New data gathered from the cybercrime underground suggests that the apparent credit and debit card breach at Home Depot involves nearly all of the company’s stores across the nation.
Evidence that a major U.S. retailer had been hacked and was leaking card data first surfaced Tuesday on the cybercrime store rescator[dot]cc, the shop that was principally responsible for selling cards stolen in the Target, Sally Beauty, P.F. Chang’s and Harbor Freight credit card breaches.
As with cards put up for sale in the wake of those breaches, Rescator’s shop lists each card according to the city, state and ZIP code of the store from which each card was stolen. See this story for examples of this dynamic in the case of Sally Beauty, and this piece that features the same analysis on the stolen card data from the Target breach.
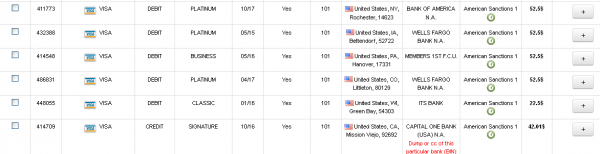
Stolen credit cards for sale on Rescator’s site index each card by the city, state and ZIP of the retail store from which each card was stolen.
The ZIP code data allows crooks who buy these cards to create counterfeit copies of the credit and debit cards, and use them to buy gift cards and high-priced merchandise from big box retail stores. This information is extremely valuable to the crooks who are purchasing the stolen cards, for one simple reason: Banks will often block in-store card transactions on purchases that occur outside of the legitimate cardholder’s geographic region (particularly in the wake of a major breach).
Thus, experienced crooks prefer to purchase cards that were stolen from stores near them, because they know that using the cards for fraudulent purchases in the same geographic area as the legitimate cardholder is less likely to trigger alerts about suspicious transactions — alerts that could render the stolen card data worthless for the thieves.
This morning, KrebsOnSecurity pulled down all of the unique ZIP codes in the card data currently for sale from the two batches of cards that at least four banks have now mapped back to previous transactions at Home Depot. KrebsOnSecurity also obtained a commercial marketing list showing the location and ZIP code of every Home Depot store across the country.
Here’s the kicker: A comparison of the ZIP code data between the unique ZIPs represented on Rescator’s site, and those of the Home Depot stores shows a staggering 99.4 percent overlap.
Home Depot has not yet said for certain whether it has in fact experienced a store-wide card breach; rather, the most that the company is saying so far is that it is investigating “unusual activity” and that it is working with law enforcement on an investigation. Here is the page that Home Depot has set up for further notices about this investigation.
I double checked the data with several sources, including with Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at the University California, Berkeley. Weaver said the data suggests a very strong correlation.
“A 99+ percent overlap in ZIP codes strongly suggests that this source is from Home Depot,” Weaver said.
Here is a list of all unique ZIP codes represented in more than 3,000 debit and credit cards currently for sale on Rescator’s site (Rescator limits the number of cards one can view to the first 33 pages of results, 50 cards per page). Here is a list of all unique Home Depot ZIP codes, in case anyone wants to double check my work.
In all, there were 1,822 ZIP codes represented in the card data for sale on Rescator’s site, and 1,939 unique ZIPs corresponding to Home Depot store locations (while Home Depot says it has ~2,200 stores, it is safe to assume that some ZIP codes have more than one Home Depot store). Between those two lists of ZIP codes, there are 10 ZIP codes in Rescator’s card data that do not correspond to actual Home Depot stores.
Finally, there were 127 ZIP codes for Home Depot stores that were not in the list of ZIPs represented in Rescator’s card data. However, it’s important to note that the data pulled from Rescator’s site is almost certainly a tiny fraction of the cards that his shop will put up for sale in the coming days and weeks.
What does all this mean? Well, assuming Home Depot does confirm a breach, it could give us one way to determine the likely size of this breach. The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May. To put that in perspective, the Target breach impacted just shy of 1,800 stores, lasted for approximately three weeks, and resulted in the theft of roughly 40 million debit and credit card numbers. If a breach at Home Depot is confirmed, and if this analysis is correct, this breach could be much, much bigger than Target.
How does this affect you, dear reader? It’s important for Americans to remember that you have zero fraud liability on your credit card. If the card is compromised in a data breach and fraud occurs, any fraudulent charges will be reversed. BUT, not all fraudulent charges may be detected by the bank that issued your card, so it’s important to monitor your account for any unauthorized transactions and report those bogus charges immediately.




I’m very interested to see any tech postmortem on Home Depot’s security strategy / implementation.
The Target breach postmortem was a fascinating checklist of many smaller bad decisions which contributed to the compromise of an otherwise sound strategy – I wouldn’t be surprised if the same holds true for Home Depot.
Yes, I’ll bet that’s the case too. Taking from something an aircraft investigator told me: Airliner crashes are usually the result of a chain of events, rarely a single point of failure. I believe the principle holds true in IT security as well: Single points of failure are not impossible, but more often than not it’s the cumulation of multiple decisions and actions that lead to a problem. Target’s breach was only one example of such.
I suspect the incompetent management (CIO, CISO), inadequate training and process, and inferior zero-day intrusion detection technology are the root causes of this breach. From what I read in Home Depot’s security engineer job description, they use Cisco’s Sourcefire as IDS, which is not as good as Fireeye’s product. Many firms use boxes from different vendors to hedge risk.
Sourcefire’s AMP beat Fireeye in NSS Labs’ most recent review of network-based anti-malware – in both efficacy and protected Mbps/dollar
Everyone in the business knows that NSS report is crap…probably Home Depot’s CISO/CIO believed so and now both will be fired. Right strategy is to implement solutions from multiple vendors to hedge risk.
…and anybody in the business would also know that “hedging” on Hardware to fix the problem (no matter the vendor) is the wrong move. Using hardware as part of the solution, that makes sense. But to flat-out blame hardware because you were “smart” enough to read their job posting, is completely laughable!
And NSS Labs has been accused on several occasions of essentially extorting companies to pay for the testing and when those companies don’t pay, they get bad results.
I’m not saying one is better than the other because I think the answer is almost always “it depends”, just that people need to take some of these rating with a big grain of salt.
http://www.crn.com/news/security/300072250/palo-alto-networks-fireeye-criticize-nss-labs-testing-firm-defends-itself.htm
Similar thing happend with Tipping Point, I believe around 2009, when they dropped off a cliff with NSS ratings from one year to the next.
Let’s also be clear – there are no magic boxes to prevent breaches. A determined and /or skilled bad guy will get in every time.
Your view on FireEye being better than Sourcefire – or placing any vendor product over another is purely subjective. I can give you many examples where FireEye didn’t catch something and I could do the same for Damballa, Sourcefire, or any other vendor. Placing your trust and faith in any single vendor is a mistake. Also, many of these products produce numerous false positives or label a threat under such a generic name (see FireEye’s generic name for the threat that ultimately brought down Target). Security analysts have a much tougher job than people realize. There are many factors and variables that come into play and no single piece of hardware is going to send you a personalized email telling you exactly what is happening in your environment. Your comment is a little trite.
All the new national security programs have punched holes in all the gear to prevent whatever. Chances are more stuff’s gonna close, more jobs lost and all that. The empty home centers will match the empty casino hotels in New Jersey. Soaring unemployment and more people trying to tunnel into networks to counterfeit plastic cards before they are declined. Cities are going to look like Detroit as the economy faulters. At least all they did was steal the data. They didn’t drive trucks through the doors to loot it.
I would have to disagree that Target had a sound strategy in place at the time of their breach. If best practices in networking and authentication were deployed, I think the attack would have been less successful. Network segregation and multi-factor authentication would have been a good place to start.
That is you’re still assuming that all store P.O.S. systems (more then one in each store) was infected with memory scrapping malware to create a huge database of credit card dumps. This story is still to speculative at this time.
Deep-Web
I blame some of this on the corp culture of not having offensive guys one staff. The corp mold is 8-5/m-f business casual with jeans on a friday. Having an offensive team on staff allows you to attack your own assets, dig for holes, look for things that aren’t locked down like they should be, and constantly test your defensive team and measures. This means attacking from the inside and out. The corp culture doesn’t understand the benefit of this type of action. It can’t be measured on productivity reports. It doesn’t jive with the any ITIL model and certainly goes against everything that change management attempts to stabilize.
Your network, and mine, is constantly being probed and tested. I’m not worried about the stuff my IDS/IPS is catching, I’m losing sleep over the stuff it’s not catching.
I guess you can tell I’m fighting the offensive battle right now. It seems one pentest a year is deemed to be adequate testing.
I agree…partly. I don’t think its so important for your captive ‘bad guys’ to try to knock holes in your systems. I do, personally, think its important to have a small group of people (who do 3rd+ level support on a regular basis) be able to spend days just looking around for things that don’t appear to be ‘right.’ I think the fact that they’re professional troubleshooters already would make them more likely to detect out-of-the-ordinary events. Sure, you can buy an appliance to do this, but in the end, you’re still responsible…at least in the consumers’ eyes.
> Between those two lists of ZIP codes, there 10 ZIP codes in Rescator’s card data that do not correspond to actual Home Depot stores.
Not surprising, as some HD stores serve a large rural area surrounding the city they are located in.
I suspect its actually a case of “Zip code error” in one list or the other (or both), where the store’s zip code isn’t correctly recorded.
Of the 10 Rescator zip codes without a corresponding one in the Home Depot list, 7 have a corresponding Home Depot zip code that is +/- 2 that is not in the Rescator list.
My research suggests 9 of the 170+ “stores with no hacked accounts posted” had hacked accounts posted under a different zip code that is on the “no store in this zip code” list. Only 1 of the 10 “no store in this zip code” entries did not seem to have a ready match in the other column. I know you already figured many of these were matches with maybe an off-by-one typo on the zip code. I think they had bad zip codes because web searches show the store and street address with multiple zip codes.
I did a web search for “Home Depot” in each missing zip code. When I found an hit showing the store ID number, I did another search for “Home Depot #NNNN” only. A “match” had to be Store ID Number and Street Address with different Zip Codes where the second zip code was in the list of “stores with no accounts released”.
This hints the hackers did not always use the Home Depot website to get the store zip codes.
Here is my list of the 9 mappings I am comfortable saying are matches:
02471 – 02472 – Home Depot #2602 (Watertown, MA)
07045 – 07058 – Home Depot #965 (Montville/PineBrook, NJ)
22554 – 22556 – Home Depot #4637 (Stafford,VA)
33445 – 33446 – Home Depot #6325 (Delray Beach, FL)
43082 – 43081 – Home Depot #3825 (Westerville, OH)
43231 – 43229 – Home Depot #3811 (Columbus, OH)
44512 – 44513 – Home Depot #3805 (Boardman, OH)
55420 – 55431 – Home Depot #2805 (Bloomington/Minneapolis, MN)
94550 – 94511 – Home Depot #6678 (Livermore, CA)
The 10th zip code is 15051 Indianola, PA. The web search did not find any store in Indianola nor 15051. The business sites recommend I shop at Home Depot #4152 Allison Park, PA 15101. It is 15 miles away I think.
I am disappointed at not scoring 10/10.
The Home Depot Allison Park|Allison Park, PA 15101
http://www.homedepot.com/l/Allison-Park/PA/Allison-Park/15101/4152
Correction: I had the wrong zip.
If this analysis is correct, does it mean that the card numbers in question were harvested from actual in-store purchasers, and not purchases made at the Home Depot website? Thanks.
You would be correct in that assumption.
Much like the Target breach, card numbers were most likely stolen at the time of transaction from physical point-of-sale stations.
Very interested to see how this all shakes out.
That’s correct. Given past such breaches from this gang, the data for sale very likely comes from compromised payment terminals within individual Home Depot store locations (assuming Home Depot confirms a breach, of course). They could not have obtained this data from hacking the company’s online store.
Really freaks me out to think I could get on Tor right now and maybe buy my own darned numbers back because I needed a couple eyebolts.
This news story is still very speculative at this stage of the game but still good analysis on the topic.
So the cards will get flagged by the bank if they are used outside of the geographical area where the owner lives? So the cards will be used for fraud only locally?
At least that means that my card info is more likely to get used by some local dirtbag, than some anonymous nameless person in Russia… Maybe the local would be easier to catch??
Is there any information about when the breach began?
That information is in the story.
“What does all this mean? Well, assuming Home Depot does confirm a breach, it could give us one way to determine the likely size of this breach. The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May. To put that in perspective, the Target breach impacted just shy of 1,800 stores, lasted for approximately three weeks, and resulted in the theft of roughly 40 million debit and credit card numbers. If a breach at Home Depot is confirmed, and if this analysis is correct, this breach could be much, much bigger than Target.”
Zipcodes are not a very good means of isolating fraud to Home Depot. Large retailers are saturated in any given zip code. In my area you will find Sally Beauty, Michaels, Dairy Queen, Albertsons, and Home Depot all occupy the same zip.
At any given time, banks are dealing with dozens of compromises. The large ones hit print as they sell clicks and ad dollars. Within those compromises you will see overlap of cards from a few percent to 20 to 30 percent. Target was a prime example of a large amount of overlap. One positive from that was when those cards were closed, they also crushed the value of out of multiple other compromises.
In the data provided by the carder site, there is a mixed bag of accounts from multiple known breaches. Accounts that have been closed. So it would appear our seller is inflating his cache of cards to drum up sales and of course create some PR.
The ability to determine the window of exposure is typically based on when a bank sees a collection of fraud events that have coalesced around a specific date. The issue is what compromise are this associated with.
Again many of the accounts with Target were compromised cards from early known breaches, such as Michaels and Harbor Freight and others.
Carder sites have some issues with large merchant compromises because it creates duplicate inventory. Who got to what card first and used it where? Was the card skimmed at a local restaurant and the owner happened to shop at Home Depot the day before? Was the card part of the Michaels compromise and never reissued and the owner shopped at Home depot.
How many consumers used their cards at Michaels, Target, Home Depot, Dairy Queen and Sally beauty all in a similar time frame. With over 500 million cards in market, the answer is millions.
The best and most definitive means of understanding the window and impact is to locate the malware and comb through the logs. Understand its purpose and determine how long it was active.
Because of the raw saturation of compromise and skimming, locating and pinning a compromise on a single entity is not as easy as look, all these cards shopped at the same store.
Just look at your own card statements. How many large retailers did you visit in the last month? How many ATM’s did you use and did you purchase any gas? If yes, you have a very high likelihood you will find your card number sitting in a carder database waiting to be sold.
As the article and banks say: “The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May.”
Not only when the breach began, but when they believe that they plugged it.
They haven’t even admitted that there was a breach – what makes you think they’ve plugged it?
So we’re not sure yet if Canada was affected?
Me too. Canadian Home Depots affected by this? FYI we have postal codes instead of zip codes in format L9L 9L9.
Looks like if you go to the corporate site for the Canadian store, you are forwarded to the US corporate site and the message about a possible breach and ongoing investigation. I’m assuming that they wouldn’t put that link in on the Canadian site unless they felt both American and Canadian cards were affected.
So far nobody is saying – Home Depot included. If recent history is any indication it would be no. Canadian franchises of American companies hit – Target, Dairy Queen, Michaels, Sally Beauty etc were all unscathed.
I asked Brian why he thinks this is so but still no answer…
Not again i cant take it anymore .Give it a break Brian . Please No more credit card breaches . They are so Boring
Just make a list of hacked shops and add names to it as it goes .Easy
There is an unusual amount of discussion, comparing notes, sharing of best practices between Target and Home Depot as they roughly the same size in the same industry yet they are not really competitors. Surprising that they would be caught in the same trap as Target as its likely they discussed the Target breach.
Really? What makes you think Home Depot discussed or even thought about the Target breach? Yes, maybe if their POS Systems are the same they may have thought about it. But I seriously doubt the CIO followed through with minimizing the risk if there was a breach in April or May. If there was a breach and they discussed the matter after the Target incident, then why would it have taken so long to discover the breach.
Me either – I’d bet the lack of leadership in retail corporations – despite all the publicity, about one breach after another, would shock the average layman!
The discussion on the breach so far has focused on credit cards, which don’t directly harm the card holder because fraudulent charges end up eating the credit card company’s money, not the card holder’s. But a criminal using a stolen debit card number can clean out the CASH in a victim’s bank account in a hurry — and that money won’t get returned by the bank in question for weeks while the bank investigates the charges to make sure the card holder didn’t really make the purchases. Theft of cash through debit cards can leave a victim in the lurch with literally no money to pay their mortgage and their bills while their bank is sorting out the mess.
Presumably, one cannot steal money from a debit card account without the PIN.
You can’t if they are straight debit, however most, if not all, debit cards carry a Visa or Master Card stamp making them credit cards as well.
“which don’t directly harm the card holder”
Does being on the receiving end of a debt collector after a fraudulent credit card purchase made nearly a year ago count?
Because that’s the boat I’m in right now.
So… if my zip code isn’t in the list then I am OK?
I’m actually surprised that the CC zip code list matches so well. I’m in an urban area, so there are a bunch of zip codes around my Home Depot, of which only the one that actually contains the Home Depot is listed.
No. The Zip Code is the Zip Code of the store the credit card # was stolen from, not the Zip code of the card holder.
It is my understanding that there are two sets of zip codes: one is the cardholder; the second is the Home Depot location. Brian posted two different links to two separate zip code lists.
The zip codes list for HD Stores is complete. The zip code list for cards is only what was posted – if there’s more batches to be released, then we havent seen those zip codes yet.
So no. If your zip code is not in the card list, you’re not “safe” – just not in the first batch.
Zip code list 1: found on the card thief’s website. He knew which store he got which card numbers from, and manually supplied the zip codes, for the benefit of his buyers.
Zip code list 2: Krebs dug up the zip codes for all the Home Depots in the USA.
There is no list of zip codes of the cardholders themselves. The hacker could not get zip codes from the credit cards.
Ah, yes – thank you, Peter. That makes sense. There was so much confusion in the thread that I got confused myself.
I am confused. I went on this Rescator website to look at the zipcodes they were selling. Are those the zips of the store or the zips of the people who own the card? I particularly went there to see if my zip was there. I didn’t find my particular zip or city but I did find lots of zips and cities right around mine.
Cardholder ZIP codes cannot be ascertained from the card itself, it’s not stored in either track on the magstripe. This does not mean you’re safe, it should be assumed that if you swiped a card in a Home Depot anywhere from April to today, you should closely monitor your card.
I myself am an avid goer of Home Depot, and see the one I usually go to up on the ZIP list. But I honestly can’t remember if I’ve made any swipes since my last card expired at the end of July, I’ll have to pick through my statements and be sure, but I think I may have, oh joy!
Well, after doing an initial search, it appears so far that mine hasn’t hit the market (or perhaps sold, but considering my locale it isn’t likely to look like a good purchase to most).
That’s not to say that’s that, though. They’ve only released the first two “American Sanctions” bases, who knows how many more they have?
Strangely, only one credit card from my financial institution returned, and it’s not mine for sure. But a ton of debit cards on there!
stop
Most all of the small operations that dealt in cash and local credit (business) accounts are gone. Another big loss. The crooks are idiots and can still defeat the security systems?
The following statement isn’t really true:
“A a 99+ percent overlap in ZIP codes strongly suggests that this source is from Home Depot,” Weaver said.
First rule of stats: correlation does not imply causation.
Most likely there are other big chains that often share the same zip code as Home Depot (like Walmart, McDonalds, etc.) which would probably also have a 99% correlation with the zips listed in the list. While it does add to the evidence, it is far from implying that Home Depot is THE source.
Using unverified sources on the web, it appears there are 2597 zip codes in California. There are about 250 Home Depots in California. That’s a lot less Home Depots than zip codes. A 99.4% correlation is suggestive.
You’re actually confusing two concepts in that statement. Correlation not implying causation is a concept of logic, and then whether Walmart and McDonalds would have the same correlation to the same list is a question of probability, not logic.
Good points, but @StatsOff take was mine as well. Location, location, location aren’t the first three rules of retail for nothing…and plenty of companies have follower strategies.
If you didn’t already “know” Home Depot was the target, I bet there are 1/2 dozen other possibilities.
If there was just a few, I’d agree with you. But we are talking an almost 100% match (and of the 10 mismatches, most have close-matches, and at least one has an exact match according to Google Maps rather than Home Depot’s store finder or the HD Zip code list).
And, as importantly, only 170 HD Zip codes are not represented: the overlap is almost complete.
Even just a spot check of the little patch where I live shows distinction: Lowes is a different zip code set than Home Depot. As is McDonalds. As is Target. As is Wal*Mart, etc…
To rule out other close-by retailers (if that was desired) it may be best to locate the most remote Home Depot on the list and pull up that map.
Whatever method(s) at least four banks used to map back to previous transactions at Home Depot hasn’t been proved wrong yet.
Nobody suggested causation. There are 40,000+ ZIP codes in the US. Work the numbers. It’s not happenstance.
correlation part of statement: “A a 99+ percent overlap in ZIP codes”
implication part of statement: “strongly suggests that”
causation part of statement: “this source is from Home Depot” (i.e. since they are highly correlated, Home Depot’s system was the cause/source of leak)
The main point of my comment was that there might be other stores that highly correlate with this list if they were tested. If I could get the list of all Starbucks or McDonalds or Walmarts, I’d happily test them myself out of curiousity. Wasn’t trying to insult anyone – just stating that statistically speaking, the statement wasn’t quite right.
Ex: If one sees a 99% overlap in increase in child’s shoe size with increase in child’s vocabulary, one would not say that it strongly suggests that the increase in vocabulary is the source. It could be a lurking variable… i.e. increase in age of child. Similarly, the 99% overlap may not be that Home Depot is the source, but that Home Depot happens to be in a popular retail zip code.
Let me reiterate I’m not saying Home Depot is NOT the source, I’m just saying that the correlation is not enough on it’s own.
I think what Pete L. might better say what I was trying to state, which is “If you didn’t already “know” Home Depot was the target, I bet there are 1/2 dozen other possibilities.”
I guess Rescator doesn’t list the full credit card number on the site because that would be a violation of PCI.
If they were smart they would have Cyber Liability Insurance coverage. remember dont think tech….think money and coverage
Cyber Liability Insurance is great but it doesn’t protect your brand image.
Cyber liability insurance only covers part of the costs associated to a breach. Target (only) had $100 million in coverage ($10 million deductible). Their costs related to the breach reported so far were $148 million.
Target’s lost sales related to the breach are much harder to measure. Some customers don’t trust them anymore, others still shop there but won’t use a card to make a purchase (which limits transactions to the cash in their purse/pocket). Same store sales are still down year-over-year. This holiday season will surely see news reports of “One year since the target data breach …” that will reinforce any lingering fears.
Target isn’t past it yet. Depending on how Home Depot handles it, and the details about how the breach occurred, will certainly play a significant role in their customer’s confidence. Home Depot doesn’t have the assortment of competition that Target does, so Home Depot may not see the same drop off in sales. And as Garet intimated, a cyber policy won’t help with lost sales.
I know in my area Home De-POT has a LOT of competitors – Menard’s, Westlake ACE hardware, just to name a few. Now I wouldn’t doubt ALL retailers have something to worry about in this market – but it seems Home De-POT goes out of their way to hire the most incompetent workers I’ve ever seen, and fire the only sales staff worth keeping. So I’m not worried about Home De-POT, I actually hope they go to POT!!
Brian, or anyone, know what cards have been affected? Is it just Visa or all? I’m thinking of calling discover and asking for a new card.
You should be able to go to the Discover Card site and set alerts for your card, although Discover goes out of their way to explain to me that their card has automatic fraud detection, and is the best thing since Brink’s Security.(/sarcasm) I went to all my card sites and set as many alerts as would indicate suspicious activity very quickly. I dropped Discover as soon as they got rid of Online Secure Account Numbers, but they did seem to have it together on some other features.
So far, all the posts are focusing on the breech. As a senior who does NOT understand the “tech” side of this at all, i.e. how this is accomplished, there seems no way that the average person can avoid being an unsuspecting, unavoidable victim…is there?
Honestly? No.
For the longest time, the big fear was credit card data being stolen online. Yet, as we see with these breaches right now, The Big Thing is to infect Point of Sale machines.
And nobody goes up to the counter asking what type of POS machine is being used before bringing out their credit card.
I’ve been waiting for brick & mortar store attacks for years; I’m really surprised it took this long. I used to ask local retailers all the time, if they really knew if the POS system was secure. After getting a deer in the headlights look from them, I generally gave them something to compare to, in the news, before such things became prevalent. There was always a good example to make a parable out of.
To put this Home Depot breach (possible breach) in another context: What would be a bigger retail POS breach that MAY happen, Wal-Mart, Costco, Kroger?
https://nrf.com/sites/default/files/styles/infographic_662xnone/public/HighlightsWorldRetailersChart_0.jpg?itok=r_mRDOLg National Retail Federation: 2 of 5 of the U.S. based companies ranked by highest retail revenue, have been breached (if Home Depot is indeed breached)
Looks like Home Depot knew about the breach this weekend, see Robert X. Cringely’s blog
http://www.cringely.com/2014/09/02/home-depot-smoking-zip-zap-machine
thank goodness for Mr. Krebs
And these guys are still in business?!
http://faziomechanical.com/
Waiting to hear if Home Depot was also a network they had remote access to, as a supplier….
Nice, thanks Brian!
the HD that I frequent uses Ingelico POS. from what I can tell it is running on WinXP of some variant.
My HD zip is included in the list above.
Thanks for your great work Brian! What can you say about the vulnerability of cash accts vested with trading firms like Etrade or TDAmer, OptionsHouse or TradeKing? Have they ever been hacked? Seems like a natural & amazed have not heard of them getting hacked.