Last month, I published evidence suggesting that future development of the ZeuS banking Trojan was being merged with that of the up-and-coming SpyEye Trojan. Since then, a flood of new research has been published about SpyEye, including a new Web site that helps track the location of SpyEye control networks worldwide.
 Roman Hüssy, the curator of Zeustracker — a site that has spotlighted ZeuS activity around the globe since early 2009 — late last week launched SpyEye Tracker, a sister service designed to help Internet service providers keep tabs on miscreants using SpyEye (take care with the IP address links listed at this service, because they can lead to live, malicious files).
Roman Hüssy, the curator of Zeustracker — a site that has spotlighted ZeuS activity around the globe since early 2009 — late last week launched SpyEye Tracker, a sister service designed to help Internet service providers keep tabs on miscreants using SpyEye (take care with the IP address links listed at this service, because they can lead to live, malicious files).
Hüssy said he’s not convinced that the SpyEye crimeware kit will usurp the mighty ZeuS. “Why should they give up something which works and pay for a new tool?” he said in an online chat with KrebsOnSecurity.com. Instead, Hüssy said he’s launching the new tracking service to help prevent that shift.
“To stay on the secure side I’ve decided to do some effort that SpyEye will not get [to be] the next ‘ZeuS’ Trojan,” he said. “My goal is to put SpyEye into the spotlight before it becomes a ‘big’ threat like ZeuS was in the past.”
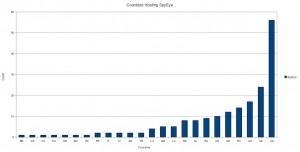 For the moment, ZeuS still far outnumbers SpyEye: Hüssy’s new tracker is following about 25 distinct botnets created with SpyEye, versus roughly 100 ZeuS-related botnets with resources online.
For the moment, ZeuS still far outnumbers SpyEye: Hüssy’s new tracker is following about 25 distinct botnets created with SpyEye, versus roughly 100 ZeuS-related botnets with resources online.
Security researchers at anti-bot company Damballa last week published an in-depth look at the worldwide distribution of SpyEye, noting that if there were a SpyEye Olympics, ISPs in Ukraine easily would take home the gold for hosting malicious control networks.
In addition, the SANS Institute has published a lengthy white paper detailing some of the code similarities and interaction between ZeuS and SpyEye. Also, Trend Micro last month released the second half of a two-part analysis on how computer crooks use the SpyEye Web interface.




Great write up Brian , but for miscreants add this to it “PARASITES” bottom feeders and so on .
im ghost just i love you
“Why should they give up something which works and pay for a new tool?”
Because it doesn’t actually work, i.e. give the client what was expected, as well as it did a year ago despite the number of installations or computers infected.