Nearly a week after this blog first reported signs that Home Depot was battling a major security incident, the company has acknowledged that it suffered a credit and debit card breach involving its U.S. and Canadian stores dating back to April 2014. Home Depot was quick to assure customers and banks that no debit card PIN data was compromised in the break-in. Nevertheless, multiple financial institutions contacted by this publication are reporting a steep increase over the past few days in fraudulent ATM withdrawals on customer accounts.
The card data for sale in the underground that was stolen from Home Depot shoppers allows thieves to create counterfeit copies of debit and credit cards that can be used to purchase merchandise in big box stores. But if the crooks who buy stolen debit cards also are able to change the PIN on those accounts, the fabricated debit cards can then be used to withdraw cash from ATMs.
Experts say the thieves who are perpetrating the debit card fraud are capitalizing on a glut of card information stolen from Home Depot customers and being sold in cybercrime shops online. Those same crooks also are taking advantage of weak authentication methods in the automated phone systems that many banks use to allow customers to reset the PINs on their cards.
Here’s the critical part: The card data stolen from Home Depot customers and now for sale on the crime shop Rescator[dot]cc includes both the information needed to fabricate counterfeit cards as well as the legitimate cardholder’s full name and the city, state and ZIP of the Home Depot store from which the card was stolen (presumably by malware installed on some part of the retailer’s network, and probably on each point-of-sale device).
This is especially helpful for fraudsters since most Home Depot transactions are likely to occur in the same or nearby ZIP code as the cardholder. The ZIP code data of the store is important because it allows the bad guys to quickly and more accurately locate the Social Security number and date of birth of cardholders using criminal services in the underground that sell this information.
Why do the thieves need Social Security and date of birth information? Countless banks in the United States let customers change their PINs with a simple telephone call, using an automated call-in system known as a Voice Response Unit (VRU). A large number of these VRU systems allow the caller to change their PIN provided they pass three out of five security checks. One is that the system checks to see if the call is coming from a phone number on file for that customer. It also requests the following four pieces of information:
-the 3-digit code (known as a card verification value or CVV/CV2) printed on the back of the debit card;
-the card’s expiration date;
-the customer’s date of birth;
-the last four digits of the customer’s Social Security number.
On Thursday, I spoke with a fraud fighter at a bank in New England that experienced more than $25,000 in PIN debit fraud at ATMs in Canada. The bank employee said thieves were able to change the PINs on the cards using the bank’s automated VRU system. In this attack, the fraudsters were calling from disposable, prepaid Magic Jack telephone numbers, and they did not have the Cv2 for each card. But they were able to supply the other three data points.
KrebsOnSecurity also heard from an employee at a much larger bank on the West Coast that lost more than $300,000 in two hours today to PIN fraud on multiple debit cards that had all been used recently at Home Depot. The manager said the bad guys called the customer service folks at the bank and provided the last four of each cardholder’s Social Security number, date of birth, and the expiration date on the card. And, as with the bank in New England, that was enough information for the bank to reset the customer’s PIN.
The fraud manager said the scammers in this case also told the customer service people they were traveling in Italy, which made two things possible: It raised the withdrawal limits on the debit cards and allowed thieves to withdraw $300,000 in cash from Italian ATMs in the span of less than 120 minutes.
One way that banks can decrease the incidence of PIN reset fraud is to require that callers supply all of the requested information accurately, and indeed the bank employee I heard from in New England said a nearby financial institution she’d contacted that used the same VRU system saw its PIN fraud drop to zero when it began requiring that all questions be correctly answered. The bank on the West Coast that I interviewed also said it had already begun requiring all five elements before processing PIN changes on any cards that have been used at Home Depot since April.
Still, some of the world’s largest banks have begun moving away from so-called knowledge-based authentication for their VRU systems toward more robust technologies, such as voice biometrics and phone printing, said Avivah Litan, a fraud analyst with Gartner Inc.
“We saw this same activity in the wake of the breach at Target, where the thieves would call in and use the VRUs to check balances, remove blocks on cards, get the payment history and of course change PINs,” Litan said.
Voice biometric technologies create an index of voice fingerprints both for customers and various fraudsters who conduct VRU fraud, but Litan said fraudsters often will use voice synthesizers to defeat this layer of detection.
Phone printing profiles good and bad callers alike, building fingerprints based on dozens of call characteristics, including packet loss, dropped frames, noise, call clarity, phone type and a host of other far more geeky concepts (e.g., “quantization,” and “taggers“).
ANALYSIS
The fact that it is still possible to use customer service or an automated system to change someone else’s PIN with just the cardholder’s Social Security number, birthday and the expiration date of their stolen card is remarkable, and suggests that most banks remain clueless or willfully blind to the sophistication of identity theft services offered in the cybercrime underground. I know of at least two very popular and long-running cybercrime stores that sell this information for a few dollars apiece. One of them even advertises the sale of this information on more than 300 million Americans.
Banks are long overdue to move away from knowledge-based authentication. Forget about the fact that most major providers of these services have been shown to be compromised in the past year by the very crooks selling Social Security numbers and other data to identity thieves: The sad truth is that today’s cybercriminals are more likely to know the correct answers to these questions than you are.
I bring this up mainly because Home Depot is, predictably, offering credit monitoring services to affected customers (which, given the length of this breach is likely to impact a significant chunk of the American population). Credit and debit card fraud is annoying and inconvenient and can be at least temporarily expensive for victims, but as long as you are keeping a close eye on your monthly statements and reporting any unauthorized charges immediately, you will not be on the hook for those charges.
Please note that credit monitoring services will not help with this task, as they are not designed to look for fraud on existing accounts tied to your name and personal information. As I’ve noted in several stories, credit monitoring services are of dubious value because although they may alert you when thieves open new lines of credit in your name, those services do not prevent that activity. The one thing these services are good for is in helping identity theft victims clean up the mess and repair their good name.
However, given the fact that your Social Security number, date of birth and every possible answer to all of these knowledge-based authentication questions can be had for $25 in order to establish new lines of credit in your name, it makes good sense for people to avail themselves of free credit monitoring services. But there is little reason to pay for these services. If you don’t already have a credit monitoring service for free then maybe you haven’t been paying close enough attention to the dozens of companies over the past year that have likely lost your data in a breach and are already offering these services for free.
For more information about the benefits and limits of credit monitoring services — as well as other helpful tips to proactively safeguard your credit file — see this story.
More information, including an FAQ about the breach, released by Home Depot is available at this link.





Now the last four digits of the customer’s Social Security number is a passport to steal more.
Bring out the inner bureaucrat in you.
SS numbers should never be used to verify transactions. The crooks will have all your finacial data before you have it. I DID NOT BUY IT!
“And yeah, yeah, yeah, we all know the best passwords are a series of random symbols that look like Dagwood Bumstead’s dialogue balloon after hitting his thumb with a hammer. Giving you the same chance of remembering them as Rob Ford has of winning the decathlon in Brazil two years hence.
On top of that, enough layers of rules are being added to qualify for croissant dough. Your password no longer can be your wife’s birthday or 1234567 or the word “password” or eatpoo&die. Can’t be any password that has ever been used before. In the history of humanity.” Will Durst
For $25 they can be you and shopping for stuff you can’t afford. They sound like you now with new talk box tech too. You have tons of social and no security.
Buy duck tapes. Duck tapes make you smart.
Would it help if banks, retailers, and credit card companies monitored the online card shops looking for data that might point back to their own customer base?
That’s how you picked up Home Depot at the Rescator site. Why could Home Depot and others use the same technique?
Is it too late once it’s gone that far?
Those personal info security questions are definitely dumb.
When forced to use them by various sites, it seems wise to have a system that doesn’t use real info. E.g. “What is your mother’s maiden name?” could have a standard whimsical answer like “Archimedes”, or a modification of the correct answer where the syllables are exchanged, e.g. “Sonjohn”. The key is to have an easy system in your head that never uses anything associated with you in public databases.
Some sites let YOU provide the correct “answer”. Try a technique employed by magicians – misdirection.
ex: An answer to “What is the name of your first pet” is the name of my first teacher.
Still, that information gets captured by that site for future comparison. Is that information kept secure? SURE IT IS! Just like our confidential charge card and other credentials.
We need a better way.
Nice to see that the cybercrime stores have “Verified ethics support”, however it does not seem to be working.
Maybe it’s time for people to ban together for a class action lawsuit? IMHO. It would appear that is the only way to help accelerate accountability by all parties here. Card Issuers, Banks and Merchants and/or their processors.
What’s beyond belief is IMHO. The multitudes of apparent “Gross Negligence” shown here. Here is my short list. But there appears to be many more.
1. That there are/were methods that were available to scan these devices that would have shown their vulnerability to this derivative of malware that hit Target. Had scans like this been done even once a week per device. This specific breach could not have been taking place since April. If there was ANY form of due diligence going on. With full knowledge that the Target breach had already occurred.
2. The Home Depot IT staff seem as if they made no serious attempt to even test if the attack/installation vector that is/was required to be used to initially install this malware was present or fortified or rigorously monitored to detect this infiltration even after knowing what happened to Target.
3. It took 6 days to announce that anything took place, once Home Depot was informed that they should check.
When at anytime during this discovery process a more definitive statement could have been made like “We see signs of a breach, we are doing more research to determine when it started and how widespread and extensive it was”. Which could have taken place after day 1 or day 2 of this research vs. day 6.
4. As you clearly stated. The company statement also should have included some detail about while no PIN data was captured from the actual breach itself. That Home Depot had or could have communicated with the bank(s) of their choice to see IF cards captured in the breach were seeing unusual levels of PIN reset fraud. Then in their statement about PIN data qualified their statement today to say that “There have been reports of cards involved in this breach of having recent PIN reset fraud and that because of that. People should be aware of that FACT!
Sadly. The ONLY way this “Breach Party” will slow down. Is by making the responsible parties more accountable by them learning that if they don’t come up with both a short term and long term and continued plan to resolve these breaches. That they will be paying dearly by their delays. In cold hard cash. Since losing sales and dropping stock prices seem not be very motivating so far.
Nothing else has worked to date. Maybe this might?
Don
I agree completely. Another sector that is in need of serious regulation are those data companies that provide credit reports and background checks. When those companies are compromised we only hear about it here so only small percentage of the population is aware.
Who will be the plaintiff in the Class Action? The consumers? They can’t prove harm since it is the issuers (banks) are on the hook for the losses, the cost of reissue, and the cost of incident response. The issuers can’t sue because of their arrangements with the card brands (Visa, MC, Amex), and card portfolios are still profitable. The card brands typically go after the those breached, but the settlements are pennies on the dollar.
Someone has yet to come up with a successful legal theory to prosecute without proven harm in these cases.
Fucking Russians…. Also if Rescator is upset with the current Ukraine govt why doesnt he join the terrorists in the east (so he can die like the rest of them)?
“John Dough
September 9, 2014 at 1:56 am
Fucking Russians…. Also if Rescator is upset with the current Ukraine govt why doesnt he join the terrorists in the east (so he can die like the rest of them)?”
Why, you ask?
Oh… that’s easy. You see, he’s a criminal, who’s really in it just for the money, and he’s using “patriotism” as a sham excuse for his profiteering at other people’s expense.
Just like Dick Cheney, FOX “News” and the rest of the U.S. military-industrial complex, in their braying for “let’s get involved in Ukraine”… is. Only thing is, Dick and his pals cause a lot more trouble, and cost the U.S. a lot more money, than your friend “Rescator”, ever will.
Any questions?
Well, if you think properly, War IS a way of making money…
But in this case the hackers are not attacking only “innocent citizens that are buying stuff”… The target IMHO is wider, into financial institutions. We saw retailers so far (Target, Home Depot, Dairy Queen, etc.), but maybe this is the tip on this iceberg.
I can probably imagine some attack targets coming next, so I’d recommend to stay alert and do a closer monitoring into much more things besides the finance inter-communications world… I’d include there any government communications (imagine if they massively tap TAX reports), Medical care/drugstores (imagine messing up with the population’s health data), and so on.
It’s not easy to keep up in security with that. It’s equivalent of a knife against a sniper rifle in the distance. And can all be targets in this war.
Every use of the PIN exposes it, and the exposure has a risk and a cost attached. For small value transactions, say less than 50$ , it is probably not economically justified.
Moreover, establishements where most of the transactions are low value could probably use much cheaper terminals, that do not have PIN pads at all.
No PIN used, no PIN stolen.
Good point. Contactless EMV would be faster and also reduce exposure from having static Track Data on Magstripes (which can be easily compromised as shown on this blog).
You did not read the story – the crooks did not capture the pins they reset them. you shold re-read the story.
Reading the story before commenting is too much to ask of some people.
I did not catch the “reset” part, most countries do not provide this option.
Why read? Most of us assume we “know everything already”…therefore that makes us able to comment even if all we read is the headline of ANY story. I see this in multiple places and it is in written form a reflection of our overall society. Little “thought” goes into much.
Sorry. But in any case, customer selected PIN is not a good idea, since customers often select weak PINs. If the bad guys have access to the customer’s personal data, such as birthday, ZIP code, family birthdays, phone number etc. there are statistics that they can guess the PIN with a very small number of trials.
I agree with your statments. pins will be more secure when they are longer and change freqently, along with ssn and the credit card number, quite doable with todays technologie.
Sure, now enter your ” good”pin at the the at the theather. Since you are not using cash, miss the opening, since you got there when the show is starting, fashionably late to miss the lame previews, and they have a sticky keyboard for you, so you have to repeat the process with the next customer getting louder every second, heh, heh.
LOL. Love this capitalism we all have in the world nowadays.
Like they say, “you don’t say whoa in a horse race” .
Keeping us busy keeping learning, protecting, capitalizing. Great stuff.
That’s what they get for showing that disturbing “Barefootin” commercial over and over again. Cramming 5 different races into an unrealistic social scenario will result in your system getting hacked every time.
That’s some weapons grade derp there. Tell us more how race mixing will lead to less secure store point-of-sale networks.
Hey Media Propaganda, bravo, I can’t tell you how much I hate that commercial it might be the most annoying thing ever.
@John Dough I’m sorry, have you been mildly inconvenienced by credit card fraud? You’re absolutely right that people should die to redress your grievance.
Well done again BK. It’s easy to lose sight of the retail banking processes that leak or can reset payment information related to this compromised track data. In addition to the underground aggregators, you can bet fraudsters are using services like spooftel[dot]com to appear as an ANI-match and flow through lesser authentication.
All the more reason to use credit, not debit, cards.
Can’t a CC PIN also be reset? Once the theives have your basic information can’t they just reset your PIN on a credit card and get that money as well?
They can but you’re in a better position while disputing the charges. With debit, the money is out of your account and you have to argue to get it back. Meanwhile, your mortgage payment may bounce, etc. With credit, the impact is lower. You still need to dispute the charge but there is less pain in the meantime and no bounced check fees.
WalMart is now requiring that cards with Chip/Pin be authenticated with the chip during the transaction.
Yes, and it works well at walmart. The chip readers at Home Depot were installed in nearby store about 9 months ago, but have not been activated, I tride to use them severel times but still had to swipe to pay.
Used my EMV card at Walmart for the last few months. Obviously they have decided the cost of being hacked is greater than the install cost.
I too tried an EMV card at Home Depot 3 months ago without success. I asked one of the store employees why the machine was not setup to accept them; were they not worried after the Target hack? I am sure they didn’t really understand what I was asking.
Maybe now the banks/stores will find the money to roll-out EMV. I don’t buy their argument it is too expensive. Europe has had it for years – I go often.
Trust me, banks are the first inline for EMV since banks are the ones eating all the costs of fraud caused by these data breaches, however it doesn’t work for debit yet, so they can’t get it. Home Depot doesn’t give a crap about EMV because they aren’t liable…. yet…..not till October 2015. Then you’ll see every retailer jumping on the EMV train. Frank Blake was so quick to tell all his customers not to worry about the fraud on their cards, they are not responsible. I’m sure they’ll be singing a different tune after October 2015. JERKS!
chip+PIN or chip+signature ?? Is this in the U.S. or maybe Canada? I have not heard of any U.S. banks offering chip+PIN (and I have asked several)
Can someone comment on how an attacker can use the stolen Zip Codes to derive SSN? Wouldn’t that require the victim to use their credit card at a Home Depot located in the same Zip Code as where they were born? I understand SSNs are based in part on location of birth, but some of us do move once in awhile. I’d like to understand that statement in the article a little better or I’m calling FUD on it.
I thought the zip code just helped identify “which John Smith” the card belongs to — not to directly calculate the SSN. After BK’s reporting on the ID theft ring being a “legitimate customer” of a credit bureau, I’m willing to believe this would be trivial.
SSNs haven’t been location based for decades. I don’t remember when it changed, may be as far back as the 70’s.
Not exactly. SSAN (the number itself) is still created based on the location of the request for a new account number. So, the number (specifically the first 5 digits) tell where and when the account number was generated. The last 4 is a sequence number.
However, you are correct that after creation there is no longer a correlation with location of the account holder.
All the information you need to answer your questions is clearly stated in the article. I’m going to guess you didn’t actually read the whole article before leaving your snarky comment.
The thieves are using underground services to buy SSN and DOB data. The card data stolen from HD customers includes the full name of the cardholder, but good luck finding info on people with common first and last names unless you also have city and state data, and having that person’s exact or adjacent ZIP code helps the fraudsters zero in on the record most likely to be the cardholder’s. Armed with SSN, DOB and expiration of the card (the last factor they got from buying the card data from the underground store) they can reset the PIN.
Wait, did you just call my comment snarky? I’m curious what part of it you thought was snarky, because if you had read the rest of the comment thread, you would see the why I thought it was confusing when I read it – because there is academic research showing that you can partially derive SSN from Zip Codes, which is what I thought it was referring to. An article that weaves back and forth through a number of related topics like this one does isn’t always the easiest to follow if the reader isn’t familiar with the workings of the underground.
“Calling FUD” is what I was referring to, Aaron. From the story:
“This is especially helpful for fraudsters since most Home Depot transactions are likely to occur in the same or nearby ZIP code as the cardholder. The ZIP code data of the store is important because it allows the bad guys to quickly and more accurately locate the Social Security number and date of birth of cardholders using criminal services in the underground that sell this information.”
Using criminal services in the underground, one of which I describe in detail toward the end of the article (and even include screen shots of). No academic hacking method involved. Straight up pay for someone’s SSN and DOB, if you can supply their address and zip.
If you are trying to find the SSN and DOB of a John Smith in Springfield, Ill. so that you can reset his debit card PIN, that’s going to be hard unless you have more specific data about him. The ZIP of his closest Home Depot will probably narrow it down significantly.
It isn’t that they use the zip to get the SSN. They use the ZIP to narrow the results when searching for John Smith.
Wouldn’t the wrong phone number used by the cyber criminals be a dis-qualifier in the Voice Response Unit if it was verifying using caller ID. Just the caller ID not matching the customers phone record should stop the pin number from being changed.
The phone number can be spoofed the same way people call 911 and appear to be calling from an unsuspecting residence to get the SWAT team to raid it.
If the attackers don’t have the correct phone number, the bank lets them slide through if they have 3 other correct pieces of the puzzle.
This is the authors point about banks needing to up their requirement to 5 out of 5, instead of 3 out of 5 correct answers.
The phone printing technology that Brian Krebs mentions in the article was developed by Pindrop Security. Pindrop can detect Caller ID spoofing and other forms of phone deception to protect against fraudsters. Pindrop also presented at Black Hat 2014 on a solution to detect fraud attacks in the VRU.
“Can someone comment on how an attacker can use the stolen Zip Codes to derive SSN?”
From what I gather in the article: The attacker gets the information from a debit card owned by Bob Jones that was used at a Home Depot at zip code 44444. Identity thieves sell SSN’s online for a few bucks. That SSN comes with other info like an address. Say they’re selling a SSN for a “Bob Jones” who lives at zip code 44445.
The attacker can then match the zip codes to get the SSN of the Bob Jones who lives within a few miles of a particular Home Depot store.
Ah, ok, that makes more sense. So it would help them buy the correct SSN, as opposed to actually being able to determine it themselves. The latter is what I thought the article was implying, because there is some really interesting academic research that shows if you know some basic information about someone, like name and zip code, you can calculate their SSN to just a few possible choices.
Thanks!
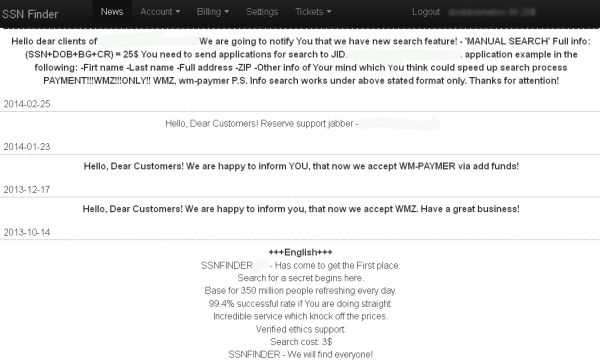
Yeah, the screenshot of the SSN seller in the article tells the attacker to give:
-First name
-Last name
-Full address
-ZIP
-Other info of Your mind which you think could speed up search process
I guess the SSN seller does the search in their database and then tells the attacker if they have an exact match or one very close. The attacker then receives the SSN and DOB
To reset the PIN, the bank requires 3 of these:
-calling from phone number on record
-the 3-digit CVV/CV2
-the card’s expiration date
-the customer’s date of birth
-the last four digits of the customer’s SSN
The expiration date might be gotten from the initial breach. The DOB and SSN are purchased after the breach.
Good analysis, thanks. I need to pass this article onto my colleagues who work in the regulatory/privacy realm. We are always talking about the potential for somewhat innocuous data elements to become damaging when combined with other somewhat innocuous data elements. This is a perfect example of that scenario.
But the first three digits of a social security number dignify the state you where born in . So if you move to another state , the zip code won’t be a one hundred percent verifier of your identity being correct
This is why when a person calls Social Security they ask you the city you where born in to identify you are the real person.
Close but not quite. The number is based upon where the SSN application was made, not where you were born.
These days it seems that you have to get one when quite young but that’s recent. Previously you only needed one about the time you started work (teens).
Are you sure about that because you have to show a birth certificate to get a social security number. My assumption is that years ago, when a person was born, the parent applied for a social security number within the first year.
It is a rather recent development to get a SSN for young children. The change was in response to tax fraud. You could say you had five kids, and there was no proof required, as unbelievable as that seems. My older sibs got their SSN’s at the same time I did, even though we’re years apart, due to the change. As a result, we all have sequential SSN’s.
Yes. The requirement for SSNO for newborns is rather recent. I am not sure how long – ten years or so (I guess).
You do need proof-of-identity which, for babies, is usually a birth certificate. But immigrants (Green-card holders typically) probably use a passport.
WTF??? They should require CVV/CV2 when resetting the PIN.
How are you going to use the card if you don’t have the card in your possesion?
Clever. Something you have (the actual card) is a big step up.
yes, that’s the most unbelievable item of info Brian provided. The one thing that these gangs can’t scan or buy on black market, that’s right on your card and is required to use the card online, and the banks don’t require it to change the PIN. Maybe the banks have experienced some situations and are trying to provide excellent customer support, but not having the security number on the card I just can’t see being viable for using the card. I suppose maybe the thought was if stolen, change the PIN which was written down next to card or something, but card should be deactivated. This is entirely unacceptable and needs to be fixed by banks immediately.
Well, that would make sense, wouldn’t it? We can’t do that.
Brian, you’ve been unusually quite about the JPMorgan breach. What gives?
As much as I dislike my current credit union, they do NOT allow me to change my debit card PIN using a VRU.
September 7th, I received a call from my bank’s security department alerting me to three ATM transactions on my checking account. The transactions are from an ATM in the U.K.
I spoke to my bank’s security department again today, and they tell me my PIN has not been reset recently. So, how do the bad guys complete an ATM transaction without a PIN, or without resetting the PIN?
They must have the PIN info skimmed from the POS terminal, and this “No debit or PIN information has been compromised” nonsense HD is advertising is just PR smoke. Bad news.
From the Home Depot press release:
“While the company continues to determine the full scope, scale and impact of the breach, there is no evidence that debit PIN numbers were compromised.”
They’re not saying your PIN wasn’t stolen too, they’re just saying they haven’t seen evidence…yet.
Scott
Its also possible your PIN was compromised somewhere other than Home Depot, such as a skimmed ATM. PIN info is encrypted so if they did capture PIN data they would have to break the encryption which if true is bad for all of us.
Also if your pin is set to something like the last 4 of your social or your DOB they could have guessed it.
They can break the encryption, fairly easily in many cases.
But that doesn’t matter. If they are scrapping the data directly from the POS terminal, they get it before it is encrypted.
PINs aren’t saved on POS terminals. They must’ve gotten your PIN another way.
I might be remembering wrong, but isn’t it CVV2 for Visa and CVC2 for Mastercard? Just noticed and thought I’d mention it…
Thanks for all your work on demystifying compromises. It makes my job a bit easier at times.
Industry standard security requirements are arcane at best. Large big box retailers are always run by CFOs’ who are more interested in profits than security.
New York Times, 8/5/2014:
“Target Puts Data Breach Costs at $148 Million, and Forecasts Profit Drop”
Security can be very profitable.
Brian, Thanks for what you do. My theory on WHY so many breaches as of late – Doesn’t it make sense that a lot of the heisted debit/ATM funds and the monetary proceeds of gift-card/merchandise “fencing” are finding their way over to the Ukraine to help financially support the Civil War? Thoughts?
why these breaches are occuring is not difficult to understand at all. In fact you’d have to be pretty clueless to see them occuring in the news and be yet another victim of the same malware. I say this as a longtime programmer, from low level PC programming back in the beginning to big iron at large corporations (IBM I formerly AS/400).
All these cards were stolen with the same software loaded onto Windows PC’s used as POS terminals. You just can’t get any more stupid than that, especially as trivial as a POS terminal is.
This article mentions PIN changing by crooks. Brian has written previously about PIN theft via pinhole camera. Here is another method of PIN theft via reading the heat signature on the keypad: http://www.realfarmacy.com/how-easily-someone-can-steal-your-atm-pin-code-without-you-noticing-how-to-prevent-this/
important to understand the PIN’s are being changed at the bank via phone call, not stolen.
Doesn’t Canada utilize EMV readers? How did these hackers compromise HD locations in Canada and steal their credit cards?
If a Canadian customer made purchases at Canadian and American Home Depot stores, the hacker might be able to link the customer’s name, card info and location together.
Most Canadian issuers still have magstripes on their credit and debit cards along with the chip. The accounts that would have been compromised were likely compromised only if the customer had to use the magstripe to complete the transaction. Since both the terminals and cards are EMV capable then the only way for that to occur would be for the chip reader to fail and then allow a “fallback” transaction to magstripe. This would therefore mean a very low percentage of accounts used at Home Depot in Canada are at risk.
Considering that banks allow information such as birth date and social security numbers that can be obtained readily from the Internet shows they are living in a dream world to think its legitimate verification of the cardholder. As this personal data moves to the Internet its no longer valid for verification. We can thank all those sites that required this information in signing up for the now availability of it to fraudsters. What were they thinking and why are banks still relying on it?
SSN and birthdate not being obtained from internet as in it’s out there somewhere. It’s obtained from hacks on systems I can only guess at. I believe I’ve seen in news through years that credit reporting systems have been hacked. Of course applying for credit cards on fake sites (phishing) gives the data to them. They have to steal it, but breaking into systems is what they do. Of course they don’t break into IBM systems like I program or else we wouldn’t be having these conversations.
Just a few practical questions:
(1) What information do you give up when you use your credit card in a store?
(2) If 60 million or more accounts were compromised how do the bad guys select promising candidates? In other words, what are the odds they pick mine?
(3) If I shopped at Home Depot should I cancel my card or just watch my account?
(1) First name, last name, middle initial, card (account) number, card expiration date.
(2) They’re probably looking for customers who made repeated purchases at the same store over a length of time. That pattern will mean that you live somewhere close to that store and they’ll be able to match your other personal ID info to the card you used.
(3) You might want to call your card service and talk to a representative. See what they think.
I did call my card service when the story broke.
They told me that they had a great fraud prevention service and said to keep an eye on my account. In other words, waitful watching.
on #2, I am not knowledgeable on this and most of what I know comes from Brian, but there are two groups of bad guys: the crackers, who scoop up all card data on the systems they’ve compromised, and the thiefs, who buy the card data to steal with it. The thiefs criteria I believe will be 1) zip code of store where cards were obtained is close to them (this is a new innovation per Brian) and 2) the class of debit or credit card. Different classes cost different amounts, and they will choose a class whose cost is low enough to make money stealing using their preferred technique.
I checked my bank/credit cards online having them each output purchases back to April and did a text search for “depot.” Only AMEX showed as having a couple purchases (legit). No bad purchases, but I frankly don’t want to having to deal with that hassle. I called AMEX and told them there was a Home Depot fraud issue going on and that I’d shopped there during that time and wanted a new card issued. They overnighted a new card (this was in the afternoon, so I had it before noon in two days). It costs you nothing – costs the issuer some cash, but it’s their fault for not moving to a more secure system. Plus side: new AMEX card has an EMV chip. I haven’t found a place I can use it yet, but hopefully soon.
Oasis Technology, Inc., has developed a device to STOP HACKERS BEFORE THEY ACCESS A COMPANY’S NETWORK.
It is an actual physical device — and it is NOT A FIREWALL.
http://www.oasistechnology.com/titan/
It is installed at customer sites and fully functional — it is not a prototype.
We can prove that it works. Please contact us at info@oasistechnology.com or 805-445-4833.
Please don’t post ads in the comments.
Marketing via spam in a comments section makes me certain that I should avoid this product. You don’t see any of the other major IDS/IPS system and service companies doing the same, and for good reason too.
Question: I made a transaction at HD on September 2, the day that they say they began investigating. Had they already done something that day to close the breach or do I still need to be concerned?
The fact that Home Depot didn’t know and couldn’t have possibly secured all their POS devices by then (or even now) – I would say you should be concerned. Call your issuing card company and tell them you made a purchase at a compromised Home Depot and want a new card issued. Watch your transactions until your next statement.
@Jason: thanks for the info. I am getting in touch with my bank now.
Don’t put this totally at the feet of the banks Brian.
I used to work for Capital One wayyy back in 1993-97. At that time to request a PIN change the customer could not:
a. Request a PIN they wanted
b. Could not get it over the phone.
We would take their request. Hit a button for PIN issue on their account and 7-10 days later they would receive a piece of mail with the new PIN that they did not choose.
It was way more secure than today. But at that time customers complained. Saying they wanted to be able to choose their own PIN. They wanted to be able to do it over the phone and have it active that moment.
So what happened? As the years have gone by this is exactly what the customer has been given. Exactly what they wanted. The ability to change PINs instantly to something they want (and assuredly less secure then a randomly picked PIN) and the ability to have it your way, right now.
We can debate what they choose to use for verification. But to lay the blame solely at the feet of the bank is disingenuous. The customer got what they asked for and what they asked for is inherently less secure than the way it was done 20 years ago.
I take your point, Mike, but the problem with the “customers demanded crappy security” argument is the banks just then go to the least common denominator. It’s unusual for a retailer, bank or any major company to offers a choice of security features; it’s usually just binary. All or nothing, on or off. Idiot-proof or hard to use.
Don’t get me wrong, I’m not saying banks are not to blame. And I’m not saying that the customer is to blame.
The push to where we are came from the customer. Are there safer ways to implement this process? Yes, and it is imperative on the banks to implement them. But we shouldn’t lose sight of how we got here because as the push comes for more convenience the pressure from the outside hackers will continue to grow.
I often say that an ounce of convenience normally yields a pound of problems.