The Washington Post acknowledged today that a sophisticated phishing attack against its newsroom reporters led to the hacking of its Web site, which was seeded with code that redirected readers to the Web site of the Syrian Electronic Army hacker group. According to information obtained by KrebsOnSecurity, the hack began with a phishing campaign launched over the weekend that ultimately hooked one of the paper’s lead sports writers.
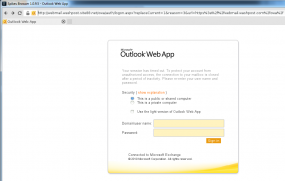
This phishing page used by the Syrian Electronic Army spoofed The Post’s’ internal email login page.
On Tuesday morning, KrebsOnSecurity obtained information indicating that a phishing campaign targeting the Post’s newsroom had been successful, and that the attackers appear to have been seeking email access to Post reporters who had Twitter accounts. The Post did not respond to requests for comment.
Update, August 16, 10:07 a.m. ET: Post spokesperson Kris Coratti finally responded, stating that the phishing attack and the site compromise were two separate incidents, and that one did not necessarily lead to the other. She emphasized that the site hack was the result of an attack on Outbrain, a third-party content recommendation site.
Original story:
But in a brief acknowledgment published today, The Post allowed that it had in fact been hacked, and in an update to that statement added that the source of the compromise was a phishing attack apparently launched by the SEA. From that message:
“A few days ago, The Syrian Electronic Army, allegedly, subjected Post newsroom employees to a sophisticated phishing attack to gain password information. The attack resulted in one staff writer’s personal Twitter account being used to send out a Syrian Electronic Army message. For 30 minutes this morning, some articles on our web site were redirected to the Syrian Electronic Army’s site. The Syrian Electronic Army, in a Tweet, claimed they gained access to elements of our site by hacking one of our business partners, Outbrain. We have taken defensive measures and removed the offending module. At this time, we believe there are no other issues affecting The Post site.”
According to sources, Post sports writer Jason Reid was among those who fell for a phishing scam that spoofed The Posts’s internal Outlook Web Access email portal (see screenshot above). Reid’s hacked email account was then used to send additional — likely malware-laced — phishing emails to other newsroom employees (see screenshot below). Reid did not respond to requests for comment.
Other well-known Posties came close to be tricked by the phishing attack. One of those nearly-phished was veteran Post staffer Gene Weingarten, one of the Post’s Pulitzer Prize winning editors and writers. Reached via email for comment, Weingarten was characteristically self-effacing about the whole ordeal (full disclosure: Gene edited my very first story to appear in The Washington Post, a 1996 Style section piece about living in the late President Gerald Ford‘s house, titled, “My Gerry Built Home“).
“I was phished….one of four, but I never entered any creds,” Weingarten wrote. “I’m stupid, but not THAT stupid.”
This type of phishing attack bears the hallmark of the SEA, which has taken credit for hijacking the Twitter accounts of several news outlets, perhaps most famously that of The Associated Press earlier this year. That campaign — which culminated in an unauthorized tweet sent from the AP’s Twitter account falsely claiming that bombs had exploded in the White House — briefly sent the Dow Industrial Average down 140 points.
As this incident highlights, phishing attacks and the phishers themselves are growing in sophistication. A survey released last month by Verizon Communications Inc. found nearly every incident of online espionage in 2012 involved some sort of phishing attack.
Update, August 16, 11:00 a.m. ET: One astute reader pointed out that the numeric Internet address (31.170.164.145) connected to the domain (site88[dot]net – see first screen shot above) used in the phishing attack against the Post this past weekend resides on the same subnet and hosting provider as blogs and Web sites belonging to some of the top Syrian Electronic Army members, including:
thepro[dot]sy (31.170.162.145)
victor[dot[thepro[dot]sy (31.170.162.145)
blog[dot]thepro[dot]sy (31.170.161.41)





Hah! “Sports Writer Hooked by Phish”
Haha, as my friend Allison just quipped, where were you when I was trying to think of a good headline! 🙂
Man, all this talk of the Post has me nostalgic. If there’s one thing I miss, it is having talented editors who can write kickass headlines.
At the Wash Post, they are gone Brian. All the talent was retired.
Maybe Jeff Bezos will hire the talented writers back.
Do not tempt me to offer to write your headlines. 😉
These major events really show the need for better prevention of phishing attacks. Most organizations are still focused on attacks from 10 years ago when phishing attempts is what they should really be targeting.
http://www.washingtonpost.com/blogs/the-switch/wp/2013/08/15/heres-how-the-syrian-electronic-armys-hack-worked/
“The Post’s engineers have confirmed that Outbrain was the source of the vulnerability. Outbrain has also confirmed that its systems have been attacked, presumably a reference to the SEA.”
They say it was a 3rd party getting hacked Outbrain.com
Brian, thanks for the link to the Jerry Built Home story, it was a good read. Your early-adult life sounds like mine and a bunch of my friends! In fact, Animal House comes to mind…
The hacking news were also affected due to the outbrain issue http://thehackernews.com/2013/08/Outbrain-hacked-Syrian-Electronic-Army.html
What about Tom’s Hardware? I know they use it between pages for something or other but I usually adblock/no script the crap out of that site anyway.
Brian, if you are able to obtain a copy of the phishing email used in this attack, can you please provide it to me? I would like to use it for employee training purposes and I don’t believe I see it here. Thank you.
I always knew sports writers were a sharp bunch. Maybe you should explain to them the difference between a phish and a fish. For a consulting fee, of course. Then you could do the same for their music reviewers about phish and Phish.
Applied against the Washington Post the next time may be a more sophisticated “new item” written within a clever propaganda scheme and inserted, automated and published before some editor is thorough or quick enough; then forcing one of those humiliating “retractions”, which quite naturally the august Washington Post will be loath to do.
Their Pulitzer prize winners are no doubt aware of potential distortions in their writing, post publication. [no pun intended].
There are, I guess, many other frightening and troublesome possibilities for serious distortions in the “News” as spun by the Post and New York Times and the BBC……I post this [no pun intended] as an inherent skeptic of the ‘Mainstream Media’.
What an effing can of worms.
GO! NSA!….GO! CIA!
What scares me also is how much news organizations rely on hackers for information. Even Independent news media uses malicious hackers as sources now. Its like they are a substitute for their own investigative journalism.
Talking about propaganda…..look at most forums and blogs online, where it seems US citizens are always the minority. Even when its an American server like a game server or blog related to America alot of times Sometimes i feel like most americans just go on androids and iphones to a couple main sites like facebook or twitter, and the rest of the internet is just one big anti american propoganda machine.
…typo correction:
Read, “…news item…”
I hope Patrick’s PIN number for his bridge changes for each call, or that he was told to change the PIN after it was leaked here in the e-mail “Top Brass huddle”
It was on the front page of the Style section this morning. Not sure why it was there rather than Metro.
http://www.washingtonpost.com/lifestyle/style/syrian-group-hacks-washington-post-web-site/2013/08/15/4e60d952-05bd-11e3-88d6-d5795fab4637_story.html
“SEA hacks WaPo again. Moves article from Metro to Style.”
Kind of surprised to see that email displayed here in its entirety. Isn’t it standard practice to redact at least phone numbers and PINs?
Not sure if posting the un-redacted email is the best thing either… there is likely some good information in there that could be abused (Patrick’s bridge number to start) not to mention the all the names of people involved in the response… if I was SEA, that would be my next target list.
Time.com was also compromised in the same way. CNN was targeted also.
http://www.reuters.com/article/2013/08/15/washingtonpost-hacked-idUSL2N0GG1YW20130815
site88[dot]net (of the phishing page) WAS residing on IP 208.43.151.204, which has a low-level alert by one intrusion detection system.
For what it’s worth, the current blogs and Web sites belonging to SEA members reside on the 31.170.160.1 to 31.170.163.254 network running the nameserver / domain name server ‘Main Hosting Servers’ which hosts 208.43.151.204 domains (where site88[dot]net also formally resided).
Do we know if the site is clean now?
“I’m stupid, but not THAT stupid.”
So, by way of Weingarten’s statement, we can safely assume that Jason Reid was that stupid. Man, would love to hear the small talk between those two when they meet at the water cooler. 😉
“The Post did not respond to requests for comment.” Curious, How long does a writer, blogger, reporter, wait for comments once they are asked for?
In this case, I waited less than 24 hours, but only because I was still chasing the story. The Post only got back to me after my story ran (3 days after, to be exact).