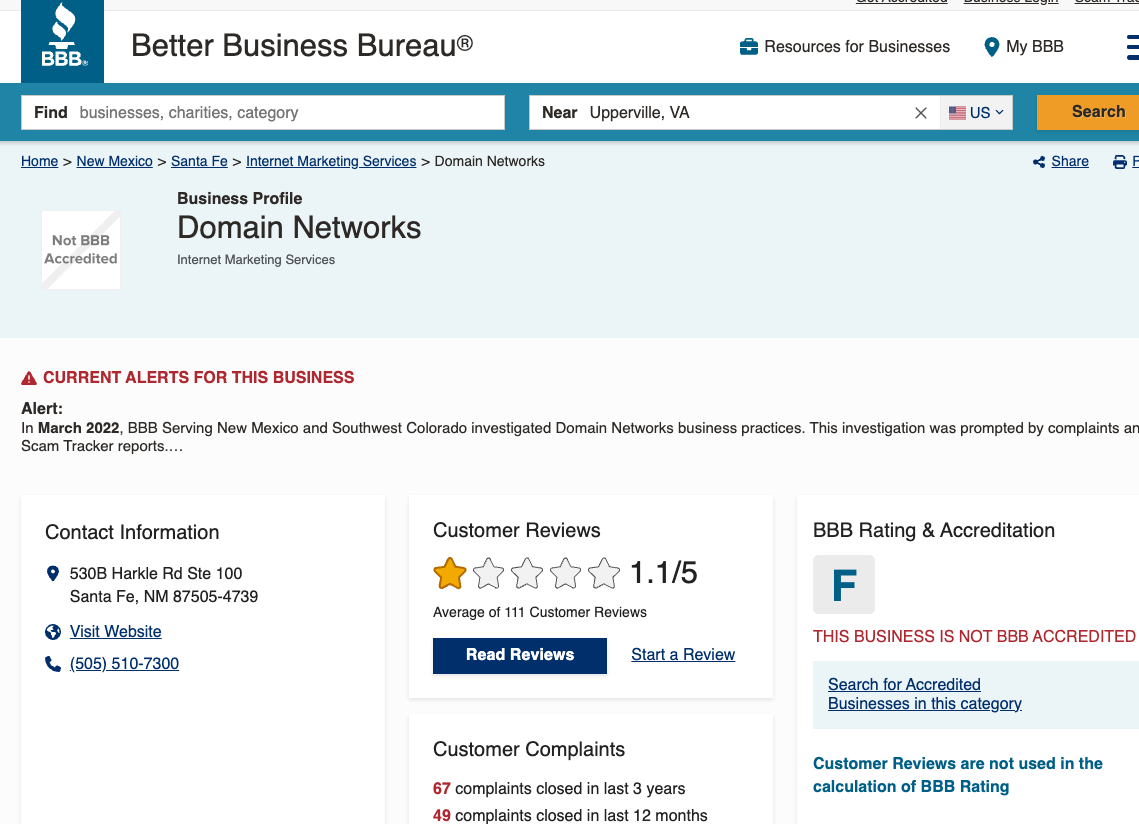
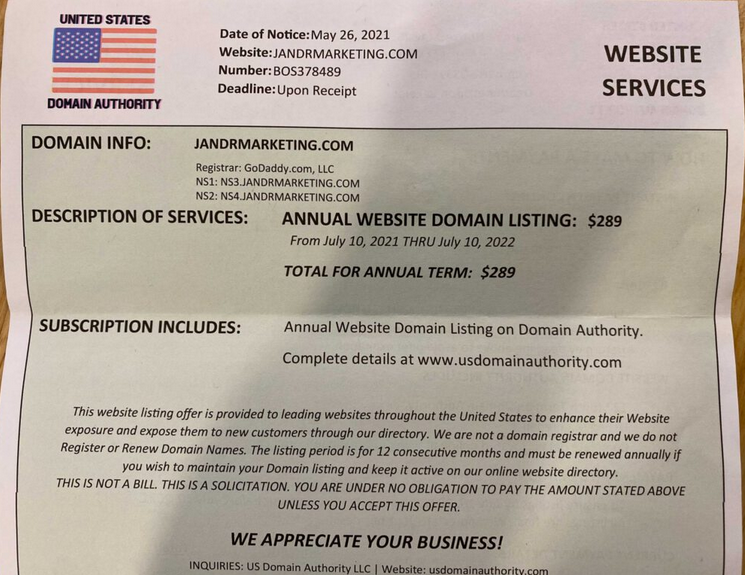
[This is Part II of a story published here last week on reporting that went into a new Hulu documentary series on the 2015 Ashley Madison hack.]
It was around 9 p.m. on Sunday, July 19, when I received a message through the contact form on KrebsOnSecurity.com that the marital infidelity website AshleyMadison.com had been hacked. The message contained links to confidential Ashley Madison documents, and included a manifesto that said a hacker group calling itself the Impact Team was prepared to leak data on all 37 million users unless Ashley Madison and a sister property voluntarily closed down within 30 days.
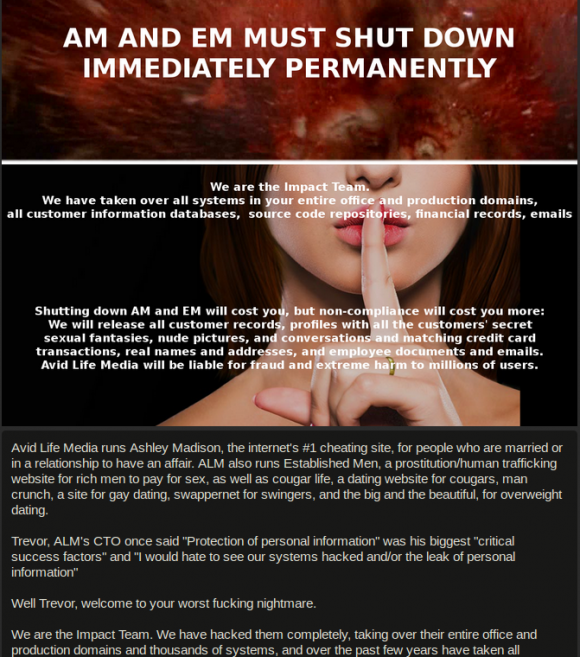
A snippet of the message left behind by the Impact Team.
The message included links to files containing highly sensitive information, including snippets of leaked user account data, maps of internal AshleyMadison company servers, employee network account information, company bank account data and salary information.
A master employee contact list was among the documents leaked that evening. Helpfully, it included the cell phone number for Noel Biderman, then the CEO of Ashley Madison parent firm Avid Life Media (ALM). To my everlasting surprise, Biderman answered on the first ring and acknowledged they’d been hacked without even waiting to be asked.
“We’re on the doorstep of [confirming] who we believe is the culprit, and unfortunately that may have triggered this mass publication,” Biderman told me on July 19, just minutes before I published the first known public report about the breach. “I’ve got their profile right in front of me, all their work credentials. It was definitely a person here that was not an employee but certainly had touched our technical services.”
On Aug 18, 2015, the Impact Team posted a “Time’s up!” message online, along with links to 60 gigabytes of Ashley Madison user data. The data leak led to the public shaming and extortion of many Ashley Madison users, and to at least two suicides. Many other users lost their jobs or their marriages. To this day, nobody has been charged in the hack, and incredibly Ashley Madison remains a thriving company.
THE CHAOS MAKER
The former employee that Biderman undoubtedly had in mind on July 19, 2015 was William Brewster Harrison, a self-described expert in search engine optimization (SEO) tricks that are designed to help websites increase their rankings for various keywords in Google and other search engines.
It is evident that Harrison was Biderman’s top suspect immediately after the breach became public because — in addition to releasing data on 37 million users a month later in August 2015 — the hackers also dumped three years worth of email they stole from Biderman. And Biderman’s inbox is full of messages about hate-filled personal attacks from Harrison.
A Native of Northern Virginia, Harrison eventually settled in North Carolina, had a son with his then-wife, and started a fence-building business. ALM hired Harrison in March 2010 to promote its various adult brands online, and it is clear that one of his roles was creating and maintaining female profiles on Ashley Madison, and creating blogs that were made to look like they were written by women who’d just joined Ashley Madison.

A selfie that William B. Harrison posted to his Facebook page in 2013 shows him holding a handgun and wearing a bulletproof vest.
It appears Harrison was working as an affiliate of Ashley Madison prior to his official employment with the company, which suggests that Harrison had already demonstrated he could drive signups to the service and help improve its standing in the search engine rankings.
What is less clear is whether anyone at ALM ever performed a basic background check on Harrison before hiring him. Because if they had, the results almost certainly would have given them pause. Virginia prosecutors charged the young 20-something Harrison with a series of misdemeanors, including trespassing, unlawful entry, drunk in public, and making obscene phone calls.
In 2008, North Carolina authorities charged Harrison with criminal extortion, a case that was transferred to South Carolina before ultimately being dismissed. In December 2009, Harrison faced charges of false imprisonment, charges that were also dropped by the local district attorney.
By the time Ashley Madison officially hired him, Harrison’s life was falling apart. His fence business had failed, and he’d just filed for bankruptcy. Also, his marriage had soured, and after a new arrest for driving under the influence, he was in danger of getting divorced, losing access to his son, and/or going to jail.
It also seems likely that nobody at ALM bothered to look at the dozens of domain names registered to Harrison’s various Vistomail.com email addresses, because had they done so they likely would have noticed two things.
One is that Harrison had a history of creating websites to lambaste companies he didn’t like, or that he believed had slighted him or his family in some way. Some of these websites included content that defamed and doxed executives, such as bash-a-business[.]com, google-your-business[.]com, contact-a-ceo[.]com, lowes-is-a-cancer[.]com (according to Harrison, the home improvement chain once employed his wife).
A background check on Harrison’s online footprint also would have revealed he was a self-styled rapper who claimed to be an active menace to corporate America. Harrison’s website lyrical-gangsta[.]com included a number of works, such as “Slim Thug — I Run — Remix Spoof,” which are replete with menacing words for unnamed corporate executives:
[HOOK]
I surf the net all night n day (the web love thug)
cuz I still surf the net all night n day
yuhh I type for my mind, got smart for my ego
still running circles round them, what’s good?
cuz I still surf, the net all night n day,
I cant stay away.
They don’t make to [sic] many hackers like me
bonafide hustler certified G
still pumpin’ the TOP 10 results
if you got the right dough!
think the results are fake? sucka Google ME
smarter than executives, bigger then Wal-Mart
Nelly strugglin’ with the fact that I’m #1 NOW
street boys know me, ain’t nuttin’ new
about to make my mill, with an all new crew
I-95 execs don’t know what to do, or where to go
watchin them stocks evaporate all their dough
I already left the hood, got up off the streets
its in my blood im a gangsta till Im deceased
moving lumber for money or typin’ in a zone
all night hackin’ till 6 in the mornin
that shit im focusin’ on, stronger then cologne
you can prolly smell the jealousy
through your LCD screen
if you still broke– better work for some green
called them Fortune execs on that legal bluff
cuz the Feds busy raidin other stuff
Imma run the Net til im six feet under
I’m a leave my mark — no reason to wonder
(Yea Yea) Continue reading →