Distributed denial-of-service (DDoS) attacks designed to silence end users and sideline Web sites grew with alarming frequency and size last year, according to new data released this week. Those findings dovetail quite closely with the attack patterns seen against this Web site over the past year.
Arbor Networks, a major provider of services to help block DDoS assaults, surveyed nearly 300 companies and found that 38% of respondents saw more than 21 DDoS attacks per month. That’s up from a quarter of all respondents reporting 21 or more DDoS attacks the year prior.
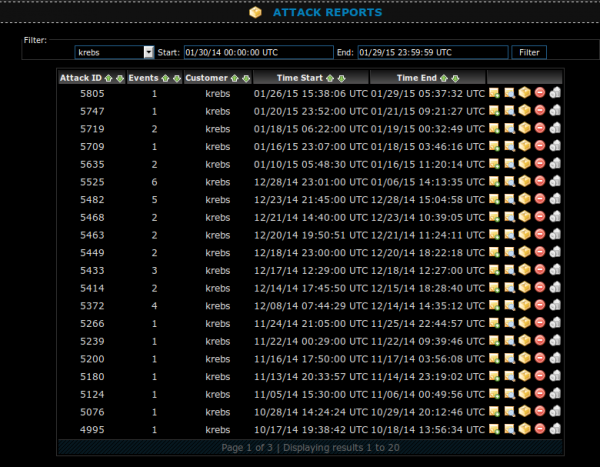
KrebsOnSecurity is squarely within that 38 percent camp: In the month of December 2014 alone, Prolexic (the Akamai-owned company that protects my site from DDoS attacks) logged 26 distinct attacks on my site. That’s almost one attack per day, but since many of the attacks spanned multiple days, the site was virtually under constant assault all month.
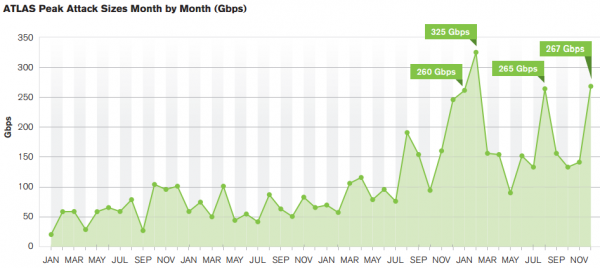
Arbor also found that attackers continue to use reflection/amplification techniques to create gigantic attacks. The largest reported attack was 400 Gbps, with other respondents reporting attacks of 300 Gbps, 200 Gbps and 170 Gbps. Another six respondents reported events that exceeded the 100 Gbps threshold. In February 2014, I wrote about the largest attack to hit this site to date — which clocked in at just shy of 200 Gbps.
According to Arbor, the top three motivations behind attacks remain nihilism vandalism, online gaming and ideological hacktivism— all of which the company said have been in the top three for the past few years.
“Gaming has gained in percentage, which is no surprise given the number of high-profile, gaming-related attack campaigns this year,” the report concludes.
Longtime readers of this blog will probably recall that I’ve written plenty of stories in the past year about the dramatic increase in DDoS-for-hire services (a.k.a. “booters” or “stressers”). In fact, on Monday, I published Spreading the Disease and Selling the Cure, which profiled two young men who were running both multiple DDoS-for-hire services and selling services to help defend against such attacks.
The vast majority of customers appear to be gamers using these DDoS-for-hire services to settle scores or grudges against competitors; many of these attack services have been hacked over the years, and the leaked back-end customer databases almost always show a huge percentage of the attack targets are either individual Internet users or online gaming servers (particularly Minecraft servers). However, many of these services are capable of launching considerably large attacks — in excess of 75 Gbps to 100 Gpbs — against practically any target online.
As Arbor notes, some of the biggest attacks take advantage of Internet-based hardware — everything from gaming consoles to routers and modems — that ships with networking features that can easily be abused for attacks and that are turned on by default. Perhaps fittingly, the largest attacks that hit my site in the past four months are known as SSDP assaults because they take advantage of the Simple Service Discovery Protocol — a component of the Universal Plug and Play (UPnP) standard that lets networked devices (such as gaming consoles) seamlessly connect with each other.
In an advisory released in October 2014, Akamai warned of a spike in the number of UPnP-enabled devices that were being used to amplify what would otherwise be relatively small attacks into oversized online assaults.
Akamai said it found 4.1 million Internet-facing UPnP devices were potentially vulnerable to being employed in this type of reflection DDoS attack – about 38 percent of the 11 million devices in use around the world. The company said it was willing to share the list of potentially exploitable devices to members of the security community in an effort to collaborate with cleanup and mitigation efforts of this threat.
That’s exactly the response that we need, because there are new DDoS-for-hire services coming online every day, and there are tens of millions of misconfigured or ill-configured devices out there that can be similarly abused to launch devastating attacks. According to the Open Resolver Project, a site that tracks devices which can be abused to help launch attacks online, there are currently more than 28 million Internet-connected devices that attackers can abuse for use in completely anonymous attacks.
Tech pundits and Cassandras of the world like to wring their hands and opine about the coming threat from the so-called “Internet of Things” — the possible security issues introduced by the proliferation of network-aware devices — from fitness trackers to Internet-connected appliances. But from where I sit, the real threat is from The Internet of Things We Already Have That Need Fixing Today.
To my mind, this a massive problem deserving of an international and coordinated response. We currently have global vaccination efforts to eradicate infectious and communicable but treatable diseases. Unfortunately, we probably need a similar type of response to deal with the global problem of devices that can be conscripted at a moment’s notice to join a virtual flash mob capable of launching attacks that can knock almost any target offline for hours or days on end.
Anyone who needs a reminder of just how bad the problem is need only look to the attacks of Christmas Day 2014 that took out the Sony Playstation and Microsoft Xbox gaming networks. Granted, those companies were already dealing with tens of millions of new customers that very same day, but as I noted in my Jan. 9 exclusive, the DDoS-for-hire service implicated in that attack (or at least the attackers) was built using a few thousand hijacked home Internet routers.
[Author’s note: The headline for this post was inspired by Glenn Fleishman‘s excellent Jan. 13, 2015 piece in MIT Technology Review, An Internet of Treacherous Things.]




Not sure why so many people pay to DDoS Minecraft servers; just make an automatic chicken farm big enough and you can kill the server completely from within the game, haha.
325gb is rather large, has anyone taken credit?
I noticed xbox live was having issues again last night too.
Maybe it is time to extend the concept of “gross negligence” to the failure to protect computers and network-aware hardware. The owners of those devices are not simply victims, they have unfulfilled responsibilities too. At the least, we should be able to keep those devices offline for as long as they are improperly protected.
it is a great idea congratulations
one small problem i can not change the insecure device to my settings except the ones in the option list ( please read small print in routers and anything else) can make no change in software and mainly i do not own the device because of the software license said so!
and i have no claim on anything because serviceability or usage or bla bla bla said so
if i don’t agree i don’t have to use it? please!! you and i are just captive customers with no voice or claim
If you are restricted by the fine print in the license then whoever owns that fine print is the one who should be on the hook for that negligence.
That makes enforcement tidier, easier to go after the Comcasts of the world instead of individuals.
I would agree except for one word: “The owners” are victims. In my opinion it’s the designers of the devices who are at fault. We as a security community have made security far too difficult for the average user to achieve. We don’t even create simple step-by-step instructions as to how to lock down the devices we continually rail against.
Until the designers wake up and start creating secure-by-default tools we will always have this problem.
The schools are just as much to blame. Even now secure coding 101 is not a required class. No student should able to graduate without fully understanding and committing to code securely.
Finally the compiler and API creators have a hand in this too. As long as they put out insecure tools for the coders to use, we’ll have problems.
There are fixes to be had, but it’s an industry-wide problem requiring multiple layers of remediation.
I’ve contacted verizon on numerous occassions to complain about the fact their latest revision routers have hard coded firmware that block you from shutting off UPNP, which makes their customers unsafe from malware or who knows what else.
There is nothing the user can do, your right, they are simply victims, and the manufacturer and ISP’s deserve alot of the responsibility! Anyone who still solely blames user error in this day and age, is suspect!
I’d say it’s worse than that. Many of the devices used for DDoS attacks are now ISP-provided equipment that are either misconfigured or broken-by-design. And even when they’re misconfigured, the ISP often will block the user from configuring the device, since they’re only concerned about their support costs.
@SeymourB That’s why I use my own router and not the one provided by my ISP. I plug my router directly into their router and configure my router to my specs. That way I don’t have to depend on their hardware for securing my network.
That works so long as you don’t have any ISP configured equipment in the mix. Even so much as a modem from them could mean that modem is susceptible to misuse.
Placing your router behind their router should protect all the devices behind your router, but it doesn’t prevent their router from being misused.
I think there was a recent report about a remote administration function being misused for DDoS purposes… which was enabled by ISPs so they could remotely manage their equipment at your location.
I’m with you up to a point, since I purchase all my own equipment and don’t rely on the ISP for anything besides a stable connection. But even that’s not a guarantee… for instance, if you have a cable modem, whether its your modem or the ISPs modem still gets sent the same configuration file from the ISP. As a result the same configuration is applied, with the same functions enabled, with the same vulnerabilities and restrictions. Nothing like being locked out of your own equipment, whee….
almost all ISP issued wireless modem/routers have modem mode then turns port1 into a WAN only port all features of the wireless router are disabled your security then lies in your wireless router and your computers
Great article! Thinking an excellent follow-up might be how individuals can access vulnerability of routers they control and links to related articles for maintaining router security.
I doubt anything will change unless/until individual ISPs are held liable for outgoing malicious traffic that originates on their networks. Most of them take many precautions against *incoming* malicious traffic, but merely take a reactive (at best) approach to dealing with *outgoing* malicious traffic.
Look at GMail, for example. They have some of the best filtering out there for dealing with incoming spam, but seem to be unconcerned with outgoing spam sent by GMail users.
I agree, but when most people still only blame users and when they see these things as victimless crimes, the ISP’s are never going to be pressured to give a dam. Companies will just continue to put backdoors in all our software and hardware and laugh at all the arrogant egotistical nerds who think it can never happen to them.
How long until my light bulb and thermostat (both running embedded, unpatched, Linux) are co-opted into an attack?
Was it Walt Kelly who wrote “We have met the enemy and they are us?”
Jonathan @nc3mobi
Why bother?… They already pwnd your router.
Close enough… “We have met the enemy and he is us.”
“…need only look to the attacks of Christmas Day 2015…”
Is that a mis-typed year or a prophecy?
If I have a pool, I am liable for damages if someone drowns in it that was trespassing unless I have taken reasonable precautions (like a fence) (attractive nuisance).
Where did you read that? some hack ambulance chasing lawyers page? lmao Maybe you should read this: http://blogs.findlaw.com/injured/2013/06/pool-hopping-injuries-whos-liable.html
I’m not sure how this analogy equates to computer networks? But what would you consider the proper precautions to stop “children” from hacking you? And how can they potentially become a victim in doing so? Which according to you would be the network owners fault for having an attractive network….lmao
Comments like yours, are why ISP’s give us hardware that is vulnerable by design, why we have an internet infrastructure that is vulnerable by design, and contrary to your delusional belief, its why even why very active computer experts aren’t that safe from being compromised. And noone is going to do a dam thing about it, which is what someone like you probably prefers!
Cool Out, AC! ;^)
Attacking eachother won’t help. Even if it’s fun for the attacker, it’s not nuch fun for the attackee.
Seriously, folks, the way to deal with juvenile hackers under 16 years is to fine the parents. Fine according to income.
Over 16 fine the parents plus counseling & community service. No internet, no computer games until community service is complete.
First of all its not only kids, to keep implying that is almost encouraging their activity. Or encouraging these criminal organizations to keep using kids as patsies. The leader of lizerd squad looks like hes in his late 20s or early 30s.
But you might be partly right, because some say bankrupting Aaron Swartz’s family is what drove him to his supposed suicide. But it also could of been the threat of 30 years jail time.
The children that pull these annoying pranks are still just children pulling pranks. Lets see what happens when one of them tries to put on big boy pants and go after the NSA or MI#.
I think the children know their place, and will keep their diapers on. lol.
A dreamy notion, but they can do serious damage, & a remedy needs to be found so they don’t just keep their diapers on, but graduate to a more serious level as they age, practicing all the way!
Fine the parents, limit access to electronic equipment, confiscate the equipment used in the attack, counseling & community service for 16 & older.
You’re not going to rein in the kids as long as you let them continue to interact with peers online that they crave impressing.
Ironically, recently DDos attacks blocked by my firewall originated from IP addresses that are assigned to Akamai.
LOL! Hilarious! ;^D
Did you let Akamai know? Their customers could be pwnd.
Along the lines of what Dick H said: the implementers of network infrastructure also bear some responsibility.
Most Cisco certified donk’s wouldn’t know an NTP reflection attack from a run of the mill man-in-the middle “walk in the park”. These sorts of “professionals” frequently deploy Internet-facing and wireless equipment.
Something like this with a few enhancements would allow anyone to independently verify the state of their border(s) http://www.whatsmyip.org/port-scanner/server/
I like that approach much better than cowboys who scan everything (without permission- erratasec for example) and try to drum up new business via press announcements/notoriety or direct contact with organizations who’ve left the proverbial kimono open.
Today’s SANS @Risk newsletter (http://www.sans.org/newsletters/at-risk) has a link to a story that appears on rapid7.com about automated tank guages (ATGs) at gas stations that are Internet-facing and have no security (https://community.rapid7.com/community/infosec/blog/2015/01/22/the-internet-of-gas-station-tank-gauges).
Talk about “Internet of Dangerous Things!”
tigger, Thanks for the link and heads-up about that SS/Rapid7 article/posting. I forwarded it to a CEO that needed the information.
Goodish article. Also good to see that point about minecraft when I tweeted you that exact thing 😉
I’m glad you write in a style that requires me to look up what “Cassandras” means.
I’ve been regular reader for awhile and have noticed this site is consistently offline, did Arbor refund your money because it doesn’t seem they are able to stop the attacks.
I also noticed that at work our systems report DDOS attacks that originate from Akamai as well.
I don’t know about ‘consistently’, but I do get an error a significant minority of the time. I figure it’s under attack, and just come back the next day.
Recently this site has been mostly accessible. During December and early January is when it was offline the most. I have access to several networks and would occasionally check from other sources to make sure it wasn’t just me.
So did the Arbor DDos protection actually work or did it just prevent the KOS web server from melting?
That’s strange. I check this site just about everyday, sometimes twice, & I’ve only had one time, as I recall, over the last few years that I couldn’t get right on the site.
Don’t know if it has to do with using Linux booted from a live disc & restricted user mode with SeaMonkey browser.
Curious, though.
That was a stupid comment, the website being up or down has nothing to do with your os or browser (facepalm)
There’s legal precedent to charge owners of home networks with crimes associated with unauthorized traffic (e.g.: a pirate using a nearby unsecured wifi network to download and share copyrighted material). Why not use the same precedents to charge owners of devices unwittingly used in DDoS attacks? If device owners aren’t cognizant of the associated security risks to others they are most definitely negligent and, I’d argue, complicit.
Uh oh! So what happens when some crook uses the “public” wifi Comcast is broadcasting from so many homes? Is that “my” legal exposure?
For me, I hope not. I told Comcast to turn off ALL the wifi with my new (25% more expensive per month) cable modem. I use a cheap WAP when I need wifi. It has a very nice security feature called an OFF switch.
Jonathan @nc3mobi
your suspect lol.
That came into my mind, also, but I think that it would punish the wrong party.
Besides, I don’t think it would play well when a young mother just got a computer that she knows little about & you go after her for something that the company that sold her the problem has not made it secure or easy to configure for the end user.
Why didn’t that company take the time & invest the resources to make a secure user interface that a non-geek could use safely?
I tend to think that the equipment being used, routers, modems, pc’s, etc. should be able to be shut down if it is being used in the commission of a crime.
No one would think twice about a cop stopping a car flying through traffic at dangerous & illegal speeds.
Or disarming a criminal who is in the process of committing a crime.
Why shouldn’t anyone who can shut down equipment that is being used in the commission of a crime, remotely? Got to be some hackers that could do this. ;^)
Of course, this might open the door to causing the problem & then wanting the user to pay to fix it, which, of course, is already happening.
Still, there might be a way is not payment is involved, or if done by the authorities, or MS. ;^)
I’m not sure I want the gov’t shutting off my internet access, because they believe my ip, router, or pc is being used in some crime, even though unbeknownst to me. I can see that leading to abuse.
But they should be able to stop the malicious traffic. We know if ISP’s could be able to do this, and then we wouldn’t have the problem anymore. OR as BK keeps eluding to if cloudfare simply shutdown known booter sites. I don’t understand the free speech argument at all…
A good analogy is, I leave my house locked up and gated. But because someone climbed the fence, broke through the window, or better yet, went through a secret door made by the architect that I didn’t even know existed, and then used my house to launch further attacks. Am I the one to be blamed? Or should the one who built the backdoor or the criminal himself take the full blame?
I have been complaining about gamers for years. My first pc game was in 1986 and I went from lan parties to the internet. I’ve always said pc gaming started to die after 2005. But I never realized how bad consoles were until this whole lizard squad vs finest squad, kim dotcom thing, this year. After reading about all the cheats even on consoles. And i had no idea until this article that consoles could be utilized in DDOS attacks. Now I might as well say all online gaming died in 2015.
The reason is, virtually noone is left in online pc gaming except computer nerds and anonymous hackers. Thats literally all there is playing now. Back in the late 90s and early 2000’s you had white hat admins who were able to protect their servers and attack back. They ensured fair play and competitive matches on their servers and kept them troll free. I feel this is one of the fakest times in human history. Maybe its the internets fault maybe its not. But Nowadays guys who try to have an honest server, or who encourage fair play, get hacked out of existence. and its sad.
I can only hope, now that besides gamers, hackers are starting to affect the rest of society things will change. One of the major problems these companies and game developes have to realize, is the moles and traitors are inside their companies and part of their own communities.
Thomas Tschersich, Deutsche Telekom AG’s computer security chief, says mobile devices “are the perfect target for attackers” and are to blame for the increased DDos attacks.
I could see an Android smartphone compromised without the owner’s consent, but an iPhone or iPad?
Later in this article: “Prolexic Technologies, now owned by Akamai Technologies Inc., last year reported an attack against an unidentified large financial institution, where mobile devices played an important role.”
Do you have a comment on this?
Here’s the full article:
http://www.bloomberg.com/news/articles/2015-01-27/smartphones-the-weak-spot-in-hacker-fight-deutsche-telekom-says
Along that line: Wife has a Note III phablet, uses it as aa phone & tablet to browse the internet. The default setting has the WIFI turned on. She went into a chain restaurant for lunch, noticed some kids at another table with a computer or smart phones, I forget which, giggling in a suspicious way. She suddenly gets a lot of gibberish on her phone from doing nothing, & knows she’s been hacked.
Take the phone to the service rep, “My phone’s been hacked.” “No way, phones don’t get hacked.” She shows him the phone’s message. “Oh, you’re phone’s been hacked.”
New sim card, transferred contacts, etc. Now, WIFI is turned off at all times.
I hate and despise all those features that claim to make some piece of technology “user friendly”. WPS, UPnP, Bonjour and the list goes on, first things to disable when I buy a new router.
Give me just clear instructions which I can use to set everything manually not “features” that are supposed to set everything for me “automagically”. Not only they are full of glitches and vulnerabilities but when there is a glitch or incompatibility (as often is the case, you can pull your hairs off, there is no recourse or things to tune other than perhaps hoping it will be solved in a future firmware upgrade.
Great article, In my opinion it’s the designers of the devices who are at fault.
My home network is well maintained and all known vulnerabilities are mitigated. Even so, it could still be co-opted for DDoS. Most likely the cable modem – being ISP configured is outside of my control even though I own it instead of renting from the ISP. Behind that IoT or other devices are probably the next likely to be enrolled in a botnet. I have 12 permanent devices on my home network and currently 10 guest subnet devices.
My home network is far better than the average. I seriously don’t think the average home network owner can secure their network enough. They could not even access some necessary configuration items thanks to their ISP. Bedside that the whole thing is more complex than necessary.
ISPs are the best positioned to provide a lot of the necessary security. They could block outgoing spoofed IP addresses. They could provide better CPE configurations and support. They could block obvious malicious outgoing traffic.
If you don’t have a commercial grade firewall, like a SonicWALL or a Fortinet home office firewall, you’re not secure. Sorry.
Interesting proposal but I would like to point out, just because someone owns a Porsche does not mean they know how to drive it and it never breaks down.
Owning expensive commercial security equipment does not automatically equate to being secure.
Fortinet: http://www.cvedetails.com/vulnerability-list/vendor_id-3080/Fortinet.html
Sonicwall: http://www.cvedetails.com/vulnerability-list/vendor_id-628/Sonicwall.html
= CIA Head: We Will Spy On Americans Through Electrical Appliances
http://www.infowars.com/cia-head-we-will-spy-on-americans-through-electrical-appliances/
= CIA Chief: We’ll Spy on You Through Your Dishwasher
http://www.wired.com/2012/03/petraeus-tv-remote/
I’ve thought someone was spying on me through my smart teeth for years. Now I’m sure of it.
Its been going on for a decade. https://www.youtube.com/watch?v=bZwJ6LeaO0Y
That’s what you get for allowing those CIA-trained dentists to work on your teeth. You thought crowns and implants were expensive because they used gold and other costly materials. Nope. It’s to reimburse the Gummint for the cost of the embedded electronics!
Here’s a little question: How much sense does it make to have the vast majority of our high-tech gizmos assembled in a country whose Army has its very own Cyber Division, leaders whose attitude toward the USA isn’t always very positive (to put it mildly) and which has about as much respect for basic human rights and privacy as the South Pole has palm trees? But that’s exactly what the current situation is, as long as our so-called American tech companies have their hardware Made In China. Especially by workers whose ‘dormitory’ housing would set off Eighth Amendment-based lawsuits if they did the same thing to prisoners here. Unbelievable.
Home Depot security is top notch. They not only had the big breach, but also 36k card numbers stolen by this guy in May –
http://kxan.com/2015/01/30/round-rock-man-sentenced-for-stealing-36000-credit-card-numbers/
http://www.linkedin.com/pub/daniel-marquardt/13/130/b07
More should be done by manufacturers when shipping their products to lock them down until the user selectively sets which features they want. It reminds me of the old days with Microsoft where they shipped their OS wide open. We know a lot more about human engineering to enable Users to open only what they actually need. Also, gaming sites should offer an audit to alert Users to find those that still have the factory settings.
OK, so December 2014 was notable for the amount of DDoS traffic to your site.
How did January 2015 fare?
And keep shining that light for all of us.
Thank you very much!