New data gathered from the cybercrime underground suggests that the apparent credit and debit card breach at Home Depot involves nearly all of the company’s stores across the nation.
Evidence that a major U.S. retailer had been hacked and was leaking card data first surfaced Tuesday on the cybercrime store rescator[dot]cc, the shop that was principally responsible for selling cards stolen in the Target, Sally Beauty, P.F. Chang’s and Harbor Freight credit card breaches.
As with cards put up for sale in the wake of those breaches, Rescator’s shop lists each card according to the city, state and ZIP code of the store from which each card was stolen. See this story for examples of this dynamic in the case of Sally Beauty, and this piece that features the same analysis on the stolen card data from the Target breach.
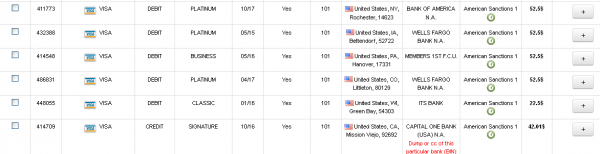
Stolen credit cards for sale on Rescator’s site index each card by the city, state and ZIP of the retail store from which each card was stolen.
The ZIP code data allows crooks who buy these cards to create counterfeit copies of the credit and debit cards, and use them to buy gift cards and high-priced merchandise from big box retail stores. This information is extremely valuable to the crooks who are purchasing the stolen cards, for one simple reason: Banks will often block in-store card transactions on purchases that occur outside of the legitimate cardholder’s geographic region (particularly in the wake of a major breach).
Thus, experienced crooks prefer to purchase cards that were stolen from stores near them, because they know that using the cards for fraudulent purchases in the same geographic area as the legitimate cardholder is less likely to trigger alerts about suspicious transactions — alerts that could render the stolen card data worthless for the thieves.
This morning, KrebsOnSecurity pulled down all of the unique ZIP codes in the card data currently for sale from the two batches of cards that at least four banks have now mapped back to previous transactions at Home Depot. KrebsOnSecurity also obtained a commercial marketing list showing the location and ZIP code of every Home Depot store across the country.
Here’s the kicker: A comparison of the ZIP code data between the unique ZIPs represented on Rescator’s site, and those of the Home Depot stores shows a staggering 99.4 percent overlap.
Home Depot has not yet said for certain whether it has in fact experienced a store-wide card breach; rather, the most that the company is saying so far is that it is investigating “unusual activity” and that it is working with law enforcement on an investigation. Here is the page that Home Depot has set up for further notices about this investigation.
I double checked the data with several sources, including with Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at the University California, Berkeley. Weaver said the data suggests a very strong correlation.
“A 99+ percent overlap in ZIP codes strongly suggests that this source is from Home Depot,” Weaver said.
Here is a list of all unique ZIP codes represented in more than 3,000 debit and credit cards currently for sale on Rescator’s site (Rescator limits the number of cards one can view to the first 33 pages of results, 50 cards per page). Here is a list of all unique Home Depot ZIP codes, in case anyone wants to double check my work.
In all, there were 1,822 ZIP codes represented in the card data for sale on Rescator’s site, and 1,939 unique ZIPs corresponding to Home Depot store locations (while Home Depot says it has ~2,200 stores, it is safe to assume that some ZIP codes have more than one Home Depot store). Between those two lists of ZIP codes, there are 10 ZIP codes in Rescator’s card data that do not correspond to actual Home Depot stores.
Finally, there were 127 ZIP codes for Home Depot stores that were not in the list of ZIPs represented in Rescator’s card data. However, it’s important to note that the data pulled from Rescator’s site is almost certainly a tiny fraction of the cards that his shop will put up for sale in the coming days and weeks.
What does all this mean? Well, assuming Home Depot does confirm a breach, it could give us one way to determine the likely size of this breach. The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May. To put that in perspective, the Target breach impacted just shy of 1,800 stores, lasted for approximately three weeks, and resulted in the theft of roughly 40 million debit and credit card numbers. If a breach at Home Depot is confirmed, and if this analysis is correct, this breach could be much, much bigger than Target.
How does this affect you, dear reader? It’s important for Americans to remember that you have zero fraud liability on your credit card. If the card is compromised in a data breach and fraud occurs, any fraudulent charges will be reversed. BUT, not all fraudulent charges may be detected by the bank that issued your card, so it’s important to monitor your account for any unauthorized transactions and report those bogus charges immediately.




I see no mention of what payment methods the criminals accept on rescator. Ten years ago, had any of the criminal goods been sold in exchange for e-gold that would have been the major thrust of the article, even if >90% had been transacted using other media.
usually paid in WMZ, BTC, or perfectmoney. WMZ is Russian aka no data retrieval from less-than-fraud-friendly countries’ LE, btc is not entirely untraceable even WITH tumbling but it works well enough. Perfectmoney is just fraud friendly too.
Last time I was in Home Depot, it appeared that the POS terminals were still running Windows XP. I imagine these are embedded systems and still supported, but the technology is still from the year 2000-2001 time frame. Not to say that a more recent OS is not vulnerable, it does show that there is a lack of strategy by C-level types when their companies are running critical systems with 14 year old technology that we know wasn’t built with strong security in mind. I wonder what the risk assessments were saying and who was reading them (assuming they were taking place).
This guy, Rick Mitchell
http://www.bradreese.com/blog/8-20-2013.htm
And Cisco, and FishNet.
And apparently Tammy Moskites
http://www.linkedin.com/in/tmoskites
I saw a self check out reboot at Walmart, not so long ago, it was XP.
Maybe this explains, why PCI-certificates are not worth the paper they are printed on:
You could get the PCI certificate for a couple of hundres bucks, though we have to state that home depot does so many transactions, the only accessible PCI-SAQ for them would be level D (the most “difficult”), but as you can see – getting the certificate and implementing the stuff properly are two different things :-/
Regards
HD’s transaction volumes are high and they would have had to undergone a full onsite audit and filed a report on compliance. This is far more rigorous than the self-assessment forms you mentioned.
PCI isn’t particularly pretty and it’s not without problems, but we would have totally hemorrhaged by now without it.
Yeah, reading through Target’s statements about their theft, banks eat most fraud but for high-profile data breaches the card companies say a merchant is suddenly not PCI-compliant, even if they were ruled PCI-compliant months ago. Then the card issuers threaten legal action enforcing their contract until, of course, a settlement is reached.
So, those so called settlements typically net 7 cents on the dollar. Not quite earning anywhere near the losses incurred. The other settlements are typically going to MC and Visa for the name recognition damages. Those don’t get shared with the issuers.
To top it off, these largest companies are suing Visa and MC, because they say that the interchange they pay is too high. Has anyone seen lower prices at Walmart due to their settlement with MC and Visa – don’t think so – straight into their pockets at the cost of the issuers.
The reason they won’t spend the money for better security is because it would come out of THEIR share. So they get the big bux at the end of the year and the consumer gets the shaft. Nothing new there. You don’t expect them to give up those big bonuses to keep our info safe, do you? Consumers are faceless to them, they never see them, hear from them, or anything to personalize them. You are just a card number. Nothing more, nothing less. So they get hacked, oh so sorry consumer, we will try and fix that. Yeah right.
and you don’t think PR scare is enough to affect gross profit? Fraud makes people weary, makes them think it’s not secure. If it didn’t come from them to re-imburse, assuming this data breach IS legit, it’ll come out of their customer base.
not sure if this’ll show since it’s in response to a comment awaiting moderation but…
….sorry, I meant “wary,” NOT “weary.”
Actually I think you were right the first time.
I know I am weary of the poor security of major retailers and other large enterprises.
Yes, people are weary of having their cards breached. But the true cost goes to the card issuers – not the customers. The issuers pay for all the fraud – Visa and MC should rewrite the rules – if you get breached – you pay for the fraud.
The CC companies should rewrite the rules you say? There’s just one little problem with your hair brained idea. It’s called federal law.
Really – hair brained – that’s what is happening with EMV – if you aren’t EMV capable by X date – then you bear the losses…
Look it up – Banks have until some date to have their cards as EMV, and merchants have to be EMV capable by another date. I think its Oct 2015 – but I would have to look it up.
FWIW, American Law has a category called “Contract Law”:
http://en.wikipedia.org/wiki/United_States_contract_law — yes, it’s really per state Contract Law, but that’s OK, Visa and MasterCard can afford lawyers to represent themselves in all 50. Besides, most groups are probably incorporated in Delaware anyway 🙂
Each merchant more or less ends up w/ a contract to each credit card vendor. If it isn’t direct between the merchant and the vendor, there may be a middleman or two. But it isn’t particularly hard for Visa/MasterCard to write a line into their contracts w/ the middlemen to demand something that gets included in the contract between the middlemen and the vendors.
I’m pretty sure the EMV liability shift was implemented more or less this way.
Why do you think the interest rate on the best credit cards is starting at 9% and goes up to about 35%? That is where you are paying for this theft at. And don’t tell me to pay off my credit card each month and I won’t be charged, I do, but most people can’t if they have a large purchase like a refrigerator they need because their old one broke. You are really ignorant if you think those costs are not passed along to the consumer in some shape or form by both the retailer and the credit card company.
You have a good point – but your model only considers credit cards. What about the other half of the equation – which is debit cards. There is no interest charged to consumers on debit cards – because it isn’t a loan…
All costs eventually get passed onto the consumer. But in this case – for debit cards – that cost is truly carried by the issuer. There isn’t a way to directly pass that fraud cost onto the consumer. Banks have to make a profit as well – we are businesses. We can’t give everything away for free.
Very well said.
Why is “rescator” not shut down?
Because what they’re doing isn’t illegal where they are. Most countries hate “fat, ugly Americans” so even in countries where it is illegal, its VERY hard to get officials to act.
The website was down for a while yesterday, it was defaced, if I’m not mistaken Brian didn’t they say something to you?
nevermind, that was old…
I see rescator has released 3 more bases of American Sanctions.
Rescator is protected by a San Francisco-based startup that calls itself CloudFlare. Attorney General Eric Holder told a Senate Committee in January that he would do something about the Target heist. The Justice Department could have shut down Rescator’s use of CloudFlare with a court order, but don’t expect anything from them now. My theory is that Obama is afraid of Silicon Valley.
A class-action lawsuit against Target is in the works, with hungry law firms behind it. They should think about adding CloudFlare to the list of negligent defendants. CloudFlare has millions in the bank from venture funding.
See: http://www.crimeflare.com/carders.html
Cloudflare is just providing the dns service, via a distributed system rather than a single server. Unless you’re planning to “shut them down” by DDoS’ing the site, that isn’t generally the the way you’re going to go. The DNS service is only an issue because the domain registrar is uncooperative.
Since Cloudflare’s TOS includes the following, I’m guessing that the Secret Service is working in cooperation with Cloudflare to investigate the people buying and selling:
“CloudFlare reserves the right to investigate you, your business, and/or your owners, officers, directors, managers, and other principals, your sites, and the materials comprising the sites at any time. These investigations will be conducted solely for CloudFlare’s benefit, and not for your benefit or that of any third party. If the investigation reveals any information, act, or omission, which in CloudFlare’s sole opinion, constitutes a violation of any local, state, federal, or foreign law or regulation, this Agreement, or is otherwise deemed harm the Service, CloudFlare may immediately shut down your access to the Service. You agree to waive any cause of action or claim you may have against CloudFlare for such action, including but not limited to any disruption to your website. You acknowledge that CloudFlare may, at its own discretion, reveal the information about your web server to alleged copyright holders or other complaintants who have filed complaints with us.”
Cloudflare is a proxy that allows users to hide their actual IP. I’m sure anyone involved in this type of activity uses multiple proxies, making it difficult, if not impossible, to locate and identify them…
*ahem ahem ahem* russian bulletproof *ahem ahem ahem*
to answer others’ complaints about cloudflare, it just offers ddos protection, don’t flame THEM because some site uses it. They protect BOTH good and bad. Just like tor, you can’t save the good without also saving some bad. Yin Yang.
Hosting the likes of rescator .cc, we’ll see.
https://www.cloudflare.com/terms “CloudFlare, Inc, a Delaware corporation” top paragraph, with contact information of San Francisco CA, as stated on the right side of the page (and professional sources).
The registrar is based in Russia (http://whois.domaintools.com/rescator.cc)
Bulletproof doesn’t mean always bulletproof. Too me, “bulletproof” only means “bulletproof until no longer bulletproof”. There are instances of “no longer bulletproof” hosters.
For those that are questioning the validity and probability and such, all the data that Krebs is using is circumstantial, however, if his contacts at the credit card companies (which started this) are correct then they know where it happened and it isn’t just correlation vs causation.
When credit card companies, or issuing banks, see fraudulent charges they do what is called Common Point of Purchase (CPP) analysis to determine where the card was stolen from. Not all cases have a CPP as not all are stolen via skimming. What they are looking for is what is the common place of purchase on a group of stolen cards. So say they have 1,000 cards reported stolen, they run computers to analyze all prior purchases and then attempt to locate the common charge prior to the fraud. Not all will have a common as not all are stolen the same way, however, when a breach happens they will find a CPP, it can take time or it can be quick, it just depends on the size of the breach and how the thieves are selling or otherwise using the cards. Sometimes those stealing are trying to outsmart to keep their skim off the radar so they will make small purchases prior to the large purchase at other ‘common’ locations, this is to attempt to thwart the computers into not finding the real CPP and potentially grabbing the wrong location or just not finding the CPP due to the all the commonality between the cards. It is really a game of cat and mouse as once a CPP is identified the card companies and issuing banks can act on it and shut down the cards, the longer it can remain out there the better for the thieves.
For all the comments on who pays for it, the merchant at the end and thus the consumer. If a stolen card is used and the goods are successfully delivered or purchased then the merchant that completed that transaction gets the charge back. The banks themselves and the credit card companies are isolated by the merchant rules and thus they play little part in the financial impact. The issuing bank is liable for the card reissue which is why they are sometimes reluctant to do a mass reissue as not all stolen cards are used and they incur ~$25 per each re-issue. The company that cause the breach is on the hook for penalty and fines under CISP/PCI compliance that can be fairly substantial, these go to the card companies (Visa/mc/amex) and I suspect are shared back to the issuing bank. (http://usa.visa.com/merchants/protect-your-business/cisp/if-compromised.jsp)
In the end, it is the average consumer that ends up paying the price, between the end retailer losing on the chargeback.
Chip and PIN is great, but it isn’t the end, once US is on it then the hackers will simply figure out how to hack it, there is little reason to hack it now when you can easily steal swipe data.
Peter – you are correct on the CPP part of your post, but not in regards to who pays for this. It is the card issuing banks that brunt the majority of the losses. When a card# is purchased, it is most often counterfeited and a duplicate card is created. If that card is used at any random merchant in person (the transaction is “card present”) and not able to be charged back by the card issuing bank when the real customer indicates the transaction is not theirs. So the card issuing bank must give their customer the back the amount of the fraudulent purchasse and then cannot charge back the transaction to the merchant who accepted the counterfeited card because it was a “card present” transaction. That is not the case for online transactions which can be charged back.
True – We run with both card present and not-present. 99% of our charge backs are in not-present so I think in those terms most of the time. While card swiped of counterfeit card is possible everytime (5) my card has been compromised the fraud was all online purchases. I am not a good sample but based on the amount of fraud attempts we see (online retail) I don’t think most are counterfeiting the card, I great deal might be, but there is a ton of online transactions, we saw a huge uptick after the Target release and have seen it again this week of attempt orders caught by our fraud protection.
on the contrary, I work at a bank and 99% of our fraud is card present and therefore we cannot charge back. We see fraud rings from all over the country purchasing these cards and then buying gift cards with the counterfeited cards (Just as Brian explains). We end up taking the loss.
If 99% of your fraud is card present then why is card present (swipe) merchant fees up to 500bps lower than not present? Something isn’t jiving. If your risk model is accurate shouldnt it be accounting for the increased fraud on card present?
I said 99% of our fraud not 99% of our charge backs (2 different things). When you talk merchant processing of credit cards that’s entirely different and a whole other discussion. when we process online transctions for a merchant, the risk of that transaction getting charged back is much higher with an online transaction due to the customer not getting what they were promised, not geting “remembering” they ordered the product, etc. Also interchange rates are different for those transactions so the fees are higher. Talk to Visa about that one. the point I was trying to make is that when these cards are sold on the black market, crime rings mostly purchase the cards, reproduce a counterfeit card, purchase gift cards or other easily sellable items and those transactions are not able to be charged back to the merchant so the card issuing bank eats the costs of not only replacing the cards but also the fraud itself.
I’ve had two fraudulent transactions in the last 20 years. One was 12 years ago. It occurred when my debit card was, I believe, skimmed at a restaurant. The info was sold to a group in Australia and they proceeded make a clone card, verify it with a quick, reverse small internet charge, and go to town. Spent over 5k in a few jewelry stores in a couple hours. Bank didn’t catch it. I did purely by accident as I was checking my account for a wire I was expecting and caught it only hours after the transaction. I had the bank shut it down but the charges, which were pending, went through anyway and I couldn’t file a claim until they posted a few days later – which they did. The bank refunded the money a week later but what if I hadn’t checked the account? This could have gone on a long time and the first time I would have found out could have been when the account was cleaned out. I’ll never understand how a bank could allow a charge to go through on a card less than 8 hours after I had bought gas in the USA using said card. Perhaps fraud detection has improved since then.
The other fraudulent charge occurred on a debit card early this year. It was for $100 at an RV camp site. Apparently it was manually entered by someone for a weekend stay that just had the card number. Closed the debit card and had it re-issued as only an ATM card.
Never had any issue with credit cards. I no longer use debit cards for purchases. I have 5 credit cards of differing flavors. Backup is good these days.
Admiral Obvious here to help. “I no longer use debit cards for purchases.” Now spread the good word. A debit card is a “key” to your checking account and therefore should only be used at your bank. Best of wishes.
Interesting that Brian deleted my comment which spoke to CPP and how card companies know about a breach and where it started….did it hit too close to home or something? Too many facts in it? Very odd sir.
Is there canada postal code listed on the seller advertisment? There is home depot store here also
Canada was hit and other Dumps including canada ones are apparently being sold on another underground card shop
All the articles I’ve seen just say they’re looking into Canada and the zip code file is just that US zip codes. Anyone have anything more definite?
they are being sold in an underground card market… I am not willing to say the name of the site BUT… they claim to have over 100,000 canada cards some of them contain city they are USED/from
Is there no chip and pin in Home Depot stores in Canada
Yes we’ve got chip and pin here in Canada at home depot. We also have paypass or paywave or whatever they call it where you dont need a ping and which works contactless. Each transaction is limited though. I think its $60 or sth. Like that.
Are pins part of the package of ca cards?
Most Canadian Issued credit and debit cards are now EMV. There may be a few leftovers from smaller financial institutions.
Debit in Canada is a bit different. Interac has the lion share of that market and all Interac Debit requires PINs (has for decades). Most Interac cards are not credit cards. All Canadian ATM encrypting pin pads and debit terminals have been certified by testing labs for as long as I can recall.
EMV has problems too. Depending on the bank the PIN is actually on the card which may not bad such a great idea. Pinpad overlays are not unknown and until not too long ago (well many years by now, I’m getting old) EPPs were only using 3DES. Also ATM manufacturers have software for remote key management for EPPs. Not the brightest idea on the planet either but it sells.
And Home depot has those custom terminals not standard ATM EPPs. Who knows where the encryption starts and whether malware can actually just grab pin data from memory before it gets encrypted. Dumb designs exist and I’ve never trusted these custom terminals especially the ones that have software button pin entry instead of hardware buttons.
Brian,
Great reporting, as usual. One side note: Banks are being hammered for losses related to credit and debit card theft. Overwhelming would be an apt description. And hiring more people is a losing proposition. (spending more money to lose more money is not a good business process)
Several things are going to happen and are likely happening:
1. Fee free cards are going to disappear to all but the best customers. Expect your existing cards to have hefty fee increases to try and stem the red ink.
2. IF, big if, we go to POS two step verification as a mandatory process (I would love using a cell phone while I pump gas….) to try and stop some of this, I fully expect we the consumer to be penalized if we choose not to. This problem is now in the hundreds of billions of dollars world wide, expect more dramatic action by the financial institutions.
3.I expect that the section of the most recent Fair Credit Act that eliminated partial bank chargebacks (fees) to consumers for fraudulent charges to be repealed if they don’t follow safe practices.
4.In our society, sadly, there is a pile on effect going on with less scrupulous people taking advantage of an overtaxed credit card system. “Shadow” chargebacks for fraud were already there, since the cost for a merchant to try and defend against a chargeback is so high, and are now getting worse, with no real solution.
While some of this may seem unfair, I feel it reflects the gravity of the situation in a modern society which for all intents and purposes relies on credit cards as a way of life. Not just consumers, merchants as well. Having us all go back to cash and credit lines isn’t a viable solution in our need for instantaneous transactions.
Unless we want to see a revival of good old fashion mail order for goods, expect that we will have to curb our “freedoms” in trying to deal with cyber criminals and the inability for anyone regardless of budget to truly build a functional but unhackable IT system.
Of course the next giant sunspot burst might take care of all this…. 🙂
The gas pumps have signs saying to leave the phone in the car.
Please adjust your sarcasm detector 🙂
Two step verification with a cell phone is whats already being done for online banking and in something cases for your online shopping when 3D (MC Securecode, Verified by Visa etc.) is used.
All that does is that mobile malware increases as they now need access to your sms.
Does anyone know if there is a time line on this yet?
On the surface, it would appear the Home Depot issued credit cards would be a little safer – but only if HD tightens up their online ordering with their cards.
There is also not much the actors can fraudulently order from HD online that would be easily moveable – washers & dryers?
You and I end up paying one way or another. Either higher prices at HD or higher fees at the bank. Or both.
The majority of banks will eat the loss out and take it out of hide of any profit projections. What these loses do is slow down or completely stop investments in improved technology. Competitive pressure keeps fees low. The marginal net profits for most banks is very low and there is a lot of pressure to satisfy shareholders expectations.
Banks are getting hammered by regulatory costs and increasing competitive pressure from non-bank entities, such as Walmart. Raising fees and interest rates is not an option.
One good example of this is the lack of investments in NFC payments and a stronger push towards digital payments. Billions of dollars are being spent on there legacy environments to ensure they are compliant. Those dollars with fraud losses make if extremely difficult to support new technology.
The bill for the migration to Chip will be well in excess of several billions of dollars of for the industry.
So, I agree in the end we all pay as capital that would have otherwise have been spent on improvements and lower rates and better products is now being shipped over seas to criminals.
Brian, I follow your website every day and always trust your knowledge and dependable advice. I saw your name mentioned very favorably on CBS News the other night, a sign that your expertise is widely recognized. Way to go, Brian!
Too bad NBC refuses to acknowledge Brian.
I wonder if this guy Rick Mitchell helped design the systems that got hit: http://www.bradreese.com/blog/8-20-2013.htm
Also wonder about this gal who left right before:
Tammy Moskites, she has received many accolades, should we reconsider the value of her services now that it is apparent that someone failed at some point to make things work properly
Moskites left a while ago – 3 years is a long time…. Should be more an indictment of potential staleness since she left.
Unless of course they were still using a system she blessed as safe and secure with no ongoing remediation work or plans for keeping things in order. You are right though three years would be a long time to sit on your hands and collect pay for doing nothing more more than outsourcing your security and hoping it all goes well. Given the above comments about the “F” grade on the commerce site it appears that HD management considers security to be an unfortunate after thought that costs them profit.
Looks like they were asleep at the helm. Too funny the stock went up after the news, shareholders are fickle creatures.
Perhaps Ms. Moskites would comment on her role at Home Depot and the stunningly clever technology she left in place when she moved on.
As usual great reporting Brian. I concur with all the positive accolades in this comment section.
Interestingly, the one retailer (at least one that I go to often, perhaps too often) that seems to have an approach that is working is Starbucks. Anyone that uses their phone app can attest to the simplicity of wiring up a virtual account number to your bank or credit card and then using the pay scanner to pay for your favorite latte. No credit card used at all (at least not physically). While I won’t state there aren’t any possible shortcomings or vulnerabilities in their solution, they are on the right track and something many retailers should take note of.
Why do you ask? Well two things that are different then traditional card scanning:
You are not hitting a large line of credit or bank account full of money and your are removing the potentially unlimited access that a credit card or bank debit card number has. I set up the app and account to only hold around $20, the worst case scenario is I am buying about 4-5 lattes for the script kiddies in Moscow. The app only works at Starbucks too so its not like it will work everywhere.
Now in a perfect world, I wouldn’t advocate or want a separate app for every store I walk into so a universal app would be best. But now we are walking back into the same pitfalls CC’s and even the chip based CCs have.
One way to solve this would be to make the virtual card number dynamic and make it a one time use card number. So coupled with the small amount of money in the virtual account, you have extremely limited exposure both in $$’s at risk and time of use on the card since its a one time use and the retailer would be the one hitting it first.
Now at the end of the day, one could argue the POS malware could just intercept and immediately go and use the virtual CC number, but in order to do so it would make a lot of network “noise” by sending the number to a C&C site. It would basically have to do exactly what they don’t want to do and call attention to themselves. The POS systems would light up like a Christmas tree.
I am sure there are ways to poke holes at this approach but its pretty clear that the standard approach retailers and banks are taking and us as consumers are contributing to or accepting, does not work anymore.
Except that they stored the information in that app in clear text. Plus, if they get the registers like this, who is to say they cannot gain access to where you stored the information for the EFT to take place. At that point, you would have your account drained, and there would be no safe guards in place to help you recoup that money at all. Maybe a lawsuit, but you would be years out before that would be settled and then I imagine you would get pennies on the dollar for your losses. Sad world, but I think I worry more about apps that have the ability to perform an EFT than a credit card. Most are insecure. Heck, most banking apps were insecure for quite a while (never checked the SSL fingerprint / serial’s), and I would imaging quite a few still have major holes in them.
Thankfully the last time I used my card at a Home Depot was in early February.
This is nothing new. My bank account was debited over $1600.00 last year for two gift cards at two Home Depot stores in Texas. Apparently, someone got a hold of my debit card number at Home Depot. My bank credited my account, but Home Depot could not have cared less. One of the managers at the Katy, TX store was even upset that someone gave me his name to contact. I no longer shop at Home Depot.
How long did it take for your bank to credit your bank account after you first contacted them? The thing I fear about Debit vs. Credit cards is you might need to pay some bills from your checking account before things get sorted out. At least with a credit card you have the ability to control your credit rating impact by just not paying that credit card bill in full if there was debate on one or more fraudulent charges. (I stopped using a debit card years ago after some 3 letter agency guy said he never uses one any more…)
“It’s important for Americans to remember that you have zero fraud liability on your credit card”
Brian: And what about debit cards? Please update your article to clarify.
In a breach situation like this – pretty much zero liability.
Qualys gives Home Depot website an F
https://www.ssllabs.com/ssltest/analyze.html?d=https%3A%2F%2Fsecure2.homedepot.com
WOW, that F is unbelievable! The secure2.homedepot.com server is for online checkout.
That SSL 2.0 flaw has been known for many years and is very easy to be fixed. It seems that nobody in the THD security team is paying attention. Hopefully someone there reads this comment board and gets it fixed ASAP.
The SSL2 and the weak ciphers have also been mandatory PCI fails for many years. Their external scanner should have failed them and the auditor who reviewed the years scans should have failed them. If it’s outsourced then the “them” above would be the 3rd party.
So with this information (SSL 2.0 etc), can banks claim that Home Depot is not PCI compliant and thus liable for the fraudulent charges resulted from this breach? The banks are suing Target for about $18 billion damage and I am pretty sure they are collecting evidence now.
This is a 2009 article talking about SSL2 and weak ciphers compliance to PCI requirements. Clearly, by this minute, the Home Depot online checkout server is not PCI compliant. In my opinion, Home Depot will suffer significant financial damages due to this breach despite their lighthearted PR.
http://blog.zenone.org/2009/03/pci-compliance-disable-sslv2-and-weak.html
Click the SSL Labs site link again, now got this message “This site’s owners requested that we do not publish their assessment results”.
Haha, finally someone at Home Depot noticed the security flaw.
as of now Qualys has this posted: “This site’s owners requested that we do not publish their assessment results (more info)”
SSLv2 and 40 bit ciphers two months after they were cracked wide open. But they are using an Extended Validation certificate! Nice! THAT makes it all better.
And now they’ve requested that SSL Labs not show the test results.
Quoting Office Space: “Thumbs up their asses, thumbs up their asses.”
Is it possible the 10 non-overlapping zip codes are Home Depot Inc. subsidiary stores or stores that somehow connect into the POS system at Home Depot? HD does have several other smaller stores that they own that may be in those zip codes.
I was wondering if cards are swiped on site when goods are delivered to customers.
Also, there is the possibility that there are Home Depot stores in close proximity to “big box” retailers that are attractive to rescator’s customers, but which happen to be on the other side of zip code boundaries. It would be better marketing for rescator to list the adjaccent big box store’s zip code, rather than the Home Depot zip code.
See the insider trades, they knew on 8/25/14
I doubt that. IMHO, they genuinely had no idea about the breach, have no idea even now about what really happened.
I’ve been reading up on the new electronic credit card “coin” What do you think of it?
Does anyone know how/when/if we can find out what the other 900-some-odd businesses also exploited by this malware are?
That’s a good question. I’d like to see that list also, sorted by country, since this is likely an international problem.
Home Depot Canadian stores support EMV. IIRC Canada banks started issuing EMV Visa/MC cards in 2009 or 2010.
Non-EMV transactions from Canada stores will likely be:
1) EMV cards that had to fall back to magnetic stripe swipe when the terminal could not read the chip
2) Manual entries
3) US Cross border shoppers
Qualys. Rated Home Depot SSL as an “F”
Home Depot has since contacted Qualys and asked that their site not be rated.
Sources investigating the breach confirm that hundreds of millions of cards have been compromised. More than previously thought and more than Target !!
The Home Depot is fully aware of the vast extent of the breach, but in order to maintain shareholder value they are attempting to withholding information attesting to these facts.
Home Depot Stock is about to take a SERIOUS hit when this information reaches the general public as it is likely that Home Depot board members will attempt to postpone confirmation of the breach for as long as reasonably or legally possible.
Moreover, Insider trading on the stock does depict board members were quick to sell some stock in Home Depot within the last month.
Home Depot’s 2Qtr earnings were released on 19-August. That is the huge spike from $83 to $90+. It climbed again to $93.52 before the breach news hit. It is still ~$9 higher than it was before quarterly earnings on 19-August.
My gut feeling is the slight dipping in late August was simply profit-taking from the jump, and insiders finally getting to cash some in when their blackout window expired a few days later. The 25th was Monday. I would want to see the specifics involved before concluding an insider dumped because of the breach and not because of stock at all-time highs woot mansion downpayment baby!
The analysis from the onsite forensic teams typically takes about two weeks. Another consideration is “insider threat”. A few Home Depot stores have had this issue in the past with rogue back-office employee siphoning off card data and selling it.
To clarify, when a Common Point of Purchase analysis is completed for any merchant there is always a high degree of large merchants being shown as common points of purchase. Stores such as Walmart, Target, Best Buy and many others will be common across your card portfolios. The longer the window, the more common the occurrence. The saturation point you are hope to find is 100% from a random sample. That’s the magic number. Most will become highly suspicious at the 90% rate, but still that’s no guarantee of a compromise. You must also consider the timeframe and geography.
If you have a very high percentage and no indication of a a breach there are only two outcomes. 1. Malware that is highly advanced and so stealth it cannot be traced or 2. Its an Insider.
Fraud rates for Home Depot are still very low for all Banks. So that would tell us that the availability, if there is a breach in this instance, those cards would have only recently been made available.
Banks will not take any action until they have conclusive evidence of the means by which card data was harvested or when there is a statistically valid variance from normal expected fraud rates for the merchant in question.
If history is a marker, we should know in the next week. I also expect there to be a copy-cat compromise coming in November that will mimic the Target breach as millions of shoppers take to the store in November. Across the country at this moment there are hundreds of merchants that are compromised. Most are small under $1M in sales. That adds to the complexity of narrowing down what card was compromised where.
Nic Cubrilovic claims leaky captcha theory doesn’t hold water: https://www.nikcub.com/posts/analyzing-fbi-explanation-silk-road/
I enjoyed your article. thank you for comment
BE SMART AND BECOME RICH IN LESS THAN 3DAYS….It all depends on how fast you can be to get the new PROGRAMMED blank ATM card that is capable of hacking into any ATM machine,anywhere in the world. I got to know about this BLANK ATM CARD when I was searching for job online about a month ago..It has really changed my life for good and now I can say I’m rich and I can never be poor again. The least money I get in a day with it is about $50,000.(fifty thousand USD) Every now and then I keeping pumping money into my account. Though is illegal,there is no risk of being caught ,because it has been programmed in such a way that it is not traceable,it also has a technique that makes it impossible for the CCTVs to detect you..For details on how to get yours today, email the hackers on : (atmmachinehacker@gmail.com). Tell your loved once too, and start to live large. That’s the simple testimony of how my life changed for good…Love you all …the email address again is ;atmmachinehacker@gmail.com