Google warned on Wednesday that hackers were launching targeted phishing attacks against hundreds of Gmail account users, including senior U.S. government officials, Chinese political activists, military personnel and journalists. That story, as related in a post on the Official Google Blog, was retold in hundreds of media outlets today as the latest example of Chinese cyber espionage: The lead story in the print edition of The Wall Street Journal today was, “Google: China Hacked Email.”
The fact that hackers are launching extremely sophisticated email attacks that appear to trace back to China makes for great headlines, but it isn’t exactly news. I’m surprised by how few media outlets took the time to explain the mechanics behind these targeted attacks, because they offer valuable insight into why people who really ought to know better keep falling for them. A more complete accounting of the attacks may give regular Internet users a better sense of the caliber of scams that are likely to target them somewhere down the road.
Google said “the goal of this effort seems to have been to monitor the contents of targeted users’ emails, with the perpetrators apparently using stolen passwords to change peoples’ forwarding and delegation settings. (Gmail enables you to forward your emails automatically, as well as grant others access to your account.)”
This statement freaked me out a little bit. When was the last time you checked whether your email forwarding settings had been modified? If you’re like me, probably never. This might be the most useful aspect of the Google disclosure, and it contains a few helpful pointers about how to check those settings in Gmail. Google also took this opportunity to remind users about the value of enabling 2-step verification, a security precaution I highlighted in a February blog post.
To my mind, the most valuable content in the Google Blog entry is a footnote that points to the Contagio Malware Dump blog, an incredibly detailed and insightful (if slightly dangerous) resource for information on targeted attacks. It’s worth noting that Google relied on Contagio to reconstruct how the attacks took place, and the author –blogger Mila Parkour — first wrote about these attacks almost four months ago.
Most of targeted email attacks chronicled on Parkour’s blog involve poisoned file attachments that exploit zero-day software flaws in programs like Adobe Flash or Microsoft Word. This campaign also encouraged people to click a link to download a file, but the file was instead an HTML page that mimicked Gmail’s login page. The scam page also was custom-coded to fill in the target’s Gmail username. Contagiodump has a proof-of-concept page available at this link that shows the exact attack, except populated with “JDoe” in the username field.
Parkour also published an informative graphic highlighting the differences between the fake Google login page and the legitimate page at https://mail.google.com.
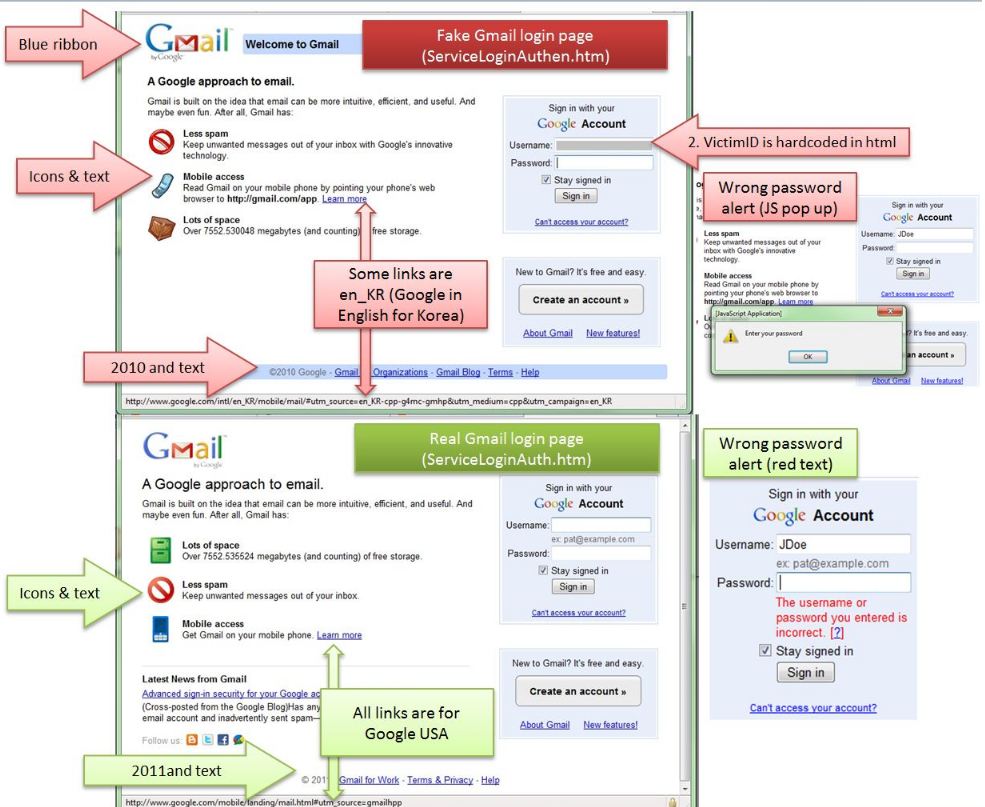 Some readers may think they’re not important enough to warrant targeted phishing attacks such as these, but the truth is that such phishing attacks can be automated quite easily. I’d be willing to bet that it won’t be long before more traditional, financially-motivated cyber crooks start incorporating these techniques in their scam emails.
Some readers may think they’re not important enough to warrant targeted phishing attacks such as these, but the truth is that such phishing attacks can be automated quite easily. I’d be willing to bet that it won’t be long before more traditional, financially-motivated cyber crooks start incorporating these techniques in their scam emails.
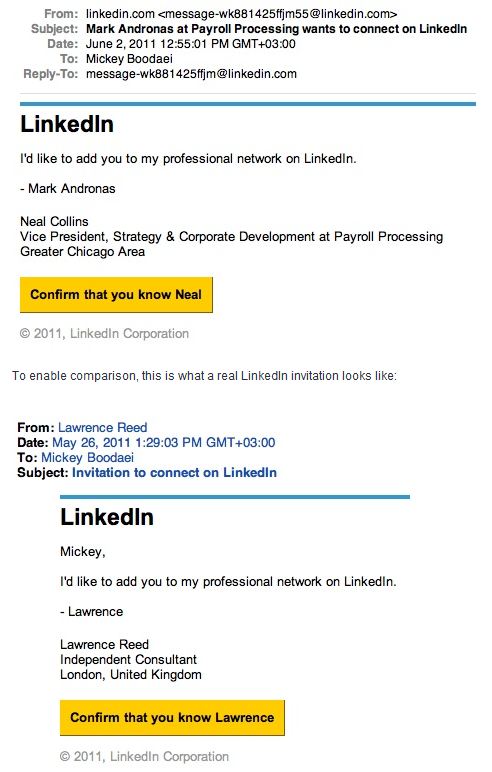
Along these lines comes a blog post today from security vendor Trusteer, which warned that scam artists are once again using cleverly disguised LinkedIn invites to foist password-stealing malicious software. Trusteer said this latest attack started with a simple connect request via email that was made to look it came from another user of the social networking service. Users who click the link are redirected to a site in Russia outfitted with a version of the Blackhole Exploit Pack, which tries to silently install a copy of the ZeuS trojan by heaving a kitchen sink full of browser exploits at visitors.
The image below, taken from Trusteer’s blog, shows the booby-trapped LinkedIn request on the top; the image below is what a legitimate LinkedIn request looks like. Would you have been able to tell them apart?
Here are a few simple tips that can help you avoid becoming the next victim of these attack methods:
- Keep your software up-to-date. Legitimate, high-traffic Web sites get hacked all the time and seeded with exploit kits. Take advantage of programs like Secunia’s Personal Software Inspector or Filehippo’s Update Checker to stay abreast of the latest security updates.
- Be extremely judicious about clicking links in emails. Try to avoid responding to invites by clicking links in emails. I notice that Twitter has now started sending emails when someone re-tweets your posts: Avoid clicking on those as well. It’s safest to manage these accounts by visiting the sites manually, preferably using a bookmark as opposed to typing these site names into a browser address bar.
- Pay close attention to what’s in the address bar: Checking this area can prevent many email-based attacks. Staying vigilant here can also block far more stealthy attacks, such as tabnabbing.
- Consider using an email client, such as Mozilla’s Thunderbird, to handle your messages. It’s a good idea to have emails displayed in plain text instead of allowing HTML code to be displayed in emails by default.




I’m confused. If these hacks stem from a stolen password and account, how is this done? If someone sends me a bogus attachment that when opened turns out to be a prompt for my Gmail account, wouldn’t that warn me that something was wrong?
I have implemented the 2-step authorization, but I don’t understand how that protects in the situation above where the victim is fooled into entering a password and ID.
I was just chatting with Mila about this. My response to your first question is, “Absolutely.” But Mila had a different response. She said:
“Answer to 1 – yes it looks suspicious but people who used to spotty internet connection like on laptops on wifi in airports, on usb modems, travelers etc
may assume it is a connection glitch and login again”
To your second question, I would say just because you have 2-step verification set up doesn’t mean you can let your guard down about making sure that the right URL is in the address bar.
I’m not sure I understand what to make of the url information from the photo in the story. According to the photo, the login url for both the fake and real gmail site is the same except for an “en” after Auth. But when I type gmail in the address bar the url is a giant string that doesn’t look like either one from the photo (ServiceLoginAuth.htm or ServiceLoginAuthen.htm )
I agree. When I go to Gmail’s login page from my PC, the url presented is a very long string that looks nothing like the one found at the bottom of the above screen shot. It looks like the url in Wladimir’s comment after the web archive portion.
The url at the bottom of the screen shot actually goes to the “Gmail for mobile” login page, not the page shown in the screen shot. http://www.google.com/mobile/landing/mail.html#utm_source=gmailhpp
Thanks, Brian. I had overlooked that the scenario for the first question involves the user having just logged on to Gmail and had downloaded the bad attachment.
“…preferably using a bookmark as opposed to typing these site names into a browser address bar…”
Here’s an example of where I was patting myself on the back because I almost always go out to the vendor website instead of clicking on links, until I got to the second part!
Do I understand you correctly, that it isn’t as safe to actually type the site name into the bar? Is that because of a potential typo? I think I’m guilty of typing in the first few letters, say “krebs” and clicking on the page that drops down from the bar.
That’s bad?
>Do I understand you correctly, that it isn’t as safe to actually type the site name into the bar? Is that because of a potential typo?
Just typing the name into the bar is not dangerous unless you make a typo. Depending on your natural typing rhythm, a typo is likely.
Newer browsers with URL prediction are a help …. unless you’ve had a typo in the past, in which case they will frequently suggest the typo’ed site along with the real site.
Bookmarking the site’s SSL page helps in 2 ways: 1. it eliminates typos, and 2. If someone is manipulating your connection, you will likely get a certificate warning popup which may save the day.
I dont know about the rest of you but all my mail comes as plain text.Its not pretty and really boring at times ,but dang i can spot russian spambots rather easily.
This actually occured on one of my email accounts.The name was correct but the link was not.I called the said individual and he said it wasnt him.He now doesnt keep his computer on at night unattended.LOL!
Hmmmm …
Sometimes when I brought up gmail my ID was already in there. Does that by itself indicate that it was a fake website ?
It is normal and most likely real if you click on gmail link in Google.com and your ID is there. However, if you are reading a webmail message (any type of webmail) and click on a link or attachment in it and you suddenly see a login screen, chances are that it is a phishing fake page. To be safe, do not enter your login. It is possible, especially with corporate webmail, that your session timed out or you got kicked off when internet connection dropped but logins are more persistent on gmail, it should ask you to login while you are using it.
typo correction: “it should NOT ask you to login while you are using it.”
Thanks.
I am careful enough to be wary of attachments and links.
The only way I bring up gmail is via inserting its URL into the URL box of Firefox.
Suppose our browser is remembering our password for us.
Is that visible to the software which plants cookies on our PC?
When we transmit our password from PC to site, is that visible to anyone who may be tapping communications to the site? Like maybe our ISP has been hacked.
If you explicitly type in http://gmail.google.com and your userID is there, it is just being pulled from a previous session. The problem lies when you are asked for your password after already loggging in.
Everyone is a target with these campaigns. It is easier to compromise family or friends of senior execs to increase their trust of a message coming from a person they are familiar with. If you work in or around the USG or the military, you know people who know people. You are worth compromising for the fruit you will bear.
Attachments and links are an avenue of attack, but with so much web 2.0 code packed into these heavy webmail sites (Gmail, Yahoo, MS/Live), expect there to be compromises that have or will occur from simply viewing/previewing messages. No clicks necessary. My Dad’s Juno account is sounding pretty good right now. 😉
Thanks Brian for the post
I had been following your blog for quite sometime and I feel it is a good place for me to start learning things like this. I was surprised when I first came across this blog and see so many big time players were attacked by hackers with different techniques. Looking forward for more. By the way, my Gmail setting is displaying HTML email format only, should be sufficient isn’t it? 🙂
Thank you Brian, very informative. Your Linkedin screenshots gave me a scare, I was trying to remember whether the last two Linkedin invites from some unknown person had the correct subject line. Yeah, I really should stop clicking the links in the email – even if the mail looks legit.
I’m surprised that the fake Gmail login page is so different from the real one. They must have created a copy of the real page and I cannot imagine them redoing the icons – could it be that the login page simply looked like this in 2010?
Got an answer to my last question: yes, that’s simply a copy of an outdated page version, see http://web.archive.org/web/20100814023726/https://www.google.com/accounts/ServiceLogin?service=mail&passive=true&rm=false&continue=http%3A%2F%2Fmail.google.com%2Fmail%2F%3Fui%3Dhtml%26zy%3Dl&bsv=1eic6yu9oa4y3&scc=1<mpl=default<mplcache=2
The LinkedIn emails that I get – plain text only – have such ugly links inside that if they ever had any security issue, they might was well be URL shortened links.
I’ve noticed a marked increase in people (bots?) wanting to link to me there too. Just received an new request this morning from someone I do not know and haven’t met. DELETED.
For now, running Linux provides some level of protection, but it isn’t perfect. Eventually, all platforms will have zero day exploits (they all probably do already) so not clicking on links will be the only real protection.
Someone really smart said something about not clicking on links if you didn’t go looking for it.
To your last point about using a standalone email client, do you include Outlook in that? I would argue that it is a less secure choice than webmail like Gmail because of Outlook’s tight integration with IE and the OS, making it much more vulnerable for attacks that take advantage of the preview pane.
I do agree that plain text is better than html, especially for spotting malicious/spoofed links. But maybe it is just better to not click on any links in email at all.
Once again your articles lead me to the conclusion that modifying ones browsing habits is an ever perpetual process, not unlike your consistent reminder of the importance of keeping ones software up to date. Being a novice with common sense I am greatly appreciative of your articles.
On another note, when I click on the link to the the “Contagiodump has a proof-of-concept page” my browser (Opera) prompts me to save the document. Once I click save my Comodo antivirus quickly warns that it is “unclassifiedmalware@172725224.
Recently Comodo has had been producing a higher amount of false positives and being a novice I lack the skills to investigate it further so I will have to leave it at that.
As a guard against this kind of social engineering, I’d also recommend installing the EFF’s HTTPS Everywhere Firefox plugin. This is an example where greater privacy means greater security, because if you teach yourself to expect and look for locked encrypted SSL web pages, you’re much less likely to fall into the trap of passing personal information in the clear through port 80.
I make it a practice to avoid doing anything on web pages that aren’t encrypted. Except of course for Brian’s.
Another, better, solution is to become, as I have, a “cloud survivalist”: get your own server and host your own cloud services: email, calendering, addressing, VPN, web proxy, and everything else that you’d find in a corporate IT environment or “free” cloud accounts. This is easy and relatively inexpensive with either a Linux box or a Mac Mini Server. Again, privacy equates to security when you host your own cloud. With good practices, a decent server will have the same or better security as any corporate or “free” account, but being an extremely tiny fish the chances of being targeted are extremely low. And your account will not be scraped for personal data by GOOG, YHOO, or anyone else. And it cannot be scraped without a warrant, as can be done now for any cloud account.
The only real solution I see to attacks like this is to disperse the cloud into micro-cloudlets (water vapor?!) that only speak to each other over encrypted channels.
“…being an extremely tiny fish the chances of being targeted are extremely low.”
The hackers constantly poll and ping every IP address looking for active networks to assault. Every fixed IP address provides a limited set of barriers to overcome. Even if they cannot figure out what is leaving the IP address, they still work to invade the network at the IP address, to install their remote-controlled botnet.
hackers constantly poll and ping every IP address looking for active networks to assault
And the basic services (e.g. Apache, IMAP) on my puny up-to-date clould has the same security as basic services on any other up-to-date cloud. But my puny cloud does not have millions of users susceptible to social engineering attacks. And the incentive to pwn my puny cloud is comparatively puny. If you really had a 0-day against ssh key authentication, would you burn it against a big target or a puny target?
Fragmenting the cloud doesn’t make the threats go to zero, but it does make them a lot smaller.
I’m surprised that so many Gmail accounts could be hacked so as to provide access to this particular scam.
As I understand it, these phishing attachments are sent from hacked accounts to colleagues who in turn open the attachments which prompts them to re-enter account info, thereby perpetuating the scam.
Were there that many State Dept and other government officials who had easily guessed passwords?
Passwords were not guessed or broken. They were stolen, which means they can be complicated or simple, it does not matter.
I think I have it now. Sorry to be a bother but many of the reports omit details.
From Mila’s site:
“Victims get a message from an address of a close associate or a collaborating organization/agency, which is spoofed.”
From this I take it that the original message contains a fake or spoofed domain name. And this is related to why Brian urged us to keep a close eye on what is in the address bar.
I got several e-mails today with same subject:
“Are you taking on new clients?”
All came with a link for response.
I responded via e-mail NO, and why not.
Some were from names I recognized, some not.
Then I got, from a discussion group I never heard of before (I am not a member, I never knowingly sent them anything):
Your mail to ‘Board’ with the subject
RE: Want to help build a referral network?
Is being held until the list moderator can review it for approval.
The reason it is being held:
Post by non-member to a members-only list
I’ve seen that response before. I post on some large public messaging boards, with some pretty wonky satellites.
The Marx Rule is appropriate no matter who’s doing the social engineering …
“I don’t care to belong to a club that accepts people like me as members.” –Groucho Marx
I’m baffled when people recommend Gmail.
Safe-Mail is better, SSL enabled through complete sessions, usable without javascript, usable through Tor (you can disable IP checks, unlike Gmail):
http://www.safe-mail.net/
It’s free.
Maybe they recommend GMail because it offers 7+GB of totally free storage space, and Safe-Mail only offers a paltry 3MB for free? Safe-Mail isn’t really “free”, it seems to be made for people who pay to be “premium” users.
Yup, the large amount of free space is the main reason why people sign up for these services in the first place.
We run a small I.T services firm and I have lost track of the number of potential clients who are adamant about using a Gmail or Yahoo id for their business email (despite the dangers of losing it and never being able to get back access) simply because a huge amount of space is being offered.
Unfortunately, people will continue to be short-sighted unless they are hit really hard through a phishing experience or lose access to their email account.
I use 4 partitions on my drive, C for the o/s, D for misc data, P for programs and X for encrypted (TrueCrypt) data. The java script shows a scan of C:\Program Files to look for a/v tools, so I guess I would have an extra layer of protection by not having my a/v files there.
I got a link in an email from a friend who has never sent me any email, so I was suspicious of it from the ‘git go’ as my dad said. Since I view email in text only, I could see the long character extension of the url.
I replied and asked him if he has sent it, he hadn’t, but guessed his account had been hacked during a 2 hour layover at an airport where he used free wifi.
I was intrigued to read that you recommend pulling up sites from bookmarks instead of typing the addresses into the browser address bar. Why? Isn’t the latter safe now?
Also, I think you should mention that such attacks are a great reason to use Gmail or other webmail services (that support them) through a regular email client such as Thunderbird. In one stroke, it protects the user from exploits such as those you described in the article. Of course, one will miss all the Web 2.0 functionality of webmail clients but it’s far safer.
Sorry, that should read, ‘Isn’t the latter NOT safe now?’.
Also, using an email client to access Gmail will not automatically protect users from the LinkedIn type phishing emails.
VMthunder- I mention as one of my tips at the bottom of this blog post that people should consider using an email client. I even suggest Thunderbird.
Also, direct navigation has always been risky. Fat finger a key or two and you could wind up somewhere dodgy really quick (it’s called typosquatting and it’s still very prevalent).
Whoops, how did I miss that? Sorry…
My computer was INFECTED (thanks Kreb) when I clicked on the link you provided above – Contagiodump has a proof-of-concept page available at this link that shows the exact attack, except populated with “JDoe” in the username field.
Elaine, what anti-virus product are you using please? I believe this is a false positive.
Dear Elaine. There is no malware in that file. It will pop up with JDoe for everyone and even if you decide to enter your ID and password (which is not very wise in general for anything except legitimate websites), nothing bad will happen. You will get “page not found”. Your computer should be fine. Thank you. Mila
This is the Virustotal scan of that file you opened, it is 0/42 – negative on malware
http://www.virustotal.com/file-scan/report.html?id=2344dd0b78b5cb28f3d5776341559576401d479b2a4ca643595b88c56abe0a22-1307326796
I am sure that my gmail has been compromised and monitored, how can i make it safe again? (beyond checking fwd) Is there a way to id the culprit?