Apple released a security update today designed to address the recent scourge of scareware targeting Mac users. The update comes as security experts spotted new versions of the rogue application family MacDefender making the rounds via poisoned links on Facebook.
Security Update 2011-003, available for Mac OS X v. 10.6.7 and Mac OS X Server v. 10.6.7, includes a component that checks for the MacDefender malware and its known variants. In its most recent advisory, Apple states: “If MacDefender scareware is found, the system will quit this malware, delete any persistent files, and correct any modifications made to configuration or login files. After MacDefender is identified and removed, the message below will be displayed the next time an administrator account logs in.”
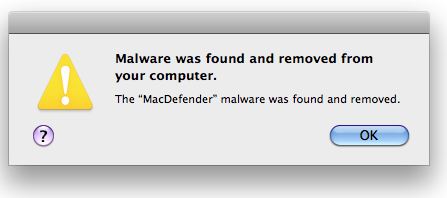 The update also adds malware definitions to warn users away from downloading MacDefender, and sets the computer to check daily for updates to the malware definition list. Mac users who apply this update and later try to download a version of this malware via Safari, iChat or Mail should see a warning similar to the following dialog box:
The update also adds malware definitions to warn users away from downloading MacDefender, and sets the computer to check daily for updates to the malware definition list. Mac users who apply this update and later try to download a version of this malware via Safari, iChat or Mail should see a warning similar to the following dialog box: 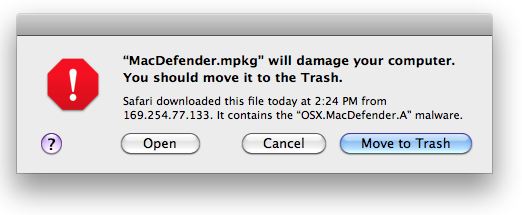 I’m glad that Apple has released this update, although I think they probably waited too long to do so. Some Windows users are no doubt experiencing a twinge of schadenfreude at this development, considering how Apple and many hardcore fans of the Mac platform have held out OS X as an unbreachable fortress. What the defenders of the Myth of Apple Invulnerability have long ignored is that a growing share of their user base is made up of people who are not technically sophisticated, and are just as prone to falling for clever social engineering attacks as their Windows counterparts.
I’m glad that Apple has released this update, although I think they probably waited too long to do so. Some Windows users are no doubt experiencing a twinge of schadenfreude at this development, considering how Apple and many hardcore fans of the Mac platform have held out OS X as an unbreachable fortress. What the defenders of the Myth of Apple Invulnerability have long ignored is that a growing share of their user base is made up of people who are not technically sophisticated, and are just as prone to falling for clever social engineering attacks as their Windows counterparts.
A reader captured this thought nicely in a comment on my post last week about an apparent source of MacDefender scams: “Yes, many Mac users are technically sophisticated. But many others are not. Many bought Macs in hopes of staying safe despite having no computer training, or they may even have been advised to get a Mac by friends and relatives who feared the worse if they were let loose on the internet with a Windows machine. Many users are elementary school children and their teachers, since Mac is strong in educational software. It isn’t necessary for the perpetrators to be able to infect every Mac for this scheme to be profitable.”
As Apple’s share of the marketplace continues to grow, let me remind readers again that the staying-safe advice often posted on KrebsonSecurity applies with equal urgency to the Mac community as it does to users of other OS platforms.




Why even give the option to “Open” a program that is identified and labeled “will damage your computer”? This isn’t likely a false positive type problem given this isn’t a full blown Anti-malware solution that is actively scanning. This setup is a simple blacklist for downloaded files. Not to mention it’s a wack-a-mole approach that could quickly escalate out of control in favor of the bad guys. I know Windows has similar functionality, but the option is better implemented in that you have to click chevron arrows to expose the “Open/Run” option and are then again prompted “Are you sure?” Apple has a lot to learn yet. 🙁
And yes, Mac users should be utilizing layered security (defense in depth)!
@xAdmin
Blacklisting of any stripe IS a whack-a-mole approach. And ALWAYS a step or two behind the miscreants.
As mentioned, Brian’s 3 rules apply to all operating systems. User behavior remains an important factor.
However, hardening options do exist for Macs. For Mac OS X, create and use a standard user account for day-to-day use and be VERY wary of authentication requests for the administrator account name and password (see Brian’s 3 rules). Better yet, create a managed user account and use App Control to setup an App whitelist that includes all the apps you need to USE (NOT ADMINISTER) the computer. Yes, certain features of OS X’s built-in Parental Controls are useful for adults too.
Once could consider this as Mac OS X’s version of Windows Software Restriction Policy whitelisting.
Yeah, i bet it does nothing else than take a md5 hash, compare it to some list, and throw up the warning.
I guess that’s better than nothing, but unfortunately everyone on 10.5 or 10.4 is screwed because Apple’s horrible lack of legacy support. I guess its time for everyone to move to 10.6 already and pay the 30 bucks. Or invest in proper AV, which is what’s going to happen in the long run now that OSX’s marketshare has made it profitable for malware writers.
“Layered security…” do we really need such a thing??? We keep hearing it from AV vendors who make a killing from the mess M$ left with their lack of attention to quality. We should applaud Apple for taking inititive and dealing with abuses of technology (abeit a bit slow). Lets hope they also take this to the next level and connect the crime and the criminal. Kudos to Brian for investigation.
There are free Anti-malware solutions from various vendors, so not sure how they “make a killing” on this. Also, I wouldn’t be so quick to applaud a software vendor that initially told their support staff to not admit a malware problem and to not help the user remove it. Any other vendor would be excoriated for doing such a thing! Apple is going to have to change, particularly as this situation escalates as all indications appear to suggest.
Do you applaud Microsoft for its monthly Windows Update based malware scanner or its free MSE AV?
Of course you don’t. Youre just a fucking moronic fanboy. Please go away, the adults are speaking.
Yo! Not cool. Keep it civil, please. Failing that, your comments will wind up in the circular file. Thanks.
I’d put them in file 13 myself.
Sophos details some shortcomings of this update:
http://nakedsecurity.sophos.com/2011/05/31/apple-releases-update-to-protect-against-macdefender/
“The biggest problem is the lack of an on-access scanning component. While LSQuarantine works to protect against downloads in most browsers, it doesn’t prevent infections through USB drives, BitTorrent downloads and other applications.
Daily updates are a good start, but it remains to be seen how frequently the criminals may release new variants. If they start moving in a polymorphic direction similar to the one the Windows malware writers have gone, XProtect will have issues.
Of course this update only applies to OS X 10.6 “Snow Leopard,” so older Mac users are left unprotected.”
And more on the recent Mac malware:
Mac malware spreads via Facebook links
http://nakedsecurity.sophos.com/2011/05/31/imf-boss-rape-video-mac-facebook-users-hit-by-a-sick-scareware-attack/
Thanks for info. on Apple’s “Defender fix.” It applies only to 10.6. I have 10.5.8. What can those of us with pre-10.6 Macs do?
Apple certainly is NOT being COMPETENT or HELPFUL for Mac users anxious to get rid of this contaminant!
It appears that the MacDefender folks have already modified it to evade Apple’s filtering system.
http://www.zdnet.com/blog/bott/new-apple-antivirus-signatures-bypassed-within-hours-by-malware-authors-update/3396
This was entirely predictable. In the wild we see these fake AV’s recompile several times a day. The definitions dont work with different versions, so its whack-a-mole just like in the Windows world.
Yeah, it’s kind of surreal that they seem to expect that to work any better than has for Windows.
I do know they have problems, but this is exactly why I like white-listing technologies. Black lists is incredibly hard to maintain. However, white lists are usually very small compared to the black lists and easier to maintain.
Denial is no longer any kind of a defense and there is no protection in ignorance.
Thats the best advise we can all offer Mac-Apple people.
It is much easier to be secure with a small installed base. If Microsoft went back in time to 1994 and saw the way computers are used today, Windows security security would be much better.
OS-X’s installed base today, in raw numbers, is still smaller than Microsoft’s was in the early to mid 90’s. That means Apple has a chance right now to improve their security position while they have a relatively small installed base, and focus more efforts on improving rather than maintaining.
Maybe. Microsoft employees sat there befuddled in not understanding IBM wanting to put in file / folder ownership, group membership, and vatious other non-group users and what each can do via permission flags into the HPFS / NTFS. If the Microsoft employees had saw Unix, AS/400 (now OS/400), VM/CSE, and OpenVMS maybe they would have understood the need for MAC and waited. Then again maybe they still would not have waited. If they had waited until MAC (Mandatory Access Controls) were in place the world would be very different today. OS-X has MAC. But if you allow admin accounts to install without a password then you just threw the MAC protection out the door. The only other Unix-like system I have observed doing something that dumb was Fedora version 12. The Fedora team corrected it, but not without almost 1000 email messages flying back and forth between the developers first. So in the mean-time I advise people who use a Macintosh to set the Safari controls to not auto open for install files, then create a normal account that doesn’t have the right to install without a password and use it all of the time with Safari still nobbled to not allow install. Some hacker could still install an app in the user’s Applications folder. But why should the hacker do that when somebody hands them the keys to the kingdom?
You have a good point on IBM. OS/2 was a really good foundation. And didn’t that start to fall apart right around Windows 95? Could that have been the moment when Microsoft went for big sales over technical ethics?
Regardless, OS-X is built on a good foundation. It doesn’t seem they have much to fix. Hopefully this is a wake-up call. They can rally the troops and take a very serious look at silly things like allowing someone to easily open a known harmful attachment.
The point was it’s always easier to fix things when you aren’t the target. There are probably hundreds of CIOs thrilled they aren’t Sony, and sweating bullets hoping they aren’t the next Sony.
Color me suspicious, but I can’t help but wonder if Apple is going to use the example of MacDefender as a rationale for pushing the “App Store” model of “vetted” applications as the sole application loading method in future OS X releases.
They’d have to surrender any hope of competing with Microsoft for business. There are too many companies that want to run in-house applications.