One of the digital underground’s most popular stores for peddling stolen credit card information began selling a batch of more than three million new card records this week. KrebsOnSecurity has learned the data was stolen in a lengthy data breach at more than 100 Dickey’s Barbeque Restaurant locations around the country.
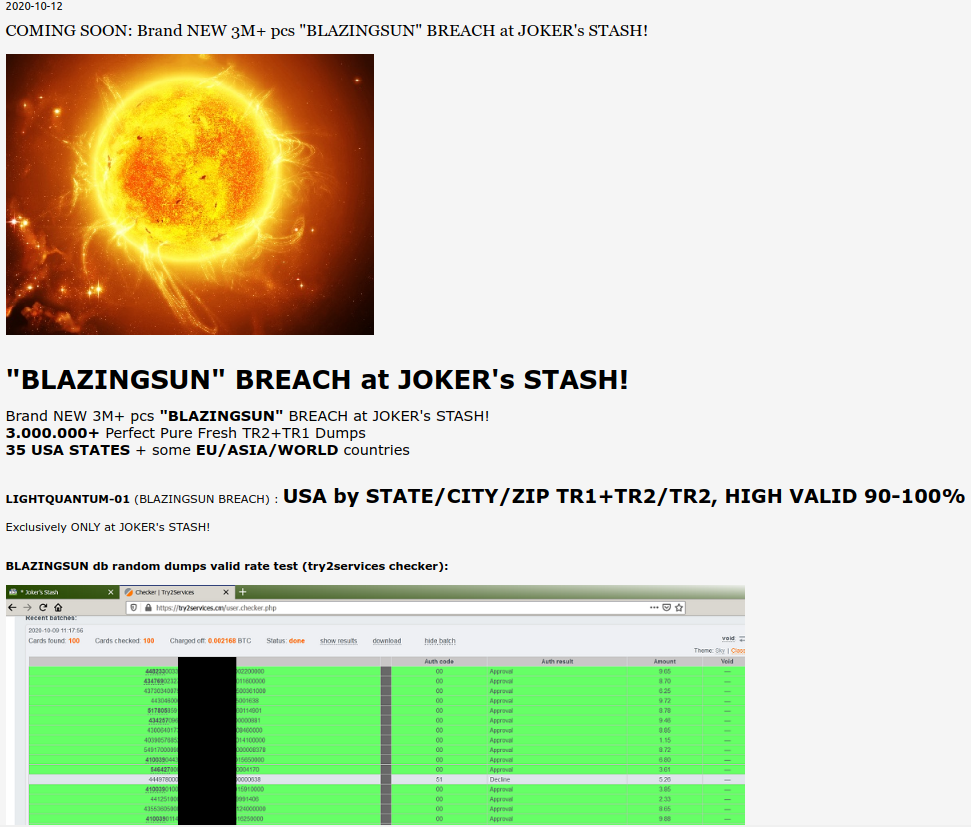
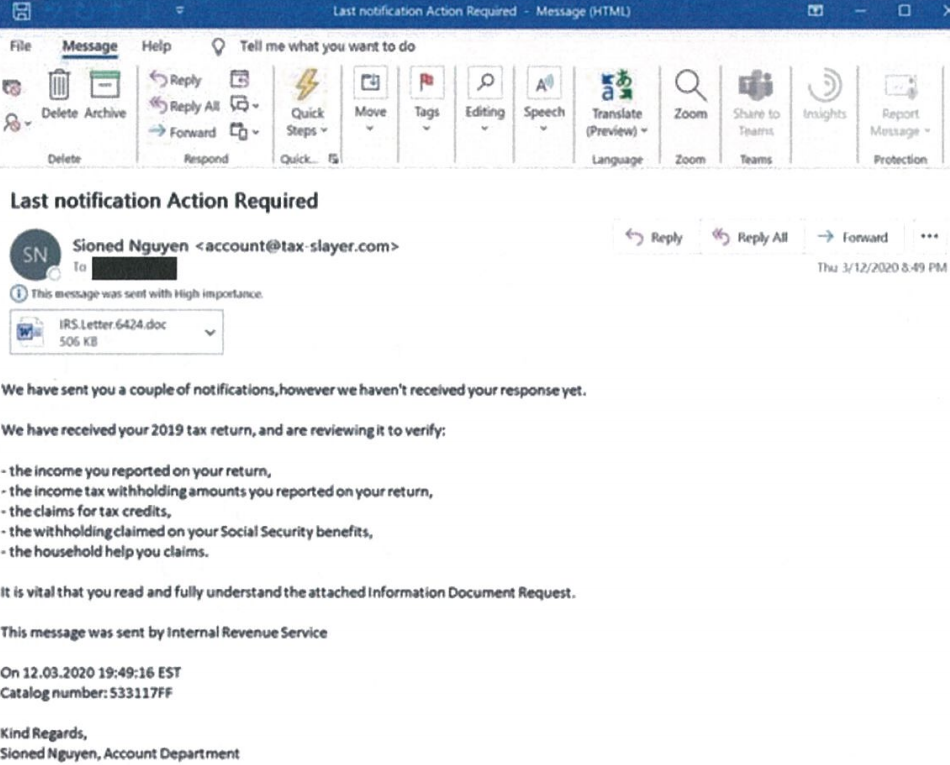
An ad on the popular carding site Joker’s Stash for “BlazingSun,” which fraud experts have traced back to a card breach at Dickey’s BBQ.
On Monday, the carding bazaar Joker’s Stash debuted “BlazingSun,” a new batch of more than three million stolen card records, advertising “valid rates” of between 90-100 percent. This is typically an indicator that the breached merchant is either unaware of the compromise or has only just begun responding to it.
Multiple companies that track the sale in stolen payment card data say they have confirmed with card-issuing financial institutions that the accounts for sale in the BlazingSun batch have one common theme: All were used at various Dickey’s BBQ locations over the past 13-15 months.
KrebsOnSecurity first contacted Dallas-based Dickey’s on Oct. 13. Today, the company shared a statement saying it was aware of a possible payment card security incident at some of its eateries:
“We received a report indicating that a payment card security incident may have occurred. We are taking this incident very seriously and immediately initiated our response protocol and an investigation is underway. We are currently focused on determining the locations affected and time frames involved. We are utilizing the experience of third parties who have helped other restaurants address similar issues and also working with the FBI and payment card networks. We understand that payment card network rules generally provide that individuals who timely report unauthorized charges to the bank that issued their card are not responsible for those charges.”
The confirmations came from Miami-based Q6 Cyber and Gemini Advisory in New York City.
Q6Cyber CEO Eli Dominitz said the breach appears to extend from May 2019 through September 2020.
“The financial institutions we’ve been working with have already seen a significant amount of fraud related to these cards,” Dominitz said.
Gemini says its data indicated some 156 Dickey’s locations across 30 states likely had payment systems compromised by card-stealing malware, with the highest exposure in California and Arizona. Gemini puts the exposure window between July 2019 and August 2020.
“Low-and-slow” aptly describes the card breach at Dickie’s, which persisted for at least 13 months.
With the threat from ransomware attacks grabbing all the headlines, it may be tempting to assume plain old credit card thieves have moved on to more lucrative endeavors. Alas, cybercrime bazaars like Joker’s Stash have continued plying their trade, undeterred by a push from the credit card associations to encourage more merchants to install credit card readers that require more secure chip-based payment cards.
That’s because there are countless restaurants — usually franchise locations of an established eatery chain — that are left to decide for themselves whether and how quickly they should make the upgrades necessary to dip the chip versus swipe the stripe.
“Dickey’s operates on a franchise model, which often allows each location to dictate the type of point-of-sale (POS) device and processors that they utilize,” Gemini wrote in a blog post about the incident. “However, given the widespread nature of the breach, the exposure may be linked to a breach of the single central processor, which was leveraged by over a quarter of all Dickey’s locations.” Continue reading