An intrusion at online dating service Cupid Media earlier this year exposed more than 42 million consumer records, including names, email addresses, unencrypted passwords and birthdays, according to information obtained by KrebsOnSecurity.
The data stolen from Southport, Australia-based niche dating service Cupid Media was found on the same server where hackers had amassed tens of millions of records stolen from Adobe, PR Newswire and the National White Collar Crime Center (NW3C), among others.
The purloined database contains more than 42 million entries in the format shown in the redacted image below. I reached out to Cupid Media on Nov. 8. Six days later, I heard back from Andrew Bolton, the company’s managing director. Bolton said the information appears to be related to a breach that occurred in January 2013.
“In January we detected suspicious activity on our network and based upon the information that we had available at the time, we took what we believed to be appropriate actions to notify affected customers and reset passwords for a particular group of user accounts,” Bolton said. “We are currently in the process of double-checking that all affected accounts have had their passwords reset and have received an email notification.”
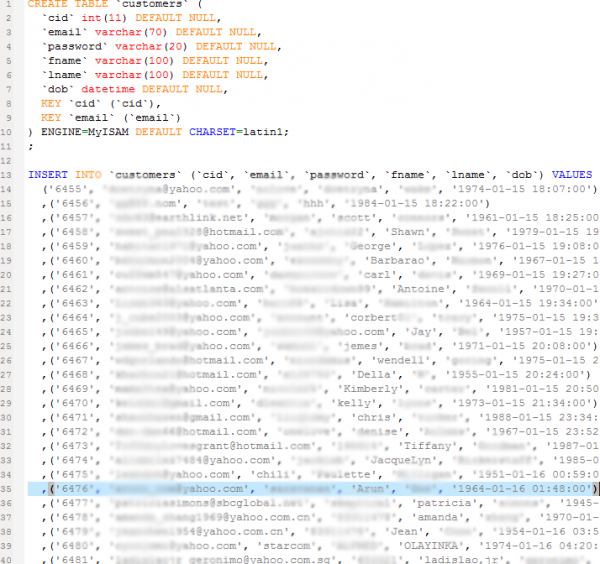
A redacted screen shot showing several of the stolen user accounts. Passwords were stored in plain text.
I couldn’t find any public record — in the media or elsewhere — about this January 2013 breach. When I told Bolton that all of the Cupid Media users I’d reached confirmed their plain text passwords as listed in the purloined directory, he suggested I might have “illegally accessed” some of the company’s member accounts. He also noted that “a large portion of the records located in the affected table related to old, inactive or deleted accounts.”
“The number of active members affected by this event is considerably less than the 42 million that you have previously quoted,” Bolton said.
The company’s Web site and Twitter feed state that Cupid Media has more than 30 million customers around the globe. Unfortunately, many companies have a habit of storing data on customers who are no longer active.
Alex Holden, chief information security officer at Hold Security LLC, said Bolton’s statement is reminiscent of the stance that software giant Adobe Systems Inc. took in the wake of its recently-disclosed breach. In that case, a database containing the email and password information on more than 150 million people was stolen and leaked online, but Adobe says it has so far only found it necessary to alert the 38 million active users in the leaked database.
“Adobe said they have 38 million users and they lost information on 150 million,” Holden said. “It comes to down to the definition of users versus individuals who entrusted their data to a service.”
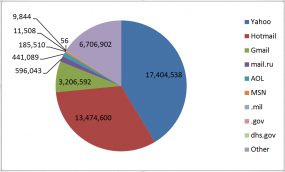
34 million Cupid users registered with a Yahoo, Hotmail or Gmail address. 56 Homeland Security Dept. employees were looking for love here as well.
The danger with such a large breach is that far too many people reuse the same passwords at multiple sites, meaning a compromise like this can give thieves instant access to tens of thousands of email inboxes and other sensitive sites tied to a user’s email address. Indeed, Facebook has been mining the leaked Adobe data for information about any of its own users who might have reused their Adobe password and inadvertently exposed their Facebook accounts to hijacking as a result of the breach.
Holden added that this database would be a gold mine for spammers, noting that Cupid’s customers are probably more primed than most to be responsive to the types of products typically advertised in spam (think male enhancement pills, dating services and diet pills).
Bolton adopted a softer tone in the second half of his email, indicating that the company may not have understood the full scope of the intrusion.
“Since you have now provided additional information we now have a clearer picture of what transpired back in January,” Bolton wrote. “We are currently in the process of double-checking that all affected accounts have had their passwords reset and have received an email notification.”
Bolton continued:
Subsequently to the events of January we hired external consultants and implemented a range of security improvements which include hashing and salting of our passwords. We have also implemented the need for consumers to use stronger passwords and made various other improvements.
We would like to thank you for bringing this issue to our attention and I can confirm that we are committed to investigate this matter further and make any additional improvements still required. Protecting our customer’s privacy and data is important to us and we will continue to make additional investments in improved security for our members. We sincerely apologize for the inconvenience this has caused our members.
It is entirely likely that the records I have seen are from the January breach, and that the company no longer stores its users’ information and passwords in plain text. At least Cupid Media doesn’t send your password in plain text when you request a password reset, like far too many other companies do. It’s also remarkable that a company with this many users would not have seen this coming. Back in Feb. 2011, I broke a story that received considerable media attention; it was about a hack that exposed some 30 million customer records at Plenty Of Fish (pof.com), an online dating service that also admitted to storing its users’ passwords in plaintext.
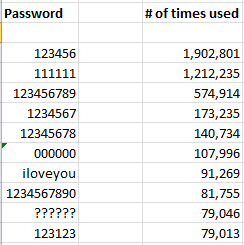
In any case, since I didn’t have to crack any of the passwords, I thought it might be useful to have a look at the top passwords used by Cupid Media customers. It seems that many Cupid users did not place much value in their accounts when picking passwords, because a huge percentage of them chose downright awful passwords. By my count, more than 10 percent of Cupid’s users chose one of these 10 passwords:
The top 10 non-numeric passwords are probably typical for a dating site, but still horrible nonetheless:



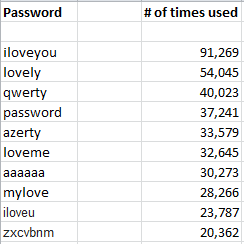

I find it highly amusing that 30,273 users picked aaaaaa as a password! 😉
That is probably what I would also say if I discovered this breach and were a former customer! (add exclamation point) 😀
I just spit out my coffee reading that! 🙂
Well sometimes, you need just register, you dont care about password, you dont put a real info. And if you care to comeback , you choose a simplest one.
I wonder if those people were actually “matched” to each other…
Important sites (anything involving money, significant effort, or the online reputation of my username) get a unique, strong password generated by diceware with casino dice and stored in KeePass.
Less important things I plan to use more than once get a password generated by KeePass.
Pretty much everything for a one-time download gets something easy to memorize that fits the common password filters: “a=7.297e-3”. The fine-structure constant is something I already know, lets me use letters and numbers, and can be adapted depending on the password rules of the site. No special characters? “alpha72973525698” probably works, or the same thing cut off at the length limit. A download should not require an account, it will get a mailinator e-mail and a password anyone can guess.
It might be interesting to run a list of fundamental constants through to see how many people use them as (crappy) passwords. Probably a few using Pi, e, and c.
i usually use a phrase, just some random words strung together lol
%th15%15%myp@ssc0d3%
lol
just a string of random words works best
%th15%15%my%p@ssc0d3%
There is noting random about your example.
You get WAY WAY WAY more entropy from a passphrase than a password. I’m sure you know the famous XKCD strip with “horsebatterystaple” and the entropy there, but if you throw in some punctuation and a few proper nouns in it reaches levels of entropy that are effectively unbreakable with current technology.
In numbers: if we take horsebatterystaple as an example, how hard is it to break it? Well, let’s say we took Word Frequency’s top 5 000 English word list (http://www.wordfrequency.info/free.asp) which is free. Logic dictates we should add punctuation, state/city/zip code info, common first and last names, and so on. But let’s say we’re feeling somewhat illogical and we just want the 5 000 words. It’s not a lot of words, you know, and we could definitely get correcthorsebatterystaple out of it. To do so we only need to go 4 words deep. So 5 000 words combined all around is a mere 625 000 000 000 000 combinations.
“But modern password tools and modern processors yada yada!” you exclaim. Well, based on current JtR benchmarks, if we had a server with 16x Intel Xeon X7550 processors (with 8 physical cores in each processor) and we were breaking some simple MD5 crypt() hashes, we could do an incredible 1 953 000c/s. So we could get through those computations (and find correcthorsebatterystaple) in only 320 020 481 seconds, or about 10.14 years.”
With 200 000 words it would take considerably longer. GPUs do little to improve this, except to lower the total cost attached to breaking a password.
If you had to make your password something like “I love lamp! It’s my second favourite dish.” that’s a total of 17 parts (each whitespace or punctuation mark is treated as a part, since an attacker cannot possibly predict where it would go in the passphrase. Again, using a mere 5 000 words (assuming we managed to jam some punctuation/spaces in there) we’d need to test 7.62e+62 combinations. Using the aforementioned benchmark, that’s 3.906e+56 seconds, or 1.238e+49 years.
Forgot to link to the JtR benchmarks: http://openwall.info/wiki/john/benchmarks
A potential problem to wide spread adoption, is people aren’t selecting “randomly chosen words” for a passphrase. They select easy to remember quotes, etc. Of which there is a profoundly large corpus.
http://arstechnica.com/security/2013/08/thereisnofatebutwhatwemake-turbo-charged-cracking-comes-to-long-passwords/
Yeah, the password/phrase is unbreakable, but the hash of it isn’t.
1 day of jail for every 1 million accounts revealed would solve this ongoing problem once and for all.
And I mean fo the CEO of the company breached, not the breacher.
was just about to finish your sentence then you replied midway through lol
I agree Jail Time for the idiots that allowed plain text passwords to be stored
Can’t put the blame solely on the CEO for that. It’s all the way down the chain: the hired help who didn’t know what they were doing, the manager that thought it would be a good idea to hire an idiot to implement their customer database, the people who didn’t fire the manager for taking shortcuts before this happened, etc.
But to be fair, assign fines/jail terms based on the total compensation package of everyone from the board down.
However, if the specification required plain text passwords, then the person doing the work should be absolved. The tech lead should be absolved if he caught the error but was overruled by his boss (and so forth).
“However, if the specification required plain text passwords, then the person doing the work should be absolved. The tech lead should be absolved if he caught the error but was overruled by his boss (and so forth).” I respectively disagree. As a rebellious child of the ’60s, I have learned that morality is absolute and stupidity can be catastrophic. In this case the tech lead should have written a succinct description of the situation and the consequences of proceeding as ordered. The writing should be damn good. The facts or opinions should be totally supported by industry best practices data. Adding one or two horror stories about those who failed to heed similar advice should be added to spice up the text. Then send the missive to the CIO and the president of the company. If the top management of the company is good you shall win because your cause is just. If you loose, then go to a competently managed company. Keep in mind what happened to RMS Titanic and to MS Costa Concordia. Those ships were managed by dummies.
42M passwords or records?
better to maintain distance with that sites!
I think most people just make a crappy password because they’re just looking around on the page and it makes you register.
Agreed. There are far too many websites that make you register for no good reason.
Well the reason is that they want to monetize their website, and they need better data on the people visiting the site.
hopefully facebook is mining this list of email and passwords and doing the same as they did previously
Haggis – I work on the security team at Facebook and can confirm that we are checking this list of credentials for matches and will enroll all affected users into a remediation flow to change their password on Facebook.
Thats Awesome Chad! keep up the good work 🙂
You do a great job with those, 123456 accounts while the NSA… hahhaha CHAD hahaha
Keep up the good work Chad, and the team.
Hi Chad,
Protect the graph!
I just wish I had the ressources to do the same for our customers.
Best wishes to Marc and the rest of the team.
Torge
It will be interesting to see if their membership numbers decrease after this incident. I can hardly wait for Neil Clark Warren to run an eHarmony commercial talking about the science behind their password rules and encryption technology…
HA ! A True security by obscurity website. GREAT.
I can understand the public relations people getting a little defensive, but its hanging out there, quite obvious. Its better left unsaid rather than have to back track and try to repair two routes of poor comany judgement.
They should have named the breach, or the investigation that may follow, appropriately, like part failure and part STD combined. Since everyone there apparently got slapped silly.
That could be a heck of a blackmail list as well. Hummm how many spouses (and potentially other spouse) are in that love shack , errrrrrrr Love hack.
Passwords were stored in plain text.
Ha Ha HA what a bunch of idiots . that will teach them .
Nice going , hashing and salting the passwords after the breach occurred then stating “Protecting our customer’s privacy and data is important to us”
Internet users should not be using that website. Period !
Who’s to say such a company has now implemented hashing and salting of passwords? Trust them (yeah right).
If you’d like to run the dump through Pipal then I’ll happily do it for you or come up with modules to create any custom stats you want.
Really good article.
Article is good but can you send me a link to that server ? I am intrested in security defence.
Hey, I think you need to blur the passwords and emails more, because I can still read them…
really? read me one email and password pair. just one.
You can read chili on line 6475 and you might be able to derive the address underneath that one but that is all I can see.
Brian:
I haven’t strained to read the obfuscated text in the graphic, but it might be possible for a computer to do so.
I don’t know whether this guy was ever caught, but I still remember being amazed at his hubris. (Or is it chutzpah? Or both?)
http://www.nbcnews.com/id/21190969/
On the other hand, I’m sure if someone wanted the original database from which you copied that, it must be easy enough to find, if you know where to look.
— Tim
If dating site users have any sense they’re using email addresses that are completely separate from any that they use for any other purpose and are giving false info on all the profile data the site asks for. In that case, I don’t see a simple password as too much of a risk.
“dating site users have any sense”
Well, there’s one bad assumption.
I don’t understand the entropy argument. If the password is plaintext, wtf?
Why haven’t haxxors learned to distribute and encrypt their warez?
Surely giving false information to a dating site is a bit against the spirit of doing it.
As for fake email addresses, do you think people would really go to the trouble? Most will be using their work addresses so they can keep track of the mails during the day.
Cold Fusion & lazy IT admins = jackpot. Again and again..
I’d like to clarify some of the incorrect assertions made by (or attributed to) Alex Holden in the story—specifically the reference to “a database containing the email and password information on more than 150 million people was stolen and leaked online, but Adobe says it has so far only found it necessary to alert the 38 million active users in the leaked database.” This information is incorrect and not based on statements made by Adobe.
Adobe has reset passwords for all users whose current credentials (Adobe ID account with valid, encrypted password) were in the database that was taken by the attackers. We are sending email notification to all users whose credentials were in the database that was taken.
In terms of the numbers of records, our investigation has confirmed that the attackers obtained access to Adobe IDs and what were at the time current, encrypted passwords for fewer than 38 million active users. The attackers also obtained access to many invalid Adobe IDs, inactive Adobe IDs, Adobe IDs with encrypted passwords that are no longer current, and test account data. We prioritized sending notice to active users first, and we are now in the process of notifying inactive users.
For the latest and correct information on the incident, please refer to our Customer Care page at http://www.adobe.com/go/customer_alert.
-Heather Edell, Sr. Manager, Adobe Corporate Communications
Heather – really? or have you been drinking the Adobe Cool Aid?
The facts, as opposed to the corporate speak you have written;
– I must be one of the ‘inactive accounts’ you speak of. I just received a notification from Evernote that my Evernote email address was compromised by Adobe (kudos to Evernote – apparently a responsible company, unlike Adobe, in my opinion, obviously)
– I confirmed this with reputable site that allow searching of the list.
– I have not received any emails or correspondence from Adobe about this security lapse by Adobe.
– I have been attempting to obtain the correct email address via the online chat… it’s been over an hour as ‘1 person ahead of you in the line’ – just now i have been engaged in a chat and complaint lodged – why so long? – This has been over 2 weeks since Adobe knew – you couldn’t staff up in time to handle the problem?
– A much as Adobe advises customers to use different email addresses and passwords, this does not absolve Adobe in anyway from maintaining adequate security protocols – no matter the cost – this is simply a cost of doing business.
– I don’t take this lightly. My time is as valuable as yours. I have a company to run as well – and I, as I expect many of your customers fell as well, am highly p’ed off with Adobe right now. Adobe should know better, and Adobe should pay!
Who needs passwords ? There are backdoors to enter accounts on such sites anyway.
That is a very big statement, would you care to elaborate.
Not here
Feel free to mail me info, my address is on my site. Sure Brian would like to know as well.
Without some kind of proof it is just a hollow claim.
There is no way this leak happened. Look at the screen shot. The dob field shows values that look like dates _and_times_. No dating site would ask you for the date and the time you were born. Looks like someone faked this story and put in random data and took a screen shot of it.
Not DOB fields, Peter, they’re account creation times.
No, it clearly says “DOB”, and the dates couldn’t possibly be the registration dates since they range all the way back to the 1950s. The times could be some artifact of something else, but those couldn’t be registration dates.
The date part is correct, the time listed in the latter part of the DoB field has been used to store account creation time. Scan down through the them, they’re in time order.
Second thought: ToB for Astrological classification?
Alexa is like a seismograph station for Internet sites.
If you check eHarmony, Match and PlentyOfFish you will see they are high activity level sites.
CupidMedia owns and operates 35+ International online dating sites, no one of them have high activity levels according to Alexa and they are all run in English language, they have low or little traffic rank, they are like phantoms.
If you register and begin to use any of those sites, perhaps you will discover the main objective is to attract men and send them to other adult content sites ( check the link www dot blackcupid dot com and see where it redirects! )
To be more clear, those 35+ online dating sites are only “special purposes vehicles” to redirect men to adult content sites, and most probably 90% of profiles in their databases, are only fake profiles of women designed exclusively to redirect men to adult content sites. No more than that. Quite similar to “AshleyMadison case, sued by ex-worker who claims she wrote too many fake female profiles.”
If you can investigate further please?
Regards, Fernando Ardenghi, Buenos Aires, Argentina
ardenghifer AT gmail DOT com
“By my count, more than 10 percent of Cupid’s users chose one of these 10 passwords:
123456
111111
123456789
1234567
12345678
000000
iloveyou
1234567890
??????
123123
”
and
“The top 10 non-numeric passwords are probably typical for a dating site, but still horrible nonetheless:
iloveyou
lovely
qwerty
password
azerty
loveme
aaaaaa
mylove
iloveu
zxcbnmn
”
Which % of them are related to females profiles?
Because that information could be useful to check if some female profiles were deliberately created to fill databases in a same manner as “A dating website for married people who want to cheat on their spouses is being sued by a former employee who says she damaged her wrists typing up hundreds of fake profiles of sexy women.”
http://www.thestar.com/news/canada/2013/11/10/ashley_madison_infidelity_site_sued_by_woman_hired_to_write_up_fake_female_profiles.html
What’s the link between the Adobe hack and stealing of Cold Fusion source code and Cupid Media running on Cold Fusion?
The initial Adobe hack seems to have triggered this and other attacks.
Fernando:
You’re using flawed data. First you’re relying on Alexa which once you get past the top echelon of sites is flaky at best. Secondly you’re comparing one site to a network of 35 sites and from a cursory glance at their sites they are run in multiple languages – not just English.
“did not place much value in their accounts” This is something that rarely gets mentioned. Often the attitude seems to be more along the lines of, “Stupid users, doh!”
I have many accounts with weak passwords. They all point at my junk account and I don’t care about any of them or the junk email account.
the clever ones used 123456 as their password.
the stupid ones used their secret and very cryptic password, they use everywhere else 😀
Once again we have an excellent cautionary example of the reputational risk for the company having been greatly amplified by them keeping passwords for closed accounts. It could be argued that the demographic information in those old accounts may have had some value to the company. But the passwords for those accounts was probably worthless to the company.
The problem seems obvious. The more old passwords you store, hashed, encrypted, or plaintext, the bigger the number that appears in the headline when they all get stolen and leaked. From a brand reputation standpoint, nobody cares or remembers the public statements from the CEO or PR department explaining that the number of customers affected by the breach is far less than the total number of accounts and passwords found in the raw data dump.
Have you received my email related to this article Brian?
As of 3:30 today, all Cupid Media sites are offline. Oops.
Obligatory joke regarding users on a dating site actually getting successfully f–ked while using it!
There isn’t any method like this specific leak took place. Consider the screen shot. Your dob area indicates valuations which seem like appointments andtimes. Zero dating website would likely ask people with the time along with the occasion you had been delivered. Appears to be someone faked this specific report as well as put in haphazard info as well as needed a new screen shot of it.