In July 2011, a customer at a Chase Bank branch in West Hills, Calif. noticed something odd about the ATM he was using and reported it to police. Authorities who responded to the incident discovered a sophisticated, professional-grade ATM skimmer that they believe was made with the help of a 3D printer.
Below is a front view image of the device. It is an all-in-one skimmer designed to fit over the card acceptance slot and to record the data from the magnetic stripe of any card dipped into the reader. The fraud device is shown sideways in this picture; attached to an actual ATM, it would appear rotated 90 degrees to the right, so that the word “CHASE” is pointing down.
On the bottom of the fake card acceptance slot is a tiny hole for a built-in spy camera that is connected to a battery. The spy camera turns on when a card is dipped into the skimmer’s card acceptance slot, and is angled to record customer PINs.
 The bottom of the skimmer device is designed to overlay the controls on the cash machine for vision impaired ATM users. On the underside of that space is a data port to allow manual downloading of information from the skimmer.
The bottom of the skimmer device is designed to overlay the controls on the cash machine for vision impaired ATM users. On the underside of that space is a data port to allow manual downloading of information from the skimmer.
 Looking at the backside of the device shows shows the true geek factor of this ATM skimmer. The fraudster who built it appears to have cannibalized parts from a video camera or perhaps a smartphone (possibly to enable the transmission of PIN entry video and stolen card data to the fraudster wirelessly via SMS or Bluetooth). It’s too bad so much of the skimmer is obscured by yellow plastic. I’d welcome any feedback from readers who can easily identify these parts based on the limited information here.
Looking at the backside of the device shows shows the true geek factor of this ATM skimmer. The fraudster who built it appears to have cannibalized parts from a video camera or perhaps a smartphone (possibly to enable the transmission of PIN entry video and stolen card data to the fraudster wirelessly via SMS or Bluetooth). It’s too bad so much of the skimmer is obscured by yellow plastic. I’d welcome any feedback from readers who can easily identify these parts based on the limited information here.
Here’s a closer look at the circuit board on top, which looks like some type of Flash storage device:
Here’s another look at the electronic parts wedged into the back of the skimmer:
It appears from the following image that the data storage capacity on the device is connected directly to the mag stripe reader (top, silver wire), while the device’s video camera is wedged behind the pinhole (bottom, gold wires).
The investigator I spoke with about the incident didn’t know much about the innards of the device, and said that those responsible have not yet been caught. But he did have something interesting to tell me about the origins of the skimmer: “It is believed that the green skimmer was made with the Stereolithography process.” Translation: The cops think thieves produced the card skimmer molds with the help of 3D printers.
These hi-tech and costly machines take two dimensional computer images and build them into three dimensional models by laying down successive layers of powder that are heated, shaped and hardened. In September, I detailed how U.S. investigators had arrested four men in Texas who allegedly built their ATM skimmers using a 3D printer they’d purchased with the proceeds of their skimming business.
In related news, New York County District Attorney Cyrus Vance earlier this month announced an 81-count indictment against three men suspected of planting skimmers at ATM machines in Manhattan. The indictment alleges that the men used the skimmers to steal the debit card numbers of nearly 1,500 individuals, and then exploited the stolen debit card numbers to make more than $285,000 in fraudulent transactions.
In the press release that accompanied the indictment, the district attorney released several images of the skimmer devices allegedly planted by the Manhattan trio. While these devices relied on a separate façade that held a hidden video camera to record customer PINs, there is little question that the same Chase ATM design was targeted. In the picture below, the hidden camera is the squarish silver block mounted vertically to the left of the PIN pad. An enlarged picture of the camera façade follows this one.
If you visit a cash machine that looks strange, tampered with, or out of place, then try to find another ATM. And remember, the most important security advice is to watch out for your own physical safety while using an ATM: Use only machines in public, well-lit areas, and avoid ATMs in secluded spots. Also, cover the PIN pad with your hand when entering your PIN: That way, if even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well.
If you liked this post, consider checking out the other stories in my ATM skimmer series, All About Skimmers.






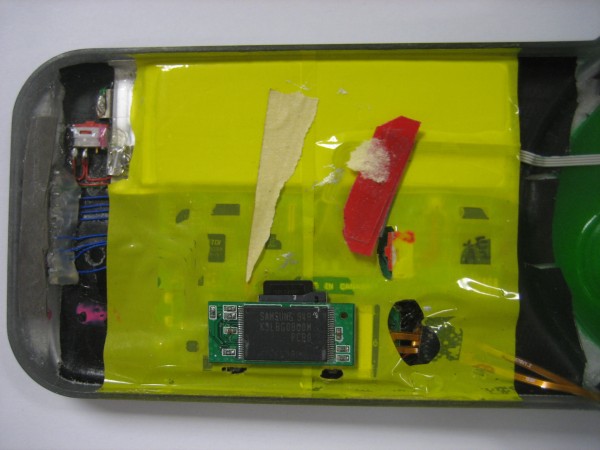




So I recognized that Samsung part immediately, having accidentally broken open a Lexar JumpDrive. It’s a USB NAND flash drive. Here’s the scary bit – based on the numbers visible, K9LBG08U0M, that’s a 32GB part. More interestingly, it appears to have been rigged to what looks like an existing slot immediately beneath it.
Here’s where things get weird, at least by my take. If you look at the zoomed shot of the Samsung NAND, you’ll notice that it appears to be stuck to an SD card which goes under the tape. Said SD card appears to be a MicroSD adapter with a MicroSD card loaded into it. So it may be a swappable custom built module.
The PCB is a bit confusing – position of slot plus battery? I think that might be a hacked BlackBerry, but don’t hold me to that. You can definitely hold me to the 32GB flash drive though.
I don’t think its a hacked Blackberry, It looks to be a Hacked camera with video and sound recording capabilities.
The FTDI chip under the yellow I believe the USB connectivity, which communicate to the rest of the device to grab the data.
The other thing I noticed was the PCB under the yellow tape was made in Canada.
“If you visit a cash machine that looks strange, tampered with, or out of place, then try to find another ATM.”
Shouldn’t you just inform the bank and ask them to inspect it? Why would you leave the hacked ATM to take advantage of subsequent customers?
Sure, if you feel like doing that. Usually, the thief who put the skimmer there is watching the ATM. Your call.
My advice was meant more for anytime (i.e., when the bank is closed, weekends, evenings, etc, when most people withdraw cash).
Also, in most of these skimmer cases, the thieves place the skimmer on the ATM after the bank closes on Saturday afternoon. Statistically, you’re probably a lot more likely to encounter a skimmer on the weekends or on Sunday.
If you encounter what looks like a skimmer or tampering on the ATM, you call the police. They will contact the bank manager or ATM owner and that person will come out and inspect the ATM with the police. I wouldn’t be surprised if there were also a 24/7 customer service number on most ATMs. Any company that ignores the warning of a skimmer on their equipment will be in the middle of a PR nightmare in no time.
I once found a skimmer on an ATM about a 20 minute drive from my house – I called my bank’s security/support line and they immediately shut down the ATM remotely, commanded it to dispense $20 for me and sent a technician out to fix it.
It was fixed when I came back 3 hours later.
This one would have got me. I usually put my other hand *over* the pin pad and not to the side when inputting my pin.
I guess US banks have still not lost enough to pay for a chip and pin system, eh? I think also perhaps a one time password chip on the card might help as well, such as a YubiKey like device embedded in the card…
But this all costs money 🙁
You need a mobile phone to “Rent-A-Bike”, but those blatant bastards at banking and finance don’t give a monkey on security and just prepone next Black Friday… How many clerks were substituted by this promised secure payment evolution? 90%? 🙁 …let’s switch to promissory notes instead. 😛
“This one would have got me. I usually put my other hand *over* the pin pad and not to the side when inputting my pin.”
Ditto me.
I usually pretend to enter a 6 or 7 or 15 digit sequence though; my real pin is entered with other numbers appearing to be entered in between the actual numbers of my pin (hope that makes sense).
Don’t know how obvious this ruse is though. I should film myself doing it actually to see if I can pick it heh.
It’s not that banks don’t want the encrypted chip cards. They really want to move to this type of card. The problem is with retail stores being unwilling to upgrade their card readers. Whats the point of issuing cards that your customers can’t use.
check out firstdata.com or star.com for more info.
Chip and pin cards still have a magnetic stripe for backup or for travel to countries w/o the readers (e.g. USA). In this case, we’re talking about ATM cards, so if the banks really wanted to roll it out they could at least start with their own ATMs. Once there’s critical mass, just increase the fee for swiped vs. chip-and-pin authenticated– that’d get the retailers to move over fast.
What they should do is implement 2 step authentication with people’s cell phones. Many web based companies are doing this now, and I would jump at the chance to use it with my bank for ATM withdrawals.
ATM Skimmers are becoming more prevalent as the sophistication of the skimmers rises, and as for sticking around a tampered ATM while reporting it there are documented instances of folks being assaulted by the fraudsters who were keeping an eye on the ATM. Best thing is to leave the immediate area and call the institution or authorities if the location is not open.
Two years ago in China I found an ATM infected by a spamming virus that opened thousands of cascading IE windows
It was hilarious
Tragic was the word you were looking for perhaps 😉
Hilarious because i took a lot of FAIL pictures 😀
Tragic because I walk other 30 minutes to find another safe ATM.
I don’t get why Diebold insists to making Windows-based ATMs instead using any other os.
Then, incompetent technicians will give full internet access to the ATM (lol) with no firewall (FAIL) and this happens…
To find out more about the device, I’d contact Bunnie Huang (his blog is here http://www.bunniestudios.com/blog/ ) He often has a “Name That Ware” contest where a lot of very VERY tech-savvy readers identify components and other features, and this looks like an excellent candidate.
Thanks a bunch, Nicholas
The link you graciously provided goes directly to my browser favorites.
There appears to be a FTDI-USB – serial port there. Whatever the hack is, it’s using a very slow method to get the data off it.
I couldn’t ID the FTDI definitively, but that’s it. Nailed it, Dennis. I don’t think it’s the data IO controller though. It’s an FT232BH – only part number that fits. Here’s some data on it:
http://www.ftdichip.com/Products/ICs/FT232B.htm
I wonder if they weren’t using that as an interface to do immediate delivery of collected data. That would make this skimmer a lot scarier to me, especially since you don’t need high resolution images to see the PIN entry.
But you got me thinking, and I don’t think it’s a BlackBerry or even a cell phone. It’s probably a mass produced SoC development board. (The big ‘MADE IN CANADA’ silk screening has me thinking that.) I would kill for a shot with the tape off, would probably tell us exactly who made the board.
It’s more likely that’s the interface to the actual card reader mechanism. Often mag stripe readers are RS232 output; it’s a pretty common set-up. If the underlying platform has no support for serial directly, but has USB ports (likely given the USB storage) then using the FTDI USB-RS232 chip makes perfect sense.
That’s what I thought initially, Jamie, but that’s where things get weird and why I’m particularly interested in this specific skimmer. The FT232BH is an RS232 to USB interface. But as far as I can tell, it’s routing to the contact pins at the bottom, rather than the magstripe reader. Either way, by my count, that puts it at 4 USB devices – possibly 3 if the NAND is piggybacking/juryrigged SD.
If we’re at 3 or 4 USB devices, which is probably accurate, that most likely rules out a phone or PDA being the base. You’d need a 4 port root hub controller. So even if the attached bits are off the shelf, that still requires a very sophisticated base to attach them to. We’re used to seeing juryrigged, hacked together skimmers built out of whatever’s laying around – MP3 players, etcetera. This one looks significantly more professional and sophisticated electronically as well.
More to the point; I suspect that under the tape is a custom built SoC PCB from a low volume manufacturer or an SoC development board. Either of which would be traceable back to the manufacturer and purchaser.
Two different circuit boards – top one is a magstripe card reader, which is connected to the card slot and the serial port out the side of the casing (MSR data is small enough that serial is OK to dump).
The second (lower) board is a video board from a micro camera, with the flash on the back being the on-board memory and the add-in memory card being the storage actually used to store the video of the customer PIN. Both are canablised from commercial products.
Criminal will have to manually retrieve the skimmer and then dump the card track and video separately, and then correlate.
Love the gizmo identification and analysis, guys! Keep it up!
I notice scratches around the download port which makes me believe the thief used it to download stolen data a number of times (notwithstanding the tests the “manufacturer” of the skimmer and the thief might have done). In my country in Western Europe there is a law requiring all POS to convert to Chip&Pin by 1st Jan 2012. The conversion runs a bit behind, around 92% were converted so far with just 3 weeks remaining. Anyway, I hope in a few months I’ll be able to run a neodymium magnet over the stripe of my debit card and fear those skimmers no more. (I’ll keep a credit card for trips abroad where Chip is not yet introduced/supported)
I wouldnt do that mate, when i went to bank a few weeks ago (natwest uk) i querieyed them on wether or not my bank card would still work as id run over the pin with a swivel chair, anyway they told me to try it but they said that with cash machines the data comes from the magnetic stripe and not the chip.
though iv heard other cases were apperently a cash machine will make sure a chip is there though dosnt actually check it
not a subject im particuarly clued up on to be honest. im sure though once everywhere changes to chip and pin a method of non virtual carding using chip and pin will emerge
I think the security is dependent on how much was invested into it. I recall an article last year in 2600 that documented an individuals experiment with the card chips, long story short he used a hole punch to take out the chip and tried to use his card minus the chip. The magnetic strip would not work at all for the user on any type of slider. When he inquired to the bank they informed him that if the chip is damaged/missing then it will not read, which is supposedly how the security for the cards works.
I tested using my card in a UK ATM, I put tape over the chip contacts and inserted it into the ATM.
The card was declined when I tried to withdraw funds. You NEED to have the chip to use an ATM.
In shop’s this is a different matter. A lot of shops will fall back to magstripe for “broken” chip cards.
Actually, not.
In my store, the POS will reject the sale if using the magstripe instead of the chip. The display will say “please insert the chip”
@ ED,
Either the chip or magstripe may be used depending on the whim of the person setting it up and the capabilities of the merchant system it is connected to.
Most ATM machines will read both if they are present and readable.
To understand why a little history and a world view is needed.
The predomanant view of the card issuers is “minimum hassle to card holders improves usuage and minimises support costs” (fraud has untill recently been an “externality” the cost of which is bourn by merchant, card holder, insurance usually in that order).
Historicaly “Chip-n-Spin” readers were rarer than hens teeth so to still work the magstripe had to still be used (and there are still merchants in Europe using magstripe only readers, as are a large number of banks for there “human tellers”…).
So as “Chip-n-Spin” transfered much of the then fraud liability onto the card holder or merchant, the card issuers included not just the Chip but the magstripe as well and if for some reason the chip failed it would “fall back” onto the mag stripe. If fraud was commited by copying the magstripe the system rather conveniantly gave the impresssion that the Chip had always been used (even when the mag sttripe had been used) so the customer got hit…
When you take a world view many countries (most of the Americas) don’t use Chip technology in their EPoS systems and US banks appear not to want to issue them.
So when an ATM card gets a card put in it reads both the mag stripe and the chip if present. If there is no chip it looks up the bank identification number to work out what to do, thus in the UK if a UK or European issued card is presented without a chip it should reject it, but if a US or other non EU issued card is used it does not have a chip so the ATM will use the magstripe info.
However originaly all systems if the chip was either not present or not acting normaly “for customer conveniance” it “fell back” to mag stripe, and would have stayed operating in this way. What changed it was all the negative publicity and research by the likes of students and researchers at the UK’s Cambridge Computer Labs ( http://www.lightbluetouchpaper.org ) who have repeatedly foound and published the failings of the EMV card issuers.
So now some banks and merchants have configured there ATM / EPoS machines to work the way you would hope.
However “watch out” if you have a combined credit / debit card, many merchants have set the terminals so it only works in “debit” not “credit” mode which puts the curd holding customer at a considerable disadvantage, and potentially large overdraft or other bank fees. It also gets the merchants and banks out of parts of consumer protection legislation.
So always always make sure you have either a debit card or credit card or one of each, but never ever ever a combined one.
Oh and guess what the next scam will be now banks are issueing “contactless” “near field” payment systems in your bank cards?
Which also don’t need your PIN to be entered if the transaction is below a certain sum…
Do yourself a favour and write to your bank refusing such a card, and back it up by shifting your account if the do send you one.
There are only two ways to stop this sort of “techno creep” that the banks use to offset liability and thus responsability for ensuring their systems are secure. 1, refuse to play. 2, take legal action. Of the two the first is the better route to take if you can…
I was looking at the screenshots and actually it looks like it could be from an old PDA. Just my thoughts…
This thing would have fooled me. I dont use ATM’s often. THe one thing I did notice is the hand drawn star on the underside of the reader. Looks like this guy tagged his work. The buttons for the impared users are worn, so this unit was inplace/used often or they really took time to make it. This almost seems that they had free access to an ATM alowing them to get percise measurments to make the device. The reality is this is impressive. I dont agree with what they are doing, the Banks need to truly implement a better security system or they ane the people who use them are goingt to start to really loose money.
You can buy ATM fascias online. There are also sometimes full ATM’s for sale on eBay.
I hope they don’t “lose” money. I’m okay if they “loose” money though
When you get a new cell phone and they give you that little plastic bag to donate your old one, I always wonder where they go. They’re not much use to poor people if the batteries aren’t replaceable.
So is the lesson learned here to grab the card slot and give it a tug when you go to use an ATM? It isn’t a failsafe against all skimming threats but is at least something….or at least can give you the feeling that you have done something pro-active 🙂
That actually is part of my protocol of going to the ATM: Give the card reader a good grab…
Yet to find anything, much to my dissapointment.
I do this aswell but thinking about it if the criminals are around the corner may not be a wise idea to remove their equipment considering these things go for 5 -8 grand on the blackmarket
Sounds like grabbing is a fantastic idea, then; if it actually comes loose, running is an even better idea. The only trouble remaining will be fencing it for your $5k.
Google south bay area Lucky’s skimmer. After 1 skimmer was found at a self checkout register at Lucky’s, they searched all of the locations and found about 20 professional skimmers.
Money was actively being taken from customer bank accounts. The recommendation was to close your account if you shopped there. Pretty severe.
The 3D printer angle is interesting. They are high-tech, but not particularly expensive anymore; it’s even possible to make a high-resolution stereolithography variant at home: http://www.instructables.com/id/Build-a-Laser-3D-Printer-Stereolithography-at-Ho/
Also see e.g. http://reprap.org/ or http://makerbot.com/ (among many others.)
The article mentions that STL may have been used to make molds. Maybe they 3d printed a mold and then cast the parts using liquid resins that solidify.3d printing, especially in the cheap end tends to produce a rough “pixelated” surface finish. That should be easy to identify from the quality of the surface finish.
http://goo.gl/TbUHi
@ Aleina,
Yes some oof the early systems do tend to be pixilated but that is not usually an issue.
The solution has been known since tthe early days of green sand pattern making for casting metal, which kind of got started big time at Iron Bridge in the UK a couple of hundred years ago.
Whatt you do is either make an “undersized plug” or “oversised mold” pattern and smoth it to the correct shape and dimensions and finaly polish by adding a surface agent (like a paint) that provides a hard wearing surface that can be pollished in use to make the secondary plugs or molds actually used to make the casts or cast molds.
Can’t ATM manufacturers put a camera on the card reader itself, with a known good image of what it’s supposed to look like to compare to? Give it a two minute time window, so that cards themselves don’t trigger the alert. Then when one of these are on, the change will be detected by the camera and alert the authorities, who can then build a sting operation to see who picks it up. Seems rather simplistic, but would eliminate a lot of the problems.
I know that cameras will see color changes with the change of day, but it should be relying on edge detection anyhow.
Please tell me that that the last picture in the article does NOT show an actual card!?!?
I can clearly read the card’s numbers except for two digits & the security code is clearly visible!
Hrm. Do you think there’s any chance that the card in the picture was NOT re-issued? It was obviously confirmed to have been stolen by NY authorities.
I do not understand what banks do. It being 10 years since this practice started and is constant in our country and they have not done anything about it.
Is it clear that they want you to pay the costs and not them.
Just hoping that that is the case Brian, but working in security myself I have often seen people build walls against the percieved threats (skimmers in this case) & ignoring off axis attacks (using what might be a valid card as an example).
Without knowing I’d blur out the numbers just to be on the safe side.
Cheers & thanks for the article
ATM’s should have perfectly flat surface with the card slot.
The monitor should first ask the customer to examine the slot. They should show a photo of what the smooth face and slot should look like. If it doesn’t look like it, then ask the customer to report it.
My thoughts on the device:
starting at the skimmer module, it looks like possibly a hacked square card reader for mobile phones. wiring looks like that used on a standard IDE ribbon cable.
a led is added to replicate the look of the target device. judging by the position, wouldn’t be surprised if the led was intended to assist the camera module capture more information by proxy.
the guts also look like COTS parts covered by yellow tape commonly used to protect electronics. battery on top, brains below. can power the card reading module 24/7 and control the camera module with motion sensitive recording. data port on outside looks like standard usb (data pins, 5 volt rail). not sure why separate storage but might be a limitation of the device maker’s ability, or intentional (usb hub).
Love how the images are served with normal http – therby causing an IE warning – the default answer to which, causes all of them to not appear!
Not impressive for a security focussed blog …
Wait, you’re security focused AND you use IE? Does not compute.
While y0u certainly can view my site in https, why would you fret about content being served that wasn’t?
I originally had the images enlargeable to their actual size, but that was killing the page load times.
If you had any idea how much bandwidth has been burned through in the last couple of days serving these pics, you wouldn’t be complaining. I guess you can always get your money back — oh wait…
Hi,
I’ve always been wondering: are the skimmers easy to remove by hand or not? Basically, can I check there is no skimmer by trying to remove the card slot by hand before inserting my card?
In other words, is there a test I can easily do when facing an ATM?
Yep. Most will come off with a good solid yank. After all, the thief has to be able to quickly retrieve it from the machine also.
OK, thanks. I’ve been doing that for some time but I don’t think I’ve ever faced a skimmer and I was really wondering how strong I had to pull.
@ Brian,
First off nice to have mobile posting back on thanks :0)
Secondly, I don’t know about the US but the ones in the UK in many cases are very very firmly attached often by double sided adhesive foam tape.
I actually saw the criminals take one off near Victoria St in London a few years ago and they used a custom designed crow/pry bar that had been machined down to do it. It was a very scary tool because if they turned it around and hit you with it it looked more than sharp enough to go straight through your clothes or skull…
All the bank bashing is quite interesting. In 30 years of security I have yet to see an atm manufactured by a bank. You can only pruchase what is for sale. Great site btw
@ BrianB,
True but only half the story, people onlyy offer for sale goods that will sell.
Thus unless an external driver comes in to change the market,
Banks will only buy what they want even if the manufacture offers more for the same price the bank will perceive the extra configuration and support required as a significant cost, so still won’t buy it…
Wells Fargo updated all the ATMs in our area last month, and they now all have that same translucent green circular plastic piece for the card slot.
Is there any security rationale for this plastic piece? The first time I saw it, my thought was that it was to make attaching a skimmer harder — but clearly it didn’t work in this case. Are the translucency and brightly-lit green attributes meaningful?
@Brian Krebs:
I see what’s happened now.
Someone linked to your page as https://, not http://.
Reasonably, I just followed that link. IE saw the mixture of secure and unsecure content (ie. the images), so it asked: “Do you want to view only the webpage content that was delivered securely?” I pressed Enter, but the default answer was Yes, so the images were not displayed.
I thought this was odd behaviour for a security focussed blog. I believe that was a fair reaction at the time. However, now I can see that the fault was in the original link – not in the blog.
@all:
Chip and pin is broken already. http://www.cl.cam.ac.uk/~sjm217/papers/oakland10chipbroken.pdf
@roofuskit:
We’d all like to reduce carbon emissions by not driving a car. Hands up all who don’t drive cars! Real life can be tempered by, how can I put this, real life practicalities.
Thanks TC, for that link on broken Chip-&-Pin tech; I needed that document for my records. It is something that has been brewing for sometime now.
The ingenuity that these skimmers have is really something to marvel at. You have to be expert in 4 fields (and probably more) to be able to pull this off. You need a fabricator, a hacker/coder, a circuit builder, and someone with knowledge of gms or bluetooth protocols. And it all has to be done seamlessly! Really interesting stuff.
I’ve been on some of these sites, and one comment that really struck me is one commenter reprimanding his younger less experience pupils saying, ‘you guys are so lazy. all you want is someone to hand you the info. go research and really learn about this stuff and you’ll be far more successful.’ Indeed! An engineering degree would be quite useful in such pursuits!
When you think about it, finding one of these things might not be a bad thing really. It’s the perfect opportunity to reverse engineer the criminals game. And it’s pretty simple:
1] find a skimming device on an atm
2] insert your card and withdraw and normal
3] some time later, disguised, withdraw as much from you account as you can
4] report skim device
5] report “missing” funds from your account
boom! merry christmas.
Hmm, just like some bank presidents did after the old timey way of banks being robbed! HA!