Sources in the financial industry say they’re seeing signs that Dairy Queen may be the latest retail chain to be victimized by cybercrooks bent on stealing credit and debit card data. Dairy Queen says it has no indication of a card breach at any of its thousands of locations, but the company also acknowledges that nearly all stores are franchises and that there is no established company process or requirement that franchisees communicate security issues or card breaches to Dairy Queen headquarters.
Update, Aug. 28, 12:08 p.m. ET: A spokesman for Dairy Queen has confirmed that the company recently heard from the U.S. Secret Service about “suspicious activity” related to a strain of card-stealing malware found in hundreds of other retail intrusions. Dairy Queen says it is still investigating and working with authorities, and does not yet know how many stores may be impacted.
Original story:
 I first began hearing reports of a possible card breach at Dairy Queen at least two weeks ago, but could find no corroborating signs of it — either by lurking in shadowy online “card shops” or from talking with sources in the banking industry. Over the past few days, however, I’ve heard from multiple financial institutions that say they’re dealing with a pattern of fraud on cards that were all recently used at various Dairy Queen locations in several states. There are also indications that these same cards are being sold in the cybercrime underground.
I first began hearing reports of a possible card breach at Dairy Queen at least two weeks ago, but could find no corroborating signs of it — either by lurking in shadowy online “card shops” or from talking with sources in the banking industry. Over the past few days, however, I’ve heard from multiple financial institutions that say they’re dealing with a pattern of fraud on cards that were all recently used at various Dairy Queen locations in several states. There are also indications that these same cards are being sold in the cybercrime underground.
The latest report in the trenches came from a credit union in the Midwestern United States. The person in charge of fraud prevention at this credit union reached out wanting to know if I’d heard of a breach at Dairy Queen, stating that the financial institution had detected fraud on cards that had all been recently used at a half-dozen Dairy Queen locations in and around its home state.
According to the credit union, more than 50 customers had been victimized by a blizzard of card fraud just in the past few days alone after using their credit and debit cards at Dairy Queen locations — some as far away as Florida — and the pattern of fraud suggests the DQ stores were compromised at least as far back as early June 2014.
“We’re getting slammed today,” the fraud manager said Tuesday morning of fraud activity tracing back to member cards used at various Dairy Queen locations in the past three weeks. “We’re just getting all kinds of fraud cases coming in from members having counterfeit copies of their cards being used at dollar stores and grocery stores.”
Other financial institutions contacted by this reporter have seen recent fraud on cards that were all used at Dairy Queen locations in Florida and several other states, including Alabama, Indiana, Illinois, Kentucky, Ohio, Tennessee, and Texas.
On Friday, Aug. 22, KrebsOnSecurity spoke with Dean Peters, director of communications for the Minneapolis-based fast food chain. Peters said the company had heard no reports of card fraud at individual DQ locations, but he stressed that nearly all of Dairy Queen stores were independently owned and operated. When asked whether DQ had any sort of requirement that its franchisees notify the company in the event of a security breach or problem with their card processing systems, Peters said no.
“At this time, there is no such policy,” Peters said. “We would assist them if [any franchisees] reached out to us about a breach, but so far we have not heard from any of our franchisees that they have had any kind of breach.”
Julie Conroy, research director at the advisory firm Aite Group, said nationwide companies like Dairy Queen should absolutely have breach notification policies in place for franchisees, if for no other reason than to protect the integrity of the company’s brand and public image.
“Without question this is a brand protection issue,” Conroy said. “This goes back to the eternal challenge with all small merchants. Even with companies like Dairy Queen, where the mother ship is huge, each of the individual establishments are essentially mom-and-pop stores, and a lot of these stores still don’t think they’re a target for this type of fraud. By extension, the mother ship is focused on herding a bunch of cats in the form of thousands of franchisees, and they’re not thinking that all of these stores are targets for cybercriminals and that they should have some sort of company-wide policy about it. In fact, franchised brands that have that sort of policy in place are far more the exception than the rule.”
DEJA VU ALL OVER AGAIN?
The situation apparently developing with Dairy Queen is reminiscent of similar reports last month from multiple banks about card fraud traced back to dozens of locations of Jimmy John’s, a nationwide sandwich shop chain that also is almost entirely franchisee-owned. Jimmy John’s has said it is investigating the breach claims, but so far it has not confirmed reports of card breaches at any of its 1,900+ stores nationwide.
Rumblings of a card breach involving at least some fraction of Dairy Queen’s 4,500 domestic, independently-run stores come amid increasingly vocal warnings from the U.S. Department of Homeland Security and the Secret Service, which last week said that more than 1,000 American businesses had been hit by malicious software designed to steal credit card data from cash register systems.
In that alert, the agencies warned that hackers have been scanning networks for point-of-sale systems with remote access capabilities (think LogMeIn and pcAnywhere), and then installing malware on POS devices protected by weak and easily guessed passwords. The alert noted that at least seven point-of-sale vendors/providers confirmed they have had multiple clients affected.
Around the time that the Secret Service alert went out, UPS Stores, a subsidiary of the United Parcel Service, said that it scanned its systems for signs of the malware described in the alert and found security breaches that may have led to the theft of customer credit and debit data at 51 UPS franchises across the United States (about 1 percent of its 4,470 franchised center locations throughout the United States). Incidentally, the way UPS handled that breach disclosure — clearly calling out the individual stores affected — should stand as a model for other companies struggling with similar breaches.
In June, I wrote about a rash of card breaches involving car washes around the nation. The investigators I spoke with in reporting that story said all of the breached locations had one thing in common: They were all relying on point-of-sale systems that had remote access with weak passwords enabled.
My guess is that some Dairy Queen locations owned and operated by a particular franchisee group that runs multiple stores has experienced a breach, and that this incident is limited to a fraction of the total Dairy Queen locations nationwide. Unfortunately, without better and more timely reporting from individual franchises to the DQ HQ, it may be a while yet before we find out the whole story. In the meantime, DQ franchises that haven’t experienced a card breach may see their sales suffer as a result.
CARD BLIZZARD BREWING?
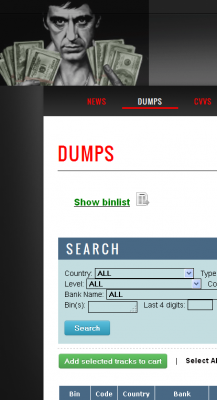 Last week, this publication received a tip that a well-established fraud shop in the cybercrime underground had begun offering a new batch of stolen cards that was indexed for sale by U.S. state. The type of card data primarily sold by this shop — known as “dumps” — allows buyers to create counterfeit copies of the cards so that they can be used to buy goods (gift cards and other easily-resold merchandise) from big box retailers, dollar stores and grocers.
Last week, this publication received a tip that a well-established fraud shop in the cybercrime underground had begun offering a new batch of stolen cards that was indexed for sale by U.S. state. The type of card data primarily sold by this shop — known as “dumps” — allows buyers to create counterfeit copies of the cards so that they can be used to buy goods (gift cards and other easily-resold merchandise) from big box retailers, dollar stores and grocers.
Increasingly, fraudsters who purchase stolen card data are demanding that cards for sale be “geolocated” or geographically indexed according to the U.S. state in which the compromised business is located. Many banks will block suspicious out-of-state card-present transactions (especially if this is unusual activity for the cardholder in question). As a result, fraudsters tend to prefer purchasing cards that were stolen from people who live near them.
This was an innovation made popular by the core group of cybercrooks responsible for selling cards stolen in the Dec. 2013 breach at Target Corp, which involved some 40 million compromised credit and debit cards. The same fraudsters would repeat and refine that innovation in selling tens of thousands of cards stolen in February 2014 from nationwide beauty products chain Sally Beauty.
This particular dumps shop pictured to the right appears to be run by a completely separate fraud group than the gang that hit Target and Sally Beauty. Nevertheless, just this month it added its first new batch of cards that is searchable by U.S. state. Two different financial institutions contacted by KrebsOnSecurity said the cards they acquired from this shop under this new “geo” batch name all had been used recently at different Dairy Queen locations.
The first batch of state-searchable cards at this particular card shop appears to have first gone on sale on Aug. 11, and included slightly more than 1,000 cards. The second batch debuted a week later and introduced more than twice as many stolen cards. A third bunch of more than 5,000 cards from this batch went up for sale early this morning.






LOL – a “blizzard” of card fraud
My reaction exactly… 🙂
I see what he did there.
I bet it was done by someone calling himself, The Dude.
LOL! And here I thought I was the only one who would notice that!
OK, I rolled my eyes a the first blizzard joke, but two? Lol.
counting down to US EMV migration????
Migration to EMV won’t solve the problem-Just makes it a little harder….The bad guys will just find other ways to defeat them..
Hey, skepticism of technology is healthy, but for cases like this where the bad guy has taken over the point-of-sale equipment, EMV is a *huge* improvement over magstripe.
Try this experiment: search for an article about millions of EMV cards being compromised by a breach in Europe somewhere. There is no such article! EMV, though not perfect, presents enormous barriers. That’s why the bad guys focus on magstripe.
You don’t hear about it because as Brian has reported the laws in place put the risk on the consumer. EVM changes some of the risks but overall it just a shift in security that allows merchants and banks to shift liability to the user.
http://krebsonsecurity.com/2012/09/researchers-chip-and-pin-enables-chip-and-skim/
EMV isnt as safe as you would think. Unless the magstripe is 100% done away with, EMV cards still carry the stripe, and all you have to do is break the EMV chip and 99% of the retailers are configured to fail back to magstripe on defective EMV chip.
Ill be interested to hear more week after next at the PCI meetings, but last year we were still YEARS away from meaningful EMV in the US. Even the new regulations passed arent changing that. My retailer for one, has decided that our yearly cost of fraud < cost to upgrade our systems to support EMV.
Its going to be a SLOW adoption, if for no other reason than its expensive to replace all those PIN terminals, especially if you are in a retail sector with razor thin margins.
icknay:
Page 8, Para 1
https://www.frbatlanta.org/documents/rprf/rprf_pubs/120111_wp.pdf
Fraud has moved to Card Not Present and Cross Boarder. Yes, it has reduced the surface area but it’s an uneducated answer to say that “you can’t find stories on fraud in Europe since EMV”… Because you can.
European fraud still happens, even today, it’s already overcome. The question is impact size.
All it means, as it’s been said here before, is liability changes, and also higher prices on marketplaces. The fact is, most so-called “security experts” in big companies know nothing of how malware works, field-style. All they know is what their “geniuses” tell them, but while that might work in some cases, it’s not always practical. Knowledge and practical use with which to put the knowledge, are 2 different things.
The workers at dairy queen might not even know how to use a computer. I doubt they read Krebs blogs and would even know if their cash register was replaced or not, let alone look for a usb or skimmer…..let alone a virus…. lol
Most stores don’t even have actual security guards, we can’t expect them to have any sort of network security. I wonder if the IT guy for w/e system they use has ever been in the store except to install it.
I think we need computer science, in between math and english for primary education in gradeschool for everybody now, or Russia and China are soon to walk all over us.
Then again probably some inside job as usual imo.
plus they’re too busy with their “state of the art systems designed by my [their] brighest prodigee” that they don’t think they need to teach.
human error is the biggest vulnerability in any computer. You could have a totally unpatched system and if you have people with brains, it can do its job without being infected once in a long time. common sense is the best defense, not a firewall or antivirus.
Use cash. For every transaction that is cash-possible. Even gasoline (despite the inconvenience at “convenience” “pay-at-the-pump” gasoline sellers). Ditch, or no longer use plastic “check” cards. Use only credit cards, if you use plastic at all.
It has apparently come to this.
Will thieves transition to armed robbery more often knowing folks are carrying cash? I work as a mortgage fraud investigator and the amount & complexity of mtg fraud is unreal!!!
“Will thieves transition to armed robbery more often knowing folks are carrying cash?”
I think not. Armed robbery is much more dangerous and much more likely to land a person in jail than all the electronic stuff. Most of the bad guys will stick with the electronic stuff (they’ve moved to) for the foreseeable future.
true, except I think there needs to be defined, the difference between a carder and a person who spreads malware. Most “experienced hackers” don’t use the CCs they harvest, but sell them. The people who use them are often street thugs with no computer knowledge except where to buy the data. They are more likely to get caught, than the people harvesting to sell it in underground markets.
meh, credit card users are typically not responsible for fraud. I’ve had cards stolen a couple times – sometimes I’ve caught it, sometimes the credit card company has. I’ve never been responsible for the charges and had a new card in hand within days. The ability to take advantage of float and the credit card rewards outweigh the inconvenience.
I would argue it gives a strong incentive not to use debit cards, though – because then they are stealing your money, not the credit card companies.
Why? The fact that a world with lots of people has lots of fraud is not surprising. But it is no reason to cut off my nose to spite my face. I will continue to use the payment methods I find convenient.
It is great that Brian keeps on top of this stuff, but one of the consequences of his doing so is that I don’t need to live in a tinfoil hat (unless I have a business checking account)
funny, however, is the fact, that even the fraudsters get defrauded. as Machiavelli has said, “It is double pleasure to deceive the deceiver.”
Given that this method of breach discovery has become standard, I have 2 questions:
1) Aren’t there legal barriers to regulated financial institutions buying cards from black market thieves?
2) Does the presence of large FIs in this black market – with persistent demand and deep pockets – actually raise the prices of stolen credit cards, and therefore the incentive for hackers to perpetrate large data breaches?
Banks are often the first to be aware of the credit card fraud *because* they’re a customer of the dump shops. The sooner the fraud is disclosed, the quicker the value of the cards depreciates, so banks buying cards may raise the value at the very beginning, in the long run it decreases the value sharply.
I’d second what Eric said, although I seriously doubt that a) most banks do this (remember there are 14,000+ FIs in the US) or b) that those banks which do are anywhere near the biggest customers. Most banks can figure out a common point of purchase (the original of the breached cards) for a single batch just by purchasing five or so cards. The crooks who are making these sites the real money are buying dozens, hundreds or thousands of cards at once.
What I dont understand, is why Visa / MC arent sharing these analytic with the banks better. Both brands have extremely sophisticated fraud tracking / identification, but apparently they keep it all in house. AMEX is much better about this, I dont see why the banks should be out on an island.
Back to the OP’s point, this is the financial industry, there is far more back room BS going on than youd ever want to know.
The banks either participate in a fraud detection network (like Falcon) that spans multiple institutions, or the banks “go it alone” if they think they can craft a system to do it better/cheaper. Sadly they use the bottom line to decide which path to take; whatever saves them more money wins (and not always just because it works better, but because it makes it easier for them to push chargebacks to the retailers who hosted the fraud).
1) The investigations are generally done in conjunction with the Secret Service, and the buys are sanctioned.
2) They don’t buy a lot of cards, so they don’t contribute much to the bad guys. Fresh cards go for maybe $20 each, so they may spend one or two hundred dollars. Meanwhile, the thieves are selling hundreds of thousands of cards, and are making millions. The fraud team’s buys certainly aren’t keeping them in business.
re “Backoff”
“The alert [from DHS and the Secret Service] noted that at least seven point-of-sale vendors/providers confirmed they have had multiple clients affected.”
Have the names of the seven POS vendor/providers and their products been published? Is the breach related to flaws in their systems? Hardware? Software? Both? Poor implementation?
From what I know and have read, in no case was the POS software at fault. It has been poor security practices that allowed the backoff malware to be installed, same as the BlackPOS malware at target. They are scanning retailers for open RDP and other remote access methods, and using default passwords / guessable passwords to gain access to the POS devices and install the malware.
But to my knowledge, the POS vendors have not been publicly named.
Even if you are infected, if you have a webfilter / IDS IPS at your egress point, its extremely easy to block how backoff is ex-filtrating data. If anyone wants the regex, Ill be glad to post it.
Here’s our Emerging Threats Open Snort/Suricata rule to detect this:
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:”ET TROJAN Backoff POS Checkin”; flow:to_server,established; content:”POST”; http_method; nocase; content:”.php”; http_uri; content:”&op=”; depth:4; http_client_body; content:”&id=”; http_client_body; content:”&ui=”; http_client_body; content:”&wv=”; http_client_body; fast_pattern:only; content:”&bv=”; http_client_body; pcre:”/^&op=\d{1,2}&id=\w+?&ui=.+?&bv=\d{1,2}\.\d{1,2}($|&)/P”; reference:md5,d0c74483f20c608a0a89c5ba05c2197f; classtype:trojan-activity; sid:2018857; rev:6;)
The Krebs’ ‘Online Point of Service Best Practices for Businesses’ hasn’t been published yet (that I’ve seen).
I find it sarcastically humorous if a ‘simple’ security measure (or simple security measures) would have prevented this (and other POS breaches at the larger corporations) that “take security serious” (as the PR like to say from their “playbooks”).
No they haven’t been announced, and vendors will not willing give that info if you ask them. Backoff is a malware, not a flaw in a POS system. Although from experience, POS vendors requiring an admin level account for their software to run correctly is a big hole that could allow installation of the malware and more than one do it.
Remote access on on POS terminal is a certain no no. Heck internet access should never be allowed on a POS terminal. Whitelisting applications should be installed on POS terminals with tight controls on approvals. There is a whole long list of what most of these corporations should be or should have been doing.
“blizzard” of card fraud” come on Krebs , you’re a journalist not a comedian ! LOL
None the less, a good article at any rate.
I don’t get all this running jokes / allusions / innuendo about blizzard of card fraud. Is it something all Americans would know and because I live in West Europe I’m blissfully unaware about it ?
One of the signature ice cream treats made at DQ is called a Blizzard. It is very thick ice cream with other items (chunks of snicker bars, for instance), and the server turns the cup upside down for a second before delivering it to the customer (to show how thick it is).
Thanks ThursdaysGeek,
It was exasperating to feel kept outside of all jokes. 🙂
http://www.dairyqueen.com/us-en/Blizzard-of-the-Month/
Try this one. Was it three or two weeks ago? Article in I believe the kc star, so that would be script publishing. Also in /., about a proof of concept at the hacker conference. That article referenced college work/article from west coast colleges, and if I’m right, during the same conference was released the first proofs of car hacking, so that would be prior to 9-11. When that card style came out, about a card reader only having to be within six foot of the intended card, . That card sleeves would be necessary to prevent crosstalk, but that makes one think of remote skimmers, and multi processor capabilities.
EMV has built in protections from this, as they use a OTP. They arent hackproof, but as of yet, it has not been demonstrated that you could attack an EMV card while it is still in someones wallet. There are theoretical attacks, but not that can be done quick enough without access to the card for extended periods.
“Nearly all stores are franchises”
I was wondering why anyone would call a piece of malware “Backoff”. Sounds like stay away or something. I like the name “Zeus”, I can relate to that. “Backoff” sounds stand offish but I guess DHS approved it. One of your reference articles indicated the name comes from what was written in the code. I guess that answers my question. Thank you for this excellent article.
I would suspect it refers to “Back office”, as most retailers, us included, refer to computers that arent out in public spaces “back office” or “backoff” computers. And if your network isnt segmented correctly, you can hop from the backoff to the POS, many of which are setup by design that way. You setup the remote access on the backoff, and then hop to the register from the backoff for remote support. Not how we do it, but I know many do, esp in mom and pop environments where they have no full time IT support.
There aren’t any DQ requirements to report breaches to HQ but aren’t there PCI requirements for breach notifications? Also many states have breach notification requirements which I think would come into play here.
It may be true that in a situation like this an individual store has an obligation to report, but I doubt any of those stores think or believe that, or are even aware of it if it’s true.
Most data breach disclosure laws require that there be personal and financial information lost or stolen, but in the case of many of these card breaches, the data stolen is “Track data”, which often does not include the cardholder’s personal information. Here’s an example of a typical track (with modified/redacted info) taken from these dumps shops:
Track1:
Track2: xxxxxx0000801599=1409101152XXXXX? State:FL
That’s it. Under most state laws, if that’s all they were leaking from their POS, then they wouldn’t have to disclose because there’s no personal data being stolen.
Thanks, Brian.
You have to know (or reasonably believe) that you have been compromised to report it, under the PCI-DSS. And that disclosure only has to be to the card brands that are affected. So if you only accept Visa / MC, you only have to report to them, it is not required to report it to the banks, or to the public, or even customers.
EMV breaches have happened, it’s EU law that mandates they are kept quiet due to their qwerky privacy laws. As a result, not a lot of media attention.
Franchisee operations are going to be a problem since the corporate parent is usually not involved with the franchisees’ systems. Even with McDonald’s, Burger King and the like, corporate is getting inventory management and sales data from the restaurants nightly so that deliveries can be made. While that puts the corporate systems into PCI scope due to their access to these systems, they are not actually doing anything with card data/processing.
The exception is Exxon/Mobil which does process transactions due to the Speedpass system at their gas stations.
As with many franchise operations, there are often times a split between the franchisee and franchisor. The former tend to fudge their reporting requirements in all matters due to lack of trained personnel. Thus, the HQ spokesman Peters was probably not waffling on you with his response.
Most likely, the entire operation will shake this off as some sort of novelty issue “others should deal with” when in reality HQ should jump on their franchisees with a flamethrower to quickly separate those acting like kids vs the adults. As a side issue, those in corporate should be grilled as to why they are not providing security expertise to those behind the counter.
Ha! OK, Sherb. It took me a minute to realize how many references to the DQ menu were in your post.
I count 10. And you didn’t even use blizzard!
Yea I don’t get why these days you would treat your franchises any different than coporate. We certainly don’t, it is not going to be the franchise name drug through the papers if a breach happens.
We force our standards and security on our franchises, they do complain and sometimes a lot, but it is still our brand and our customers that we are looking out for. So their bottom line is a little lighter… And the hardware/software we buy or license is not cheap, but in the end it is the right thing to do to protect our customers and employees.
Backoff is short for Back of Office which is the server (not the POS front end) in Visa lingo.
Brian I guess that is why you are the Guru of all Gurus. THANK YOU!!!!
POS = Point of Sale or Piece of S–t?
yes
Yet another franchise with franchisees in Canada but not the same problem. Michaels, PF Changs etc – when will they clue in?
I’m told that there is perhaps slightly better information sharing in Canada between FIs/networks/etc.
But a bigger point about Canada, there are fewer everything.
http://en.wikipedia.org/wiki/List_of_banks_and_credit_unions_in_Canada
There are 28 domestic banks as of July 2014.
There were 24 Canadian banks that are subsidiaries of foreign banks
As of September 2013, there were 24 foreign banks with branches in Canada.
Total: <80.
As at December 31, 2012, the 394 credit unions and caisses populaires + odd caveats about Quebec/Desjardins.
FI Total: <500. Compare that with 14000. Coordinating with <500 is much easier than coordinating with ~30x as many entities.
There are also fewer Credit Card networks (Discover has an incredibly tiny footprint, and you aren't likely to steal it).
Population: <35million. vs. <320million (<10x).
The concentration in Canada is much higher, in ways that probably to some extent help.
Wolfram alpha says there are 20x.
Basically, there aren’t that many places for you to try to use your cloned credit cards, there are probably fewer police departments that would need to coordinate about your credit card. Also, because of HST and exchange rates, your stolen dollar doesn’t go as far. You’ll lose money on each exchange (including purchases).
Oh, and for the most part, Canada has deployed EMV. It’s also partway through deploying Contactless EMV (I can’t find a more technical branded name, although it has a consistent logo).
As more information comes out, hopefully we can be illuminated with the brand of POS hardware that was attacked, or details as to the way the track data was ex-filtrated.
It would be nice to have a statement from the manufacturers of the POS equipment involved and what if any communications they are sharing with their customers.
Also wonder if the POS stuff used in DQ shops was mandated or blessed by the corporate entity. Seems like some guidance would have made them liable as well. Perhaps that is why they have no reporting policies, so they can duck the liability for the loss and place all the risk on the mom and pop owners.
The mom and pops probably would not pay for cyber breach insurance.
Does this place the liability and loss only on the card issuing banks, or would the card processor/clearing house also share in the loss?
Thanks for the track data distinction on state breach reporting requirements, I had not considered that the data in question is not considered a breach in most states.
It is already known how the data was exfiltrated. It was sent out using regular http post commands (provided that DQ was hit with the backoff malware). It also has nothing to do with the POS software or hardware (except in the fact that end to end encryption /might/ prevent the attack).
Here is fortinet’s write up:
http://blog.fortinet.com/post/an-analysis-of-the-backoff-pos-malware
Well, with all this stuff going on in so many local establishments its back to cash is king for small purchases. Who wants the hassle of getting burned in one of these stunts. I can get my ice cream with greenbacks in Carvel just as easily.
What ever happened to those pizza stores that got those “Notice of Extortion” letters in the mail. Aug 15 was the deadline to pay. now they’re attacking DQ?, i smell desperation in the SK criminal realm. plain and simple desperation, it smells like it’s time for the script kiddies to go back to school, summers over pizza face. life was so much simpler before teh interwebz. but also we never knew what the truth was. now all will be revealed. i luv it. anonymity just as security is all an illusion. I Scream, You Scream, we all hack for Ice Cream. better hurry, its melting.
Blizzard references = #Facepalm
You’re better than that, Brian!
If you’re going to do it, go all in. Use references like “dilly”, “dipped”, etc.
You guys know that Warren Buffett’s Berkshire Hathaway empire owns Dairy Queen?
Maybe the problem is at the very top.
Now what is strange is that Warren is investing in Burger King. But that’s another story.
International Dairy Queen is still a subsidiary of Berkshire Hathaway, Warren ‘Buffet,’ CEO. It’s doubtful that he or his right hand man Charlie Munger will be happy about this publicity.
I am pretty sure we have fraud items coming in on cards that were used in DQ’s in Kansas.
We believe this is related to the IS&S breach earlier this year:
http://www.bankinfosecurity.com/pos-vendor-warns-restaurant-breach-a-7009
Many, but not all, Dairy Queen locations used them as their POS provider.
FWIW, DQ didn’t think so. Peters said Dairy Queen determined that none of its stores had suffered card exposure from that incident, and that ISS was not an approved point-of-sale vendor for use by Dairy Queen franchisees (the preferred DQ point-of-sale vendor is apparently POSitouch, a Warwick, R.I. based company that works primarily with the food service industry).
I’ve got a relative that owns multiple DQ stores. They are shockingly independent. I’m pretty sure he used a local shop for all his retail computer/networking needs, including POS terminals….and you can be sure he bought the least expensive system available.
Bryan – Is it possible to find what this new black market site is that is selling cards according to state?
Well I’m just relieved that I went to Ben and Jerry’s yesterday and not DQ. And now I need to hit the ATM so I can use cash as much as possible. But seriously – am looking forward to hearing about how the particular vulnerabities of franchisees and how they can better protect their entrepreneurs.
Brian – is there any way to know if one of the DQ’s was in Richfield, MN (2800 W. 66th St.)?
I used my VISA there on August 11th and August 22nd and today that card got the Unauthorized flag when my husband tried to use it at a gas station. Talked to VISA fraud and they said the card was being used at a Kroger’s grocery story in Southland, MI. They of course couldn’t be sure of how the info was stolen, but did suggest we no longer pay at the pump as they’re seeing more cards being stolen in that manner. But now seeing this article it seems it likely could have been connected to DQ.
It was good to see the quick catch by VISA so these thieves don’t continue to benefit, but most frustrating is we have several automated billings to that card each month and each now must be contacted with the new card info when I receive it. Time that could be better spent! And hopefully we have the new card and can contact them before the automated bills come into that account and get rejected. What a pain.
I haven’t seen a list of the breached locations, but that location is one of the two Corporate owned locations.
This happened to me yesterday unfortunately! Someone used my credit card number to purchase $548 worth of WWE tickets! BillGuard warned me of the breach yesterday and had a link to this article. Also TicketMaster called me last night to inquire about this charge. Be aware people!
Hi Kelsey – I’m BillGuard’s community Manager. I’m sorry to hear that you were a victim of fraud and glad we could help.
Would you feel comfortable sharing your story to help others through this 4-min survey: http://bit.ly/1kihMM9? You can also follow up with me at marinabg at billguard dot com. Thank you!