Microsoft and identity management platform Okta both this week disclosed breaches involving LAPSUS$, a relatively new cybercrime group that specializes in stealing data from big companies and threatening to publish it unless a ransom demand is paid. Here’s a closer look at LAPSUS$, and some of the low-tech but high-impact methods the group uses to gain access to targeted organizations.
First surfacing in December 2021 with an extortion demand on Brazil’s Ministry of Health, LAPSUS$ made headlines more recently for posting screenshots of internal tools tied to a number of major corporations, including NVIDIA, Samsung, and Vodafone.
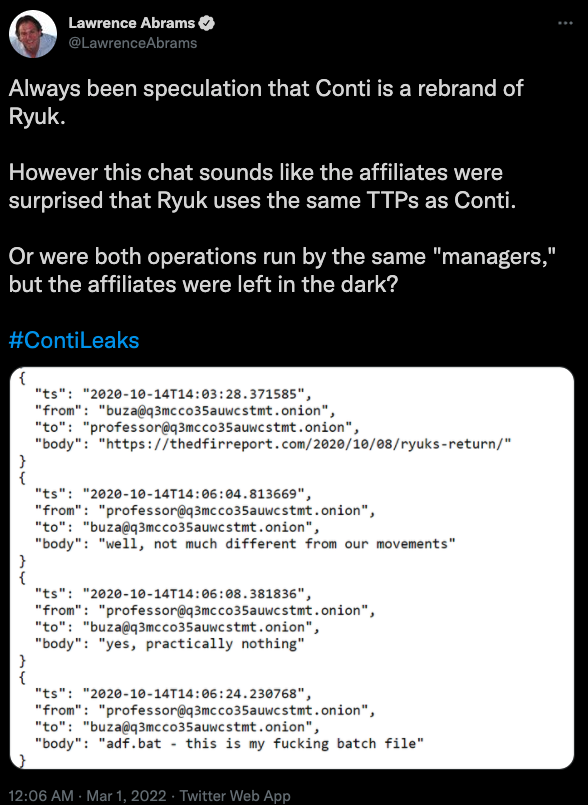
On Tuesday, LAPSUS$ announced via its Telegram channel it was releasing source code stolen from Microsoft. In a blog post published Mar. 22, Microsoft said it interrupted the LAPSUS$ group’s source code download before it could finish, and that it was able to do so because LAPSUS$ publicly discussed their illicit access on their Telegram channel before the download could complete.
One of the LAPSUS$ group members admitted on their Telegram channel that the Microsoft source code download had been interrupted.
“This public disclosure escalated our action allowing our team to intervene and interrupt the actor mid-operation, limiting broader impact,” Microsoft wrote. “No customer code or data was involved in the observed activities. Our investigation has found a single account had been compromised, granting limited access. Microsoft does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk.”
While it may be tempting to dismiss LAPSUS$ as an immature and fame-seeking group, their tactics should make anyone in charge of corporate security sit up and take notice. Microsoft says LAPSUS$ — which it boringly calls “DEV-0537” — mostly gains illicit access to targets via “social engineering.” This involves bribing or tricking employees at the target organization or at its myriad partners, such as customer support call centers and help desks.
“Microsoft found instances where the group successfully gained access to target organizations through recruited employees (or employees of their suppliers or business partners),” Microsoft wrote. The post continues:
“DEV-0537 advertised that they wanted to buy credentials for their targets to entice employees or contractors to take part in its operation. For a fee, the willing accomplice must provide their credentials and approve the MFA prompt or have the user install AnyDesk or other remote management software on a corporate workstation allowing the actor to take control of an authenticated system. Such a tactic was just one of the ways DEV-0537 took advantage of the security access and business relationships their target organizations have with their service providers and supply chains.”
The LAPSUS$ Telegram channel has grown to more than 45,000 subscribers, and Microsoft points to an ad LAPSUS$ posted there offering to recruit insiders at major mobile phone providers, large software and gaming companies, hosting firms and call centers.
Sources tell KrebsOnSecurity that LAPSUS$ has been recruiting insiders via multiple social media platforms since at least November 2021. One of the core LAPSUS$ members who used the nicknames “Oklaqq” and “WhiteDoxbin” posted recruitment messages to Reddit last year, offering employees at AT&T, T-Mobile and Verizon up to $20,000 a week to perform “inside jobs.”
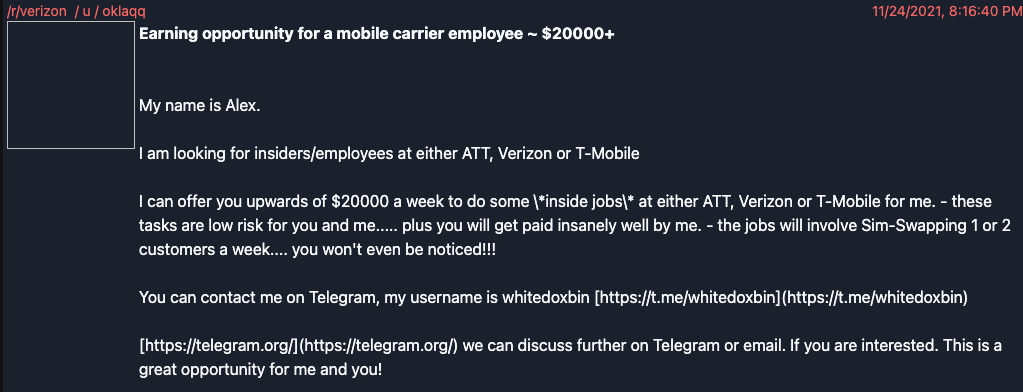
LAPSUS$ leader Oklaqq a.k.a. “WhiteDoxbin” offering to pay $20,000 a week to corrupt employees at major mobile providers.
Many of LAPSUS$’s recruitment ads are written in both English and Portuguese. According to cyber intelligence firm Flashpoint, the bulk of the group’s victims (15 of them) have been in Latin America and Portugal.
“LAPSUS$ currently does not operate a clearnet or darknet leak site or traditional social media accounts—it operates solely via Telegram and email,” Flashpoint wrote in an analysis of the group. “LAPSUS$ appears to be highly sophisticated, carrying out increasingly high-profile data breaches. The group has claimed it is not state-sponsored. The individuals behind the group are likely experienced and have demonstrated in-depth technical knowledge and abilities.”
Microsoft said LAPSUS$ has been known to target the personal email accounts of employees at organizations they wish to hack, knowing that most employees these days use some sort of VPN to remotely access their employer’s network.
“In some cases, [LAPSUS$] first targeted and compromised an individual’s personal or private (non-work-related) accounts giving them access to then look for additional credentials that could be used to gain access to corporate systems,” Microsoft wrote. “Given that employees typically use these personal accounts or numbers as their second-factor authentication or password recovery, the group would often use this access to reset passwords and complete account recovery actions.”
In other cases, Microsoft said, LAPSUS$ has been seen calling a target organization’s help desk and attempting to convince support personnel to reset a privileged account’s credentials.
“The group used the previously gathered information (for example, profile pictures) and had a native-English-sounding caller speak with the help desk personnel to enhance their social engineering lure,” Microsoft explained. “Observed actions have included DEV-0537 answering common recovery prompts such as “first street you lived on” or “mother’s maiden name” to convince help desk personnel of authenticity. Since many organizations outsource their help desk support, this tactic attempts to exploit those supply chain relationships, especially where organizations give their help desk personnel the ability to elevate privileges.”
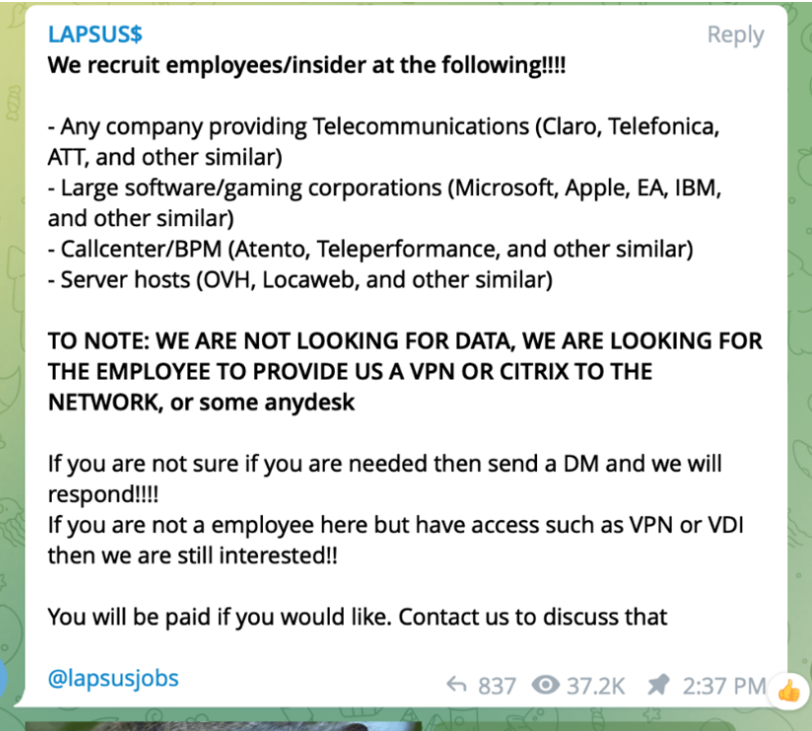
LAPSUS$ recruiting insiders via its Telegram channel.