A $170,000 cyberheist last month against an Illinois nursing home provider starkly illustrates how large financial institutions are being leveraged to target security weaknesses at small to regional banks and credit unions.
I have written about more than 80 organizations that were victims of cyberheists, and a few recurring themes have emerged from nearly all of these breaches. First, a majority of the victim organizations banked at smaller institutions. Second, virtually all of the money mules — willing or unwitting individuals recruited to help launder the stolen funds — used accounts at the top five largest U.S. banks.
The attack on Niles Nursing Inc. provides a textbook example. On Monday, Dec. 17, 2012, computer crooks logged into the company’s online banking accounts using the controller’s credentials and tunneling their connection through his hacked PC. At the beginning of the heist, the miscreants added 11 money mules to Niles’ payroll, sending them automated clearing house (ACH) payments totaling more than $58,000, asking each mule to withdraw their transfers in cash and wire the money to individuals in Ukraine and Russia.
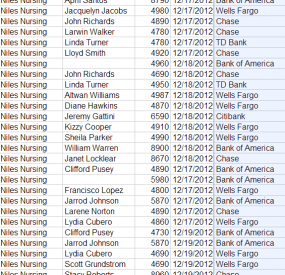 Niles’ financial institution — Ft. Lauderdale, Fla. based Optimum Bank — evidently saw nothing suspicious about 11 new employees scattered across five states being added to its customer’s payroll overnight. From the bank’s perspective, the user submitting the payroll batch logged in to the account with the proper credentials and with the same PC that was typically used to administer the account. The thieves would put through another two fraudulent payment batches over next two days (the bank blocked the last batch on the 19th).
Niles’ financial institution — Ft. Lauderdale, Fla. based Optimum Bank — evidently saw nothing suspicious about 11 new employees scattered across five states being added to its customer’s payroll overnight. From the bank’s perspective, the user submitting the payroll batch logged in to the account with the proper credentials and with the same PC that was typically used to administer the account. The thieves would put through another two fraudulent payment batches over next two days (the bank blocked the last batch on the 19th).
In total, the attackers appear to have recruited at least two dozen money mules to help haul the stolen loot. All but two of the mules used or opened accounts at four out of five of the nation’s top U.S. banks, including Bank of America, Chase, Citibank, and Wells Fargo. No doubt these institutions together account for a huge percentage of the retail banking accounts in America today, but interviews with mules recruited by this crime gang indicate that they were instructed to open accounts at these institutions if they did not already have them.
ANALYSIS
I’ve spoken at numerous financial industry conferences over the past three years to talk about these cyberheists, and one question I am almost always asked is, “Is it safer for businesses to bank at larger institutions?” This is a tricky question to answer because banking online remains a legally and financially risky affair for any business, regardless of which bank it uses. Businesses do not enjoy the same fraud protections as consumers; if a Trojan lets the bad guys siphon an organization’s online accounts, that victim organization is legally responsible for the loss. The financial institution may decide to reimburse the victim for some or all of the costs of the fraud, but that is entirely up to the bank.
What’s more, it is likely that fewer cyberheists involving customers of Top 5 banks ever see the light of day, principally because the larger banks are in a better financial position to assume responsibility for some or all of the loss (provided, of course, that the victim in return agrees not to sue the bank or disclose the breach publicly).
I prefer to answer the question as if I were a modern cyberthief in charge of selecting targets. The organized crooks behind these attacks blast out tens of millions of booby-trapped emails daily, and undoubtedly have thousands of stolen online banking credentials to use at any one time. There are more than 7,000 financial institutions in the United States…should I choose a target at one of the top 10 banks? These institutions hold a majority of the financial industry’s assets, and they’re accustomed to moving huge sums of money around each day.
On the other hand, their potential for fraud is almost certainly orders of magnitude greater than at smaller institutions. That would suggest that it may be easier for these larger institutions to justify antifraud expenditures. That incentive to enact antifraud protections is even greater because these institutions have huge numbers of retail customers, a channel in which they legally eat the loss from unauthorized account activity.
Wearing my cyberthief glasses, if I’m looking at a huge pile of data stolen from thousands of victims, I’m probably more apt to target victims at smaller banks based on one simple assumption: Because I’m going to have a much higher success rate than I would targeting customers of larger institutions.
COMPETING ON SECURITY?
All of this raises several questions: Can smaller financial institutions realistically hope to compete with the larger banks on security? Should they even try? The smaller institutions would not appear to have the same economies of scale to achieve the same security that the top banks have. Perhaps to compensate for this, many smaller institutions have contracted with banking industry service providers to help them operate their online banking services.
Unfortunately, securing the customer transaction space has traditionally not been a major component of these outsourced services, which focus on identifying phishing attacks and other anomalies on the bank’s Web portal and internal systems. For whatever reason, these providers generally have not used the intelligence coursing through their networks to help smaller bank customer discover and stop ACH fraud.
Case in point: Optimumbank’s service provider is Fiserv, one of the largest banking industry service providers. According to Fiserv’s site, at least 52 percent of the nation’s $19 billion in ACH payments are processed using Fiserv software. If this is true, one might think that Fiserv’s systems handled about half of the mule transfers that were sent from Niles Nursing’s hacked bank account.
But according to Murray Walton, Fiserv’s chief risk officer, the software that most of its customer banks run — called PEP+ — is a client solution that does not interact with the company’s data centers. He said while Fiserv does offer an antifraud solution called FraudNet, that tool is designed for online bill pay services that banks can use to detect fraud patterns on consumer accounts.
“There are vendors who can knit it all together for banks, but that isn’t what we do,” Walton said in an interview. “For various and sundry reasons we don’t offer an engine that does the same thing as [an anti-fraud provider like] Guardian Analytics. Realistically, the client and end-user have responsibilities that they can’t abdicate to us. Everyone in this needs to take it seriously and not think that someone else has their back.”
Mark Ackerly, vice president and director of information security at Community Bank N.A., a financial institution based in DeWitt, NY, said there are a number of benefits that come from small banks that may not be immediately obvious.
“Generally speaking, community bank’s that may not have the ability to offer complex automated anti-fraud solutions are able to leverage their smaller size and strong customer knowledge to utilize more simplified solutions in a manner that makes them very effective,” Ackerly said. “It is also this same high level of customer interaction, typically found at community banks, that makes opening of accounts for malicious activity less anonymous or simplified.”
Although historically service providers may have trailed in some of their technological security offerings, that posture has shown significant change, he added.
“Some of the major service providers are starting to show substantial promise in their offerings to detect malware and malicious activity,” Ackerly said.
C.Y.A.
As it stands, the big banks don’t have an incentive to police new accounts for mule activity, because it’s generally not their customers who are getting robbed from this activity, said Avivah Litan, a fraud analyst with Gartner Inc.
“The bad guys shouldn’t be able to set up these mule accounts in the first place,” Litan said. “The bigger banks are not doing a good job of screening for this activity because they’re not the ones eating the fraud on these attacks on smaller bank customers. [The bank service providers] should be spending more money. And the regulators should be coming down on them harder.”
It appears that banking regulators are taking a closer look at the role of service providers. Federal Financial Institutions Examination Council (FFIEC) recently issued revised guidance for bank examiners clarifying that “outsourced activities should be subject to the same risk management, security, privacy, and other internal controls and compliance policies as if such functions were performed internally, and that a financial institution’s board of directors and management have the responsibility for ensuring that outsourced activities are conducted in a safe and sound manner and in compliance with applicable laws and regulations.”
In the end, it may be that small, regional and local banks can pool their clout and resources to extract more from service providers than what those companies are currently offering. It would also be encouraging to see these smaller institutions taking the lead in educating their customers about the seriousness of the threat that faces them.
I’ve often heard it said that in times of economic uncertainty, smaller and local financial institutions are more likely than larger banks to lend money to small businesses. If this is true, then it is likely because these institutions truly know their customers, and know a good bet when they see one. My hope is that smaller institutions make every effort to better understand their customers’ online activity as well, and have the ability to detect and act on red flags that too often indicate an account compromise.
In the meantime, none of this matters: As Fiserv’s Walton said, the best solution for businesses is to behave as though nobody has your back. Like it or not, the “applicable laws and regulations” still ultimately leave businesses responsible for ensuring their own security when banking online. If you run a small business and wish to bank online, shop around if you can and find a bank that offers and advocates additional layers of security. If your bank offers it, consider signing up for Positive Pay; this anti-fraud service was built to defeat check fraud, but it is remarkably effective at stymying unauthorized transfers both online and offline. Niles Nursing was not signed up for Positive Pay at the time of its cyberheist, although the company is now, according to an employee who spoke with KrebsOnSecurity.
But the best way to avoid a cyberheist is to not have your computer systems infected in the first place. The trouble is, it’s becoming increasingly difficult to tell when a system is or is not infected (for example, Niles Nursing was using Microsoft Security Essentials, which failed to detect the banking Trojan used in the attack.) That’s why I advocate the use of a Live CD approach for online banking: That way, even if the underlying hard drive is infected with a remote-access, password stealing Trojan like ZeuS or Citadel, your online banking session is protected.
In an upcoming post, I’ll be looking at different affordable options available to small businesses for insuring themselves against losses from cyberheists. In the meantime, I’ve assembled a short list of other tips that small businesses should consider when banking online.
Be careful out there, folks.




Cudos, Brian, good work! – I stay with your advise:
“Don’t use Microsoft Windows when accessing your bank account online.”
(http://krebsonsecurity.com/2012/07/banking-on-a-live-cd/)
Great summary of the landscape surrounding a critical problem. So much of our economy is based on trust in the integrity of our financial system. The stakes are huge. If knuckleheads are allowed to tarnish that trust with abandon with schemes like you describe and without effective countermeasures, the entire system is in danger of collapsing on itself.
I am forwarding a link to your posting to my local credit union’s officers, several small businesses and various legislators this morning.
Thank you for continuing to research and publish on this very important topic.
Brian, was MSE the only major (free) AV to miss that trojan vulnerability at the time, or were others among the major vendors also vulnerable when the exploit took place? Has MSE now patched itself to block that particular trojan and any variants?
As you’ve recommended use of MSE in the past for average users, has this failure altered your view on that recommendation in any way?
Recent tests of AV capability by two of the main AV testing organizations labeled Microsoft Security Essentials as less capable than a number of others.
Both Avast and AVG – two AV products I recommend to home user clients – did better and are free for home users.
Microsoft Security Essentials is free for business users for up to ten machines, but as a result of the recent tests I can no longer recommend it to small business clients.
I switched from MSE to Bitdefender Internet Security two months ago when it was reported that AV-test.org had decertified MSE.. Bitdefender isn’t free, but then neither is my fire insurance.
I just finished cleaning up a PC that had MSE on it, and that was one of the top worst messes I’ve seen in a long while. I don’t need to read comparatives on AV, I know I don’t ever want MSE on any of my machines!
For regular business one needs the blended defense – for banking I’ll stick to Puppy Linux LiveCD!
For regular business one needs the blended defense – for banking I’ll stick to Puppy Linux LiveCD!
> I fully agree, I can’t stress this enough
Heh 😉 … bad as MSSE is comparatively your probably still going to be cleaning up a lot of crap regardless of AV if your dealing with less savvy users. Not that I’d recommend using it.
Very true Neej;
But once a client gets onboard with me, the only things they catch are usually something a boot scan with a rescue disk can take care of. My Hiren’s USB stick ain’t bad either – usually a small job if they do what I tell them. I only have one stick in the mud, and I continually threaten to end support if she doesn’t wake up. She knows going elsewhere will cost her dearly!
Some of the good tools like Combo Fix have been bypassed by the malware as well. This is why I like a good HIPS, where there are no signature updates or obsolete technology like that. Keeping most of the junk OFF the machine in the first place goes a LONG way! B-)
This article is hitting on all cylinders. Fraudsters will always go for the easy target first. After all, theirs is a game of odds. If they stand a better chance of getting your money than that of the guy down the street, they’ll take yours.
Taken another way, you don’t have to have to be the fastest gazelle in the herd, but you sure don’t want to be the slowest.
Make it hard enough for the fraudsters to get your money, and they’ll just go someplace else. For a lot of small businesses, the problem becomes knowing how to do this without spending a ton of money. The Live CD approach advocated by Brian is the most effective free way to mitigate your risk.
Several years ago, we identified that the most challenging fraud for a Bank to detect was Account Takeover Fraud used to manipulate a payroll batch.
For many reasons, Banks have very limited visibility into changes in payroll (think of all the new employees being added/removed to a restaurant franchise payroll, for example).
The major software providers are taking steps — albeit slowly — to enhance their software. But until the methods we identified are used for every payee/recipient change made to an ACH or Wire batch, the problem will continue.
In the meantime, we continue to recommend that Small and Medium Business insure themselves with an underwritten crime policy (see your insurance agent) or our EFTGuard product.
A DSL line costs $35-40 per month. Use it only for on-line banking. Do not connect it to your network.
Use a non-windows live CD.
I learned the hard way…
Don’t think “if we ever get hacked”…think “when we get hacked”…
Thank you for highlighting the need to look at the entire value chain/banking ecology. I think too much effort is wasted on transaction security, but if any of the other links, customer systems, customer employees, bank systems, bank employees, outsourced services, service employees are compromised the last step in the chain is moot.
It is key that everyone in the chain takes responsibility for their people, processes, systems, and outsourced services. By looking at the transaction alone, people get a false sense of security. That is why not only customers need to assume their are compromised, so do the rest of the players. Banks and processors need to stop operating like their are ‘safe’.
The articlediscusses the role and responsibilities of
large and small banks as well as 3rd party providers when it comes to providing a secure environments when doing online banking (or payroll or …). It basically boils down to a small number of principles (which every security professional will preach over and over):
Don’t trust anyone. Trust if good – control is better!
Do your homework when it comes to security.
Keep your providers on their toes and demand security, transparency and assurance.
Simply not going to happen: it’ is too expensive for small banks to effectively secure their online banking systems. Inertia is also a problem. Convenience will always trump security when it comes to the human factor and nowhere is this illustrated most than the banking industry. A very good effort Brian but nothing is going to change. At least not until either congress steps in with stricter compliance laws and accountability or there is such s major breach exposed that they can’t absorb it as “the cost of doing business”
When the live CD can seamlessly coordinate banking transactions with accounting software like Quicken, you’ll see more interest.
QuickBooks Online usage is increasing:
22 August 2012
http://www.theprogressiveaccountant.com/news/move-to-quickbooks-online-continues.html
Sadly, the service is “officially supported” only on Windows and Macs. Unofficially, Intuit recommends that either the Chrome or Firefox browser is used with Linux:
“What browsers can I use to access QuickBooks Online?
https://qboe.custhelp.com/app/answers/detail/a_id/1667
And some small businesses are successfully using the service with Chromebooks:
http://decomplexification.com/2012/11/05/can-you-use-quickbooks-on-a-chromebook/
On Chromebooks, the Chrome browser includes a built-in PDF Reader plug-in and most Linux LiveCDs include the Firefox browser and a PDF Reader.
Putting your money in any bank can be a risky business, bank failures seem to be gaining momentum.
http://www.fdic.gov/bank/individual/failed/banklist.html
How would you make payments to employees and vendors without a Bank? Cash? Seems like using a Bank is pretty much required if you are going to be more than a sole proprietor. Even if your Bank fails, you’ll hardly notice it (while the taxpayer, certainly does). The failed bank gets a new name and off you go on Monday morning.
=”Niles’ financial institution — Ft. Lauderdale, Fla. based Optimum Bank — evidently saw nothing suspicious about 11 new employees scattered across five states being added to its customer’s payroll overnight. ”
In Payroll 101 you are going to learn about controls. You have a base control. + maintenance = new base control . + wagelist = batch control .
anyone thinking because they are using a computer they don’t need to do these fundamental controls belings in Niles Nursing but not as IT Staff .
I wouldn’t assume that payroll staff didn’t perform a weak control before batch processing of the new employees began.
So pretend you’re giving a recommendation to the payroll department’s management prior to this event.
Payroll Manager: “You think we should do what?”
Infosec: “You really need someone to review the new employee listing more carefully before they’re added to the payroll master file.”
Payroll Manager: “Well how do we know if they should be there or not?”
Infosec: “Get their supervisor or manager to ok it.”
Payroll Manger: “Ok, well let’s look at these new 11 names right here, they were added by the company controller. Do I really need to go above him? Besides, we’re busy enough as it is. We don’t have the budget to hire another person to perform all these reviews.”
To me the most interesting follow-up item in this story is who will lose their job over this event? My guess would be that the head of information security will get axed and the payroll manager and the controller will have to follow the controls they argued against implementing as a punishment for being stupid.
Or, the bank could ask for (perhaps insist on) some independent, separate verification from a company’s HR department of new hires and terminations prior to a each new payroll cycle. So if the payroll request set doesn’t match the validation reference of employment from the 2nd source, a flag is raised and the bank actually initiates a person-to-person phone call to resolve the discrepancy before any funds are actually issued. It wouldn’t have to be onerous and could be set up as a mostly electronic function — just a two-step authentication that involves a simple arithmetic verification check without personal identification before any human is notified.
JimV, I completely agree with you, but who does that?
I’m sure these people will do that…now. But prior to a major breach in security, what business spends the extra time and money to implement smart controls. They don’t, they won’t.
What they will do is say “What’s the risk?” Translation: How can you pin that on me? Even in that scenario I’ll still collect my pension, 401k, drive a new SUV and make my house payments because I’m a Payroll Manager, I’m not in charge of security. While if I add in two factor authentication or any other control that might inconvenience me (mainly by increasing my budget) that actually might impact my ability to put my kids in private school this year.
I think an interesting form of new legislation would be to require all companies, private and public to disclose how much of their overall budget goes towards information security.
Isn’t a separate verification really just a form of “out of band” authentication?
The issue is MITB manipulating sensitive data elements (like routing # and account #) on the wire while displaying what was entered on the screen.
Only some form of out of band is an effective control against this, something that prevents MITB, or an insurance type solution.
goeastern europe go !!! well done
Sorry for offtopic,
Here is some relatively fresh information about Chronopay case in Russian court.
http://www.compromat.ru/page_32949.htm
This site has many articles on “controvercial” stories and cases.
Why isn’t more attention paid to the mules? Perhaps the banking industry should sponsor TV ads that advise the public about what a mule does and why it is part of an illegal enterprise.
Negative publicity about the mule profession could make it more difficult to find people to do that job.
SoundPass removes the human element from the total Login, therefore preventing any Trojan real-time Keyloggers from stealing the virtual SoundPass credential dynamic token. This solution is better than any existing solution available at any major Bank protecting massive volumes of users. Besides being more secure, it is also more user friendly and more affordable.
Yes it uses a Java applet to generate a new virtual token for every Login because Java is the stronges program language online. Today’s Java vulnerbilities would not allow a Hacker into a SoundPass protected account. The Hacker would have never gotten into the online bank account in the first place if it were protected by SoundPass. For a major online banking provider to make the comment that user’s must watch their own backs will not hold up in court of law, as we have already seen. Banks are responsible for providing best possible security per the FFIEC.
Banks could implement Smartcards to properly protect their online banking members but Smartcards are more expensive, difficult to deploy to massive volumes of users and they are cumbersome for the users. By the way, SoundPass was designed from a Smartcard. So their are strong solutions available and these types of breaches DO NOT have to keep happening over and over again!
Instead of trying to freeload off of Brian’s blog, why don’t you do the ethical thing and buy some ad space.