An underground service that is selling credit and debit card accounts stolen in a recent data breach at retail giant Target has stocked its virtual shelves with a new product: Hundreds of thousands of cards issued by non-U.S. banks that were used at Target across the United States during the retailer’s 19-day data breach. It’s not clear how quickly the non-U.S. cards are selling, but they seem to be fetching a much higher price than those issued by U.S. banks.
On Dec. 20, this blog published a story about the “card shop” rescator[dot]la. That piece explained how two different banks — a small, community bank and a large, top-10 bank — had bought back their customers’ stolen cards from the fraud service and discovered that all of the purchased cards had been used at Target during the breach timeframe. The shop was selling data stolen from the magnetic stripe of each card, which thieves can re-encode onto new, counterfeit cards and use to go shopping in bricks-and-mortar stores for items than can easily be fenced or resold.
As I wrote in that story, a key feature of this particular shop is that each card is assigned to a particular “base.” This term is underground slang that refers to an arbitrary code word chosen to describe all of the cards stolen from a specific merchant. In this case, my source at the big bank had said all of the cards his team purchased from this card shop that matched Target’s N0v. 27 – Dec. 15 breach window bore the base name Tortuga, which is Spanish for “tortoise” or “turtle” (also an island in the Caribbean long associated with pirates). The small bank similarly found that all of the cards it purchased from the card shop also bore the Tortuga base name, and all had been used at Target.
On Friday, the proprietor of this card shop announced the availability of a new base — “Barbarossa” — which consists of more than 330,000 debit and credit cards issued by banks in Europe, Asia, Latin America and Canada [side note: one Russian expert I spoke with said Barbarossa was probably a reference to Operation Barbarossa, the code name for Germany’s invasion of the Soviet Union during World War II].
According to one large bank in the U.S. that purchased a sampling of cards across several countries — all of the cards in the Barbarossa base also were used at Target during the breach timeframe.
As with cards sold under the Tortuga base, debit and credit cards for sale as part of the Barbarossa base list the country of origin for the issuing bank, and then directly underneath include the state, city and ZIP code of the Target store from which the card numbers were stolen.
When I first became aware that this card shop was selling only cards stolen from Target stores, I noticed a discussion on a related crime forum wherein customers of this shop seemed very enthusiastic about this ZIP code feature. I couldn’t figure out what the big deal was: I’d assumed the state, city and ZIP described the bank that issued the card.
Later, I learned from a fraud expert that this feature is included because it allows customers of the shop to buy cards issued to cardholders that live nearby. This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder’s immediate geographic region.
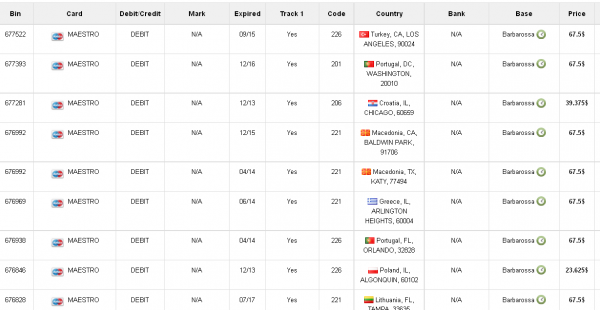
Non-U.S. cards used at Target generally fetch higher prices than U.S. cards, between $67 and $100 apiece.
The cards for sale in the Barbarossa base vary widely in price from $23.62 per card to as high as $135 per card. The prices seem to be influenced by a number of factors, including the issuing bank, the type of card (debit or credit), how soon the card expires, and whether the card bears a special notation that often indicates a higher credit limit, such as a Platinum card.
The prices also appear to be influenced partly by how rare it is to find cards for a specific bank available on the black market. The highest-priced cards I found for sale were issued by banks in Singapore, South Korea and the United Arab Emirates.




The spammers are out on Christmas day! I received an Email from a Netherlands URL that I’m sure was bogus (said it was from Costco – probably trying to get personal info) – read my blog post.
Merry Christmas everyone.
That’s the same botnet that to claimed to send you a WhatsApp message. They changed to “Costco emails” with Christmas theming a couple weeks ago. And a few days ago they also started impersonating Best Buy.
Those links lead to compromised web servers (it was random that you got one at a .nl domain), serving a .zip which contains a .exe No special tricks there.
The email senders are compromised websites, too.
I have been wathing these guys for months now, feel free to mail me if you want more info about them (or you want to complete something, specially if you have the server code they use).
(This would have been more appropiate on your blog entry, but your comment form doesn’t seem to work⁈)
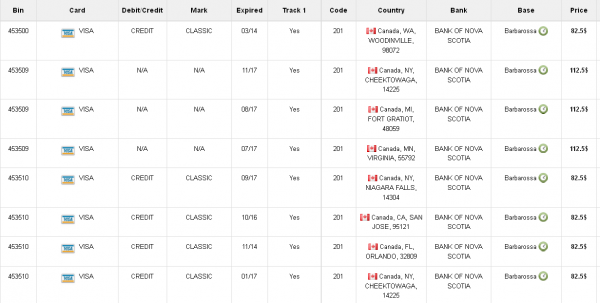
Thanks for the great work and insights…in Canada, day-trip or holiday shopping in the US is very popular – the prices and selection are always better, and the Canadian Gov’t allows a pretty high amount that can be declared without paying extra taxes. Something like 90% of the Canadian population is within an hour or two of the US border, and there are plenty of outlet malls that make it easy to shop there. The store locations included in the data makes sense…this would help thieves ‘blend-in’ with legitimate activity. Another good point in your piece was reluctance to reissue at this time…banks make a lot of money on Credit Card interchange fees…and we have Boxing Week sales starting tomorrow.
Thanks Again.
Tortuga and barbossa – that will be a reference to Captain Barbossa, the bad guy in the pirates of the carrabean films, and the island the pirates call home
Some banks are re-issuing cards, which makes me happy, and hopefully I can get new PINS etc. The one thing that aggravates me is that the corporations get notified and they do not care: unless it has done some damage, or a application is at issue, then they do nothing, and they demand that basic researchers like me who rely on the full time researchers with proper tools like Brian and others, just conform to useless write up scripts which tells them nothing. Some corporations I assume do some pre-emptive work, but It is aggravating that the info I pass on is ignored as being “too much” or inapplicable.
I find the entire Target subject to be mostly a lot of hype. I get a credit card number “borrowed” about once a year. There is never any cost to me, other than having the card reissued. If you use a credit card, it is going to get “borrowed”, just a fact of life. The card issuers push it all back to the merchant, who has insurance to cover this. Nobody wants to prosecute the people doing the crime, so it continues.
The hype about the Target breach is that somehow this is different or that it constitutes “identity theft”. People are worried that because of this they are going to have their credit ruined and will be stuck with mysterious loans and purchases. The truth is that no card holder will lose anything from this, ever. However, scammy companies like LifeLock will use this in their advertising and make out very well from it.
LifeLock will use this in their advertising and make out very well from it.
While true, however the person who used his own SSN in ads as proof that it is safe was hacked into. Nothing is safe as it is more like a game of chess between both sides (hacker and card companies).
The US is the only country using the magnetic strip to store information whereas EMV has been in use for 10 years in Europe. The only recourse the issuer has is reissue the card with new PIN. Many card issuers are ‘voluntarily” putting EMV on cards with the goal of all by 2015. To me, it should have been done years ago but the argument is the merchant’s cost of upgrading to accept them.
So you think this is no big deal? Please read http://hal2020.com/2014/01/03/data-breaches-are-a-big-deal/ and http://hal2020.com/2014/01/05/more-on-credit-card-data-breaches/
I don’t think that the zip code corrispond to zip code where was stolen it. Simply determine the location of CC. It’s fool publish this kind of information..
Nice work!
Fabio: Based on the screenshots featuring Canadian cards – none of which show Canadian postal codes – the ZIP data is indeed from the compromised US store locations as opposed to registered locations of the card holders.