Microsoft has fingered a possible author of the late Rustock spam botnet – a self-described software engineer and mathematician who aspired to one day be hired by Google. Microsoft has apparently allocated significant resources to finding the author, but has not been able to locate him.
Rustock remains dead, but Microsoft is still on the hunt for the Rustock author. In its Second Status Report (PDF) filed last week with a district court in Seattle, Microsoft said it inquired with virtual currency provider Webmoney about the owner of an account used to rent Rustock control servers, and confirmed that the account was affiliated with a man named Vladimir Alexandrovich Shergin. Microsoft also mentioned another suspect, “Cosma2k,” possibly named Dmitri A. Sergeev, Artem Sergeev, or Sergey Vladomirovich Sergeev. Microsoft said it is continuing its investigation of these names, to determine whether additional contact information can be identified and to which notice and service can be effected.
To help in the hunt, I hereby offer some details about him.
Microsoft helped to dismantle Rustock in March after a coordinated and well-timed “stun” targeting the spam botnet’s infrastructure, which was mainly comprised of servers based in U.S. hosting facilities. Two weeks after that takedown, I tracked down a Web hosting reseller in Eastern Europe who acknowledged renting some of those servers to the apparent Rustock author. That reseller shared the Webmoney account number used to purchase access to the servers, and Russian investigators I spoke with confirmed that the account had been registered by a Russian named Vladimir Shergin. By consulting a leaked database I obtained last year of the top earners for Spamit.com — at the time the world’s largest rogue online pharmacy network — I discovered that the same Webmoney account was shared by three of the top ten Spamit affiliates.
The information from the reseller and from the Spamit database traced back to a Spamit affiliate who used the pseudonym “Cosma2k.” The email address tied to that Cosma2K account was “ger-mes@ger-mes.ru”. When I came into possession of the Spamit.com data back in August 2010, the site ger-mes.ru was still responding to requests, and the homepage presented some very interesting information. It included a job résumé, underneath a picture of a young man holding a mug. Above the image was the name “Sergeev, Dmitri A.” At the very top of the page was a simple message: “I want to work in Google.” Beneath the résumé is the author’s email address, followed by the message, “Waiting for your job”!
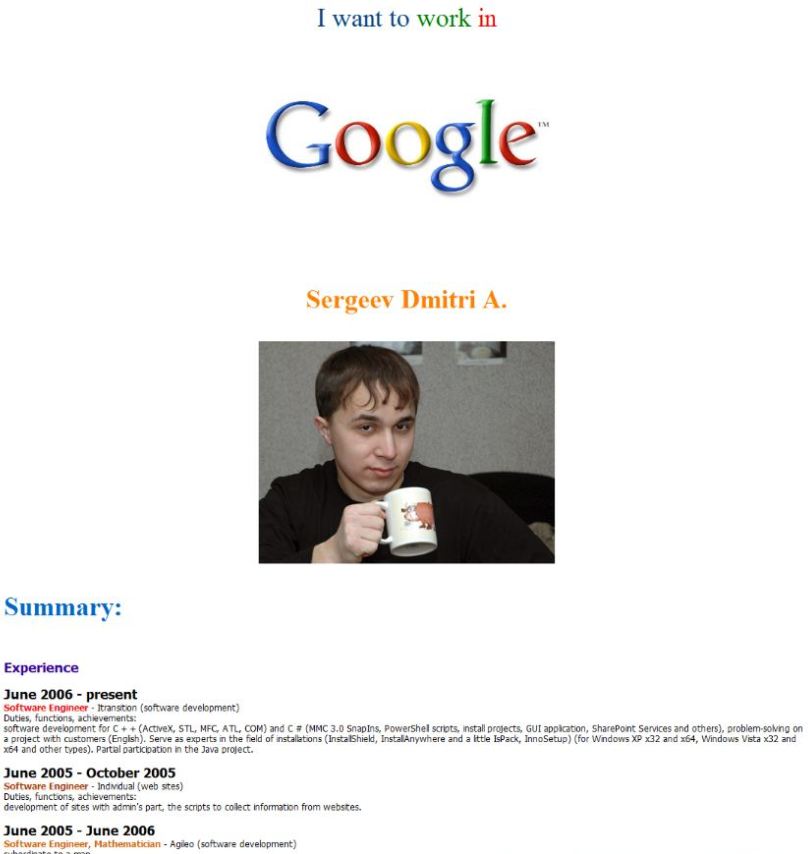 Here is the complete page and résumé, in case anyone wants a closer look at this Belorussian-educated job seeker. I shared the information with Google in August 2010, to find out if they’d received a job application from this person, or if they’d considered flying him to Mountain View, Calif. for an interview. I still don’t have an answer to either question. I shared this same information with Microsoft in March.
Here is the complete page and résumé, in case anyone wants a closer look at this Belorussian-educated job seeker. I shared the information with Google in August 2010, to find out if they’d received a job application from this person, or if they’d considered flying him to Mountain View, Calif. for an interview. I still don’t have an answer to either question. I shared this same information with Microsoft in March.
Microsoft seems determined to bring the Rustock malefactors to court. Maybe the mug shot in this résumé will help to identify at least one of them.




Whoa! You keep outdoing yourself, Brian!
Has Microsoft, like so many large companies, gotten so big that they can’t respond quickly to new information? Do they have to go through a bunch of depts. and managers before any decision on positive action can be achieved? It would seem that with the info that you supplied, that they would be able to find out something about this guy. And you are only one man. I’m impressed.
Maybe you can get hired by Microsoft as a stringer … they pay you for leads … provided this is Ok with your current employer … or Microsoft pays the both of you.
I think Brian’s his own employer so two paychecks might be a nice enticement. 🙂
The Washington Post is salivating at this possibility. They really, really, need the exposure (!)….sorry…that just lept up out of the ether, either that, or, net (!), Krebs can leverage even more well deserved prominence…..
Off topic but only very slightly, everyone should read that book, “The Kingpin”, by Kevin Poulsen, if they haven’t already. My geriatric fingers are quivering at the lost opportunities of my now quite long vanished youth.
I marvel at the way such intangibles as this subject of “hacking and spamming” can be “monetized”….talk about Ponzi’s!
It violates Physics 101 to demonstrate that something can be created out of nothing. “Ex nihilo”, as it were.
Seems the easiest way to track him down is through ITransition. They’d most likely have his address and maybe even bank account info.
Brian, you’re the Mossad of cyber security. I laughed so hard reading this entry that coworkers came in to see what could be so humorous.
If I could have only one site on my feed, yours would be it. Brilliant!
Two mugs with one shot, I like it. 🙂
With all due respect cloud liam hes hardly a mug. theres only a few people in the world who could code such sophisticated malware.
Get the feeling that alot of these folk end up working for the security services (bear in mind rustock was primarely a root kit).
It was a comment on Brian’s amusing little play on words.
You would think a root kit author would be more adept at covering his own tracks though wouldn’t you? I mean there he is in living color for all the world to see and all.
@a problem with spam?
He is being identified as a suspect, not a criminal. It’s in the title of the article.
We don’t have a court trial to determine if a person is a suspect. We do have grand juries for indictments, but not if you haven’t even positively identified the suspect.
If anything, Brian did the guy in the picture a favor. If he is the criminal he has the opportunity to hide even deeper in the criminal underground. If he is not the criminal he has the opportunity to come forward and get removed from the suspect list, and most likely be able to point Microsoft and law enforcement in the right direction.
It is common for the public to know who the suspects are in criminal cases unless law enforcement purposely keeps it secret for fear the suspect will flee. In this instance the suspect has effectively already fled.
@a problem with spam?
Sorry, replied to the wrong comment.
Again, Brian, great detective work. Hmm, with Microsoft ‘dead set’ on finding this ‘Sergeev’ fellow, I wonder how long before large tech companies, like it and Google, resort to financing and training their own ‘Seal Team Six’ groups to handle the ‘unpleasant business’ of dealing with these folk? Thanks for the updates, and I’m getting the family to live/learn Brian’s “The Three”…
Great post, Brian.
The resume and the picture you’ve posted in an earlier post in response to a comment, and I remember at that time thinking it is possible the photo and the resume to represent someone unrelated to Rustock which was “planted” by the real author to send off-track any possible pursuers. I guess this is the problem Microsoft is facing also, to make sure the person in the photo is the Rustock perpetrator, he has to be apprehended, his property searched, etc. But for an international warrant to be issued, more (non-circumstantial) evidence is needed.
Unfortunately, if the chance to catch him looks rather dim at least I hope he will be inconvenienced seriously by not risking to travel to western countries or ever landing a job at Google. (I shiver thinking which opportunities to do bad such monsters would have by being employed at Google, Yahoo, etc).
Nevertheless, in today’s column Brian gave a lot more details about how the trail leading to the resume and photo was followed and I tend to believe it is (a lot) more likely to be someone closely related to Rustock rather than planted evidence.
Great detective work Brian! As I follow this blog for a long time it is good to hear Microsoft is doing botnet assault nowadays. IMHO the resume couldn’t be of a rootkit programmer. To write a rootkit like rustock it needs more years of driver programming which clearly lacks in this resume.
Very good observation, he might not be the programmer, but he may be the bot herder (more likely since it was the Webmoney trail leading to ger-mes.ru). Working for ISP’s he was in quite a good position to be a herder: All that free bandwidth and possibility to screen abuse complaints…
I’m wondering what he means in his Resume by sentence: “Working for a man”. I doubt he considers of relevance to mention having only male supervisors, it must mean something else.
Yes, I noticed “subordinate to a man” as well – it is strange. All his other mistakes are pretty typical for a Russian-speaker. This one is probably a literal translation of some Russian phrase but I cannot fine one that would match. I guess this is simply meant to say that he had a subordinate position.
@Siva, a lot of talented Russian programmers who end up in criminal activities are underemployed. If he’s been active in blackhat pursuits, he may have an entire parallel resume he can’t share publicly.
He doesn’t have to be the only programmer. He does list several months on his resume developing admin and data collection scripts – in parallel to working for Agileo. Anyway, seeing that he usually didn’t stay at any company longer than a year, I think that this resume most likely hasn’t been updated since 2007 or something like that. Enough time to gather the necessary experience.
Mugshot?
(picture of a guy holding a mug).
What a terrible PUN! You should be ashamed–or impressed !!
Sounds like a mugwump.
We see his mug but not his wump. Need more location data.
Or maybe PUNished ?
I found it both funny and ironic. Well, if “Sergeev, Dmitri A.” is hired, he will not be the first to migrate from bad to being one of the good guys. Changing side is not new.
Gregory Evans was once an A-list hacker. In fact, he was once in the FBI’s list. Today, Evans is now a cyber security expert and owns the The Cyber Group Network Corporation and the LIGATT Security.
The other guys to this roll include Marc Maiffret, Kevin Mitnick, and Fisher Stevens.
And don’t forget to add Kevin Poulsen, currently senior editor at Wired.com, their go-to guy for guess what – hacking and internet security news (among other things).
And as somebody already mentioned, in Eastern Europe and in many cases, there simply isn’t gainful legitimate employment for a lot of these guys. Not that this makes what they do acceptable, but at least it’s not too hard to see that many of them do have potential as good guys, given the chance.
Why you are judging this guy without any court? You published his photo, his real name and said that he is cybercriminal. Who you are thinking you are? Judge or prosecutor?
hmm this is what i thought initially, you just cant post a picture of someone and their name + résumé on a blog. I know he had it up on his stire, but it doesnt mean you should share it on yours without any factuall proof that the person is him Brian.
Good work on other articles 🙂
I understand what you’re saying but it is the guy’s public webpage.
The only real charge against Brian is presenting a string of evidence ending in the guys page. Grey area as far as I’m concerned.
Abram, Alan – Actually I waited until Microsoft publicly named him as a suspect in a court of law before I wrote about him.
@Abram
He is being identified as a suspect, not a criminal. It’s in the title of the article.
We don’t have a court trial to determine if a person is a suspect. We do have grand juries for indictments, but not if you haven’t even positively identified the suspect.
If anything, Brian did the guy in the picture a favor. If he is the criminal he has the opportunity to hide even deeper in the criminal underground. If he is not the criminal he has the opportunity to come forward and get removed from the suspect list, and most likely be able to point Microsoft and law enforcement in the right direction.
It is common for the public to know who the suspects are in criminal cases unless law enforcement purposely keeps it secret for fear the suspect will flee.
In this instance the suspect has effectively already fled.
Cross reference it on the PSN database: Gotcha! :;
The supreme irony would be if he were indeed to be offered a job, not by Google, but by Microsoft.
Brian,
Have you considered writing a book about spam? I find your articles fascinating and believe that your knowledge of the subject would make a great book.
I’ve read Kevin Poulsen’s book Kingpin and found that following the trail from beginning to end was an excellent way to understand many of the facets involved in credit card cyber theft. Kevin does a good job covering the subject in his blog but the book really hit home. I’ve recommended it to my friends and family simply to get them to understand how this crime works on the internet.
I think your writing style and knowledge of the spam industry makes you quite qualified to write a book about it.
I was so confused about what to buy, but this makes it undesrtanabdle.
The funny part is that ITransition is a Microsoft Certified Partner http://en.wikipedia.org/wiki/Itransition
They’ve been one since 2008.
It seems to me that they shouldn’t be to far to knowing who this gu really is and if he really done what he’s suspected of doing 😀