Nate Anderson at Ars Technica has a good story about how investigators tracked down “Virus,” the nickname allegedly used by a Romanian man accused by the U.S. Justice Department of running the Web hosting operations for a group that created and marketed the Gozi banking Trojan. Turns out, I’ve been sitting on some fascinating details about this hosting provider for many months without fully realizing what I had.
On Wednesday, federal prosecutors unveiled criminal charges against three men who allegedly created and distributed Gozi. Among them was Mihai Ionut Paunescu, a 28-year-old Romanian national accused of providing the gang “bulletproof hosting” services. Bulletproof hosting is an Underweb term for a hosting provider that will host virtually any content, from phishing and carding sites to botnet command centers and browser exploit kits. After I read the Ars story, I took a closer look at the Paunescu complaint (PDF), and several details immediately caught my eye.
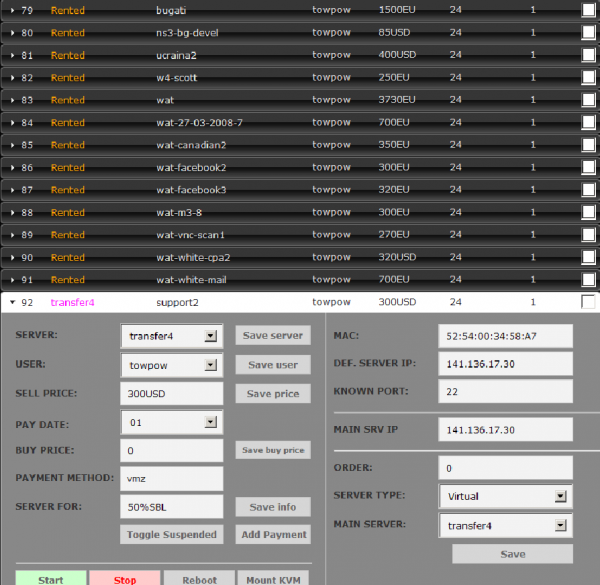
For one thing, the feds say Paunescu was an administrator of powerhost.ro (virus@powerhost.ro). In December 2011, a source shared with KrebsOnSecurity several massive database dumps from that server, which had apparently been hacked. Included in that archive was a screenshot of the administration panel for the powerhost.ro server. It visually depicts many of the details described in the government’s indictment and complaint against Paunescu, such as how the BP provider was home to more than 130 servers, and that it charged exorbitant prices — sometimes more than 1,000 euros per month for a single server.
The above screenshot (which is a snippet taken from this full-screen version) shows that this server was used for projects that were “50%SBL,” meaning that about half of the properties on it were listed on the Spamhaus Block List (SBL), which flags Web sites that participate in malicious activity online, particularly sending or benefiting from spam and hosting malware. Some of the names chosen for the servers are fairly telling, such as “darkdeeds1,” “darkdeeds2,” “phreak-bots” and “phis1.” The data dump from powerhost.ro included multiple “drop” sites, where ZeuS and SpyEye botnets would deposit passwords, bank account information and other data stolen from tens of thousands of victim PCs.
Paunescu is of course innocent until proven guilty. But from reading the government’s indictment of him, it’s clear that if he is the bad guy the government alleges, he was not super careful in hiding his activities. Within a few seconds of searching online for details about Internet addresses tied to powerhost.ro’s operations, I found this record, which includes his full name and lists him as the owner. Also, a simple Google search on powerhost.ro indicates that Paunescu is the rightful owner of the address space assigned to powerhost.ro.
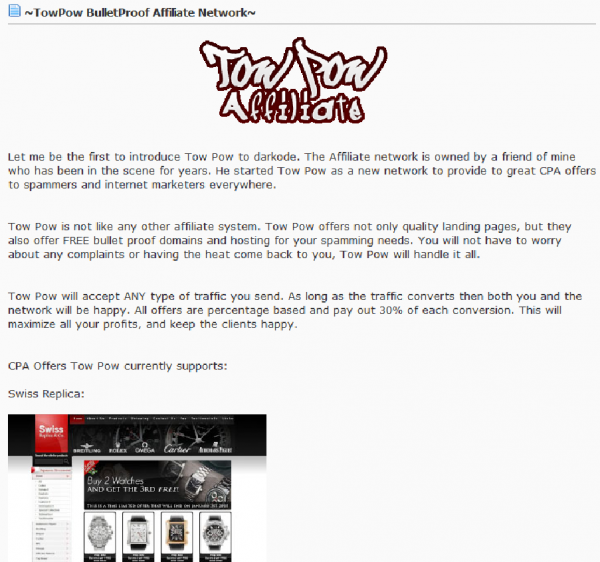
In the screenshot above, we can see several servers on powerhost.ro that were rented to miscreants who ran the TowPow pharmacy and replica affiliate program. TowPow advertised itself as a bulletproof hosting provider that was “Made by Spammers, for Spammers,” and would accept any type of traffic.
“TowPow is not like any other affiliate system. Tow Pow offers not only quality landing pages, but they also offer FREE bullet proof domains and hosting for your spamming needs,” read one advertisement for the affiliate program posted to an underground forum in March 2010. “You will not have to worry about any complaints or having the heat come back to you, Tow Pow will handle it all.
Stefan Savage, a professor at University of California, San Diego’s Department of Computer Science and Engineering, said TowPow affiliates were a huge source of junk email.
 “They basically owned the U.S. spam-advertised replica market, and they seem to dominate the herbal market as well,” Savage said.
“They basically owned the U.S. spam-advertised replica market, and they seem to dominate the herbal market as well,” Savage said.
Among the files leaked from powerhost.ro was the entire affiliate database for TowPow. It’s not clear who ran TowPow, or if “Virus” was somehow involved in the day to day operations beyond providing hosting for it, but the TowPow SQL database (saved as “blue4rep90_felon.sql”) includes a “tickets” section where users could submit help requests, place orders for hosting, or pass special instructions for wiring funds.
For example, in the following message, an affiliate pings the program administrators and asks for new hosting to be set up to handle ZeuS botnets. To wit:
(72, 61, ”, ‘Hi!\r\nI need BP link for Zeus site!\r\nThanks’, ”, ‘Web’, ‘80.232.219.254’, ‘2011-07-18 16:59:42’, NULL)
This user, “Daniel Mihai,” shows up throughout the database:
(58, 49, ”, ‘wire info:\r\niban: RO23INGB0000999901772881\r\naccount holder: Dan Mihai Daniel\r\nswift code:INGROBU\r\nbank name; ING Office Targoviste Independentei\r\nbank address:Bd.Independentei nr.3A, bl.T1, targoviste/dambovita\r\n\r\nplease tax me the 80$ wire fee’, ”, ‘Web’, ‘82.137.10.254’, ‘2011-05-13 00:37:58’, NULL),
Some of the top TowPow affiliates earned thousands of dollars a week advertising the program’s herbal and replica sites via spam:
UCSD’s Savage said the TowPow database indicates that many of its affiliates were referred from ZedCash, another affiliate marketing program strongly associated with replica and herbal pharmacy spam. In fact, the top referrer used the nickname “TowPow” and password “ZedCash.”
According to Spam Trackers, ZedCash is run by a hacker who uses the nickname “Ucraineanu”. Interestingly, this nickname shows up as “Ucraina2” in the powerhost.ro screenshot above next to one of the servers that TowPow rented for USD $400 per month. Savage notes that the TowPow database shows which members ran the program, and that at the top of the list is a member who used the email address “ukraineanu@yahoo.com”.
INSERT INTO `requestaffiliate` (`raid`, `raemail`, `referrer`,
`radate`, `rastatus`) VALUES
(159, ‘ukraineanu@yahoo.com’, ‘279’, ‘2010-05-25’, 1),
(160, ‘cergatus@yahoo.com’, ‘1050’, ‘2011-01-15’, 1),
(161, ‘techoweb@gmail.com’, ‘1050’, ‘2011-01-15’, 0),
(162, ‘techoweb@googlemail.com’, ‘1050’, ‘2011-01-15’, 0),
(163, ‘filelv2011@yahoo.com’, ‘1092’, ‘2011-05-30’, 1),
(164, ‘rodobone@yahoo.com’, ‘1111’, ‘2011-10-30’, 1);




I like Brian Crebs cos he is so stupid .
You sound butthurt.
Brian,
How often do you get sent copies of dumps of forum databases? Is this a common occurrence? And is it more due to grudges or would you say it is more done by people who believe they are on the ‘white’ side of the fence?
Thanks for your reply.
It’s hard to generalize. In many cases, I do not know the identity of the people sharing the information. Sometimes that is why I don’t immediately use it, because it’s not clear the time whether it is a) accurate and good information and b) can be relevant to anything that is going on.
Thank you for your reply. So how do you manage to authenticate this sort of data? I assume you do not ask other sources to collaborate on credibility by showing them what you’ve been given? Isn’t it a troubling possibility that any source would have the ability to insert “false data” among the “true data” perhaps out of spite or malice?
There are many ways to authenticate data. In this case, it was helpful to have the complaints and indictments with so much of the data about IP addresses, hostnames and other things named in this blog post match up after the fact.
In general (but not always), when someone tries to manufacture information for the purposes of feeding you bad info, there is an element of timeliness involved; in other words, time and experience has a way of revealing what is false. In any case, it’s always a good idea to set that kind of info aside.
Conversely, if you take information that you get from anonymous sources and hold onto it until other bits of info you obtain from other trusted sources happens to gel with it, that’s a bit different situation.
Brian you want to ask Bill Gate how did he made his first million . MIND you his not going to like that question . And post it here what he said .
Good old days NO Av .No Firewalls do what ever you want for as long as you want no one will stop you anyway .
Hi Brian – great article.
It is amazing how many of these guys still get caught through historic whois domain/IP registration data. Following your blog for a while now and it seems like 50% of them get busted because old whois data. You would think they would me smart enough not to use emails that are associated with their real names and address information.
Thanks, K. Yes, you would think that but not everyone who gets involved in cybercrime activity thinks things through in the first place, and often by the time they’re involved in all kinds of bad stuff, they’ve left history and other digital fingerprints all over the place.
Interesting that even the bad guys pick crappy passwords.
I agree, but my past reporting on the quality of passwords from users of a dodgy hacker forum suggests that many of these folks are no more careful about picking strong passwords than your average user.
http://krebsonsecurity.com/2011/06/antichat-hacker-forum-breach-reveals-weak-passwords/
@Kreb
Ucraineanu = romanian name, only one romanian can use such name.
Ucraineanu = ukraina guy, or ‘the guy from ukraina’.
While the nickname suggests it was created/picked by someone speaking romanian language, it could have been also someone from Republic Moldova or even from Ukraina, as parts of it were in the past (before 1940) inside Romania borders and there are still sizable communities there speaking romanian. It could also have been a (gross and ineffective) way to plant false leads.