Ooh, you might not ever get rich
But let me tell ya, it’s better than diggin’ a ditch
“Car Wash” by Rose Royce
An investigation into a string of credit card breaches at dozens of car wash locations across the United States illustrates the challenges facing local law enforcement as they seek to connect the dots between cybercrime and local gang activity that increasingly cross multiple domestic and international borders.
 Earlier this month, police in Everett, Massachusetts arrested a local man named Jean Pierre for possessing nine stolen credit card accounts. The cards themselves weren’t stolen: They were gift cards that had been re-encoded with data from cards that were stolen from a variety of data breaches at merchants, including a Splash Car Wash in Connecticut.
Earlier this month, police in Everett, Massachusetts arrested a local man named Jean Pierre for possessing nine stolen credit card accounts. The cards themselves weren’t stolen: They were gift cards that had been re-encoded with data from cards that were stolen from a variety of data breaches at merchants, including a Splash Car Wash in Connecticut.
How authorities in Massachusetts connected Pierre to a cybercrime at a Connecticut car wash is a mix of odd luck and old-fashioned police work. In May, the Everett police department received a complaint from a sheriff’s department in South Carolina about a resident who’d had his credit card account used repeatedly for fraudulent transactions at a Family Dollar store in Everett.
Everett PD Detective Michael Lavey obtained security camera footage from the local Dollar Store in question. When Lavey asked the store clerk if he knew the individuals pictured at the date and time of the fraudulent transactions, the clerk said the suspects had been coming in for months — several times each week — always purchasing gift cards.
“The clerk told me they would come into the store in pairs, using multiple credit cards until one of them was finally approved, at which point they’d buy $500 each in prepaid gift cards,” Lavey said. “We have two Family Dollar stores in Everett and a bunch in the surrounding area, and these guys would come in three to four times a week at each location, laundering money from stolen cards.”
Not long after Lavey posted snapshots from the video footage on a state-wide police network, he heard from an officer in Boston who said a suspect resembling one of the men in the photos was recently questioned at a city hospital after being stabbed in the legs and buttocks in an unrelated robbery. The assailant in that attack was arrested, but his victim — Jean Pierre — refused to answer questions about the incident. The police seized Jean Pierre’s pants as evidence in the assault case, and discovered numerous prepaid cards in the pockets of the trousers.
Lavey said he subpoenaed the credit card records, and working with investigators at American Express and Citibank was able to determine that at least one of the cards had been stolen from the Splash Car Wash in Connecticut. In effect, thieves were buying stolen cards to finance the purchase of gift cards, some of which would later serve as hosts for new stolen card data once their balance was exhausted. The cops call it money laundering, but in this case it might as well be called card washing.
WILL THAT BE A SUPER OR DELUXE WASH?
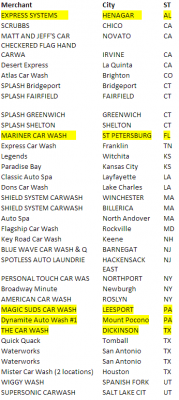
Soon enough, Lavey had linked up with Michael Chaves, a detective with the police department in Monroe, Conn. who’d been investigating card breaches at 14 separate car washes in his state, including the Splash case. Working with the Connecticut Financial Crimes Task Force, a broad law enforcement group that includes the U.S. Secret Service and state police, they determined that the local company was but one of at least 40 car washes across the country that had been hacked and relieved of countless customer credit and debit cards since at least February 2014.
Chaves said he interviewed several of the car wash owners, and discovered that they were all using the same point-of-sale systems developed by Randolph, N.J.-based Micrologic Associates. Chaves said the store owners told him the devices had remote access via Symantec’s pcAnywhere enabled, access that was granted to anyone who knew the same set of default credentials.
“The pcAnywhere credentials were created by Micrologic, but unchanged for years,” Chaves said.
That was the same conclusion independently reached by Detective Steven LaMears with the police department in Keene, N.H. Earlier this month, a police captain at the Keene Police Dept. saw fraudulent charges show up on his credit card shortly after using it at the town’s Key Road Car Wash, an establishment which used Micrologic’s point-of-sale system.
LaMears also heard from a company in New York which reported that two its executives each had their cards compromised multiple times after visiting the Key Road Car Wash in Keene.
“We confronted them, and working with the U.S. Secret Service got them back up and running,” LaMears said of the local compromised car wash. “The Secret Service told us they were running an old version of Micrologic that had the same, one login for everything, and were using an old version of Windows XP.”
MICROLOGIC POS: CAR(D) WASHING SOFTWARE?
Micrologic President and CEO Miguel Gonzalez said that only about one-third of the 40 or so car washes on the Secret Service’s list of compromised stores (see above left) were running Micrologic point-of-sale software; the rest, he said, were using products made by other software vendors.
Gonzalez said Micrologic recently began urging all of its customers to transition away from pcAnywhere and adopt multi-factor authentication that involves the use of a one-time code that is sent via text message to the administrator’s mobile device.
Asked about the claim that crooks may have been abusing default credentials in Micrologic’s software to steal card data from car washes running its product, Gonzalez said the breached companies were running older, outdated versions of pcAnywhere . He said attackers appear to have targeted vulnerabilities in the remote access software itself — not merely abusing some set of default credentials.
“What the investigators we’ve worked with so far have been able to gather is that [the thieves] were exploiting not the pcAnywhere credentials, but a flaw in old versions of pcAnywhere,” Gonzalez said.
In January 2012, Symantec acknowledged that hackers had stolen the source code to the popular remote access software, and it urged users to either update the software — which included fixes for several critical bugs — or remove the program altogether.
Whether the crooks are exploiting software vulnerabilities or weak/default credentials in this case, security experts routinely advise companies to avoid using remote administration tools on point-of-sale devices — or else to severely lock them down with strong passwords and other restrictions. One stubbornly static finding in data-breach reports published annually by Verizon, Trustwave and other companies that get hired to investigate breaches involving card data is that far too many point-of-sale breaches start when the thieves abuse some kind of remote access tool installed on the point-of-sale device itself. Typically, this involves the attackers scanning the Internet for remote administration software, and then using automated tools that can break into any systems that are protected with weak passwords.
THE NEW THUG LIFE
Point-of-sale compromises at restaurants, retailers, car washes and elsewhere are frequently attributed to hackers in Romania, Russia, Ukraine and other parts of Eastern Europe. But according to Detective Lavey, the buyers of these stolen goods increasingly are street gang members here in the United States. Lavey said Jean Pierre — the stabbing victim who was found in possession of nine stolen credit cards — is a member of the Bloods an African American street gang.

Surveillance camera footage from Dollar Stores where police say these individuals used stolen credit cards. Source: Monroe, Ct. Police. Jeanne Paul is pictured top right.
“All these kids are Blood gang members, tattooed up or self-admitted,” Lavey said. “And they’re starting to work smarter, not harder. Individually, this card fraud doesn’t meet the threshold where the federal government is going to say ‘Hey, let’s grab these guys.’ Locally, they’re doing it across broad jurisdictions and jumping from state to state and coming away with hundreds of thousands of dollars.”
Lavey said he recently worked a case where a number of kids in their late teens were using stolen credit cards to go on shopping sprees at multiple Target stores along the east coast.
“We just wrapped up a case where these kids were coming up from New York, and they were hitting every Target store in the area for $6,500 a whack,” Lavey said. “In one weekday, they did this hitting all Target stores up and down the eastern seaboard. They now have charges pending in New York, New Jersey, Virginia and Pennsylvania.”
Given how easy it is to buy stolen cards, encode them onto gift cards and then use those cards to buy goods in big-box stores that can be easily resold for cash, Lavey said he wonders why old-fashioned bank robberies are still a problem.
“Honestly, the fact that we still have bank robberies is sort of perplexing,” he said. “Rob a bank and you’re lucky if you get away with $600. But you can rob a credit card company and all the banks are afraid to have their name associated with a case like this, and they quickly reimburse the victims. And most of the retailers are so afraid of having their name in the press associated with credit card fraud and data breaches that make the job doubly hard for us.”





I don’t think I have enough facepalm in stock to cover all the angles on this one o_O
HA! +1 🙂
I had two credit cards “cloned” while I was in Toronto in 2008, probably at a gas station I used to use and was busted by the police for credit card fraud 6 months later, and the perps used both cards in one of those shopping sprees in Florida. I got a $4000 or so in one card and almost 5 grands on the other, spent in 6 Target stores in different cities between Jacksonville and Gainesville.
Luckily the Brazilian bank that issued both cards didn’t charged me, but I’ve always wondered what this guys bought with my credit cards…
I had my credit card cloned by Europcar car rentals at Johannesburg airport. Because you are renting a car they also make a copy of your driver’s license and passport, which is great for identity theft.
I reported it to the local police, and Europcar, both of didn’t really care, saying it is a common occurrence, and the credit card company will reimburse me, so I shouldn’t care either.
I mean:
“they would come into the store in pairs, using multiple credit cards until one of them was finally approved”
should really tip off even the most lackadaisical minimum wage clerk.
on that note, a lot of the thief’s will actually befriend someone “on the inside” so they can get unrestricted access to the readers.
I was going to post this exact same bit. I appreciate not everyone on the planet is a rocket scientist but how on Earth could this not raise any alarm bells?
As said here often, human beings routinely remain one of the weakest points in the chain.
(to anyone *who* knew the)
It is likely the clerk was well aware there was something shady going on. They either just didn’t care or were not in a position to do something. I am sure in many cases clerks like this are told not to do anything, it isn’t worth the risk to them just to save some big bank a few dollars.
Sadly, you are probably correct. A store manager could get wacked. The U. S. government has a gang website: http://www.nationalgangcenter.gov
The stolen numbers are cloned onto gift cards. It’s not uncommon for honest consumers to have multiple gift cards, some of which have been used. The criminal only has to hand a gift card to the cashier and say “let’s try this card – I think I still have enough on that one”. The cashier attempts to charge the total to the card and it is declined – they do not get to see why it is declined. It could very well be that there is $250 on the card when $400 is needed, so when the criminal says “not that one huh, okay, let’s try this one” it doesn’t ring alarm bells.
There are a few obvious fixes here.
1. The banks have to start pursuing merchants that are happily letting some guy swipe card after card, get rejection after rejection, with no basic check of ID or any other form of verification. If banks are too worried about reputational risk (which they’re already running), then their insurers need to refuse insurance. It isn’t just the banks that are paying for this, it’s everyone – just so a few shops can get every transaction they can get their grubby hands on. They’ll be the same shops that sell cigarettes to six year olds.
2. Surely there are criminal charges associated with presenting a card that isn’t in your name, and with accepting that card. In other words, there needs to be criminal liability on the shopkeeper as well. That way the employee who’s a friend of the gang still gets not just sacked but jailed.
3. Who owns that machine in the shop? Doesn’t it phone home to a bank every time a transaction is presented to it? If I were that bank, I’d want my people on the phone to that shop as soon as card number two fails from the same location, within one minute, in a different name. I would want some an explanation of WTF they are doing. The only alternative I can present to this that might make sense (depending on available resources) is instead of phoning the shop making sure cops are there in the next five minutes and rejecting every transaction between now and then.
This whole story looks like “how can we set up a system that’s designed to fail, for the processing of credit card transactions”. Where are the incentives for the shop clerk or shop owner to say “this isn’t your card, nothing for you today”?
The merchant is heavily punished. It’s called a chargeback. Anytime we accept a card that is presented fraudulently the burden of proof is on us, the merchant, to prove that we adequately verified identity. Unfortunately the banks and card brands idea of identity verification is a signed receipt. Unfortunately for us that’s all they require, but then they often reject it when we get asked to show proof of signature.
We eat that transaction. When Targets were getting hit up and down the eastern seaboard who do you think paid for that? Not the banks – they refunded the cardholders the money and then took it out of Target’s settlement for the day.
Not exactly true – if it is a counterfeited magstripe then the issuer doesn’t have any chargeback rights under any of the card associations (pending the October 2015 liability shift). Under card-not-present rules such as telephone, mail, and eCommerce transactions, the issuer could potentially have chargeback rights pending the merchant representment of the facts. Counterfeit card and lost/stolen cards that are swiped are 100% financial institution losses that the merchant will never sustain.
Merchant is correct.
If Merchant is correct then the money is going somewhere other than the issuers – we’re not getting it and any restitutions from the association recoveries from the points of compromise is negligible.
Actually in 2013… 63% of all card fraud was borne on the Issuing bank and NOT the merchant. For card present-counterfeit fraud ,the Association rules are currently in the favor of the merchant, in that, if a signature is captured for the transaction (regardless of legibility) the merchant has no responsibility for the fraud. If an issuer does submit a chargeback request, it will be denied. With Card Not Present fraud the merchant does have a little more liability. The system is lopsided and understandably so, at least to an extent… if the majority of the fraud losses were held by the merchant, they would never accept the cards as payment. The financial institution makes the money needed to keep their credit or debit card program going by the interchange fees it receives. I have seen fraud losses in a few days add up to months worth of interchange fees for community sized institutions and they had to eat nearly all of it. And yes… they in part blame the merchants. The problem is that merchants and banks are too busy pointing fingers at one another and not working together. The hackers and fraudsters of course, prefer it that way. Divided we are a much easier target.
In principle, I’d agree with you, but my understanding is that you can have authorized users who aren’t the named party on a card.
Worse, if the card is a gift card, there isn’t a name to it, and I personally have no idea how much is on any of mine.
I actually had an AmEx gift card issued to me once by an employer. I lost track of the card and had it reissued. I’ve since found the original card, but it wouldn’t have been unreasonable of me to try to use it (heck, that might have been how I found out it expired – I can’t remember) – note that in California, gift certificates don’t expire (the expiration date is overruled by state statute).
If I ran credit card processing for one of these stores, after X failed charges within a certain time interval, I’d probably ask the police to investigate. As Brian notes, this is the new world replacement for bank robbery and it should be treated as such – silent alarms triggered by monitoring stations, not requiring the involvement of clerks / management. Given that the criminals involved are in genuine gangs, you don’t want clerks to confront them – just as we don’t ask tellers to confront bank robbers.
Come, on. I suppose you have a have a gift card, with your name on it? The information is usually not showing up on the pos, even if being read at a bank, there is no verificationof the user. It can be anyone. A credit card, is a letter to the salesman,sorry ladies,sales person, like a letter of mark,granted in leiu of actual money. And can be assigned anywhere.
But the thing I hated to see in the article was the statement “to small to prosecute” and “gang ”
Reminds me of collusion, and one needing the protection of law? So for the ” honest” citizen, don’t give gift cards,give cash.
Why not spread some of the cost of the cops time back to the card companies that don’t force merchants to keep their hardware, operating and application software up to date? (Given that these companies are eating the cost of the fraud, the additional costs from authorities won’t do much to encourage them to force to do proper maintenance and reinvestment in their POS systems, but it will help law enforcement and the taxpayers to not shoulder costs that could easily be prevented by credit card companies monitoring the POS equipment the accept charges through.)
Robert,
You’re punishing the victim. I bet the locks on your house could be quickly bypassed using an bump key.
Should you have to pay the police for their time if some one breaks into your home?
We already compensate the police for their time via taxes.
Why not force the banks and credit card companies to implement a more secure technology for allowing cardholders to present payment? How about supporting end to end encryption so the merchants can focus on running their businesses instead of fighting cyber crime fires?
Can you imagine how the face of American business would have been different if 50 or 100 years ago every merchant from the local tavern to the local hardware store to the local grocery had to employ or retain the services of experts in cash handling (the predominant payment method of the times) in order to have the privilege of accepting the customers money? It would have significantly altered the course of history and probably not in a positive way. That’s where we are today.
Let’s get the banks and card brands to build a truly secure infrastructure and then let the merchants get back to business.
You can’t. Credit is a sham, built on a shaky foundation that will never be secure.
Agreed.
I didn’t think Brian was old enough to remember that movie.
I used a POS at a local car wash just last week… I thought at the time that the car wash could be a prime target for cybercrime. How little did I know.
“Family Dollar” isn’t a “dollar store”, ftr. Not a big deal, but mildly relevant.
Technically it is a dollar store, the problem is that dollar stores can’t sell very many things for a dollar anymore thanks to a strengthening Yuan, rise in shipping costs, and weakening dollar. As a result most of the items in dollar stores, like Family Dollar, now cost more than $1. They keep the names because they have “brand recognition,” not because they still make sense in their original context.
“And have an A1 day”…
These POS systems are just that, a real P0S. Since a lot of the liability ends up resting with the merchant rather than the software vendor (because, lets face it, the system is never actually PCI compliant when audited), I’m surprised there hasn’t been a greater push for a segregated design.
Especially with Square or similar processors, you have the credit cards themselves processed on iPod touches that just handle the credit cards, with everything else on a second device.
Also, chip-cards can not come soon enough. Reducing the fraud to mostly be on “card not present” is a huge win, since card not present fraud requires shipping, which leaves a huge paper trail and also enables a huge amount of secondary fraud detection based on shipping addresses.
>The police seized Jean Pierre’s pants
LOL – that comment made my day!
Interesting article
Stabbed in the butt, lol.
Nah… with these guys, a stab in the butt would have probably missed the pants.
I think it takes vigilance on the part of clerks and employees to spot these crooks. Observing repeated suspicious behavior is one thing to look for before alerting authorities. It’s often the human component that catches these low-lives.
It is not realistic to expect a low-paid clerk in a crime-ridden neighborhood to confront someone or even notify authorities when a local gang member attempts to use credit cards and the cards are rejected. Vigilant clerks might help in some situations, but not in this story.
Improved processes and technology will help.
Confront them, no. Notify their credit card processor something is afoot? Yes. Especially if they are repeat offenders, then the credit card processor has a better chance of catching the crooks by involving the local PD who would then ask for the stores video footage and be on alert. All the clerk needs to do is mark it “fishy” to assist them in flagging and pinning these guys down sooner. We’re talking days instead of weeks or months.
“then the credit card processor has a better chance of catching the crooks by involving the local PD who would then ask for the stores video footage and be on alert. All the clerk needs to do is mark it “fishy” to assist them in flagging and pinning these guys down sooner. We’re talking days instead of weeks or months.”
You think? I think we’re talking “never.” You think the NYPD (or the Secret Service whose jurisdiction this technically falls under) are going to waste their “limited resources” going after a couple of homeys with a stolen card or three?
If they come back week after week, particularly if it’s always on the same day, then it’s easy pickings for law enforcement. If they don’t follow a set schedule then the local PD probably won’t spend the money to keep a plainsclothes officer lounging around the store waiting for them to show up.
Still, it’s unreasonable to expect a below-poverty-level clerk to get stabbed/shot for testifying against the gang, just to benefit some multinational financial institution. Their credit card processor should be the one implementing some kind of alarm when a half dozen or more credit cards (from multiple individuals) are run against a single transaction, not to mention the bank noticing recurring fraudulent transactions at the same store.
It’s amazing the kind of response large firms can get from local PDs, too bad they can’t offer that same level of support to normal citizens. If only we all had their class of law firms on retainer…
“Still, it’s unreasonable to expect a below-poverty-level clerk to get stabbed/shot for testifying against the gang, just to benefit some multinational financial institution.”
Totally agree with that. It’s even unreasonable if the clerk was making 60k a year….
I live in Eugene Oregon. My card was compromised about two months ago and someone made a purchase at a dollar store in Florida. After reading the article I wonder if my card was compromised at a local car wash that I had used. I went to the same car wash as recent as yesterday.
It’s so hard to tell, unless you’ve only ever used that credit card at the car wash. It definitely could have been compromised somewhere else.
Going to cash overall seems like a good thing, but especially at standalone credit card swipers exposed at places people aren’t at for a good chunk of the day (like car washes) – where the bad guys can fiddle with them without being noticed.
I’m a little unclear from the article, but it’s saying that default pcAnywhere creds were used? So, that would give people the ability to start a pcAnywhere session, but wouldn’t there still need to be creds on the Micrologic devices themselves? Or, is pcAnywhere using pass-through authentication (gasp!) to Micrologic?
Yeah, according to the investigators I spoke with, the hacked systems were running Logicwash installs with web front-ends that had some default credentials built in. See this
http://krebsonsecurity.com/wp-content/uploads/2014/06/README.txt
Note that the help file states that they were “hard coded” into the devices. Micrologic said in an interview that those credentials were not hard-coded, but instead the default. Looks like some people just didn’t change the default.
Assuming limited intelligence in the gang, if someone had changed the credentials, a key logger would be sufficient to resolve this.
Once you have remote access, the system is compromised.
Also, 2FA wouldn’t help if the attacker could replace it.
I.e., 2FA in the POS + misconfigured Remote Access = no security.
There’s a lot of remote access control available on the Internet (home automation and power production are amongst the scary ones).
I’m waiting for articles by Brian about someone using a weak password on a Cable company offered “home monitoring system” to remotely unlock and disable the monitoring (before robbing the house).
Well either people didn’t change the default on purpose, or they believed the documentation when it said the security was hard coded. Kind of hard to fault people for not trying to do exactly what the developer tells them they can’t do.
Then again, documentation is always the black sheep of software development. Nobody ever wants to write it, nobody ever wants to update it, nobody ever wants to document what changes they’re making. Google is absolutely the worst offender I’ve ever come across in this department, I spend countless hours chasing my tail reading through official documentation after official documentation that are all hopelessly out of date and don’t apply anymore.
“Well either people didn’t change the default on purpose, or they believed the documentation when it said the security was hard coded.”
I’d be willing to bet that most didn’t even know that these systems could be accessed remotely, probably never had a need for it.
The most common skimming locations in America are ATM’s, Self-Service Gas Pumps, Parking Garage kiosks and Car Washes.
Some may find it interesting that the number one Retailer where stolen/counterfeited cards are used is “Grocery Stores”. Next on the list is Pharmacies and after that you will find “Home Improvement”. What do all these retailers have in common? They all sell Pre-Paid Gift Cards.
One huge myth is that when a card is counterfeited criminals rush out to an electronics or jewelry store and run up large charges. The fact of the matter is that the vast majority of losses stem from Pre-Paid Gift cards.
I think that is the real story here. If retailers that sell Gift Cards, had policies that required them to capture the CVC2/CVV2 3 digit code on the back of the card for these purchases, we would see a substantial drop in fraud and the desire to obtain these cards.
But that is not the case and everyone from a boutique kiosk at a Farmers Market to a Large Multi-product national retailers sells gift cards and they are the number one diet supplement for fraud.
Many of the large retailers are converting over to accept “Chip” by October of 2015. At that time all counterfeit fraud liability will shift (expect for unattended gas pumps Oct 2017) to the store. This has the potential to wipe out a number of small businesses as the fraudsters will migrate from the Walmarts of the world to mom and pop stores where a single loss could wipe out all their profit for an entire month.
Krebs had a story a indicating that fraudsters typically purchase high end retail items and resell them on ebay or craigslist at a discount. This does happen, but it is not preferred. Certainly not by the more organized players. They much prefer cash. Use a prepaid to buy a money order and cash out or sell gift cards on the black-market is more preferred.
Requiring a check of credential for these purchases will not stop fraud, but it will put a whale of a dent in the problem. If Target, as an example is doing so much after their issue, what have they done to quell the purchase of Gift Cards in bulk in their stores by fraudsters with counterfeit cards captured from thier stores. The answer to that is “Nada”. Same is true for all the top retailers.
If you ever get frustrated because you have been declined at your favorite Grocery store and you think you bank is an idiot, its because that store is selling hundreds if not thousands of gift cards at a very high margin and the banks eat those losses. Your $300 in groceries does not look any different to the $300 in gift cards as banks cannot decision on what is being purchased only where. So ask you grocery store to ask for your three digit code when they sell gift cards and you will see skimming and fraud and the best, the number of times your are declined go down.
Greed is the enemy here. The fraudsters want Gift Cards and the store wants to sell this low carrying costs very high margin item. The only loser is the consumers that are constantly getting declined and the rates they are paying from banks for cards as fraud is not free.
Sorry for the long post, but this skimming is no where close to subsiding and will pick up dramatically and until stores that sell what could be called the “Cocaine” of the fraud trade (a.k.a. Gift Cards) improve their security at the POS, you can expect to get a lot more cards in the mail.
It is staggering the number of “gift cards” for sale on eBay, Craigslist, and other sites. It is also amazing to me that these cards tend to go for 85-95% on the dollar.
As a LEO the only time I saw merchants do something constructive was when Eddie Bauer had fraudsters purchase gift cards with forged checks, they turned off the card that was purchased. Most will not or can not even do that.
Your local PD in any city of any size does not have the time or ability to chase down videos of some meth head using the fraudulent card, when the banks undercut any possible prosecution by the refusal to cooperate without subpoena or search warrant in most cases. Couple that with the cost of bringing witness from long distances for trial and most D.A.s are not going to pursue it very far. The feds have the jurisdiction but they don’t touch anything until you get to pretty high dollar figures. Since it is never pursued, you almost never get to the feds charging minimums.
Most property crime is driven by meth and the pursuit of cash to purchase drugs. Couple that with low prosecution and presumed probation you have the formula for more and more crime.
“It is staggering the number of “gift cards” for sale on eBay, Craigslist, and other sites.”
It shouldn’t be. There can actually be a legitimate resale market for gift cards (I seem to even remember a site dedicated to just that).
What *I* find staggering is the amount of iPhones (I’d guess it’s the same for Android phones) for sale on eBAY with “Bad MEI” in the description. In other words, it’s a stolen phone that the carrier has disabled from rejoining their network. In iPhone land, “cloud locked” has now entered the jargon from stolen/lost phones that the owners have bricked through iCloud’s Find My Phone.
All brazen and open, but eBAY makes money off of it, and we all know that’s what counts.
“The clerk told me they would come into the store in pairs, using multiple credit cards until one of them was finally approved, at which point they’d buy $500 each in prepaid gift cards,”
Nothing suspicious about that…
“The cops call it money laundering, but in this case it might as well be called card washing.”
har har good one there Brian, DORK.
Well glad to see a few basketball Americans were apprehended. Now the hamburgers can feel safe.
We all know the fix for this is EMV. What’s the hold up?
The ‘solution’ can be temporary EMV, yes. But for the ones who didn’t understood why USA still not switch for this system is because corporations are making more money from fraud than from a secured system. Fraud = money for crooks (including the white collar ones).
This is why I wash my own car, not only do I do excellent detail, I don’t do crappy detail, especially in software design and security. Really, only 11- 50 people working at this company? wow, in NJ? no surprise there. Hah. I bet they have tanning salon management software too. that’s a big business in NJ.
They’ve got their software in too many staples in our society. this was a simple human error, that should’ve never happened. well, you get what you pay for. if they don’t want to go out of business I suggest they start going through all of their offered product code with more than eyes wide shut. either that or they spend way to much time at the tanning salon and their brains are fried. I do like the Tunnel Controllers. I know I won’t be going through any tunnels when I’m in NJ.
Hey BK, where did you get the README.txt install file from, on their website? wouldn’t surprise me if you did
===
===[Blurb or Burp, from their Not so LinkedIn site]===
Micrologic Associates is a leader in the sales, installation, service, and support of Point of Sale systems, Tunnel Controllers and Auto Payment Machines for Car Washes, Quick Lubes and Parking facilities. We provide easy to use solutions ranging from wireless hand held devices, conventional touch screen point of sale computers and controllers tailored to your specific requirements. Our systems provide Cash Management, Instant Credit clearing (to any processor), Labor management, VIP/ Fleet Management, Customer Tracking, as well as Unlimited Wash Program in the base software package. These systems can interface with most tunnel controllers available today and offer the ability to replicate the data from multiple sites for consolidated reporting and transferring of customer information. In addition, we offer our Web application for Management control. From any Web browser you can view live data, run reports, check time card activity and modify services.
Additionally, we offer a RFID solution for IBA/Rollover and Tunnel applications. This system can work with any Entry Machine and offers “Unlimited Wash” functionality with Credit Card on File.
Micrologic has the engineering know-how, support capabilities, and consultative resources needed to offer you a system tailored specifically to your requirements. Micrologic’s commitment to our customers does not end with the completion of the installation. We offer on-line support and a variety of support programs to ensure maximum performance and longevity of your investment.
===
Thanks for the great read Brian, excellent story.
It’s getting hard to feel sorry for the banks when they post large profits and pay no interest on savings, offer enormous bonuses to their upper management, and place the cost of all this right back on the consumer.
But crime is crime and someone has to pay.
It’s important to remember, that the banks can deduct up to half their losses from credit card theft from their federal tax and pass the other part on to the consumer in various ways.
Great article Brian, thank you. Basically trying to migrate over to cash, but its not an easy thing (who wants to get and carry cash all the time), with checks seeming even more dangerous than credit cards.
Interesting to note that Symantec announced end of life for pcAnywhere in May 2014…which is probably a good thing from a “was this even a good idea as a product” perspective.
Brian, do you use credit cards for much these days?
The fact that magstripe use is so prevalent in the USA is sad. That is the fundamental issue.
” …They would come into the store in pairs, using multiple credit cards until one of them was finally approved, at which point they’d buy $500 each in prepaid gift cards”
And that never evoked any suspicion, any checking action ?
A few months ago I needed to complete spending $3K on a credit card (to get a substantial number of airline points). So I went to Lowe’s to buy a $500 gift card.
They asked for picture ID, and made more than one phone call before let me do the purchase.
Lowes folks are actually pretty clueful. They participate at a local level with LEOs to see what’s going on with crooks and provide feedback to others who participate in HTCIA meetings.
I’m betting they spotted this theft method very early on, came up with those procedures, and then quickly implemented them in all their stores.
I work for a carwash on this list and was told that we have experienced the same issue and we do not run micrologic. I guess its a widespread issue
The Merchant is the individual who signed the user agreement to accept payment cards. In that user agreement is the requirement they must maintain PCI-DSS compliance. Most merchants “DON’T” read the user agreement, they only look at the cost of transaction fees, what percentage they will pay per sale, and how quickly the funds will be deposited into their accounts. The user agreement is a CONTRACT and the merchant is responsible for maintaining his end of the CONTRACT regardless if he/she read it or chose to ignore it.
PCI-DSS does not dictate to merchants; “You Must Use This Equipment/Software or Payment Processor to accept Payment Cards.”
The PCI-DSS website shows you a list of evaluated/validated and approved hardware/software and payment card processors found to meet the requirements of PCI-DSS (if installed correctly). To meet PCI requirements merchants are required to utilize approved vendors/products among other requirements.
I, go to a merchant and make a purchase. The merchant or his employees take actual possession of my payment card or I swipe the card myself on POS equipment provided by the merchants sub-contractor (payment processor) or utilizing POS equipment the merchant purchased elsewhere. The sub-contractor then processes my purchase directly or through their sub-contractors (oftentimes unknown to the merchant) utilizing hardware/software on their systems that may or may not meet PCI requirements. Eventually the funds are credited into the merchants bank account.
Under a signed contract the merchant agreed to be PCI-DSS compliant. If he/she was, they would know if their equipment was validated, their payment card processor was validated, and if any sub-contractors besides the processor are involved and PCI compliant.
The entire process starts with the merchant and ends in the merchants bank account…hopefully without being breached.
Do you want to see something scary??? Go to ebay.com and enter “Point of Sale” in the search box. The search will return thousands of listings for POS systems, all of them that I looked at are NOT on the approved list at the PCI-DSS website. If they ever were on the list, the validation has expired because most utilize Windows 2000 or XP operating systems that no longer receive support from Microsoft.
If you look under some of the POS sellers history you will see they have sold hundreds if not thousands of these outdated or no-name POS systems placing any and all customers at risk.
If I ever wanted to use my powers for evil, I would purchase thousands of these defunct POS systems and add back doors for online systems, and rig dial-up POS systems with card capture, remote access and probably add Bluetooth for downloading numbers. I would list these POS systems on ebay and offer free upgrades and ongoing support. After the purchase the buyer registers with me and I would know the business name, location, phone line or IP address the POS system was connected to.. Everything I needed to access the systems anytime, from anywhere. Money in the bank baby !!!
So yes, PCI compliance starts and ends with the merchant and those they sub-contract(s) to process his payments.
On a side note; due to large incidents of skimming payment cards here in Northern Nevada a few years ago, we launched an awareness program for merchants. Of the 485 small/midsized local business we surveyed we found 94% were not compliant with basic security practices, let alone PCI-DSS requirements.
Most of the owner/operators told us they never heard of PCI requirements, even though Nevada’s, Consumer Protection law mandates compliance with PCI-DSS for any organization that accepts payment cards.
Should be part of their business licensing process. To get a licensing, you should have to state if you take credit card payment. If you take credit card payment, you should have to show proof of PCI training and compliance when obtaining/renewing your annual business license.
This helps prevent crime which helps local law enforcement and keeps them free for other tasks.
Jason,
You’re so correct in your reply. Now that I’m a retired LEO I have approached the Attorney General (she’s as useless as Harry Reid) and other prominent state elected officials on the enforcement of NRS 603A-Protection of Personal Information. As I’m sure you’re aware Nevada has a small population totally dependent on the tourist industry for its survival such as; gaming, hospitality, and unions who have great influence on our elections… once again I will use Dirty Harry Reid as an example of the influence they have.
Forget the fact that every criminal dirtbag travels to Nevada for work or pleasure and we are #6 worst state for payment card fraud (formally #2). Amazingly NRS 603A passed probably because everyone was asleep at the switch. However, requiring proof of PCI compliance or training prior to receiving a business license isn’t seen as a positive political move.
I will have to push again for this during a non-election year.
Thanks for your simple and logical comment to correct the problem!!!
To Retired Criminal Investigator. I worked for the moron who wrote that bill. An attorney with no tech expertise. He’s now running EITS. Scary crap.
SOLUTION: Pay Cash!
“…the clerk said the suspects had been coming in for months — several times each week — always purchasing gift cards.” … “The clerk told me they would come into the store in pairs, using multiple credit cards until one of them was finally approved, at which point they’d buy $500 each in prepaid gift cards,” …
And this didn’t raise any red flags… not even one?
Time to ditch the credit cards and use cash only.
It all started when they put that sign up. Much like “Target” – if your going to paint a target on your…. enterprise or if a potential hacker sees humor in some means of communication, sometimes that all it takes for them to muster the initiative to violate ( in respect to the sign – no pun intended) and break in a business.
Before Target’s major card breach, I can remember them having issues with gift cards and people hopping behind closed counters with a mini crow bar, laying down and popping open those display cases and exiting the building with phones, cameras or other small high priced items. Not to mention the fact of people doing the Target thing and stealing a huge amount of OTC drugs and Pharmacy related products.
This is another avenue which leads to the cesspool. All is fine and dandy when he POS ( errr that could have 2 meanings) works fine. A false sense of security by the shop owners means lax security standards.
All POS systems should be blacklisted to every IP minus the payment gateway. There is no reason to have a POS open to the world. They should also be behind a NAT.
Never assume that these people get any of the critical emails or correspondence because they may not read them, or get them. An older copy of of XX operating system? How old? Looks like there are too many issues and avenues of attack to make these things compliant. Use a Laptop with a strict whitelist and plug it in only long enough to update, process payments and then disconnect/disable the internet connectivity (remove cable / disable NIC). Many will say update the POS software – but if it is inventory based – it may be a bigger feat that climbing a mountain 50 dollar bills totalling of the US debt.
If you need your car detailed, stay away from gas station car washes. It will not help your car at all. Taking it to a professional is definitely the best option.