Microsoft and Adobe today each released updates to fix critical security holes in their software. Microsoft’s patch batch tackles at least 33 vulnerabilities in Windows and other products, including a fix for a zero-day vulnerability in Internet Explorer 8 that attackers have been exploiting. Separately, Adobe pushed security updates for Flash Player, Adobe Reader, Acrobat and Adobe AIR.
 Microsoft’s Patch Tuesday bundle includes two separate updates for Internet Explorer; the first (MS13-037) is a cumulative update for Internet Explorer. The second is a fix (MS13-038) specifically for a critical bug in IE 8 that miscreants and malware have been using to break into Windows computers. Other, slightly less severe holes were fixed in Microsoft Publisher, Word, Visio and Windows Essentials.
Microsoft’s Patch Tuesday bundle includes two separate updates for Internet Explorer; the first (MS13-037) is a cumulative update for Internet Explorer. The second is a fix (MS13-038) specifically for a critical bug in IE 8 that miscreants and malware have been using to break into Windows computers. Other, slightly less severe holes were fixed in Microsoft Publisher, Word, Visio and Windows Essentials.
Last week, Microsoft released a stopgap “Fix-it” tool to help blunt the threat from the IE8 zero-day flaw. If you installed that interim fix, Microsoft recommends taking a moment to disable it before applying today’s patches.
<soapbox>On a side note..Dear Microsoft: Please stop asking people to install Silverlight every time they visit a Microsoft.com property. I realize that Silverlight is a Microsoft product, but it really is not needed to view information about security updates. In keeping with the principle of reducing the attack surface of an operating system, you should not be foisting additional software on visitors who are coming to you for information on how to fix bugs and vulnerabilities in Microsoft products that they already have installed. </soapbox>
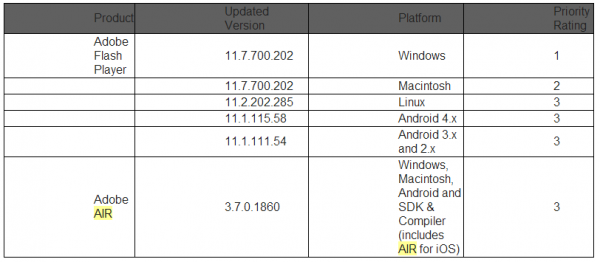
As it usually does on Microsoft’s Patch Tuesday, Adobe used the occasion to push its own security updates. A new version of Flash (v. 11.7.700.202 for Mac and Windows systems) fixes 13 vulnerabilities. IE 10 and Google Chrome automatically update themselves to fix Flash flaws. This link should tell you which version of Flash your browser has installed. If your version of Chrome is not yet updated to v. 11.7.700.202, you may need to just restart the browser.
The most recent versions of Flash are available from the Adobe download center, but beware potentially unwanted add-ons, like McAfee Security Scan). To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here. Windows users who browse the Web with anything other than Internet Explorer will need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.).
In addition, Adode AIR (required by some applications like Pandora Desktop, for example) was updated to v. 3.7.0.1860. Also, Adobe has released new versions of Adobe Reader and Acrobat that fix at least 27 security holes in these products. See this link for more detail on those patches. Adobe said it is not aware of any active exploits or attacks in the wild targeting any of the issues addressed in these updates.
As always, please drop a note in the comments section if you experience problems applying any of these updates.




Was just going to post something about the IE 8 (2847204) update, I noticed it on an old XP system I have.
Thanks, as always, for keeping another Patch Tuesday sane.
As someone who has to update 8 computers because the rest of the people have no idea how to do any of this I am very happy these updates from Windows and Adobe happened almost at the same time. Coincidence ?? Or not?
Mr. x, Adobe typically issues some of their advisories on the same day Microsoft does (2nd Tuesday of the month). Part of this is because Microsoft now issues the Adobe Flash Player updates for IE10, and those can be synchronized with the updates that Adobe issues for Flash Player on other platforms.
Adobe also issues advisories (irregularly) on other days, so you have to pay attention to Adobe more than just once a month.
I just wanted to say that’s the best graphic yet for a Windows updates article! Please consider making it your standard graphic for such articles!
Putting this out here. Only issue I noticed is Comodo picks up install_flashplayer11x32_mssd_aih.exe as a false positive (TrojWare.Win32.Trojan.Agent.Gen) according to VirusTotal.
Nothing to worry about.
The Silverlight requirement is for the videos on the page only.
Every time I go to krebsonsecurity.com I get a “This website wants to install the following add-on: ‘Adobe Flash Player’… Now let’s do a comparison of number and severity of vulnerabilities between Silverlight and Flash shall we?
The difference, of course, is that Flash is only required to view ads on this website, not the content.
During the dotcom era sites could make edicts about the format ads could use, but since then you have to take what the advertisers give you.
Microsoft, on the other hand, requests you install Silverlight for reasons that make little sense.
Amen in regards to the (unnecessary) Silverlight offer!
Thankfully, I only have to put up with it once a month.
Given the well-known vulnerabilities of Flash Player, if you also run the workalike Silverlight you can have twice the fun!
I’m guessing that without the proximity of Black Tuesday this cycle, the IE8 flaw would have merited an out-of-band release.
Today was also the release of Firefox version 21.0
I am so frustrated! When I went to disable the MS fix-it, I found no icon to disable the fix-it. If MS recommends “taking a moment to disable it before applying today’s patches.” Then Why does MS make it impossible to find it? (at least for a tech-handicapped person like me) This happened once before. Can anyone point me in the right direction to disable the fix-it I applied against my better judgment.
KB Goods, as Brian noted in his previous blog, just go back to the same page where you got the fix, but this time look under the “Disable” heading for the Fix-it image to click.
Here’s that previous blog entry; read the third (last) paragraph:
http://krebsonsecurity.com/2013/05/a-stopgap-fix-for-the-ie8-zero-day-flaw/
You don’t HAVE to uninstall the fix it. Brian’s wording can very easily be mis-read. Here’s the actual MS recommendation:
Customers who implemented the Microsoft Fix it solution, “CVE-2013-1347 MSHTML Shim Workaround,” in Microsoft Security Advisory 2847140, do not need to undo the Microsoft Fix it solution before applying this update.
However, since the workaround is no longer needed, customers may wish to undo the workaround after installing this update. See the vulnerability workarounds in this bulletin for more information on how to undo this workaround.
I wonder: How many person-years of productivity are siphoned off the U.S. economy every month by people spending time updating their software?
Hi James,
That’s true but if those computers were to become infected due to not being patched far more time would be wasted and far more damage would be caused.
Patching is the lesser of 2 evils. This is why we should all patch as soon as possible to reduce the likelihood of infection. Thank you.
“Patching is the lesser of 2 evils. This is why we should all patch as soon as possible…”
Better yet, not run software that is permanently vulnerable.
I wonder how many person-years of productivity are siphoned off from all the people who don’t update their software and follow basic security practices?
You don’t even want to know how many people I see on a day to day basis who don’t install security updates. I know a school that doesn’t let their students install updates because the kids are apparently too spastic to sit there and wait for the update to install, they’ll just turn the system off in the middle of an update. And if its a firmware update? Bye bye system.
“I know a school that doesn’t let their students install updates…”
Isn’t that what sysadmins are for?
I feel sorry for the systems administrator who’s responsible for updating the thousands of laptops in the hands of students, who may or may not show up to class on a particular day, even week.
Dealing with students is akin to herding cats. I’m thankful all the sytstems I’m responsible for are secured to desks, so I can walk around updating them every patch Tuesday with minimal fuss.
Agreed, totally.
Just a personal opinion: I think it’s kinda dumb that schools provide laptops to students. It’s unnecessary, expensive, and leads to problems you mention, plus many others, like the one where school officials spied (via webcam) on students while they were naked in their bedrooms at home.
I too pity administrators with lots of Windows boxes to maintain, but tools to distribute patches from central location are available from Microsoft for free, and from other vendors cheaply that address this issue.
The biggest problem is around the “handful of users” size, because it is work/effort/cost to setup and maintain such tools. If you have thousands of users it is easy to justify the effort of automatically installing fixes. Always happy to learn of good solutions for “patching” in the small business.
Trying to install security updates when a user is about to use software is a bad pattern. It steals time from people who are keen about security, it permits vulnerable software to lurk on systems, and it encourages people in a hurry to say “no thanks” (if they can). Patch on starting an application is almost certainly a worse problem than the problem it is trying to solve!
Basically patching anytime but when an application is started, the best is when a patch is available (and suitably tested), and ideally when it doesn’t disrupt the user much (lunchtime, shutdown), but there are always difficult cases. The proliferation of systems that patch themselves sensibly, and across all applications, as updates become available is a welcome trend, although Android Play Store seems to be running an experiment to see just how frequently applications can be updated before people buy an iPhone.
Thanks, Steve. I had been to that site yesterday. The link that took me to the Disable Fix-it was not on the site yesterday.
All I found was: We have removed the solution (and removed the enable, disable icons although it doesn’t say that) . No link to enable me to disable fix-it.
Today the link was there. All done.
I disabled the fix-it after I installed the update.
Problem ? if so, solution ?
Get rid of all Adobe products and do not use them…
I removed Flash Player sometime ago and have little issues using the Internet…
Get rid of all Adobe products, switch to linux, and security updates are easy to get 🙂
It should be noted that Silverlight is installed, without your informed consent, into Firefox…along with other Microsoft rubbish.
I believe this can be considered hacking in it’s truest meaning.
For maximum benefit of using Firefox for security, these MS garbage items must be counter-measured by disabling them, and using “NoScript”.
They will re-enabled without consent at update time.
These reasons, and all the other Microsoft mistakes and constant babysitting required is the reason I no longer use PC’s on the ‘Net.
Linux does not haves the merry-go-round fix and repair problems…I recommend this strategy for those fed up with the insanity.