Ooh, you might not ever get rich
But let me tell ya, it’s better than diggin’ a ditch
“Car Wash” by Rose Royce
An investigation into a string of credit card breaches at dozens of car wash locations across the United States illustrates the challenges facing local law enforcement as they seek to connect the dots between cybercrime and local gang activity that increasingly cross multiple domestic and international borders.
 Earlier this month, police in Everett, Massachusetts arrested a local man named Jean Pierre for possessing nine stolen credit card accounts. The cards themselves weren’t stolen: They were gift cards that had been re-encoded with data from cards that were stolen from a variety of data breaches at merchants, including a Splash Car Wash in Connecticut.
Earlier this month, police in Everett, Massachusetts arrested a local man named Jean Pierre for possessing nine stolen credit card accounts. The cards themselves weren’t stolen: They were gift cards that had been re-encoded with data from cards that were stolen from a variety of data breaches at merchants, including a Splash Car Wash in Connecticut.
How authorities in Massachusetts connected Pierre to a cybercrime at a Connecticut car wash is a mix of odd luck and old-fashioned police work. In May, the Everett police department received a complaint from a sheriff’s department in South Carolina about a resident who’d had his credit card account used repeatedly for fraudulent transactions at a Family Dollar store in Everett.
Everett PD Detective Michael Lavey obtained security camera footage from the local Dollar Store in question. When Lavey asked the store clerk if he knew the individuals pictured at the date and time of the fraudulent transactions, the clerk said the suspects had been coming in for months — several times each week — always purchasing gift cards.
“The clerk told me they would come into the store in pairs, using multiple credit cards until one of them was finally approved, at which point they’d buy $500 each in prepaid gift cards,” Lavey said. “We have two Family Dollar stores in Everett and a bunch in the surrounding area, and these guys would come in three to four times a week at each location, laundering money from stolen cards.”
Not long after Lavey posted snapshots from the video footage on a state-wide police network, he heard from an officer in Boston who said a suspect resembling one of the men in the photos was recently questioned at a city hospital after being stabbed in the legs and buttocks in an unrelated robbery. The assailant in that attack was arrested, but his victim — Jean Pierre — refused to answer questions about the incident. The police seized Jean Pierre’s pants as evidence in the assault case, and discovered numerous prepaid cards in the pockets of the trousers.
Lavey said he subpoenaed the credit card records, and working with investigators at American Express and Citibank was able to determine that at least one of the cards had been stolen from the Splash Car Wash in Connecticut. In effect, thieves were buying stolen cards to finance the purchase of gift cards, some of which would later serve as hosts for new stolen card data once their balance was exhausted. The cops call it money laundering, but in this case it might as well be called card washing.
WILL THAT BE A SUPER OR DELUXE WASH?
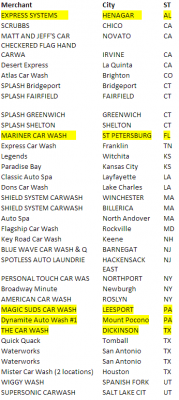
Soon enough, Lavey had linked up with Michael Chaves, a detective with the police department in Monroe, Conn. who’d been investigating card breaches at 14 separate car washes in his state, including the Splash case. Working with the Connecticut Financial Crimes Task Force, a broad law enforcement group that includes the U.S. Secret Service and state police, they determined that the local company was but one of at least 40 car washes across the country that had been hacked and relieved of countless customer credit and debit cards since at least February 2014.
Chaves said he interviewed several of the car wash owners, and discovered that they were all using the same point-of-sale systems developed by Randolph, N.J.-based Micrologic Associates. Chaves said the store owners told him the devices had remote access via Symantec’s pcAnywhere enabled, access that was granted to anyone who knew the same set of default credentials.
“The pcAnywhere credentials were created by Micrologic, but unchanged for years,” Chaves said.
That was the same conclusion independently reached by Detective Steven LaMears with the police department in Keene, N.H. Earlier this month, a police captain at the Keene Police Dept. saw fraudulent charges show up on his credit card shortly after using it at the town’s Key Road Car Wash, an establishment which used Micrologic’s point-of-sale system.
LaMears also heard from a company in New York which reported that two its executives each had their cards compromised multiple times after visiting the Key Road Car Wash in Keene.
“We confronted them, and working with the U.S. Secret Service got them back up and running,” LaMears said of the local compromised car wash. “The Secret Service told us they were running an old version of Micrologic that had the same, one login for everything, and were using an old version of Windows XP.”
MICROLOGIC POS: CAR(D) WASHING SOFTWARE?
Micrologic President and CEO Miguel Gonzalez said that only about one-third of the 40 or so car washes on the Secret Service’s list of compromised stores (see above left) were running Micrologic point-of-sale software; the rest, he said, were using products made by other software vendors.
Gonzalez said Micrologic recently began urging all of its customers to transition away from pcAnywhere and adopt multi-factor authentication that involves the use of a one-time code that is sent via text message to the administrator’s mobile device.
Asked about the claim that crooks may have been abusing default credentials in Micrologic’s software to steal card data from car washes running its product, Gonzalez said the breached companies were running older, outdated versions of pcAnywhere . He said attackers appear to have targeted vulnerabilities in the remote access software itself — not merely abusing some set of default credentials.
“What the investigators we’ve worked with so far have been able to gather is that [the thieves] were exploiting not the pcAnywhere credentials, but a flaw in old versions of pcAnywhere,” Gonzalez said.
In January 2012, Symantec acknowledged that hackers had stolen the source code to the popular remote access software, and it urged users to either update the software — which included fixes for several critical bugs — or remove the program altogether.
Whether the crooks are exploiting software vulnerabilities or weak/default credentials in this case, security experts routinely advise companies to avoid using remote administration tools on point-of-sale devices — or else to severely lock them down with strong passwords and other restrictions. One stubbornly static finding in data-breach reports published annually by Verizon, Trustwave and other companies that get hired to investigate breaches involving card data is that far too many point-of-sale breaches start when the thieves abuse some kind of remote access tool installed on the point-of-sale device itself. Typically, this involves the attackers scanning the Internet for remote administration software, and then using automated tools that can break into any systems that are protected with weak passwords.
THE NEW THUG LIFE
Point-of-sale compromises at restaurants, retailers, car washes and elsewhere are frequently attributed to hackers in Romania, Russia, Ukraine and other parts of Eastern Europe. But according to Detective Lavey, the buyers of these stolen goods increasingly are street gang members here in the United States. Lavey said Jean Pierre — the stabbing victim who was found in possession of nine stolen credit cards — is a member of the Bloods an African American street gang.

Surveillance camera footage from Dollar Stores where police say these individuals used stolen credit cards. Source: Monroe, Ct. Police. Jeanne Paul is pictured top right.
“All these kids are Blood gang members, tattooed up or self-admitted,” Lavey said. “And they’re starting to work smarter, not harder. Individually, this card fraud doesn’t meet the threshold where the federal government is going to say ‘Hey, let’s grab these guys.’ Locally, they’re doing it across broad jurisdictions and jumping from state to state and coming away with hundreds of thousands of dollars.”
Lavey said he recently worked a case where a number of kids in their late teens were using stolen credit cards to go on shopping sprees at multiple Target stores along the east coast.
“We just wrapped up a case where these kids were coming up from New York, and they were hitting every Target store in the area for $6,500 a whack,” Lavey said. “In one weekday, they did this hitting all Target stores up and down the eastern seaboard. They now have charges pending in New York, New Jersey, Virginia and Pennsylvania.”
Given how easy it is to buy stolen cards, encode them onto gift cards and then use those cards to buy goods in big-box stores that can be easily resold for cash, Lavey said he wonders why old-fashioned bank robberies are still a problem.
“Honestly, the fact that we still have bank robberies is sort of perplexing,” he said. “Rob a bank and you’re lucky if you get away with $600. But you can rob a credit card company and all the banks are afraid to have their name associated with a case like this, and they quickly reimburse the victims. And most of the retailers are so afraid of having their name in the press associated with credit card fraud and data breaches that make the job doubly hard for us.”





I don’t understand why is swiping still prevalent method when paying by card. Here in Europe we use chips on cards accompanied by PIN entry. I don’t remember when I swiped my card last time. If USA switched to chip cards, these problems would be gone. Of course there would emerge other problems, but swiping is really PITA from security point of view.
In short it’s because individual European countries are smaller markets with way fewer PoS locations. Fed taxi cabs, fewer ATMs, fewer restaurants, fewer bars / pubs, fewer grocery stores, fewer contractors. Fewer people, and fewer credit cards per person. Fewer banks (tens of thousands? – European countries can easily have dew than 10!) and fewer credit unions (I’m not even sure how many European countries even have credit unions).
European countries are also physically smaller. And while most Europeans like most Americans don’t travel outside their country and tolerate / expect some level of difficulty when doing so, these people expect things to work in their entire country, not just 100km (or 100 miles).
It’s also possible that the ownership model for payment processing terminals is different. In fact US, I’m pretty sure that historically merchants bought the equipment. If you as a merchant have paid for equipment (sunk cost) and it “works”, why would you spend any money to replace it? It’s possible that in some European countries that equipment is leased / owned by the bank / payment processor. (In Canada, it looks like this is the case.) If you the merchant don’t own it, and are given a replacement unit to use, you’ll use it.
Let’s meet our Chickens and Eggs – this will be “which came first”…
1. The merchants have no reason for pay to upgrade their terminals – extra confusing buttons and no cards to use them
2. The banks (and other issuers including department stores and state governments) have no reason to issue cards with a feature that won’t be used anywhere. Worse, it requires their cushion to pick and remember a number. If you were given a card with a number and then didn’t have a single occasion to use the number for a year or more, do you think you would remember the number? When you forget the number, the bank loses money verifying you and resetting the PIN.
In Europe with few issuers, and the most likely issuer being a brick and mortar bank, replacing the PIN isn’t a big deal. That isn’t the case in the US.
In some cases there’s also technology leap frogging at work. E.g. Some European countries jumped from bank “pass books” straight to credit cards – skipping checks. I don’t think any skipped magnetic credit cards, but it’s possible that the introduction of debit cards was PIN only and thus drove the adoption of PIN readers. Whereas Debit cards in the US have been around for a while.
Your reply makes no sense at all. A chipped credit card will work anywhere in the world and the economy of numbers would be a reason for introducing chipped cards to USA instead of against.
As for forgetting the PIN surly Americans are not that dumb and the PIN can be one of your choosing.
Chipped credit are much more secure and would prevent the theft, home invasions and muggings that people experience because others want to steal their credit card.
The banks would also save a lot of money on compensation for fraudulent card use and reissuing stolen cards.
There is no reason not to have chipped card, they do offer a much greater level of security.
Cow-chip-N-pen, has been cracked -why make bank customers foot such a huge cost for so little benefit. There is better – cheaper tech out there, like MagnePrint, and Passwindow, and the financial risk of an expensive system going bad nation wide is lower.
If you don’t know what you’re talking about, don’t talk.
Because Chip and Pin is late coming to the US. http://www.eweek.com/security/u.s.-consumers-ready-to-adopt-chip-pin-credit-cards-survey-finds.html
With regards to Gift Cards – If card associations would classify gift cards as a seperate MCC instead of lumping it with the MCC code of the business purchased (, 5310, 5411, ECT..) Gift card fraud would be easier to stop from a processor perspective.
Up-to-date information– mcafee antivirus plus 2014 (win) for free Will Have A Vital role In Almost Any Administration