I shared a meal not long ago with a source who works at a financial services company. The subject of ransomware came up and he told me that a server in his company had recently been infected with a particularly nasty strain that spread to several systems before the outbreak was quarantined. He said the folks in finance didn’t bat an eyelash when asked to authorize several payments of $600 to satisfy the Bitcoin ransom demanded by the intruders: After all, my source confessed, the data on one of the infected systems was worth millions — possibly tens of millions — of dollars, but for whatever reason the company didn’t have backups of it.
This anecdote has haunted me because it speaks volumes about what we can likely expect in the very near future from ransomware — malicious software that scrambles all files on an infected computer with strong encryption, and then requires payment from the victim to recover them.

What we can expect is not only more targeted and destructive attacks, but also ransom demands that vary based on the attacker’s estimation of the value of the data being held hostage and/or the ability of the victim to pay some approximation of what it might be worth.
In an alert published today, the U.S. Federal Bureau of Investigation (FBI) warned that recent ransomware variants have targeted and compromised vulnerable business servers (rather than individual users) to identify and target hosts, thereby multiplying the number of potential infected servers and devices on a network.
“Actors engaging in this targeting strategy are also charging ransoms based on the number of host (or servers) infected,” the FBI warned. “Additionally, recent victims who have been infected with these types of ransomware variants have not been provided the decryption keys for all their files after paying the ransom, and some have been extorted for even more money after payment.”
According to the FBI, this recent technique of targeting host servers and systems “could translate into victims paying more to get their decryption keys, a prolonged recovery time, and the possibility that victims will not obtain full decryption of their files.”
Today there are dozens of ransomware strains, most of which are sold on underground forums as crimeware packages — with new families emerging regularly. These kits typically include a point-and-click software interface for selecting various options that the ransom installer may employ, as well as instructions that tell the malware where to direct the victim to pay the ransom. Some kits even bundle the HTML code needed to set up the Web site that users will need to visit to pay and recover their files.
To some degree, a variance in ransom demands based on the victim’s perceived relative wealth is already at work. Lawrence Abrams, owner of the tech-help site BleepingComputer, said his analysis of multiple ransomware kits and control channels that were compromised by security professionals indicate that these kits usually include default suggested ransom amounts that vary depending on the geographic location of the victim.
“People behind these scams seem to be setting different rates for different countries,” Abrams said. “Victims in the U.S. generally pay more than people in, say, Spain. There was one [kit] we looked at recently that showed while victims in the U.S. were charged $200 in Bitcoin, victims in Italy were asked for just $20 worth of Bitcoin by default.”
In early 2016, a new ransomware variant dubbed “Samsam” (PDF) was observed targeting businesses running outdated versions of Red Hat‘s JBoss enterprise products. When companies were hacked and infected with Samsam, Abrams said, they received custom ransom notes with varying ransom demands.
“When these companies were hacked, they each got custom notes with very different ransom demands that were much higher than the usual amount,” Abrams said. “These were very targeted.”
Which brings up the other coming shift with ransomware: More targeted ransom attacks. For the time being, most ransomware incursions are instead the result of opportunistic malware infections. The first common distribution method is spamming the ransomware installer out to millions of email addresses, disguising it as a legitimate file such as an invoice.
More well-heeled attackers may instead or also choose to spread ransomware using “exploit kits,” a separate crimeware-as-a-service product that is stitched into hacked or malicious Web sites and lying in wait for someone to visit with a browser that is not up to date with the latest security patches (either for the browser itself or for a myriad of browser plugins like Adobe Flash or Adobe Reader).
But Abrams said that’s bound to change, and that the more targeted attacks are likely to come from individual hackers who can’t afford to spend thousands of dollars a month renting exploit kits.
“If you throw your malware into a good exploit kit, you can achieve a fairly wide distribution of it in a short amount of time,” Abrams said. “The only problem is the good kits are very expensive and can cost upwards of $4,000 per month. Right now, most of these guys are just throwing the ransomware up in the air and wherever it lands is who they’re targeting. But that’s going to change, and these guys are going to start more aggressively targeting really data intensive organizations like medical practices and law and architectural firms.”
Earlier this year, experts began noticing that ransomware purveyors appeared to be targeting hospitals — organizations that are extremely data-intensive and heavily reliant on instant access to patient records. Indeed, the above-mentioned SamSAM ransomware family is thought to be targeting healthcare firms.
According to a new report by Intel Security, the healthcare sector is experiencing over 20 data loss incidents per day related to ransomware attacks. The company said it identified almost $100,000 in payments from hospital ransomware victims to specific bitcoin accounts so far in 2016.
RUSSIAN ROULETTE
An equally disturbing trend in ransomware is the incidence of new strains which include the ability to randomly delete an encrypted file from the victim’s machine at some predefined interval –and to continue doing so unless and until the ransom demand is paid or there are no more files to destroy.
Abrams said the a ransomware variant known as “Jigsaw” debuted this capability in April 2016. Jigsaw also penalized victims who tried to reboot their computer in an effort to rid the machine of the infection, by randomly deleting 1,000 encrypted files for each reboot.
“Basically, what it would do is show a two hour countdown clock, and when that clock got to zero it would delete a random encrypted file,” Abrams said. “And then every hour after that it would double the number of files it deleted unless you paid.”
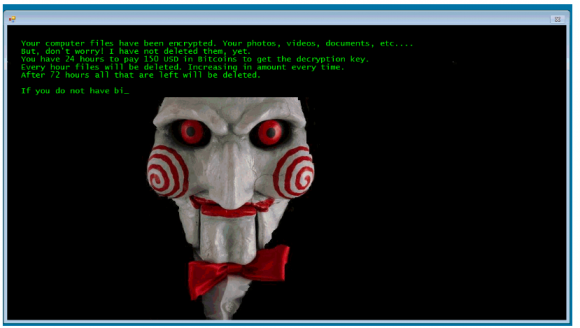
Part of the ransom note left behind by Jigsaw. Image: Bleepingcomputer.com
Abrams said this same Russian Roulette feature recently has shown up in other ransomware strains, including one called “Stampado” and another dubbed “Philadelphia.”
“Philadelphia has a similar feature where [one] can specify how many files it deletes and how often,” he said.
Most ransomware variants have used some version of the countdown clock, with victims most often being told they have 72 hours to pay the ransom or else kiss their files goodbye forever. In practice, however, the people behind these schemes are usually happy to extend that deadline, but the ransom demands almost invariably increase significantly at that point.
The introduction of a destructive element tied to a countdown clock is especially worrisome given how difficult it can be for the unlearned to obtain the virtual Bitcoin currency needed to pay the ransom, Abrams said.
“I had an architectural firm reach out to me, and they’d decided to pay the ransom,” he said. “So I helped my contact there figure out how to create an account at Coinbase.com and get funds into there, but the whole process took almost a week.”
Hoping to get access to his files more immediately, Abrams’ contact at the architectural firm inquired about more speedy payment options. Abrams told him about localbitcoins.com, which helps people meet in person to exchange bitcoins for cash. In the end, however, the contact wasn’t comfortable with this option.
“It’s not hard to see why,” he said. “Some of the exchangers on there have crazy demands, like ‘Meet me at the local Starbucks, and absolutely no phones!’ It really sort of feels like a drug deal.”
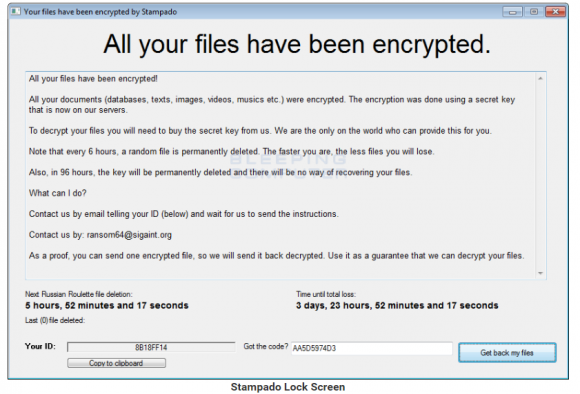
The ransom demand left by Stampado. Image: Bleepingcomputer.com
HOW TO PREVENT ATTACKS & WHAT TO DO IF YOU’RE A VICTIM
In its alert published today, the FBI urged victims of ransomware incidents to report the crimes to federal law enforcement to help the government “gain a more comprehensive view of the current threat and its impact on U.S. victims.”
Specifically, the FBI is asking victims to report the date of infection; the ransomware variant; how the infection occurred; the requested ransom amount; the actors Bitcoin wallet address; the ransom amount paid (if any); the overall losses associated with the ransomware infection; and a victim impact statement.
Previous media reports have quoted an FBI agent saying that the agency condones paying such ransom demands. But today’s plea from the feds to ransomware victims is unequivocal on this point:
“The FBI does not support paying a ransom to the adversary,” the agency advised. “Paying a ransom does not guarantee the victim will regain access to their data; in fact, some individuals or organizations are never provided with decryption keys after paying a ransom.”
What can businesses do to lessen the chances of becoming the next ransomware victim? The FBI has the following tips:
- Regularly back up data and verify the integrity of those backups. Backups are critical in ransomware incidents; if you are infected, backups may be the best way to recover your critical data.
- Secure your backups. Ensure backups are not connected to the computers and networks they are backing up. Examples might include securing backups in the cloud or physically storing them offline. It should be noted, some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real-time, also known as persistent synchronization.
- Scrutinize links contained in e-mails and do not open attachments included in unsolicited e-mails.
- Only download software – especially free software – from sites you know and trust. When possible, verify the integrity of the software through a digital signature prior to execution.
- Ensure application patches for the operating system, software, and firmware are up to date, including Adobe Flash, Java, Web browsers, etc.
- Ensure anti-virus and anti-malware solutions are set to automatically update and regular scans are conducted.
- Disable macro scripts from files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full Office Suite applications.
- Implement software restrictions or other controls to prevent the execution of programs in common ransomware locations, such as temporary folders supporting popular Internet browsers, or compression/decompression programs, including those located in the AppData/LocalAppData folder.
Additional considerations for businesses include the following:
- Focus on awareness and training. Because end users are often targeted, employees should be made aware of the threat of ransomware, how it is delivered, and trained on information security principles and techniques.
- Patch all endpoint device operating systems, software, and firmware as vulnerabilities are discovered. This precaution can be made easier through a centralized patch management system.
- Manage the use of privileged accounts by implementing the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary; they should operate with standard user accounts at all other times.
- Configure access controls with least privilege in mind. If a user only needs to read specific files, he or she should not have write access to those files, directories, or shares.
- Use virtualized environments to execute operating system environments or specific programs.
- Categorize data based on organizational value, and implement physical/logical separation of networks and data for different organizational units. For example, sensitive research or business data should not reside on the same server and/or network segment as an organization’s e-mail environment.
- Require user interaction for end user applications communicating with Web sites uncategorized by the network proxy or firewall. Examples include requiring users to type in information or enter a password when the system communicates with an uncategorized Web site.
- Implement application whitelisting. Only allow systems to execute programs known and permitted by security policy.




Our company has had this hit a folder 2-3 times, believed to be from email links or attachments – which can be difficult to spot if you are in a department that gets a LOT of those each day like accounting or purchasing etc.
Looking at how complicated the above list of “what to do is” I see no present hope for the typical home user, especially those who are older and typically less technically savvy.
Maybe backups will go the way of auto-spawned docker containers with multiple cloud instances so you never have to worry about losing one container to a ransomware, just delete that instance and fire up another. Only loss might be the usual “since you last synced a backup” type of thing.
The typical home user can keep important files on a USB stick and only use it as needed which is Not going to be often.
And after the first time you guys still continued running Windows?!
It’s not just Windows that gets hit by this. Stop blaming the OS and start blaming the people that are doing it. Also, poor understanding of how a computer works by consumers plays a large role.
Is this a Windows phenomena or has this been seen in the wild on Linux systems? If so, is anti-virus for Linux a worthwhile thing? We struggle with this idea as AV has to be kept up to date on a daily basis these days and if it does not provide decent security, the cost likely outweighs the benefits.
This could happen on Linux as well. See https://en.wikipedia.org/wiki/Linux.Encoder.1
Having proper access control, and not running things as root, as is common on Windows (Administrator account) helps to make such attacks harder.
Linux.Encoder seems to be mostly a minor annoyance, but Red Hat is mentioned, and since the server community is threatened, that may implicate Apache, etc.
The problem with not running things with administrative privileges (root) is that too much software is designed to run as root, where there is no technical justification for doing so, other than it is just easier to write and architect it that way. This is an industry flaw which allows attacks, including ransomware, to have a wider impact than it should. And, in the business environment, this is even worse, especially as applications become more and more distributed. The problem of software unnecessarily running with administrative privileges exists in both proprietary and open source software, and this is the rule, rather than the exception (even though best practices for a couple of decades has dictated otherwise). If we, as an industry, can better ensure rule of least privilege when it comes to the credentials under which software is run, as well as all vectors of access, it will help limit the exposure for many of these attacks.
Why internalize a hidden extra cost like refactoring when there is no incentive to do so.
IT operations is the storm sewer for poor design, failure to plan, failure in planning, inaccurate targeting of goals, weak constancy of purpose, and outright greed.
Security is the river that IT operations dumps their overflow, except that the river is 5-10% the size of the storm sewer.
Another poster talked about a bunch more stupid absolutes that are equally unrealistic. Don’t show ads; yet most of the sites that have solutions someone has both seen and solved before are ad-funded. Don’t run java, yet lots of security administrative consoles need it to function day-to-day. Don’t use IE, yet if you go to any enterprise of consequence you will be forced to for say… your timesheet. Don’t visit sites with active content. Hah. LOL try surfing with noscript these days. It is unusable. My brain is not a very good renderer.
Distributed objects are the issue. There is no such thing as intelligent data; there is only data and code which operates on it. Abstraction was created for humans to simplify but it has allowed a virtually infinite layer sandwich of micro-organisms that interact in strange and interesting ways.
The issue is economic and social and manifests in IT. The IT system, with its constant human interaction, resembles a biological organism constantly hosting and fighting off foreign bodies and diseases that are forced by the demands larger system that enables it.
The answer to that question is in the article:
“In early 2016, a new ransomware variant dubbed “Samsam” (PDF) was observed targeting businesses running outdated versions of Red Hat‘s JBoss enterprise products.”
What about True Crypt and Vera Crypt? If I put all my My Docs folders in a True Crypt or Vera Crypt Container would they be safe and secure from ransomware? Would the container have to be closed, not mounted to be safe? Could the container be open and mounted and still safe?
Use true crypt/vera crypt for your off-site backups. Assume that if you are infected, the infection will have just as much (if not) more power than the user on the system, and once you open and mount data from True/Vera, it, too can become infected.
Whatever file or folder you use to back-up your data, encrypted or not, must NOT be mapped to, or logically or physically connected to, your computer.
The key is the physical and logical disconnection between your device and the back-up. Encryption is not relevant in this context.
Analogy – if your garage is connected to your house, it will most likely burn when your house catches fire. If your garage is 40 feet from your house, it won’t burn (most likely) if your house catches fire.
Having high grade door locks on your garage that are different from those in your house, have no relevance or value in that context and will do nothing to stop your garage from burning if it is connected to your house.
Just to make sure users don’t get the wrong idea –
Simply un-mapping/mounting a network drive isn’t an effective control against Locky. This ransomware attempts to enumerate and access/encrypt any network shares it can discover and has r/w access to with the account it’s running as.
Even if the machine doesn’t have the drive mapped, if the user’s account/group has access to the share Locky Will encrypt it. Seen this specifically happen in the field. And I imagine as time goes on more variants of ransomware will as well.
Is the TC container a separate partition, or just a file stored somewhere?
Because, if it’s just a file, then even if the container isn’t mounted, it can also be encrypted by the ransomware. Just because it’s encrypted by TC/VC doesn’t mean that the attacker can’t encrypt it again, causing you to lose access to all the data in that container.
Back up your data to a location that is offline or disconnected from what you’re protecting.
Would ransomware on a Mac encrypt files on an external hard drive that is not mounted and is not powered on?
I keep a Time Machine backup of docs and some media on a dual-drive external HD. I run Time Machine once every few days. The other drive is a bootable clone that is updated about once a week. I do not mount the bootable clone when Time Machine, and vice versa. If I’m not using either, the external hard drive power is off.
It appears that the only way to overcome backup file compromise is to use non-volatile media, i.e. DVD or Blue-Ray disks and close them after burning. However, that will not be a good solution for large businesses that have hundreds of GB of data that needs to be backed up daily…
@Simply Fred, if your computer processes can read & write files, then the malware can too. So I wouldn’t think True Crypt would provide protection.
Also, the container file itself could be encrypted and rendered inaccessible.
Question re these Russian Roulette countdown timers: Wouldn’t simply shutting down the infected system prevent ongoing deletions? But I guess the malware might be set up so doing that would prevent any recovery at all…
The thing with Russian Roulette (at least with Jigsaw) is that each time the process is restarted (or the computer itself), it deletes 1000 files, so just turning off the PC is not a great solution.
Do a hard (yank the power) shutdown. Physically remove the drives. Buy SATA/SAS USB adapter to plug said drives in assuming you don’t have spare server hardware already, then mount the drives as read only. Then hope the ransomware key folks eventually pop that breed of malware. You might even want to volunteer your data for them to crack.
Given that many of the skiddie types running this software just cut and run after taking payment makes doing any kind of payment just an embarassing insult to an extant injury.
Its a wonderful solution, so long as you pull the power cord to hard power it off (alternately hold the power button for 4 seconds, although the PC will see that you[ pressed the power button and trigger whatever the shutdown action is), then don’t allow it to boot off the same drive again.
Re: countdown timers, I think shutting down would probably be bad. But just pulling the power plug might work. Then pull the hard drive out and use forensic tools to image it, so you can go back to the hopefully pre-delete state. But if you’re on a laptop, that can’t remove the battery, you may be outta luck.
It depends on the progression of the infection.
Does this stuff need intervention of the Operating system to encrypt files? If the infection resides in the OS folder and spreads to other areas, then there might be hope to recover some of the files.
Maybe shutting the system down, take out the hard drive which has critical files. Find another PC that does not have anything vital on it. Attach a USB hard drive cradle to this secondary PC. Put the partially encrypted drive into the USB HDD cradle and move all important non encrypted files over to this PC.
That may save some of the files, if they can be seen. It depends on the original PC’s configuration and file structure. If it has a format to where the original OS protects some of the files from “unauthorized use”, you may be out of luck.
Remember your need to run as administrator, or elevated privileges is not always needed. A good file structure with proper permissions can corral a ransomware infection to a single system and maybe a single folder on a file server if the infection requires elevated priv’s.
Backups are essential. Not only for ransomware, but in case something crashes and burns up. Backups are incredibly easy to do. Plug in a removable hard drive to a server and let it backup files to that. When its done, simply unplug the USB connection. I suggest having TWO type USB external hard drives. One is used for any major upgrades, or used to back up things once a month. The other is used on a regular basis. This way your going to have at least 1 good backup either way, and do not have to recreate the server(s) from scratch.
One of the first things that should be done upon becoming infected, make sure the backups are stopped immediately so the infection is not applied back onto systems once again.
As for the bank – lets hope they are absolutely sure that nothing residual is on that system. All it takes is one temp file laying dormant somewhere and it may be able to communicate and potentially exfiltrate data.
Its all about the PC’s and if the Rings of Trust applies to PC, servers and networks, then crimeware would be out of business.
Technically all laptops, even ones that are glued together, can disconnect the battery. The difficulty varies from manufacturer to manufacturer, but basically you have to crack open the case (normally held together by screws – I’m looking at you, Apple. Stop gluing things together), then typically there’s a fairly easy to find set of wires coming off the battery and plugging into a receptacle on the motherboard. Disconnect that plug and voila, it’s turned off.
Two things almost everyone can do/be taught that will help to keep ransomware (and other malware) incidents down:
1. Hover (do not click) the browser over a link to see what it is and compare that to what the email or web page says. If they do not agree–exactly, do not go there.
2. Download files (if you must) to a download folder but do not click/execute/run them until they are checked out. Check a file out by right clicking on it and select a scan by your antivirus software. Even if the antivirus says the file is okay, go on to the next step. Next step: upload the file to Virus Total (second choice is VirScan, third choice is Jotti) to see what multiple antiviruses say about the file.If two or more antiviruses say the file is infected, do not use/run/execute the file–just delete it.
Regards,
Better yet, if any of them report it’s bad, delete it.
sure these solutions may wok for some things, but watch out for zero-day or currently undetected ransomware variant(s). If the “new” ransomware is a strain of an existing ransomware, your suggestion has a good chance at detecting it.
Running PC’s with elevated priv’s to surf the web is like riding a wagon of long wicked explosives through a lava field. Its disaster waiting to happen.
Most of this stuff today requires NO user intervention. A user simply has an ad displayed on the PC and before you know it, the system is being fed ransomware. Check out the TALOS blog (cisco owned):
There is a short video showing this style of attack, which currently is sent to only a small number of people out of the thousands that see that ad. I can imagine that the crooks are doing this to perfect the system.
Figure out one way to curb a crook, and they come back via two other avenues. They have all the time in the world to make people pay, and the good side typically only works at the cure for 40 hours a week. Who’s gonna come out on top ?
Old school tactics are simply NOT enough.
Though this version may have been taken down, its super fast for the crooks to stand up another, “better” version in days:
Detailed Talos Blog:
http://blog.talosintel.com/2016/09/shadowgate-takedown.html
Talos Video:
https://youtu.be/-E56rSF01no
Yeah, but 99% are delivered via email.
same can be said for emails. Typically to stay below the radar and obtain a “low threat score” the crooks imbed a JPG in the email. This does two things. One it gives an avenue of infection, and it shows the person on the other end has opened the email, since the photo (of any size – even if it is a pixel) resides on a server that is controlled by the crooks.
The concept is the same, but a different delivery method.
Proper network segmentation would make a great deal of sense. It won’t stop the infection but it will stop it from spreading through the network. As long as you pay these people they’ll continue to amp up their attacks.
“Philadelphia” decryptor is released.
One ransomware issue I remember was so easily fixed by just formatting C drive and reinstalling the OS. Most people wont do this for fear of losing everything on the drive. The thing is, only the OS was wiped out. All other non-os related data was kept on D drive as a seperate partition (with the OS only taking a small portion of the total physical drive). The effort it took to initially set this up to start with was basically meaningless when considering what would have happened otherwise.
My only point here is that these things can be dealt with without ‘paying ransom’ (which is pretty much a fruitless venture).
Just because it worked once doesn’t mean that it will work now or later. Software tends to get better over time.
Doing things this way might not be efficient for an office of hundreds of computers but it does work quite well for home users. The files on D drive could still be tampered with but the main issue can be effectively removed with a format of C.
Paying the ransom (in bitcoin or whatever) is just plain stupid.
Better yet keep the really important files on a USB stick drive and only use it as needed. Most people don’t have that much and don’t need them that often.
Ya know……
With all the negative talk and disdain people give for WinXp there is something that no one seems to care anything about…..
Most (if not all) thumb drives still run on FAT32 which is from way back in the Win98 days. Not even NTFS (Win2K/WinXP). It just amazes me that the use of such outdated technology can still be suggested while at the same time rejecting things that are newer under the thinking that the older stuff needs to go away. If the older stuff is not safe, secure, or even desired……then FAT32 surely is part of all that.
Part of the reason for using FAT on USB drives is that it’s able to be read by almost any kind of operating system. NTFS support for OS X and Linux is fairly limited out of the box, and with licensing from Microsoft needed for NTFS, most manufacturers go with something that will work on any kind of system.
I do understand. But there are reasons why USB drives can be very dangerous to use. My point is that it is outdated technology (like FAX machines). The inability to turn loose of this antiquated tech calls into question anything that gets said by anyone that calls for turning loose of antiquated tech. While we are all suffering from a ransomware problem that is getting worse, no one seems willing to actually deal with the problem.
It’s difficult to take security seriously when no one takes security seriously.
How can you count on that, when the new variants can actually go out on the internet and find your cloud backups? Finding your files on the PC isn’t even a speed bump for the new bugs.
Regardless of who you are, what job you have, how much money you have, or how many computers you have…..
There is absolutely nothing that anyone can do that will be 100% effective. There WILL be something vulnerable somewhere. This is the position that people need to start from.
I don’t use the cloud for anything willingly. I really have no purpose for it. I do keep backups (mostly offline and some offsite).
There are things that can be (and should be) done:
a) separate the OS from other data
b) filter out as much advertising (and other) as you can
c) don’t use Java
d) don’t use Flash
e) don’t use IE (edge)
f) avoid websites that force the use of Java, Flash, IE, and Active X
g) don’t use any kind of ‘preview pane’ with any email
h) don’t open email from unkown or unsolicited sources
i) don’t just hap-hazardly install/use apps/programs without regard
j) take the time and effort to know your computer (what’s on it and what’s not)
——————
You will not win the war but if you do these things you will be alot happier and alot less frustrated as you live online
Thank you mike. This is very helpful.
The newer ones scan all your drives, and your network drives.
I fully expect to hear about ransomware on self-driving cars in a couple years.
“$40 in bitcoin or you’ll be late to airport.” Who wouldn’t pay that?
“$200 or I’ll spam your contacts that you left from a Planned Parenthood just now.”
…and now I see that yesterday is released Stampado decrypter, by Emsisoft.
Just curious, does Cryptoprevent or Malwarebytes AntiRansomware help in these attacks?
By making group policy edits to extensively block permission to do encryption tasks. You would have to pay for the Malwarebytes version, where Foolish IT provides it for free. I just downloaded it today – Brian’s articles finally made me nervous enough, even though I have a full image backup of my drive stashed away.
Why have these ransomware attacks been so successful?
Because its a vector that attacks the weakest links-backups.
In any IT department, backups are the job that nobody wants yet its the most critical aspect of ongoing operations. Being responsible for backups is akin to being responsible for washing the latrine.
It is also cheaper for many companies to just pay the ransomware rather than invest in a good security and backup solution.
JR, you’re absolutely correct, performing backups is a time consuming, pain in the ass “menial” chore, usually farmed out to the lowest person on the totem pole…and restoring from backups? wow…also an excruciating process….if someone could actually invent a full on the fly backup, where you didn’t have to time everything, pull stuff, label it, and then made it actually easy to restore, then most folks would do it.
There is a saying that, “No one cares about backups; they only care about restores.”
Another one:
“Just because it verified, doesn’t mean it can be restored”
I learned that one the easy way.
My company (Datto) sells backup appliances providing automatic, redundant snapshots every few hours. We have seen a huge spike of ransomware attacks among our customers. So far, attacked customers mostly just go back a few hours to the pre-encryption snapshot and restore the file system.
We have seen only Windows attacks so far, to the best of my knowledge.
As @JR wrote, backups are a crappy chore nobody wants. Automating it guarantees it is done systematically and saves a lot of tears.
Backups are easy…
Having time to validate the backup with a true restore and DR test is another story that over worked sys admins don’t have time to do…. there is not a single backup vendor that i trust when they run a verify after the backup. You need to do a full real life restore test not auto-backup>auto-verify.
Then you have to worry if the attack file is in your backups; and that is if they don’t get encrypted too! There has to be an air gap between the files and the system you are administering to. Some folks claim Carbonite is invulnerable to this, but I think they just have a good restore routine. At least that is how I see it – maybe their cloud service firewalls off the backups and puts them in a proverbial vault, but then the date of backup would still be an issue..
Carbonite is basically an automatic versioning system. It sounds like Datto is too. It has a web interface that more or less lets you recover any version of any individual file.
The reason that randomware is dangerous is that it can arbitrarily rewrite your disk and any attached volumes.
Carbonite is essentially an API which allows you (really your agent) to add a new record (a file/directory) to a database (append only) or mark a record as obsolete. The records are never deleted by the Carbonite API.
Recovery via Carbonite of a whole computer is basically a database query: select all files where date created X.
(Yes, I’ve used Carbonite, and if asked, I’d encourage people to as well. Especially because their pricing model mostly charges for recovery, I.e. no use, limited cost –it matches the needs of normal people.)
There only attack I can think of against it is an out of band attack: deleting your account (or changing the credentials and then deleting it). I’m not sure how Carbonite the service responds to account recovery requests in such cases. Remember that there isn’t much of a difference between this and someone impersonating you and asking for a recovery of your data in order to steal it, so Carbonite as a company has to be very careful about how they handle such requests…
Check out Veeam’s SureBackup for verified VM backups.
Because Veeam can launch a VM directly from its backup, it creates a sandbox (they call it a “Virtual Lab”) which is used to host the VM. So it’s not, exactly, restoring the backup then running the VM. But it gets pretty close. The OS boots up, stuff runs, you can set automated rules for environment testing, etc.
If you’ve got a VMware or Hyper-V environment, it’s the only backup software that I know of that can do what you’re asking.
I’ve seen first hand RDP ( http://krebsonsecurity.com/2013/12/hacked-via-rdp-really-dumb-passwords/ ) has become a very popular vector for deploying ransomware. Once an account is compromised, the attacker returns in the night, sometimes on weekends, and deploys their payload. They also check it is running, as sometimes it is blocked by anti-virus. Then come the following morning, all files are encrypted.
Our company deals with cyber security training’s and top company in this fields. We are guides and counseling of people from protect to cyber crimes.
other information get ……visit my official website
http://www.codecnetworks.com/
Interesting article.
I see the operative problem to be :
“… was worth millions — possibly tens of millions — of dollars, but for whatever reason the company didn’t have backups of it. …”
I personally have used a “disk image” of my drives as a back-up. I currently do such an image on a weekly basis. When I had multiple servers with multiple users we ran a disk image on every disk within each server every day. It was on occasion needed for hardware breakdowns, and made life so much easier than a traditional file ‘backup’.
None of my disk images are ever stored within proximity of the imaged disks.
I have created VM images of machines from time to time as a usable snapshot of the entire machine state.
The files that tend to get modified more frequently during normal usage get regular backups as well. The VM image could be used as a starting point in some disaster recovery scenarios.
please note, there is a great initiative in Europe going on,
The No More Ransom (NMR) project is a public-private initiative launched on 25 July 2016 which created a common portal (www.nomoraransom.org) containing relevant information on the subject matter, including:
Available decryption tools for some of the existing ransomware families (offered by the project partners to the victims, free of charge),
Tips and advice to prevent users from becoming a victim (educational and awareness material),
Direct links to the national police agencies of the EU Member States to encourage the citizens to report the cases (one of the common problems law enforcement faces with this phenomenon is the lack of information to investigate further).
https://www.nomoreransom.org/
Nice article. I also got another useful article covering all details of ransomware
http://blog.logix.in/ransomware/
Hard drives are cheap. Disk cloning software is free. Get a cheap drive, clone your C: drive and whatever on it, disconnect it, put it in a safe place. Repeat the procedure as required and use a thumb drive in between to keep your data files up to date.
Here is a modest suggestion:
Hard drives are cheap. Disk cloning software is free. Get a cheap drive, clone your C: drive and whatever on it, disconnect it, put it in a safe place. Repeat the procedure as required and use a thumb drive in between to keep your data files up to date.
The problem w/ old fashioned backup systems like this is that it assumes the user knows the point of first corruption and has a master from before that point.
In the old days of tape backups, people had X tapes for full backups and Y tapes for incremental backups. Which eventually they rotate through (X could be 0 or 1, which wasn’t a great idea, and Y was typically smaller than X, often 1, but the amount of data added to it each time wasn’t a lot).
If your malware (or other source of data corruption) was particularly patient, you might not realize that X+Y tapes have all been replaced by corrupt content.
Malware can of course also do bad things to your tapes, so if you didn’t actually check the tape on another device, you might think that your incremental tape backup was being helpful when in fact the entire tape was being wiped out.
This is where an API based backup system ([1] ZFS-send, [2] Carbonite, …) is much better than locally attached physical media. — Remote based systems can enforce append-only, whereas anything local can’t — if your system is infected, the infection can override your instructions…
—
[1] http://royal.pingdom.com/2013/06/04/zfs-backup/
There are a number of books about ZFS. Unfortunately, I don’t have a great single page reference that walks through “ZFS is a backup system”
[2] https://www.carbonite.com
ransomware is boring, nfc payment fraud tools are available..
http://pastebin.com/9yium2an
How is it supposed to get the private encryption key off the card? No key, no valid transaction cryptograms – no transactions. Smells like a scam to me.
You can add: use micro-segmentation technology, or at least use network filtering through internal firewall
Look they are real I have confirmed it, contact: Deltagenesis@programmer.net for your hack issues ranging from , University Grades change, Email and phone hack for text, whatsapp , call logs,Gps tracking including even Credit Report fix. He provides proof and trust me he’s real. Ive been ripped severaly they are very good and reliable or text them at t +1 480 439 6115
The thing about Jigsaw is… my goodness, everyone missed the point.
The point was that it was a DNM crowdsourced, to a degree open-source Ransomeware. You didn’t pay for a final product, you paid for the raw code, written in C#.
But for some reason people didn’t realize that there are two things glaringly obvious once you aggregated enough datapoints regarding its variants:
a) Some of the versions are straight up jokes, or rather, they didn’t do anything. No deletions, not even real encryption, just renaming and rearranging. And the program taunted but did very little otherwise.
b) Reverse-engineering the executable, you can literally see the comments the creator left that wasn’t taken out because many of the users simply, well, barely knew how to compile the damn thing, and even paid others to do it.
c) The open ended capabilities were curtailed at least in part by two things: the creator releasing the original version of the decryption key very early on and the lack of implementation of some of the features proposed but abandoned because, well, the core code itself got picked up by ESET (whose bloggers, funnily, missed the whole point), and so things like Sophie’s Choice (which file should be deleted, or you want these photos deleted or autouploaded en masse online) weren’t implemented. Also, it became apparent that Sophie’s Choice wasn’t a popular movie in Europe.
d) People began precompile the software and selling it without disclosing that there are dummy parts and much of the money went to the sellers of the binaries, but incestuous scamming is almost the rule on the DNM.
e) Open source ransomware is effectively the threat that somehow neither the security community didn’t realize the danger of or didn’t know about, but this was quite literally open source from the start and debugged within a community. In a way it’s remarkably similar to webapp and software development today, there’s just no Github that hosts these AFAIK in any scale, but the whole delete 1000 files every time thing, actually, the program didn’t work without a restart, and it wasn’t in the original plans. If something unplanned can cause this kind of havoc, what if actual coding communities engaged this model, the BetaList model. We’ve seen malware change but not on a scale that creates this many forks, some serious, some not, some malicious, some not. It would also eliminate one central C&C system past the code distribution stage, the potential, if the author’s goal is subversion and not purely monetary, to terrorize can be greater than the actual impact of the software.
Brian or anyone else still reading: any comments on software like Anti-Ransom to protect from this type of malware?
http://www.security-projects.com/?Anti_Ransom
Thanks in advance.